Chapter 2: Certification Acquisition Framework (CAF)
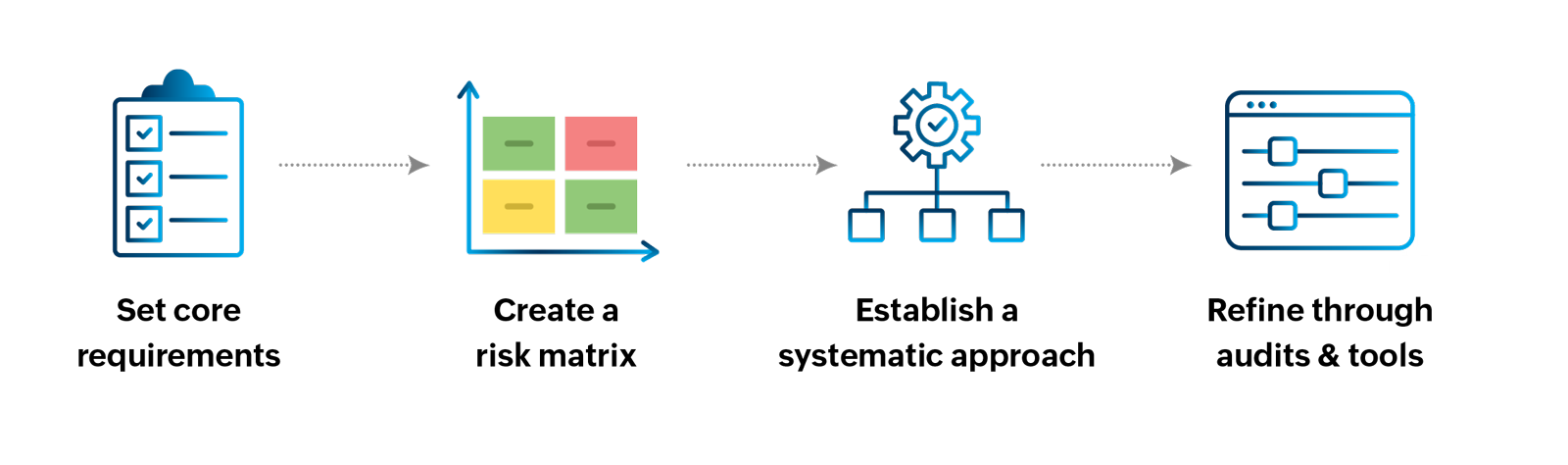
1) Set the core requirements
ISO 27001 clauses 4–10 laid the groundwork for ManageEngine's compliance framework. These clauses enabled us to create a strong baseline, which we could then adapt to meet the requirements of other standards like ISO 9001, SOC 2, and ISO 22301. Let's take a closer look at each clause, the principles behind them, and our approach to enforcing them.
| ISO 27001 Clause | Function |
|---|---|
Clause 4 |
Organization |
Clause 5 |
Leadership |
Clause 6 |
Planning |
Clause 7 |
Support |
Clause 8 |
Operation |
Clause 9 |
Performance Evaluation |
Clause 10 |
Improvement |
Clause 4: Context of the organization
What it covers: Understanding the internal and external issues that can impact the ISMS and defining the scope of the ISMS in relation to the organization's operations.
ManageEngine’s approach:
- Defining scope: Given our diverse product portfolio and global presence, we decided that ISO 27001 standards would be applied organization-wide rather than be product-specific. This broad scope allowed us to create a unified security posture across all operations.
- Internal and external factors: We conducted a thorough analysis of internal factors (e.g., company culture, IT infrastructure) and external factors (e.g., regulatory requirements, market conditions). For instance, we identified that different regions had varying data protection laws, which influenced how we structured our ISMS to meet global compliance needs.
Clause 5: Leadership
What it covers: Leadership's role in establishing and maintaining the ISMS, including setting policies, assigning roles, and demonstrating commitment to security.
ManageEngine’s approach:
- Top management commitment: Our leadership team has been actively involved in the ISMS from the outset. They set the tone by establishing an information security policy that aligned with our business objectives and market expectations.
- Assigning roles: We appointed key roles, including an Information Security Officer (ISO), who was responsible for the overall management of the ISMS. This individual coordinated with various product teams to ensure that security practices were consistently applied across the board. Central teams like Security, Privacy, and Compliance drafted comprehensive information security policies, accessible to all employees via the compliance management tool. Teams were required to acknowledge and adhere to these policies, maintaining documented evidence of acceptance.
Clause 6: Planning
What it covers: Assessing risks and opportunities, setting information security objectives, and planning how to achieve them.
ManageEngine’s approach:
- Risk assessment: A comprehensive risk assessment based on the confidentiality, integrity, and availability (CIA) triad helped us identify potential threats to our information assets. Each team conducted assessments using an internal risk register tool, identifying potential threats across various processes and product features.
- Setting objectives: We established measurable objectives, such as reducing the number of security incidents by 20% annually. These objectives were aligned with our business goals and regularly reviewed for effectiveness.
