Password Access Control Workflow
(Feature available only in the Premium and Enterprise Editions)
What is Access Control?
Access control is an assurance methodology that ensures the authenticity of users and that they have suitable access to perform a task or access data. In other words, access control can be defined as a selective restriction of access to data. Access control is made of two major components: authentication and authorization. Authentication is a way to verify if a person is who they claim to be. However, authentication alone is not sufficient to protect data, and an additional layer called authorization, which determines whether a user is intended to access the data or perform an action they are attempting, is mandatory. Data security is null without authentication and authorization.
Glossary of Terminologies
| Term | Description |
|---|---|
Request |
The user has to make a request to view the password. |
Waiting for Approval |
User's password release request is pending with administrator(s) for approval. |
Check Out |
Administrator has approved the request and the user can view the password. |
Approve/Reject |
Administrator can either approve or reject the password request. |
Yet to Use |
Indicates that the user is yet to view the password released by the administrator. |
In Use |
Password is being used exclusively by a user. |
Check In |
Giving up/revoking password access. |
Access Control Mechanism in Password Manager Pro
Password Manager Pro provides a password access control mechanism that allows administrators to grant password access to users for a specific period. Admins can start granting exclusive privileges once a password is ready to share, and only one user is allowed to use a particular password at a single point of time.
You will learn the following topics concerning Password Access Control workflow in this document:
- How does the Password Access Control mechanism work?
- How does precedence work for Password Access Control?
- Steps to implement Password Access Control workflow
3.1 Implementing Access Control at Resource level
3.2 Implementing Access Control at Account level
3.3 Viewing Access Control Details - Use case scenarios
- Message Templates
- Limitation in Access Control Workflow
1. How does the Password Access Control Mechanism Work?
Once the password access control is enforced for a resource or an account, the following workflow is invoked for password access attempt by the users:
- A user needs access to a password that is shared with them.
- The user makes a request to access the password.
- The request is sent to the designated administrator(s) for approval. If more users require access to the same password, all the requests will be queued up for approval.
- If the administrator does not approve the request within the stipulated time, the request becomes void. In case the user has specified a particular time frame for password access, then the request becomes void after the user-specified stipulated time.
- If the request is rejected by even one of the designated administrators, it becomes void.
- If the administrator approves the request, the user will be allowed to check out the password only during the stipulated time, or at the time set by the administrator during approval. In case more than one administrators have to approve a password request, the user will be allowed to check out the password only after all of the designated administrators have approved the request.
- Once the user checks out the password, it will be available exclusively for their use till the stipulated time.
- If any other user requires access to the same password concurrently, they will be provided access only after the previous user checks in the password. This rule applies to all types of user roles in Password Manager Pro, including administrators, password administrators and owner of the password.
- Administrator can also revoke password access for the user any time. The password will be forcefully checked-in during such circumstances, denying access to the user. Once the user finishes their work, the password will be reset.
- While granting a temporary exclusive access to a user, you can enable administrators to view the password concurrently by selecting the option Enforce users to provide reason for password retrieval under Admin >> Settings >> General Settings.
Note: The access control workflow does not override the password ownership and sharing mechanism of Password Manager Pro. Rather it is only an enhanced access control mechanism. Normally, when a password is shared with a user, the user will be able to view the password directly. Now, with the password access control mechanism, the user will have to request access to a password, even if they have access to it.
2. How does Precedence work for Password Access Control?
Account level access control configuration takes higher precedence over Resource level access control configuration as explained below in detail:
- When Access Control settings are enforced on a resource, the settings are automatically applied to all the accounts within the resource. However, when Account level access control settings are applied to an individual account within the resource, it overrides the resource level access control settings that were previously applied for the selected account.
- Let's assume, PMP-win10 is a resource with several accounts under it. When access control mechanism is enforced for the resource PMP-win10, the settings are applied to all accounts under PMP-win10 automatically. In case, if Account Level access control is applied for a user account, say Administrator, within the resource PMP-win10, that action will override the resource level access control that was earlier applied for the user account Administrator. However, the access control settings for the rest of the accounts within the resource will remain unchanged.
- If resource level access control settings are deactivated, it will not affect the account level access control configurations within the same resource.
- If account level access control settings are deactivated for an account, then the resource level access control, if configured, will be applied to the account automatically.
- Account level access control settings come in handy when certain accounts within a resource require a higher level of security.
- Let's assume CentOS-1 is a resource with several accounts under it. Access control mechanism is enforced for CentOS-1 and settings are customized in a way that it requires the approval of one authorized administrator to access the resource; the same settings will be applied to all accounts under the resource. However, the user account Root under the resource requires better security. In this case, account level access control configuration can be applied to Root so that it requires approval of at least five authorized administrators to gain access to its password. Modifying access control configuration for Root will not affect the configuration done for CentOS-1 and the other accounts under the resource.
3. Steps to Implement Password Access Control Workflow
Follow the below steps to implement password access control for a resource or an account:
3.1 Implementing Access Control at Resource Level
3.2 Implementing Access Control at Account Level
3.3 Viewing Access Control Details
3.1 Implementing Access Control at Resource Level
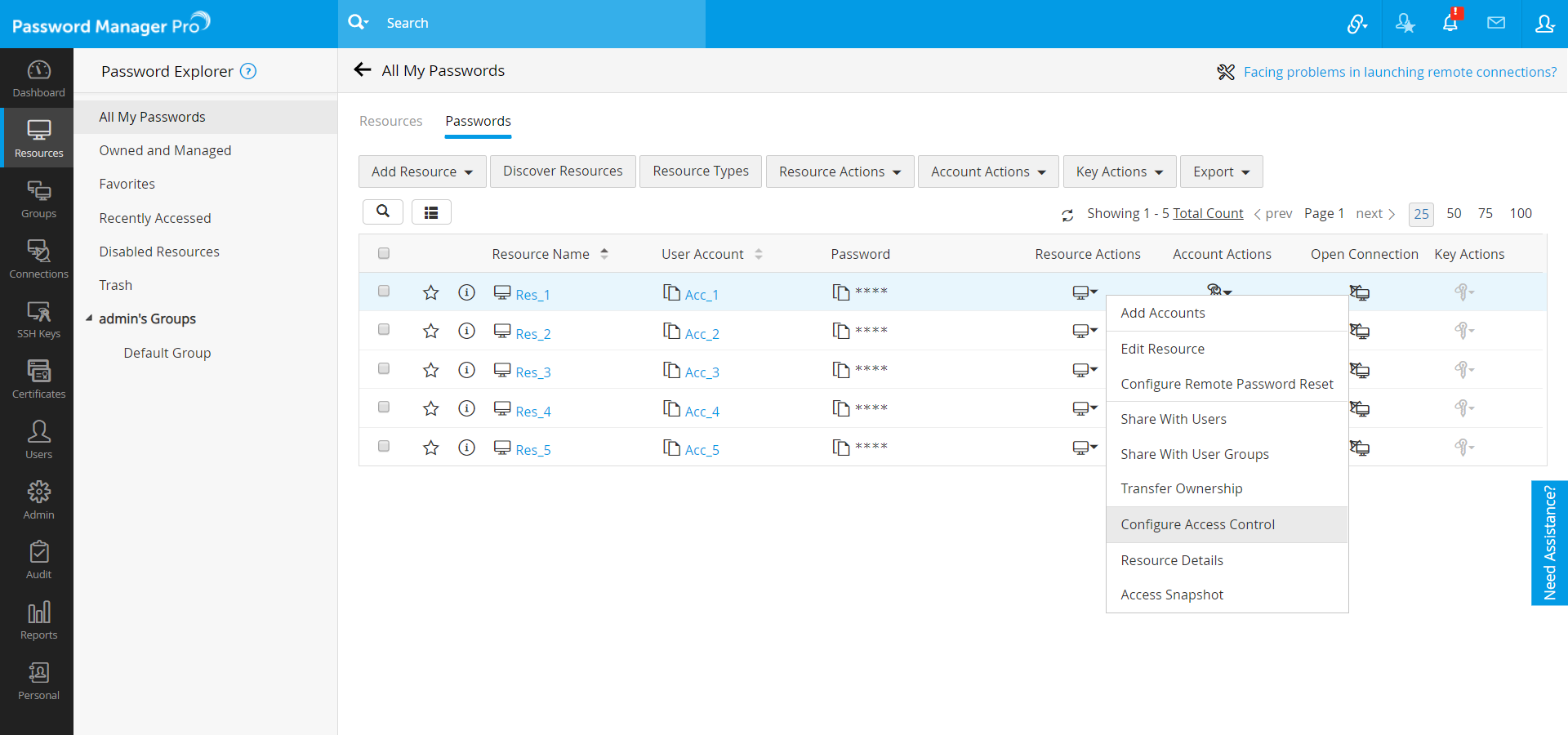
- To implement access control for multiple resources, navigate to the Resources tab and select the resources for which you wish to enforce access control, click the bulk Resource Actions menu and choose Configure >> Access Control.
