Multi-factor authentication (MFA) was designed to significantly reduce password-based attacks. Even with the widespread implementation of MFA, we have witnessed sophisticated threat actors like Lapsus$ successfully breach major corporations through a deceptively simple attack method known as MFA bombing (also known as MFA spamming or a MFA fatigue attack).
This attack method does not require hacking skills or expensive tools. Instead, it focuses on exploiting the most unpredictable element within any security system: human behavior. According to research conducted by Microsoft, they have detected over 382,000 MFA fatigue attacks in a single year, with 1% of users blindly accepting the very first unexpected push notification. It has become evident that organizations need more than just MFA implementation—they need comprehensive protection strategies.
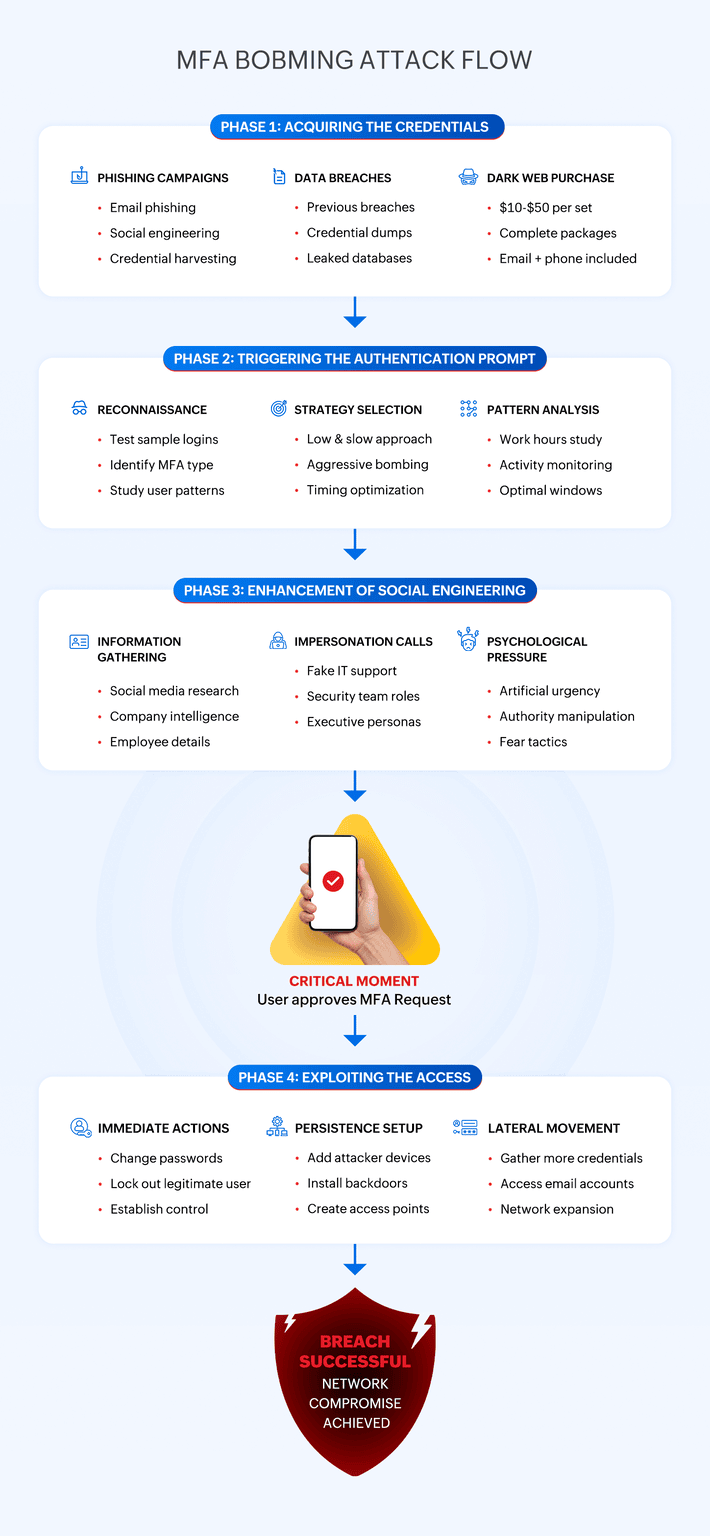
MFA bombing—also known as MFA fatigue, MFA prompt bombing, or push bombing—refers to a social engineering attack where threat actors flood the target device with repeated MFA requests. The goal is to provoke the target until they approve one of the malicious authentication attempts out of frustration, confusion, or simple muscle memory.