Clause 7: Support
What it covers: Resources, awareness, communication, and documentation needed to support the ISMS.
ManageEngine’s approach:
- Resource allocation: We ensured that all necessary resources (personnel, technology, and training) were available to maintain the ISMS. For example, we invested in training for our compliance teams to stay updated on emerging threats and new standards. Security and privacy quizzes were administered regularly to enhance awareness across the organization. Leadership ensured participation and tracked progress, reinforcing a culture of continuous improvement. Teams developed a Competency Matrix to outline required skills, which was updated following training sessions. Internal auditor training sessions were also scheduled periodically, and attendance was tracked through our in-house learning platform.
- Documentation: We created a centralized repository for all ISMS-related documentation, including policies, procedures, and audit reports. This repository was critical when we needed to demonstrate compliance during external audits.
Clause 8: Operation
What it covers: Implementation and operation of the processes needed to meet the ISMS objectives, including risk treatment plans.
ManageEngine’s approach:
- Implementing controls: We implemented various controls identified during the planning phase, such as encryption for data at rest and in transit. These controls were regularly monitored and tested to ensure their effectiveness.
- Incident management: We developed a comprehensive incident management process to quickly detect, respond to, and recover from security incidents. This process was crucial for maintaining customer trust, especially in high-risk areas like cloud services.
Clause 9: Performance evaluation
What it covers: Monitoring, measurement, analysis, and evaluation of the ISMS, including internal audits and management reviews.
ManageEngine’s approach:
- Internal audits: We conducted regular internal audits to assess the performance of our ISMS and identify areas for improvement. Teams prepared for audits using compliance management tools that facilitated scheduling, document sharing, and communication. Any identified non-conformities (NCs) were categorized by severity, making it easier to prioritize and resolve issues. These audits were scheduled annually but also conducted on an ad-hoc basis.
- Management reviews: Our top management regularly reviewed ISMS performance metrics, such as the number of incidents detected and resolved. This ensured that our ISMS remained aligned with our strategic goals. The compliance team facilitated these reviews, presenting key performance metrics and audit findings.