- To implement access control for a single resource, in the Resources tab, click the Resource Actions dropdown beside the required resource and choose Configure Access Control.
3.2 Implementing Access Control at Account Level
With Access Control at account level, it is possible to set password access control independently for each account under a resource, without affecting the access control configurations of other accounts in the resource. This ability to set unique configurations for each account helps users maintain unparalleled security levels for each account, based on requirements.
Follow the below steps to implement access control for accounts:
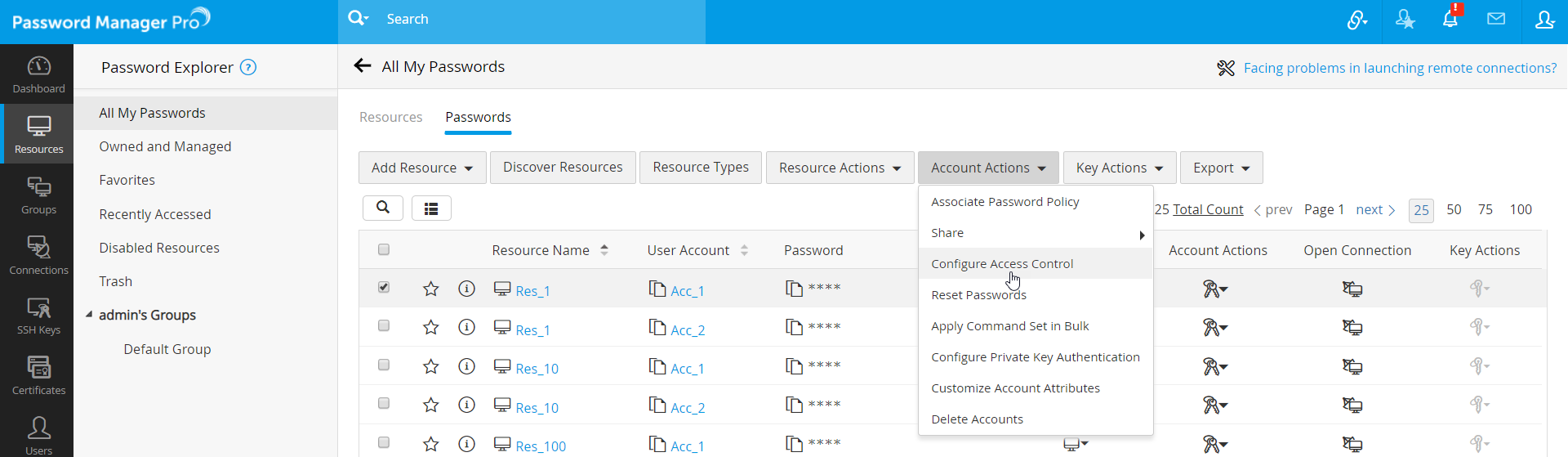
- To implement access control for multiple accounts, navigate to Resources and switch to the Passwords tab. Select all accounts for which you wish to enforce access control in bulk, click the bulk Account Actions menu and choose Configure Access Control.
- To implement access control for a single account, switch to the Passwords tab, click the Account Actions dropdown beside the required account and choose Configure Access Control. Alternatively, to implement access control for one or more accounts belonging to the same resource, click the resource name in the Resources tab. In the Account Details dialog box that opens up, select the required accounts and click More Actions >> Configure Access Control or click Account Actions >> Configure Access Control beside the required account.