Unlike other password attacks, MFA bombing succeeds because it weaponizes everyday technology against users. Every legitimate push notification can potentially be exploited as an attack vector when threat actors control the frequency and timing of these authentication requests.
This phase often begins weeks or months before the actual bombing attack. Threat actors invest considerable time in gathering valid login credentials through various channels. The dark web marketplace for compromised credentials has become vast and cheap, with attackers sometimes able to purchase verified credential sets for major corporations for as little as $10 to $50 per set.
Once attackers have valid credentials, they move into the authentication prompt triggering phase, which requires planned timing and strategy. Rather than immediately launching an aggressive bombing campaign, sophisticated threat actors often begin with reconnaissance. They'll attempt a few sample logins to get an understanding of the target's MFA setup, identify the specific authentication app or service being used, and determine the user's typical online activity patterns.
Some attackers adopt a staying low approach, sending just a few MFA requests per day over a period of several weeks, while others prefer aggressive MFA spamming with dozens of notifications per minute. The former method aims to condition the target to see authentication requests as routine, making them less likely to inspect each notification carefully.
The social engineering enhancement phase separates the less skilled attackers from the professional cybercrime organizations. Advanced threat actors understand that technology alone rarely succeeds and that human manipulation is the key differentiator.
During advanced MFA bombing campaigns, the victims may also receive phone calls from individuals claiming to be tech support, security team members, or even executives within their own organization. These callers are typically well-prepared with information about the target's company, colleagues, and current projects gathered from social media, company websites, and previous reconnaissance activities. They create a sense of artificial urgency by cooking up fake security incidents or system maintenance requirements that supposedly require immediate authentication approval.
The access exploitation phase begins the moment a victim approves a bogus authentication request. Professional attackers know they have a limited window of opportunity before the breach might be discovered.
Within minutes of gaining access, they may execute a predetermined checklist of activities. Password changes lock out the legitimate user and buy additional time for the attackers. They may add their own devices to the account to ensure persistent access even if the original compromise method is discovered. Installing remote access tools or backdoor Trojan horses provides alternative entry points to the network. Gathering bonus credentials from password managers, saved browser passwords, or email accounts enables lateral movement within the organization.
The speed at which this phase gets executed often determines whether the attack results in a minor security incident or a major data breach.
Security professionals often design systems assuming users will make rational, careful decisions about every authentication request. However, decades of behavioral research reveal that human decision-making becomes increasingly flawed under pressure, repetition, and time constraints—exactly the conditions MFA bombing creates.
The human brain was not designed to maintain constant vigilance against repetitive, seemingly legitimate requests. When users receive multiple MFA prompts throughout a normal day, several psychological factors begin working against their security awareness.
Automation bias causes people to develop unconscious patterns around familiar interfaces. After months of legitimately approving MFA requests during normal work activities, the action becomes so automatic that users can approve notifications without consciously processing the context or timing. This muscle memory effect becomes particularly dangerous when attackers time their bombing campaigns to coincide with periods when users typically authenticate, for example, the start of the workday on Monday morning.
Trust bias creates another psychological vulnerability that attackers manipulate. MFA prompts originate from trusted systems that users interact with daily as part of their legitimate work activities. Unlike obviously suspicious phishing emails with poor grammar or unfamiliar sender addresses, authentication notifications appear completely legitimate because they are generated by real security systems.
Users have been trained to trust these notifications and respond promptly to maintain productivity and system access. This learned trust becomes a weapon when attackers can trigger the same trusted notifications through illegitimate means.