Clause 10: Improvement
What it covers: Continuous improvement of the ISMS through corrective actions and ongoing enhancements.
ManageEngine’s approach:
- Corrective action: NCs identified during audits prompted immediate action. Teams worked with the compliance team to implement corrective measures. We maintained a corrective action log to track and resolve issues or gaps identified during audits and reviews.
- Continuous improvement: The compliance team established a feedback loop to improve the ISMS consistently. Inputs from audits, risk assessments, and management reviews helped refine policies and procedures, adapting the ISMS to meet evolving security needs. This proactive approach ensured that we were always ready for new challenges and certifications.
By mastering these ISO 27001 clauses, we created a flexible and scalable compliance framework at ManageEngine. This framework not only supported our immediate certification needs but also allowed us to easily adapt to new standards and regulatory requirements as our business grew.
2) Create a company-wide risk matrix
Risk in information security is the potential for threats to exploit vulnerabilities in an organization’s information assets, leading to negative impacts. These risks are analyzed in terms of impact (potential damage if the risk occurs) and likelihood (probability of the risk occurring).
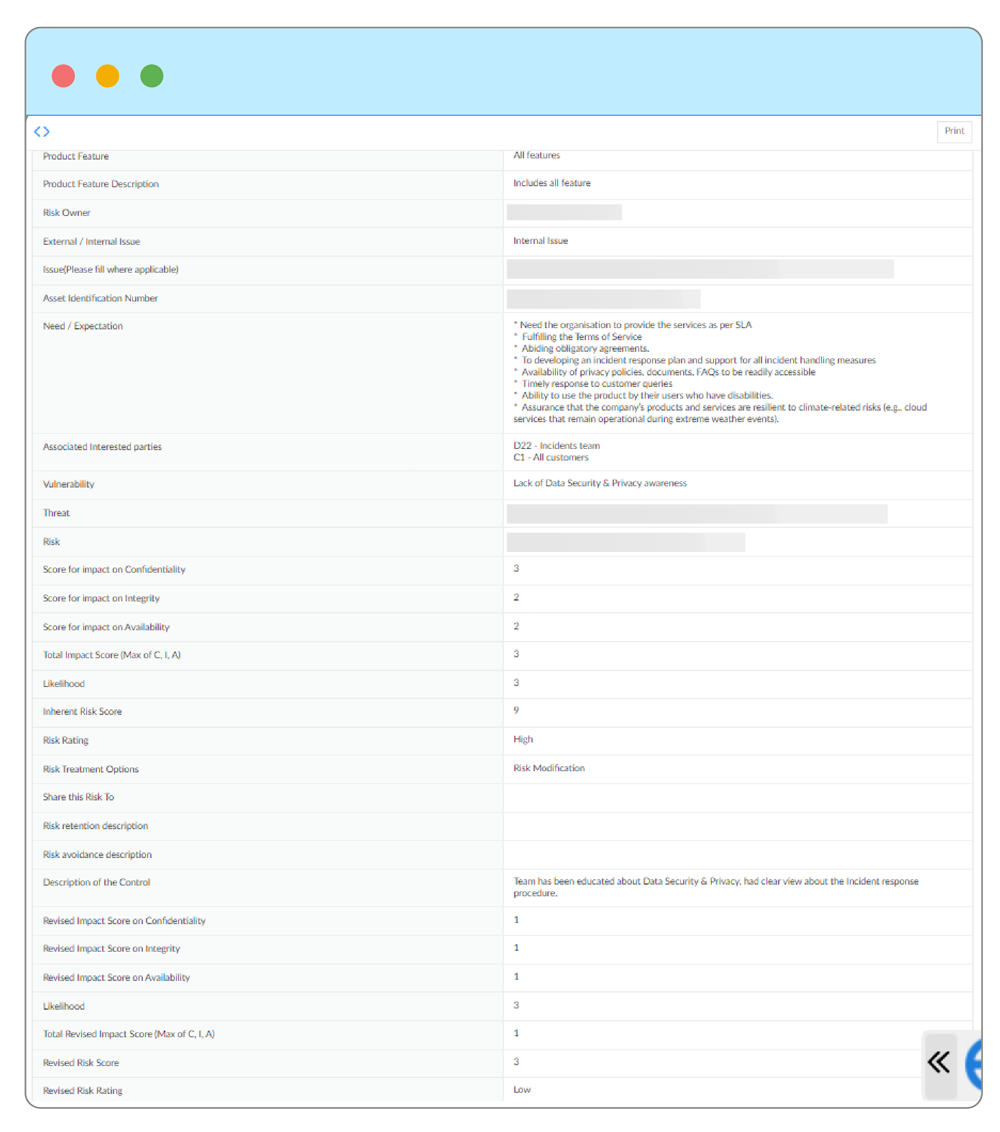
Case study: Addressing security vulnerabilities in Zoho's product development
Identifying and addressing risks is integral to maintaining a secure and compliant environment. For example, during the development of Zoho's customer relationship management tool, a critical feature was assessed for potential vulnerabilities. A security weakness was identified where unauthorized access could lead to email spoofing, threatening confidentiality and integrity. This risk was mapped to relevant interested parties (customers and regulators) and mitigated by implementing controls like encryption and access management.
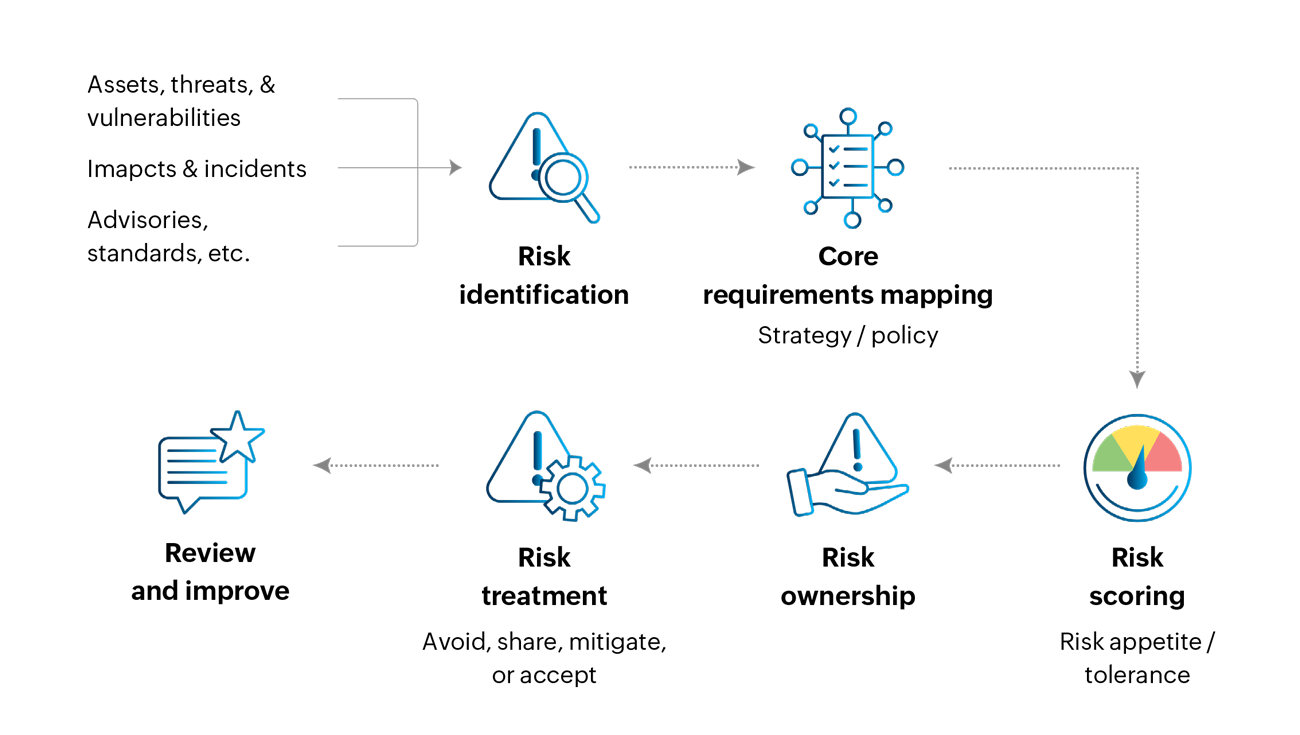
Risk identification
Identifying the risk is the first step and the foundation of our matrix. Risk identification in ISO 27001 involves recognizing potential threats and vulnerabilities that could impact the confidentiality, integrity, and availability of information. This is typically influenced by factors like:
- Threats and vulnerabilities: Direct sources of risk. For instance, a vulnerability in the point-of-sale system in a retail setting could be exploited, leading to data breaches.