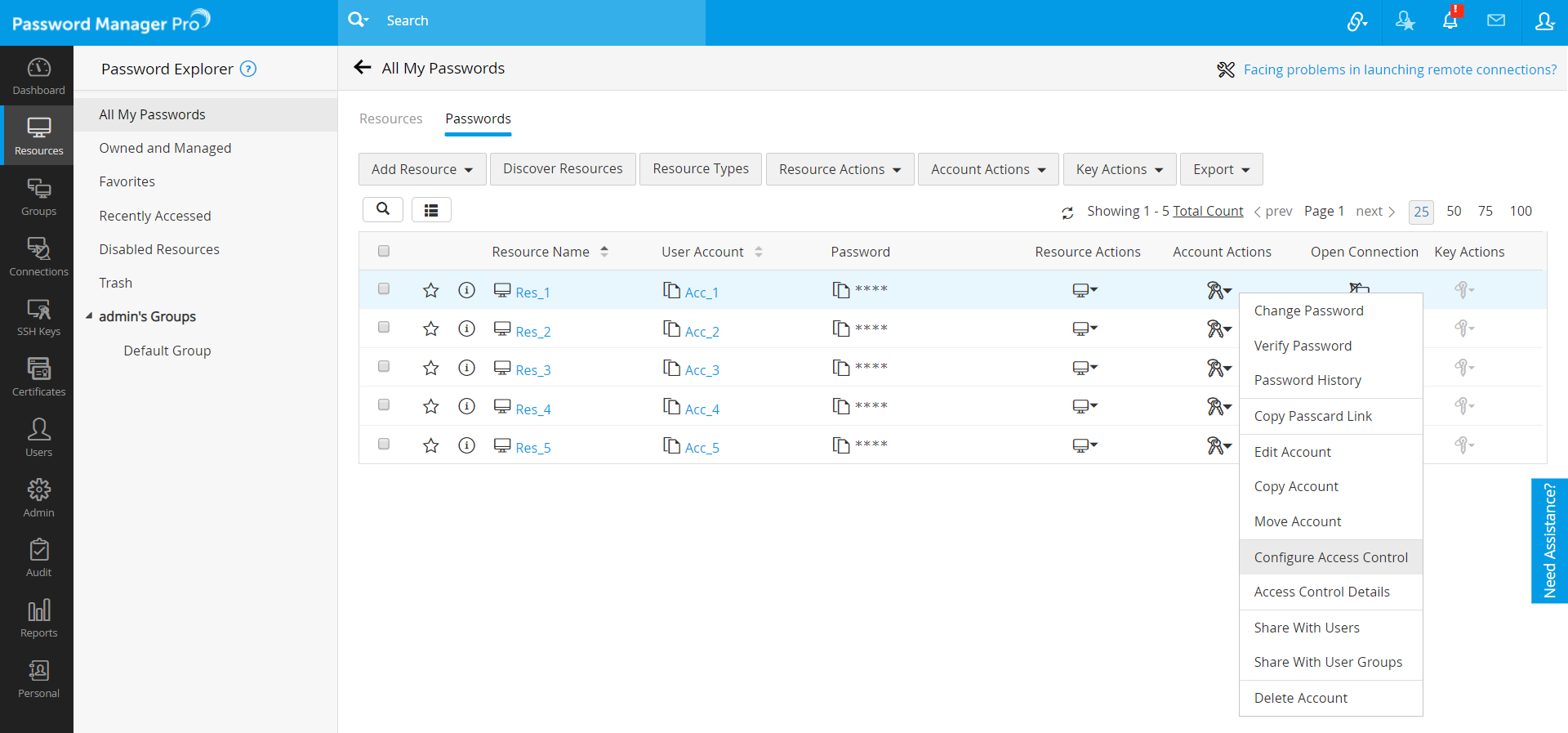
- In the Configure Access Control window that opens, you will see four tabs. Customize the settings as required.
- Approval Administrators
- Excluded Users
- Miscellaneous Settings
- Auto Approval
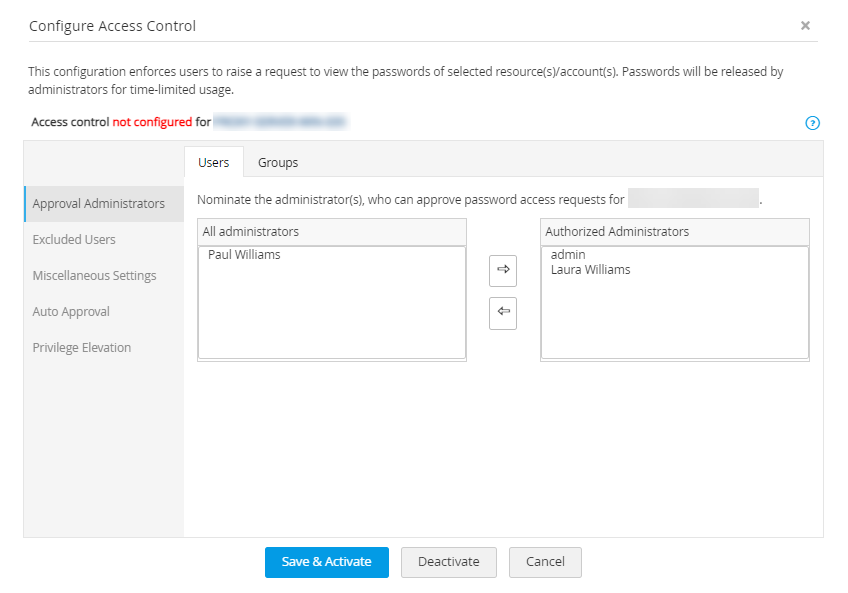
i. Approval Administrators
Designate the administrator(s) as the approvers of password release requests. The list of all administrators, password administrators, and privileged administrators in the system are listed in the left pane. You can designate as many administrators as you wish for a particular resource or an account. Anyone from the list of Authorized Administrators could approve the requests raised by users.
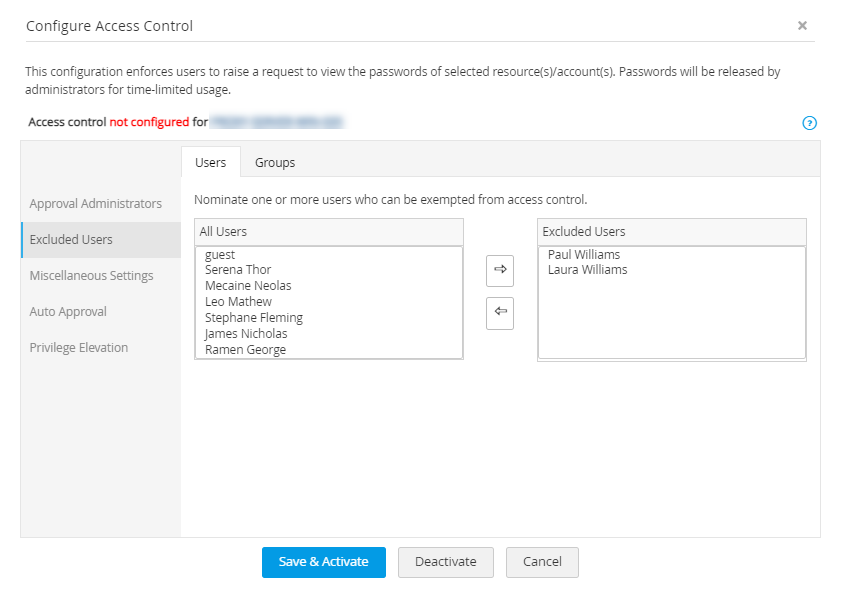
ii. Excluded Users
Exclude a set of users from the access control workflow using this option. The excluded users will be able to access passwords directly without raising requests.
iii. Miscellaneous Settings
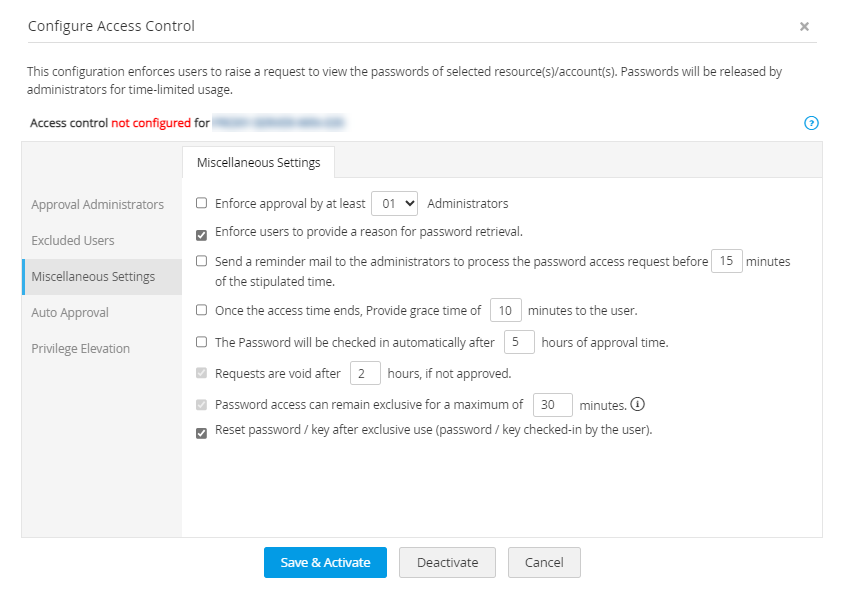
- Enforce approval by at least __ administrators: Select this option to enforce approval by a specific number of administrators for all password requests. This number can vary from 1 to 10 administrators and you can customize this by choosing the number of admins under Admin >> Settings >> General Settings >> Maximum X approval admins (You may give minimum of 1 to maximum of 10 admins). If you wish to enforce approval by at least 10 admins, then you must designate 10 admins as the authorized administrators under the Approval Administrators section.