The "just make it stop" mentality represents perhaps the most dangerous psychological response to MFA bombing. Security professionals often underestimate the genuine disruption these attacks could cause to daily workflows and personal device usage.
Research in behavioral security has shown that high-pressure scenarios—like a remote employee preparing for a meeting while being bombarded with MFA prompts—create a powerful incentive to approve notifications just to restore normalcy. Users begin viewing the notifications as technical problems to solve rather than potential security threats to evaluate.
In September 2022, Uber fell victim to one of the most publicized MFA bombing attacks. The Lapsus$ group had somehow gotten hold of an Uber contractor's login credentials and decided to test just how far social engineering could take them.
The attack was surprisingly straightforward. Instead of trying to crack Uber's security systems, the attackers simply started flooding the contractor's phone with MFA requests. Every few minutes, another notification would pop up asking for authentication approval.
The contractor initially did the right thing by denying one request after the other. But the notifications kept coming. During work hours; during dinner, late at night. The phone wouldn't stop buzzing.
Then came the phone call. Someone claiming to be from Uber's IT department explained they were running system maintenance and needed the contractor to approve the authentication requests. The caller sounded professional, knew internal terminology, and created a sense of urgency around completing the maintenance window.
Tired from the constant interruptions and convinced by the caller's authority, the contractor finally tapped on the Approve button. That single tap gave Lapsus$ everything they needed.
Within hours, the group had accessed Uber's internal systems and was posting messages in company Slack channels, essentially announcing their successful breach to the entire organization.
What makes this case particularly telling is how it didn't require any sophisticated hacking. No zero-day exploits, no advanced malware—just persistence, convincing acting, and an understanding of human psychology under pressure.
Prevention of MFA bombing attacks requires a two-pronged approach that covers both the technical and human factors that make these attacks successful. Organizations require strategies that go beyond simply implementing MFA and calling it a day.
Implement context-aware authentication systems that analyze geographic location consistency, device fingerprinting, time-based access patterns, and network origin analysis in real time. These systems flag authentication requests from unusual locations, unfamiliar devices, or suspicious timing patterns. When anomalies are detected, the system automatically escalates security requirements by demanding additional verification methods or requiring manual IT approval for high-risk scenarios.
Organizations can configure systems to limit authentication attempts per user per a given timeframe (such as three attempts per five-minute window). Implement exponential back-off that increases delays between attempts after each failed request. For example, start at 30 seconds and extend to hours for persistent suspicious activity. Include account quarantine features that automatically disable suspicious accounts while alerting security teams and providing clear restoration procedures.
Create specialized guides to help security teams distinguish between legitimate authentication issues and bombing campaigns. Make sure to include detection criteria for multiple rapid requests, unusual geographic patterns, and user reports of suspicious calls. Establish secure communication channels and standardized scripts for user contact, plus immediate remediation steps like temporary account disabling, securing password resets, and enhanced monitoring.
Implement real-time monitoring systems that track authentication frequency, geographic anomalies, and user behavior patterns. Establish baseline patterns for users and departments, automatically flagging significant deviations. Set up tiered alert systems that escalate based on threat severity and integrate with security information and event management (SIEM) systems to correlate authentication anomalies with other security events across your organization.
Where feasible, organizations can develop training programs that simulate high-pressure business scenarios where attackers exploit emotional states and time pressure. These programs should teach users to maintain security awareness, provide practical decision-making frameworks that work under pressure, and establish clear escalation procedures.
Industry security experts and research organizations have been warning about the growing risk of MFA bombing attacks. Their findings paint a concerning picture of how these seemingly simple attacks are penetrating even well-protected organizations.
A few years ago, Microsoft's security research team delivered perhaps the most eye-opening wake-up call to the industry when they revealed the large scale of MFA bombing in the wild. Their comprehensive monitoring detected over 382,000 MFA fatigue attacks during just a twelve-month time frame.
But the findings get even more alarming. Microsoft's behavioral analysis uncovered that approximately 1% of users will blindly accept the very first unexpected MFA prompt they receive, without any verification or checking for context. While 1% of the users might sound small, when applied to enterprise-scale user bases, it represents thousands of potential breach entry points.