- Internal and external issues: Internal issues, like inadequate staff training, and external issues, such as new data privacy regulations, introduce risks.
- Stakeholder obligations: Meeting stakeholder requirements or expectations, like customer data protection, is crucial.
- Assets: Protecting assets, including physical devices and intellectual property, is essential.
- Incidents: Learning from past incidents helps in preventing recurrences.
Core requirements mapping
Align risks with the organization's core requirements and compliance standards. Each risk can be associated with appropriate control measures to mitigate or manage the risk. These controls could include technical measures (e.g., encryption, access controls) or organizational measures (e.g., training, policies). For instance, if the core requirement is data integrity, vulnerabilities must be addressed to maintain data accuracy. Similarly, if customer trust is the focal point, identifying risks related to customer-facing processes helps in building and maintaining trust.
Risk scoring
The next step is to quantify the risk. Teams must assess and score risks by combining impact and likelihood. The placement on the matrix helps visualize which risks need immediate attention and which can be monitored over time.
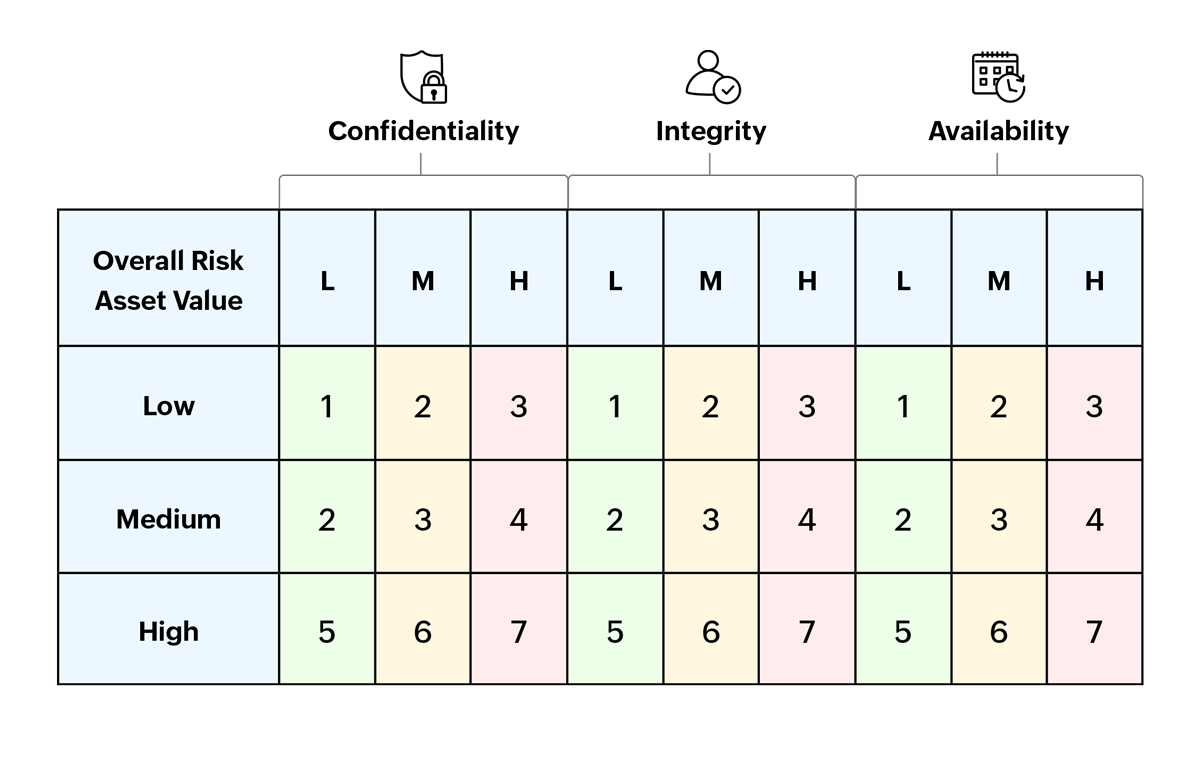
Example: ISO 27001 Control A.8.1.1: Inventory of Assets. This ensures that all assets are accounted for and that high-risk assets are given more focus.