- Enforce users to provide a reason for password retrieval: Use this option to mandate users to provide a reason when they try to retrieve a password in plain text by clicking the asterisks. This is useful for auditing purposes.
- Send a reminder mail to the administrators to process the password access request before X minutes of the stipulated time: Use this option to set a time at which a reminder email will be sent to the administrator about the password request that is yet to be approved. Password Manager Pro will send the reminder email at the specified number of minutes before the void time.
- Once the access time ends, provide grace time of X minutes to the user: Enable this option to provide a grace time of up to 60 minutes to the user, after the password access time ends.
- The password will be checked in automatically after X hours of approval time: Use this option to specify the exact time after which the password will be checked in automatically and will no longer be available for use.
- Requests are void after X hours, if not approved: Use this option to specify the maximum time, in hours, after which a pending password request will become void if the administrators do not approve. If even one administrator approves the password request, then the approval status will be sent as notification to the other authorized administrators.
- Password access can remain exclusive for a maximum of X minutes: Select this option to enforce concurrency controls for password access. During this specified time, the password is made available for the exclusive use of a particular user and no one else, including the resource owner, is allowed to view the password. By default, the password will remain exclusive for 30 minutes. However you can modify it to a desired value. For example, if you specify the time period as two hours, the password will be made available exclusively for that user for two hours. Others cannot view the password during that time. After the specified time, the password access will be void and will not be available to the user and other users will be able to view the passwords. If you specify the value as '0' hours, the password will remain exclusive for unlimited hours.
- Reset password / key after exclusive use (password / key checked-in by the user): Select this option to enforce automatic reset of password once the user checks in the password thereby giving up access. For automatic password reset to take effect, you need to ensure that all required credentials have been supplied to the resource for remote password reset or you should have installed Password Manager Pro agents in the resource. Otherwise, the automatic password reset will not take effect. Click here for instructions on Remote password reset and password reset via Password Manager Pro agents.
Note: You can also designate user group(s) as approvers for password release requests. When a user group is designated as an approver, all the users with admin rights within that group (the administrators, password administrators, privileged administrators and admin users with the custom role) are given access rights. If you have enforced approval by a particular number of administrators, say 5, then the authorized user group must have at least 5 valid administrators.
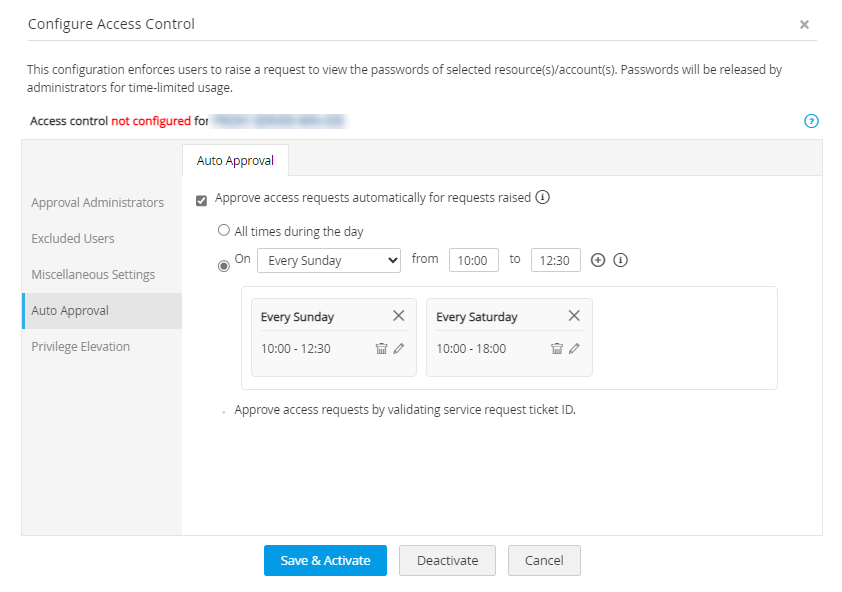
iv. Auto Approval
- Password Manager Pro provides the option to set automatic approval of password access requests. This auto-approval feature will be handy during the times when an administrator may not be available to approve access requests for users. To implement this, administrators can set an approval time for every day or specific times on specific days of the week. All password access requests that are raised in this time frame will be auto-approved and the authorized administrators will be notified. For example, you can set auto-approval for all requests raised between 2 p.m to 3 p.m on Saturday. You can set upto 3 approval time frames for a single day. Except for the automatic nature of approval, all other aspects of this feature will follow the access control workflow.
- Once you have configured the necessary options for setting up the access control workflow for a resource or an account, click Save & Activate.
3.3 Viewing Access Control Details
Once Access Control is activated for an account or a resource, the Access Control Details option consolidates all the settings applied and provides it in a single window for easy perusal. Please note that the Access Control Details window can be accessed from the Account Actions menu only. Follow the below steps to view the access control details:
- Navigate to the Resources tab and switch to the Passwords tab.
- Click the Account Actions icon beside the required account and choose Access Control Details from the dropdown. Alternatively, click a resource name in the Resources tab. In the Account Details dialog box that opens, click Account Actions >> Access Control Details beside the required account.