The research revealed that attackers have become remarkably sophisticated in their timing and approach. Rather than random MFA bombing campaigns, threat actors carefully study their targets' work patterns, identifying optimal attack windows when users are most likely to approve requests without scrutiny (for example, during a busy Monday morning, right before important meetings, or during known system maintenance periods).
According to major cybersecurity industry reports, 2025 will mark a critical turning point in authentication security threats.
Google Cloud's Cybersecurity Forecast 2025 specifically warns that "Threat actors will increasingly use AI for sophisticated phishing, vishing and social engineering attacks," with particular emphasis on techniques designed to bypass MFA.
Trend Micro's Security Trends for 2025 report anticipates that "Malicious actors will go full throttle in mining the potential of AI in making cyber crime easier, faster and deadlier." Their research indicates that AI-powered social engineering will make traditional MFA bombing campaigns significantly more convincing and harder to detect.
Industry analysts are particularly concerned about the emergence of agentic AI, which are autonomous AI systems capable of independently planning and executing tasks—in this case, attacks. Fortinet's Cyberthreat Predictions for 2025 report warns that these AI agents can automate cyber attacks, reconnaissance and exploitation, increasing attack speed and precision while adapting in real time to bypass traditional defenses.
The consensus among industry experts is clear: MFA bombing represents a fundamental shift in attack methodology that requires equally fundamental changes in how organizations approach authentication security and user training. As multiple leading cybersecurity firms have documented, the combination of AI enhancement and human psychology exploitation will make these attacks increasingly difficult to defend against using just the traditional security measures alone.
MFA bombing attacks typically exploit push notification vulnerabilities, but ManageEngine ADSelfService Plus offers several defense mechanisms against these threats. By providing diverse authenticator options beyond traditional push notifications—including FIDO2 security keys, biometric authentication, and TOTP tokens —organizations can reduce their reliance on the notification methods that are targeted by MFA bombing attacks.
The solution's adaptive MFA capabilities help strengthen authentication security by evaluating risk factors during login attempts. ADSelfService Plus also includes account lockout policies that can automatically block users after a configured number of failed authentication attempts, helping to halt MFA bombing campaigns that rely on repeatedly prompting users for approval.
Additionally, ADSelfService Plus supports passwordless authentication methods, which eliminate the initial credential compromise that attackers often need before launching MFA bombing campaigns. Organizations can also leverage the solution's comprehensive authentication logging to maintain visibility into authentication patterns and investigate potential security incidents when they occur.
Attackers typically obtain user credentials through phishing emails, data breaches, credential stuffing attacks, or purchasing them from dark web marketplaces. They can also use social engineering techniques to trick you into revealing your login information directly.
Never approve any MFA request that you didn't initiate yourself. Treat unexpected notifications as potential MFA fraud alerts. If you receive multiple notifications, deny all of them and immediately contact your IT security team. Turn off your device's notifications temporarily if the bombardment continues, and change your password as soon as possible since attackers would likely have your credentials.
Genuine MFA requests should only appear when you're actively trying to log into an account. Check the timing, location, and device information in the notification. If you didn't initiate a logon attempt, or if the request's location or originating device seems suspicious, always deny the request and investigate further.
MFA bombing primarily targets push-based authentication systems that send notifications to your mobile device. Other MFA methods like hardware security keys, biometric authentication, or time-based codes from authenticator apps are much more resistant to bombing attacks.
Yes. MFA is still significantly more secure than using passwords alone. MFA bombing requires attackers to have your credentials already and rely on tricking you into approving requests. The solution isn't to avoid MFA, but to use more secure MFA methods and stay vigilant about unexpected notifications.
Yes, attackers often deliberately target users during off-hours, weekends, or early morning hours when people are more likely to be tired, distracted, or eager to stop the notifications quickly. Some attackers specifically choose these times hoping you'll approve requests just to make them stop.
Act immediately. Change your password right away, log out of all active sessions, contact your IT security team, and monitor your accounts for any suspicious activity. The faster you respond, the less damage attackers can do with their temporary access.