Attributes for ISO Controls
In addition to scoring, consider the following attributes when implementing ISO controls:
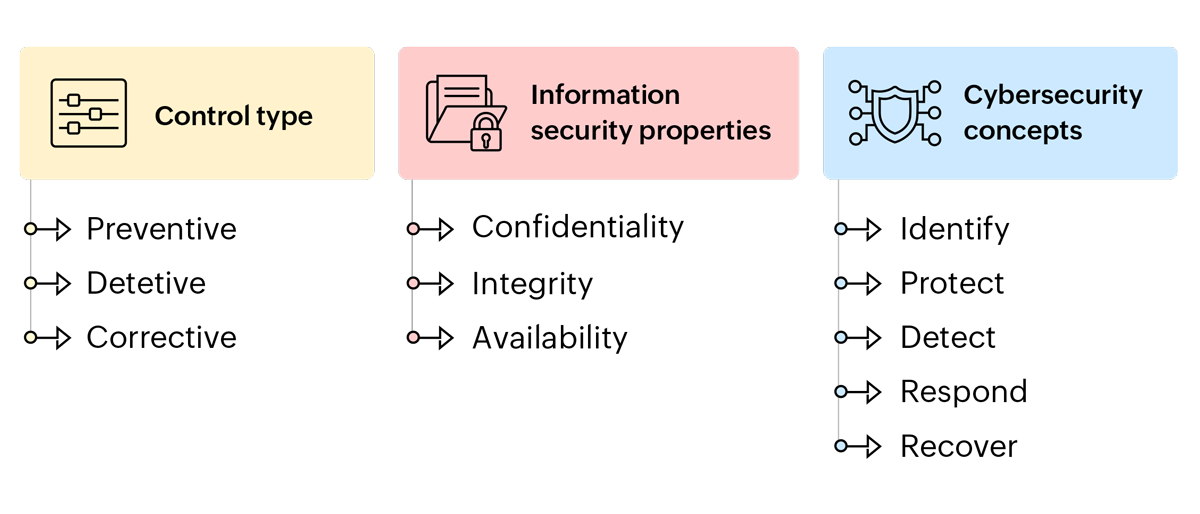
Identifying risk owners
Designate individuals (risk owners) for each risk for better accountability and effective risk management. With clear responsibility for monitoring, mitigating, and managing specific risks, we avoid overlooking key aspects and ensure appropriate resources are allocated. Overall, this leads to timely decision-making, consistent implementation of mitigation strategies, and improved communication across teams.
| Type of risk | Accountability |
|---|---|
Process or activity-based risks |
The risk owner is usually the person accountable for the activity, i.e., process owners or operations managers. These risks are tied to specific operational processes such as data handling, access control, and incident response. The process or operations manager is accountable because they understand the workflows, can implement necessary controls, and ensure processes are followed consistently to minimize risks. |
Product feature-based risks |
The risk owner is the responsible product manager. These risks arise from the specific features or functionalities of our products, such as vulnerabilities in software code or weak encryption protocols. Product managers or technical leads are responsible because they oversee product development, ensuring that security measures are integrated during the design and implementation phases to prevent risks related to product features. |
Combined risks |
The risk owner is typically the person accountable for related activities, like an Information Security Officer (ISO) or risk manager. Combined risks often involve multiple areas of the business, such as a mix of operational, product, and regulatory compliance risks. The ISO or risk manager is accountable for these risks because they have a holistic view of the organization’s security posture, ensuring that all risk types are managed in alignment with standards and that mitigation strategies across different areas are integrated effectively. |
Assign ownership for each risk to ensure accountability
Example: ISO 27001 Control A.18.1.1: Identification of Applicable Legislation and Contractual Requirements. The risk owner for compliance-related risks should be the compliance officer or a member of the legal team.
Risk treatment
Once risks are identified and scored, they must be treated. In the context of a standard like ISO 27001, risk treatment protects assets, maintains compliance, and supports the organization's overall security posture. It ensures a proactive approach to potential vulnerabilities.
Review and improve
Regularly update the risk matrix and engage leadership in the review process. Embed the risk matrix in the organization's ISMS for continuous monitoring and improvement. By aligning these examples and controls with the organization's core requirements, the risk matrix becomes a powerful tool for ensuring compliance, security, and operational continuity.