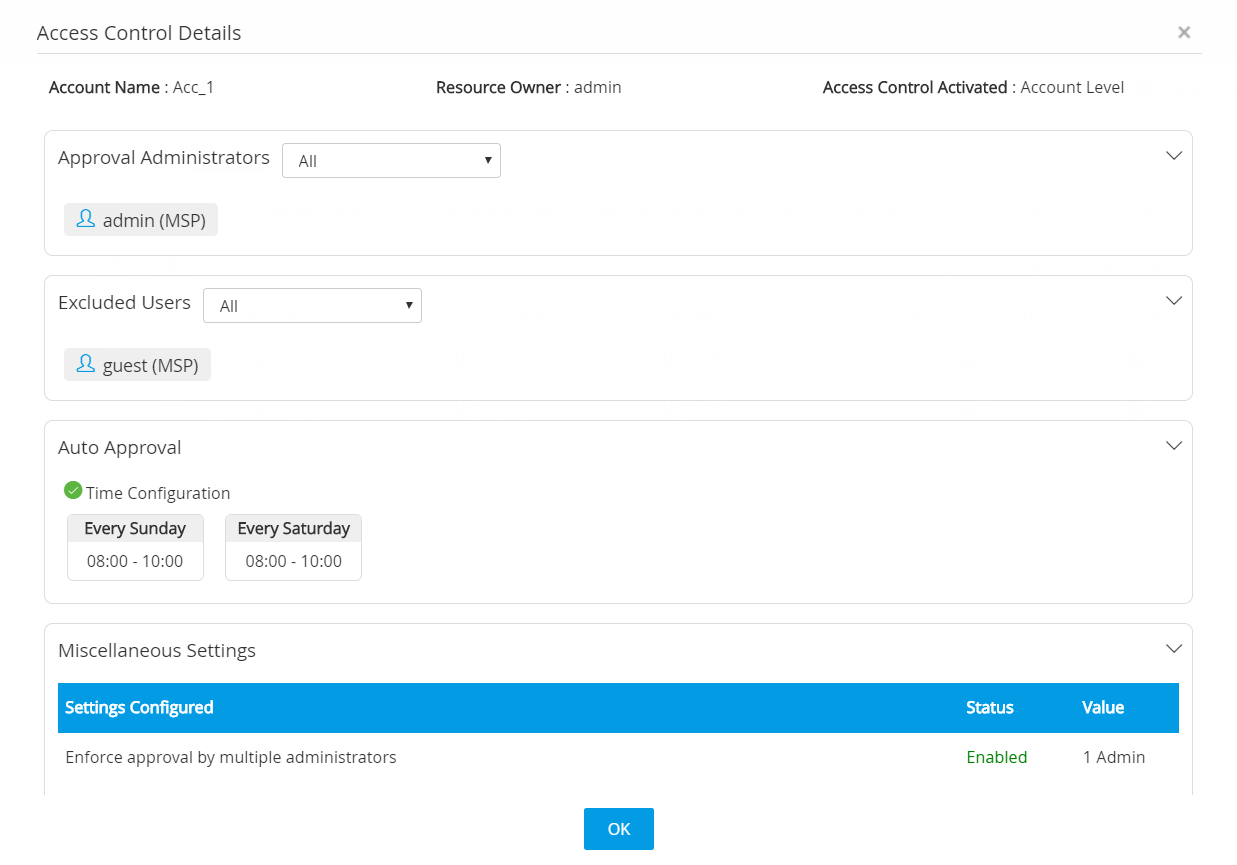
- The Access Control Details dialog box will display the following details:
- Account Name.
- Resource Owner.
- Type of Access Control activated: Resource Level or Account Level.
- List of Approval Administrators (users and/or groups).
- List of Excluded Users (users and/or groups).
- Auto Approval time frame set for this particular account or resource.
- Any Miscellaneous Settings configured such as, enforcing approval by multiple administrators, enforcing users to provide a reason for password retrieval etc.
Note: Users can choose the required resources in the domain account and request permission to access them. Users will be able to access only the approved resources using that domain account.
4. Use Case Scenarios
The following are some of the use case scenarios in which access control workflow will be useful in an organization.
Case 1: User Requesting Access to View a Password
To access a password protected by the access control workflow, a user will have to request the administrator to grant permission to view the password.
Steps To Make a Request:
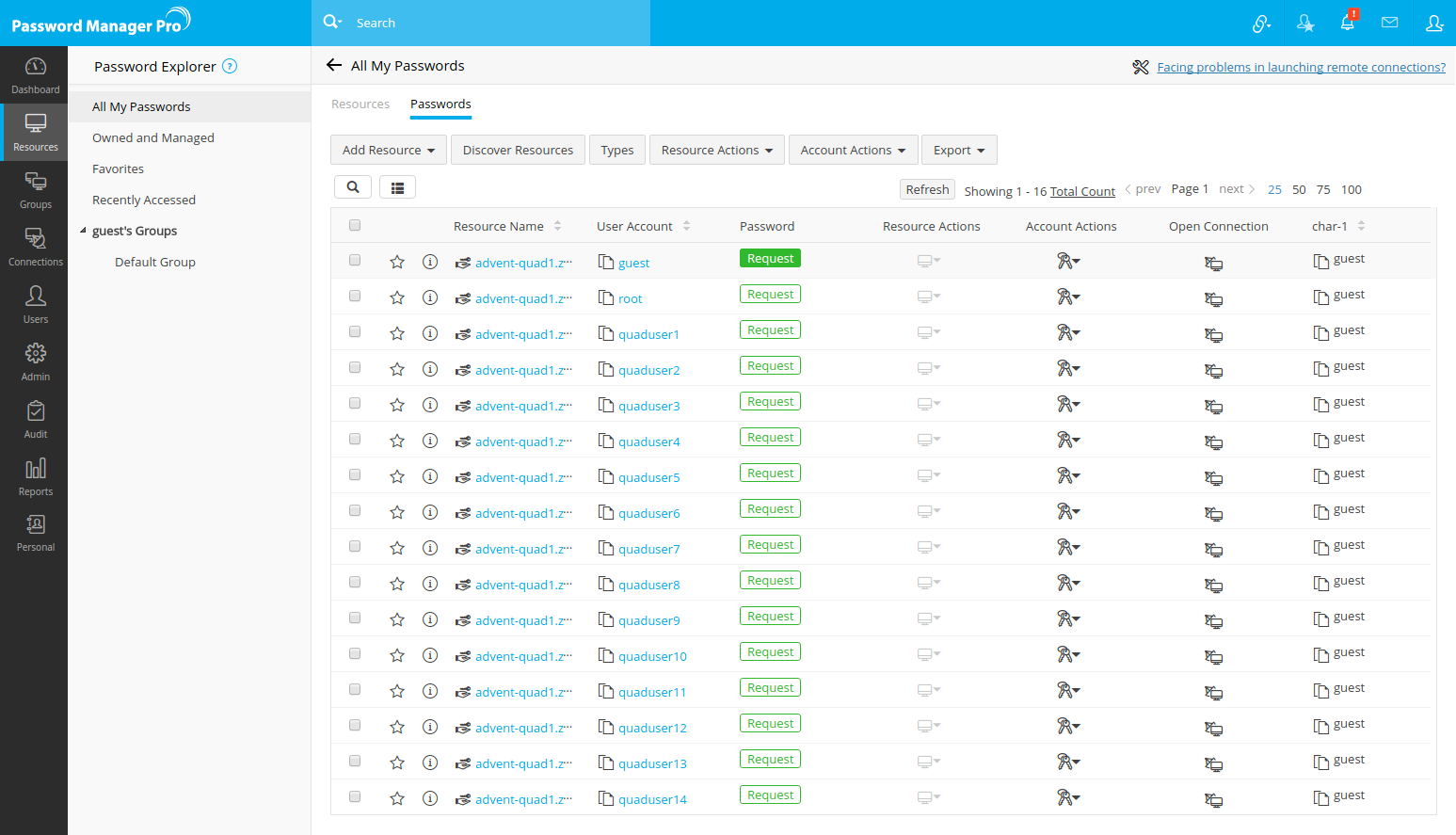
- Click the Resources tab from the left pane and click the Passwords tab.
- All the passwords will be listed in the table below. Click Request beside the desired passwords to request the administrator to grant permission to view the passwords.
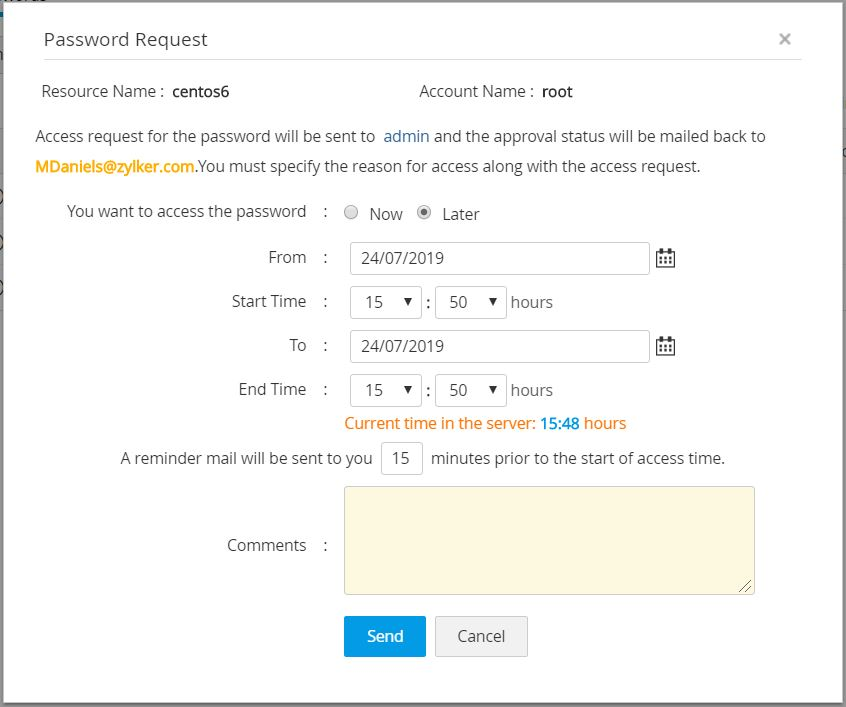
- In the new pop-up form that opens, you will be able to:
- Specify when you want to access the password - now or later.
- Enter a reason to view the password.
- Specify the time before which a reminder email is to be sent.
- Click Send.
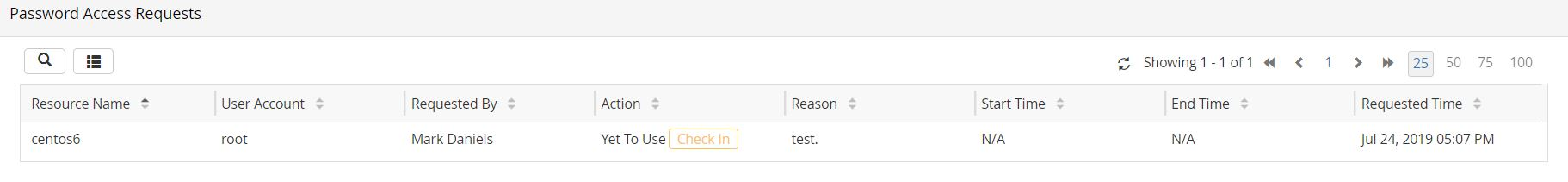
- Once the administrator approves your request, you will be allowed to view the password. Till then, the status will be Waiting for approval.
- Once the administrator approves the request, the status will change to Check Out. To view the password, click Check Out. Please note that the Check Out button will be enabled only during the approved access time.
- Click Save. Now, you will be allowed to view the password.
Case 2: Administrator Approving a Password Request
If you're an administrator and a user has requested your approval to view a password, you will receive an email notification about the request. You can view all the requests pending your approval from the Admin tab.
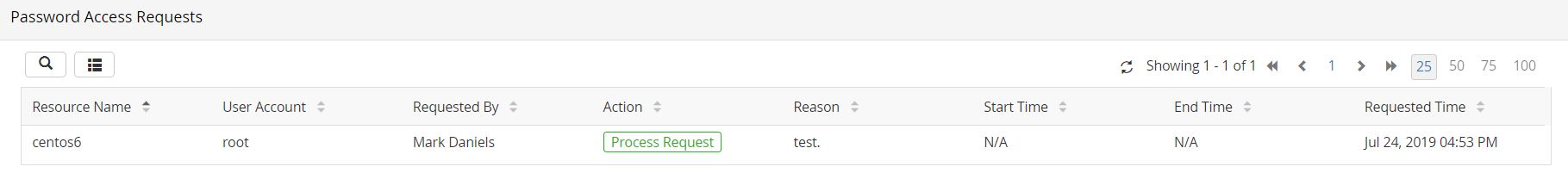
Steps to Approve a Request:- Navigate to Admin >> Access Review >> Password Access Requests.
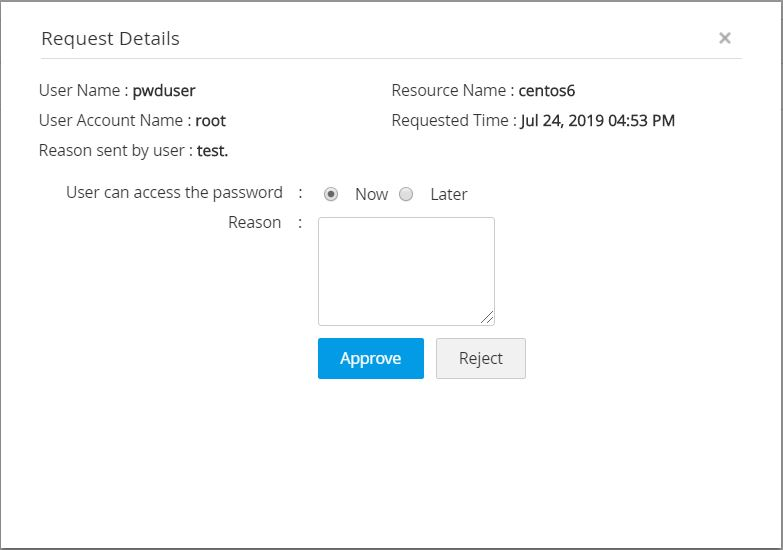
- Click Process Request beside a request to allow the user to view the password. Once you do this, a new window will open where the administrator can do any of the following things:
- Approve or reject the password access request.
- Specify when the user can access the password - Now or Later.
- Specify the reason for approval / rejection of the request.
- Immediately after you approve the request, the status of the link will change to Yet to Use, indicating that the user is yet to check out the password.
- Once the user has viewed the password, the status will change to In Use.