3) Approach new certification systematically
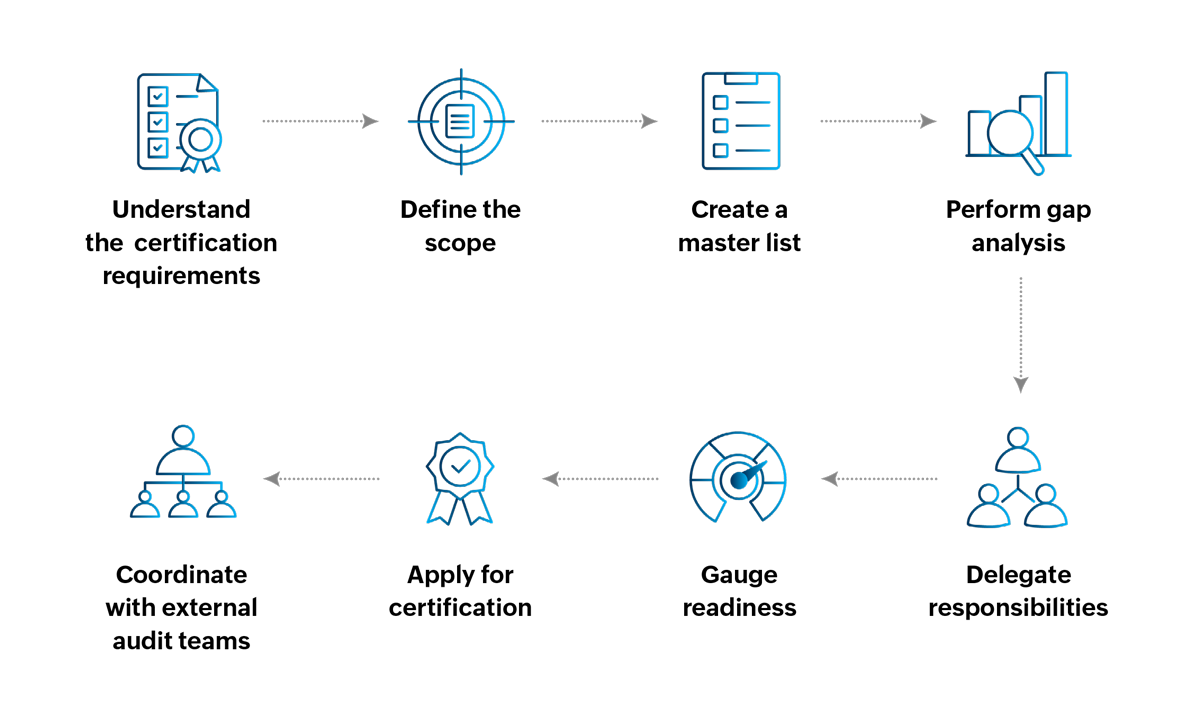
Step 1: Understand the certification requirements
We begin by thoroughly reviewing the specific requirements of the certification the organization is pursuing. By grasping these requirements, we lay the basis for tailoring our compliance efforts. Let's say, for ISO 27001, one must be familiar with Clauses 4-10, which are essential for setting up a robust information security management system (ISMS). For SOC 2, review the specific control activities related to the service type, such as access controls or incident response procedures.
Step 2: Define the scope
Decide whether to pursue organization-wide or product-specific certification based on the company's needs. The choice impacts how the certification is applied, the level of effort required, and the benefits it brings to the organization.
Organization-wide certification includes all departments, products, processes, and functions. It is ideal for organizations aiming to demonstrate a holistic security posture. It is also resource-intensive (time, personnel, financial), but offers broad compliance benefits (e.g., ISO 27001).
Product-specific certification focuses on a specific product or service within the organization. It is more suitable for companies that need to demonstrate compliance for a particular offering but may not require the same level of scrutiny for the entire organization. It is not as resource-intensive and is more focused in comparison to organization-wide certifications (e.g., ISO 9001).
Step 3: Create a master list
Develop a master list of requirements from the certification standards and map them to the organization’s operations. This list will act as a comprehensive guide to ensure all relevant requirements are addressed.
Example: For ISO 27001, this list might include requirements for risk assessment, control implementation, and documentation. For SOC 2, it will involve specific control activities like multi-factor authentication (MFA) for access management.
Step 4: Perform gap analysis
Conduct a gap analysis, i.e., compare the current state of an organization, process, or system against a desired standard or goal. This could be through documentation review, stakeholder interviews, or control evaluations. A thorough analysis will highlight areas where organizations fall short and need to make improvements or implement new controls. Teams can then summarize their findings in a report with an actionable roadmap — a lifesaver for audit season.
Example: An organization does not have a formal access control policy defining how employees, contractors, and third-party users should access systems and data. Currently, access is granted ad hoc without a standardized process, increasing the risk of unauthorized access to sensitive information.
Consequences:
- Lack of accountability for who has access to critical systems and data.
- Increased risk of data breaches or accidental data exposure.
- Non-compliance with ISO 27001 Annex A.9 (Access Control), which requires organizations to establish access policies and procedures.
Proposed solutions:
- Develop and document an access control policy that includes rules for user authentication, authorization, and periodic access reviews.
- Implement role-based access controls (RBAC) to ensure users only have access to information relevant to their job responsibilities.
- Enforce MFA for all critical systems.