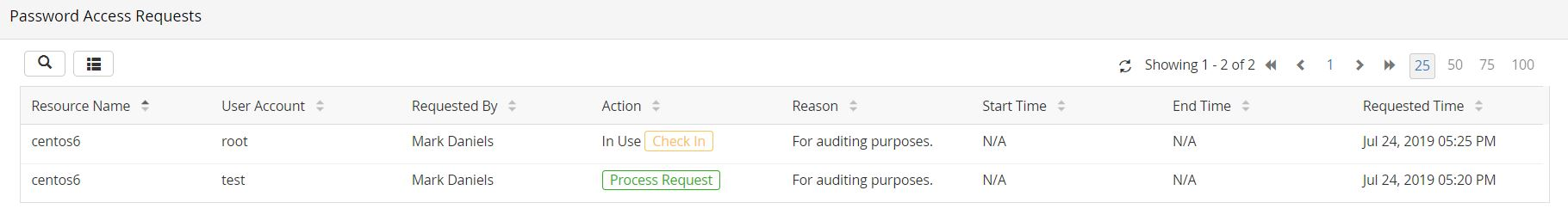
Note: If a password access request is rejected by an admin in the above scenario, the request will be removed from the queue.
Case 3: User Requesting Access and Administrator Approving a Password Request for Windows Domain Account
Steps to request a password:
- Click the Resources tab from the left pane and click the Passwords tab.
- All the passwords will be listed in the table below. Click Request beside the desired passwords to request the administrator to grant permission to view the passwords.
- In the new pop-up form that opens, you will be able to:
- Choose the resource(s) to be accessed - Current Windows Domain Machine, All Resources or select the required resource(s) from the dropdown.
- Specify when you want to access the password - now or later.
- Enter a reason to view the password.
- Click Send.
- Once the administrator approves your request, you will be allowed to view the password. Till then, the status will be Waiting for approval.
- Once the administrator approves the request, the status will change to Check Out. To view the password, click Check Out. Please note that the Check Out button will be enabled only during the approved access time.
- Click Save. Now, you will be allowed to view the password.
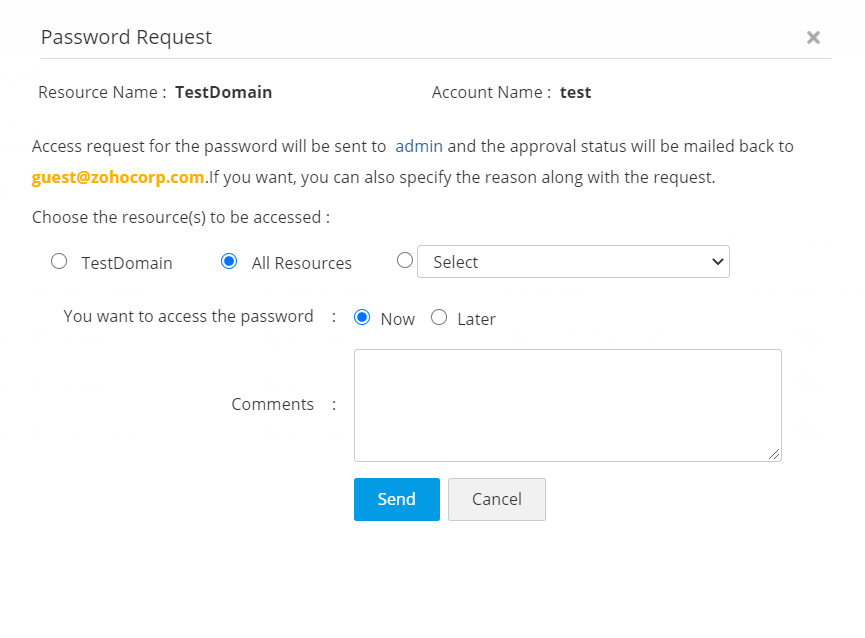
Note: Users can choose the required resources in the domain account and request permission to access them. Users will be able to access only the approved resources using that domain account.
To Approve a Request:
- Navigate to Admin >> Access Review >> Password Access Requests.
- Click Process Request beside a request to allow the user to view the password. Once you do this, a new window will open where the administrator can do any of the following things:
- Change the Target Resource(s).
- Specify when the User can access the password - Now or Later.
- Specify the reason for approval / rejection of the request.
- Approve or Reject the password access request.
- Immediately after you approve the request, the status of the link will change to Yet to Use, indicating that the user is yet to check out the password.
- Once the user has viewed the password, the status will change to In Use.
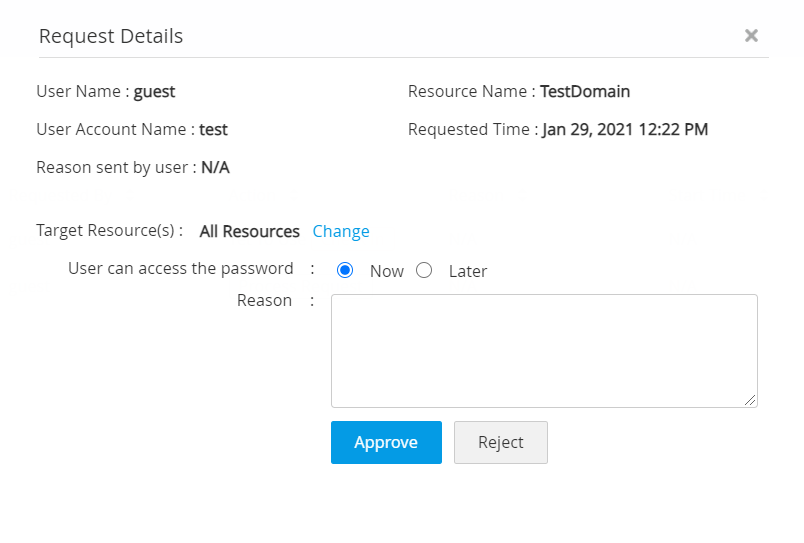
Case 4: User Completes their Password Usage
The crux of the access control mechanism is that the user will be allowed only temporary access to passwords. So, once the user finishes their work, they can give up the password.
To Give Up Access to the Password:- Click the Check In button beside the password. Now the password will be checked back into the system and the status will change as Request again.
- You will no longer be able to view the password. In case, you require access again, you will have to go through the Request-Release process again.
Case 5: Administrator Forcefully Checks In the Password
Access control mechanism allows exclusive access privilege to a user for a specified time period. During this period, no one else will be allowed to view the password, including the owner. In case an emergency arises to revoke the exclusive permission to the user, administrator can forcefully check in the password at any point of time.
To Forcefully Check In a Password:
- Go to Admin >> Access Review >> Password Access Requests.
- Click Check in beside the specific request to revoke the user's access permission. Once you do this, user will not be allowed to view the password. The password access request will also vanish from the list.
Case 6: What Happens if the Automatic Scheduled Password Reset Fails During Password Check In
Once a password is checked out by a user, it will be checked in due to any of the following three reasons:
- User checks in the password on their own after password usage is complete.
- System automatically revokes the password after the stipulated time.
- Administrator forcefully checks in the password.
When password is checked in, if the admin settings require automatic password reset, Password Manager Pro will try to reset the password. In case Password Manager Pro is not able to reset the password in the actual resource, Password Manager Pro will immediately trigger email notifications to the administrators who approved the password access request of the use so that they can troubleshoot and set things right. The password reset failure will also reflect on the audit trails.
Case 7: What Happens if a Scheduled Password Reset Scheduled Task Runs When a Password is Checked Out?