- Conduct regular access audits to identify and remove unused or unnecessary access privileges.
Step 5: Delegate responsibilities
Assign specific tasks and responsibilities to teams based on the findings of the gap analysis. Keep stakeholders informed about the certification process and any changes required. Effective communication is crucial for ensuring everyone understands their role and the importance of compliance. Regular updates through workshops or town hall sessions will help keep the teams aligned and motivated.
Example: Assign the IT team the task of implementing new security controls identified in the SOC 2 gap analysis. For ISO 27001, allocate the responsibility of updating the risk register to the compliance team.
Step 6: Gauge readiness
Perform internal audits or mock assessments to evaluate the organization's readiness for the official certification audit. This helps identify any remaining issues and ensures the company is well prepared.
Audits can be planned as:
- Initial audit: A comprehensive internal audit early in the implementation process to assess the current state of compliance.
- Ongoing audit: A regular audit (e.g., monthly or quarterly) throughout the preparation phase to track progress, validate the effectiveness of implemented controls, and ensure consistent alignment with the standard.
- Pre-certification audit: A final, full-scope internal audit shortly before the certification audit to confirm the ISMS meets requirements and to address any residual NCs.
Step 7: Apply for certifications
Submit the application for certification once all stakeholders are confident that all requirements have been met. This involves formally applying to certification bodies or auditors and scheduling the necessary assessments. For organizations with robust ISMS practices already in place, the process can take as little as two to three months, but for those starting from scratch or with significant gaps, it may take longer. As challenging as it may seem, a little preparation can go a long way in simplifying the process.
Step 8: Coordinate with external audit teams
Collaborate closely with external auditors throughout the certification process. Zoho Corp. has a designated point of contact to liaise with the external auditors. During the audit, there may be requests for additional evidence, explanations, or access to specific personnel. It is crucial to address these requests promptly to avoid delays. The purpose of an audit is to support our business and streamline operations, so consider it a partnership rather than a test.
4) Refining and improving using tools and internal audits
Effective compliance management requires continuous refinement and adaptation. ManageEngine relies on a system of internal audits and advanced tools to ensure ongoing compliance and improvement. This section explores how we leverage these methods to enhance our security posture and streamline our compliance processes.
Objectives for internal audits
Internal audits are conducted regularly; these audits aren’t simply checking off boxes in a list, but are instead approached as opportunities to identify issues, enhance processes, and make external audits smoother. With the introduction of new standards and periodic changes to existing ones, it is imperative for us to maintain consistent quality management practices. Our past efforts have played a crucial role in expanding and refining our compliance framework. Key achievements include:
- Global expansion: By including more of our global offices—such as those in Brazil and Mexico—in the audit program, we ensured a consistent approach to compliance across all regions, alongside our existing offices in the US, EU, Singapore, and Australia.
- Effective issue management: Introducing a system for categorizing NCs by severity allowed us to prioritize and address compliance issues more efficiently.
- Broader compliance coverage: With 15 new teams added to the compliance scope, internal audits have standardized practices across 260 teams, ensuring a consistent security posture.
As we streamline the audit procedure, we aim to unify quality standards and expand auditing to include ISO 9001 standards for all compliance-scoped teams. We also intend to update our internal processes to automatically categorize NCs, making audits more efficient and accurate.
Scope of audits
Our audit scope encompasses diverse locations and activities to maintain a holistic compliance framework:
- Location: Offices across multiple regions, including India, the US, Europe, Australia, Brazil, Mexico, Singapore, and the UK, are all within the audit scope.
- Activity: All operational, framework, and development teams undergo audits, ensuring that compliance is embedded in every aspect of our operations.
- Standards: We evaluate teams against applicable standards like ISO 27001, 27701, 27017, 27018, 20000, 9001, SOC 2, HIPAA, WCAG, and 21CFR. Standards such as ISO 27001 and 9001 are applied universally, while others are assessed based on team activities.
To ensure smooth and effective audits, we have set specific prerequisites. Teams must maintain up-to-date documentation, including ISMS, PIMS, QMS, and cloud security and privacy checklists, before their audits. They are also required to address and resolve any NCs identified in previous audits. This helps auditors verify compliance quickly and accurately.
Enhancing compliance with Zoho Comply
Zoho Corp. has refined its internal audit process by integrating it with Zoho Comply, a governance, risk, and compliance management tool developed in-house. This tool streamlines the audit workflow and ensures consistency across teams. Here's how:
- Automated scheduling and coordination: Once the compliance coordinator sets the audit time, the tool generates automated event links for teams, reducing manual scheduling efforts.
- Physical and virtual audits: Teams can choose between physical and virtual audits, with each mode supported by Zoho Comply, allowing for flexibility based on the team’s preferences. This approach is key for global consistency. The integration of global teams under the same compliance framework ensured that our security standards remained consistent, regardless of location.
- Centralized management and reporting: Compliance coordinators can easily manage audit slots and monitor team readiness through a centralized system. This ensures all teams are aware of their responsibilities, audit timelines, and any necessary preparations.
- Automated questionnaires: We have integrated questionnaires across various compliance standards (ISO 27001, 27701, 27017, 27018). This allows teams to respond to pre-audit questions ahead of time.
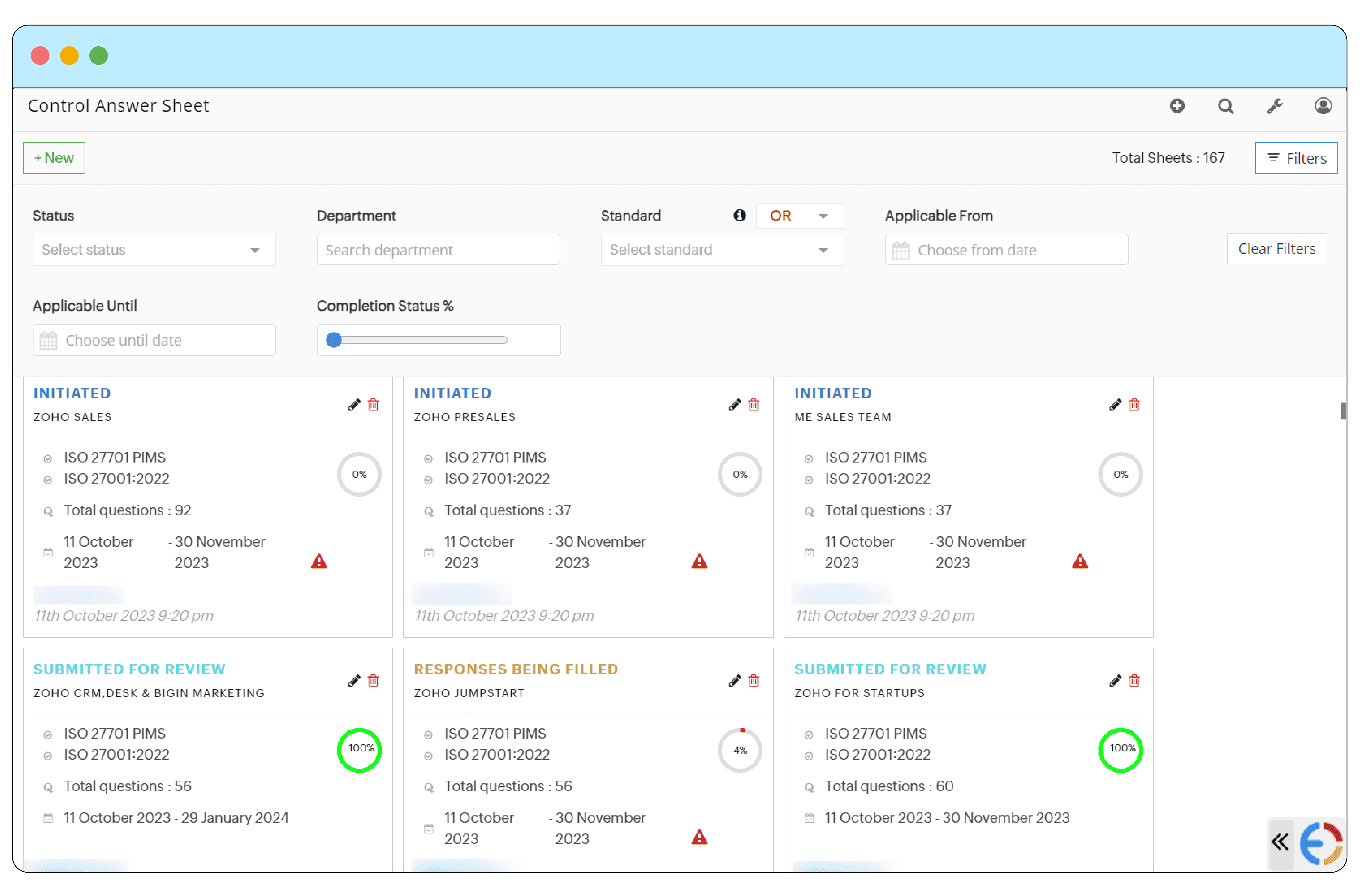
In addition to internal audit management, we have also developed a vendor risk management module within the application to streamline vendor evaluations. This module enhances how we manage third-party risks, ensuring vendors meet our security, privacy, and compliance standards.
- Integrated vendor risk assessment: Teams can initiate vendor evaluations through the app, where vendors respond to assessments directly via a client portal. This eliminates the need for traditional, manual methods like spreadsheets and emails, providing a more efficient, trackable, and secure process.
- Risk identification and resolution: Any risks identified during vendor assessments are highlighted and managed through the tool, enabling teams to work closely with vendors to address issues before proceeding with partnerships.
Through our continuous investment in tools like Zoho Comply and our strategic internal audits, ManageEngine has built a dynamic compliance framework that adapts to new standards and regulations, ensuring we maintain a world-class security posture.