Password Manager Pro provides an option to create scheduled tasks for automatic and periodic password resets. It is possible that a scheduled task starts executing the reset of a password that is currently checked out by a user. If that reset task is allowed to execute successfully, the user will be working with an outdated password. To avoid such password mismatch issues, Password Manager Pro will prevent the reset of that password alone while all other passwords of other resources that are part of the scheduled task will be reset. The failure to reset the exempted password during the password reset schedule will reflect on the audit trails.
Case 8: Disabling Access Control
As an administrator, if you want to disable access control for any resource or an account, you may do so at any time as explained below.
i. Deactivating Access Control for Resources
- Go to the Resources tab and select the resources for which you wish to disable access control.
- Go to the bulk Resource Actions menu, choose Configure >> Access Control and click Deactivate in the Configure Access Control dialog box.
- To deactivate access control for a single resource, click the Resource Actions icon beside the required resource and choose Configure Access Control from the dropdown. Click Deactivate in the Configure Access Control dialog box.
Note: Deactivating the Resource level access control will not affect any Account level access control configuration enforced on the accounts belonging to that resource.
ii. Deactivating Access Control for Accounts
- Go to the Resources tab, switch to the Passwords tab and select the accounts for which you wish to disable access control.
- Go to the bulk Account Actions menu, choose Configure Access Control and click Deactivate.
- To deactivate access control for a single account, click the Account Actions icon beside the required account and choose Configure Access Control from the dropdown. Click Deactivate in the Configure Access Control dialog box.
Now, the Access Control for the selected resources or accounts is deactivated. So, any user who has permission to view a password (owned/shared) can directly view the password without going through the access control process.
Note: If Account level access control is deactivated and there is a Resource level access control already in place for the resource, then the Resource level access control will be automatically applied to the account as well. Click here to read more about how precedence works for access control settings.
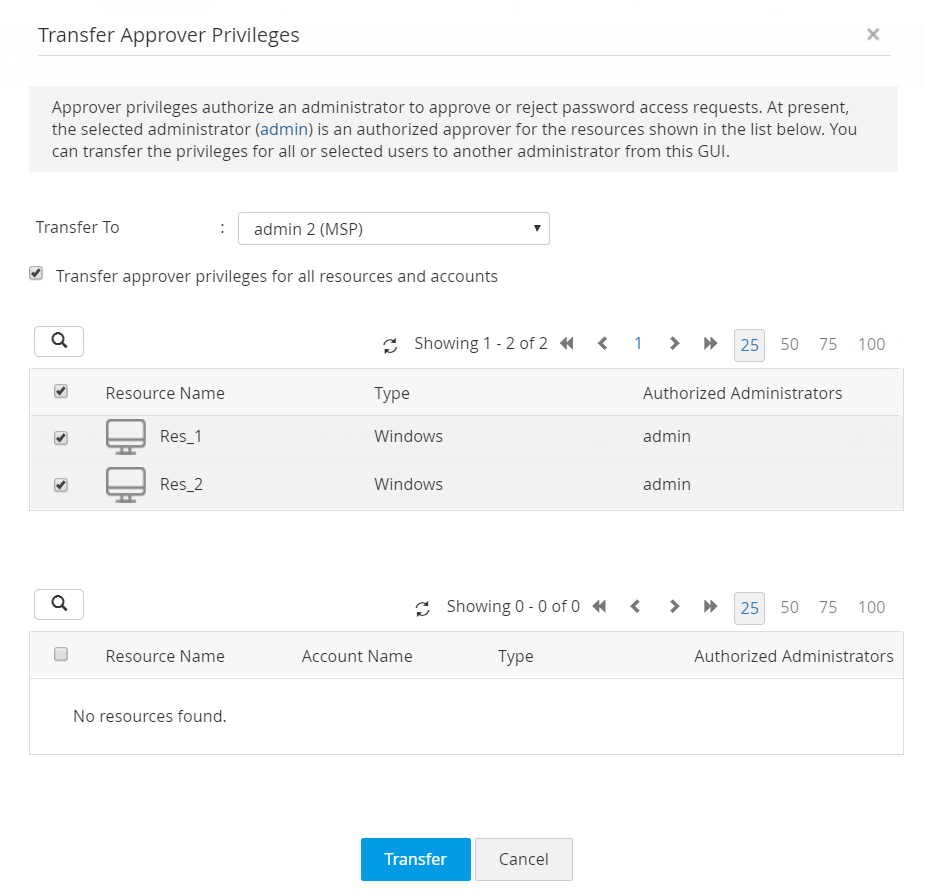
Case 9: Transferring Approver Privileges to Other Administrators
When an administrator leaves the organization or moves to a different department, resources/ accounts owned by that administrator are transferred to some other administrator. If the departing administrator had acted as the approver for password release requests, the approval privileges should also be transferred. All the resources and accounts that were earlier controlled by one admin can be easily transferred in bulk to another admin. Follow the below steps to learn how to transfer approver privileges from one administrator to another.
To Transfer Approver Privileges:
- Navigate to the Users tab and select or search for the user whose approver privileges you would like to transfer to another admin.
- Click the User Actions icon beside that user and select Transfer Approver Privileges from the drop down list.
- In the Transfer Approver Privileges window that opens, all the resources and accounts for which the selected admin is an authorized administrator will be displayed. Choose the desired resources.
- From the Transfer To drop down, select the admin to whom you would like to transfer the approver privileges to and click Transfer. The approver privileges will be transferred and the authorized administrator will be subsequently changed.
5. Message Templates
By default, Password Manager Pro has predefined templates for access control dialog boxes such as Password Request, Password Check In, Password Check Out. Using message templates, the administrators will be able to alter the messages in access control workflow dialog. To customize the messages in access control dialog:
- Navigate to Admin >> Customization >> Message Templates.
- For each category, you will find a number of sub-categories with a dedicated message template.
- Preview the existing content for each template by clicking the respective Preview link.
- Click Edit Template against the desired template to edit the content.
- In the Access Control Template window, enter a customized Message.
- While entering the Message, you can specify placeholders for certain values like ORG name or user email, etc. The exact ORG name will be replaced with the place holders at runtime. The allowed placeholders for each template can be found at the bottom of its respective Access Control Template window.
- Click Save to save the message template.
- Click Reset to Default to reset the message template to the default message.
- Click Cancel to cancel and exit the Access Control Template window.
- The Access control dialog box of the respective categories will now have the new content.



6. Limitation in Access Control Workflow
The password access control workflow in Password Manager Pro currently presents a compatibility issue when it comes to High Availability secondary servers. If the primary server becomes unavailable, Password Manager Pro users won't be able to utilize the password access control workflow.
To solve this, administrators can use a workaround solution, though it needs careful tracking of approved requests in that timeframe. Here's how to use the password access control workflow when the primary server is down:
- Head to the <Password Manager Pro installation directory>/conf folder on the secondary server and open the system_properties.conf file.
- Append a new system property - PwdAcsSecSrvr.AcsCtrl=true at the file's end, then save the changes.
- Proceed to restart the Password Manager Pro application on the secondary server to ensure the modifications take effect.
Upon the primary server's restoration, the automated check-in will not work efficiently for the resources checked out from the secondary server during the interim time. So, it becomes the administrator's responsibility to review manually and check-in the resources that were checked out during the interim period.