Securing remote access with Zero Trust principles
Use case 1: Guest users visiting ManageEngine
In a scenario where we have visitors on-premises who are accessing our resources, they must install the 0Agent. This can be done by the sysadmin, who also terminates sessions and blocks users and devices that do not comply with our policies. However, if a guest needs to access their own organization's intranet, they have to install the 0Proxy server.
Use case 2: Restricting access to high-value enterprise applications
Zorro is our Data Center Operations team. It handles all the procedures involved in maintaining our data centers, improving their performance, and mitigating potential threats. One of its key responsibilities is to perform maintenance activities on app servers, such as updating firewall configurations and patching.
For a systems analyst from Zorro to access the server, these are the steps they usually follow:
- Step 1: Connect to the VPN.
- Step 2: Log in via our privileged access management tool.
- Step 3: Connect to the application server.
- Step 4: Carry out upgrades.
Ever since we implemented 0Trust, our systems analysts have found it easier to access the app server. They can connect directly to our privileged access management tool and carry out the upgrades.
Use case 3: Accessing development tools
Development tools have far more requirements than other tools. A development lead has to review and test different features built by their team. These features are hosted in the local distributed server, so they cannot access it via Wi-Fi alone.
Right now, team leads have to connect to the VPN to access the local builds. This often impacts connectivity speed because all of the access is tunneled through the VPN. Sometimes, it requires multiple logins after the VPN session times out. After implementing Zero Trust, they will be able to directly connect to the tools without needing to log in to the VPN every time.
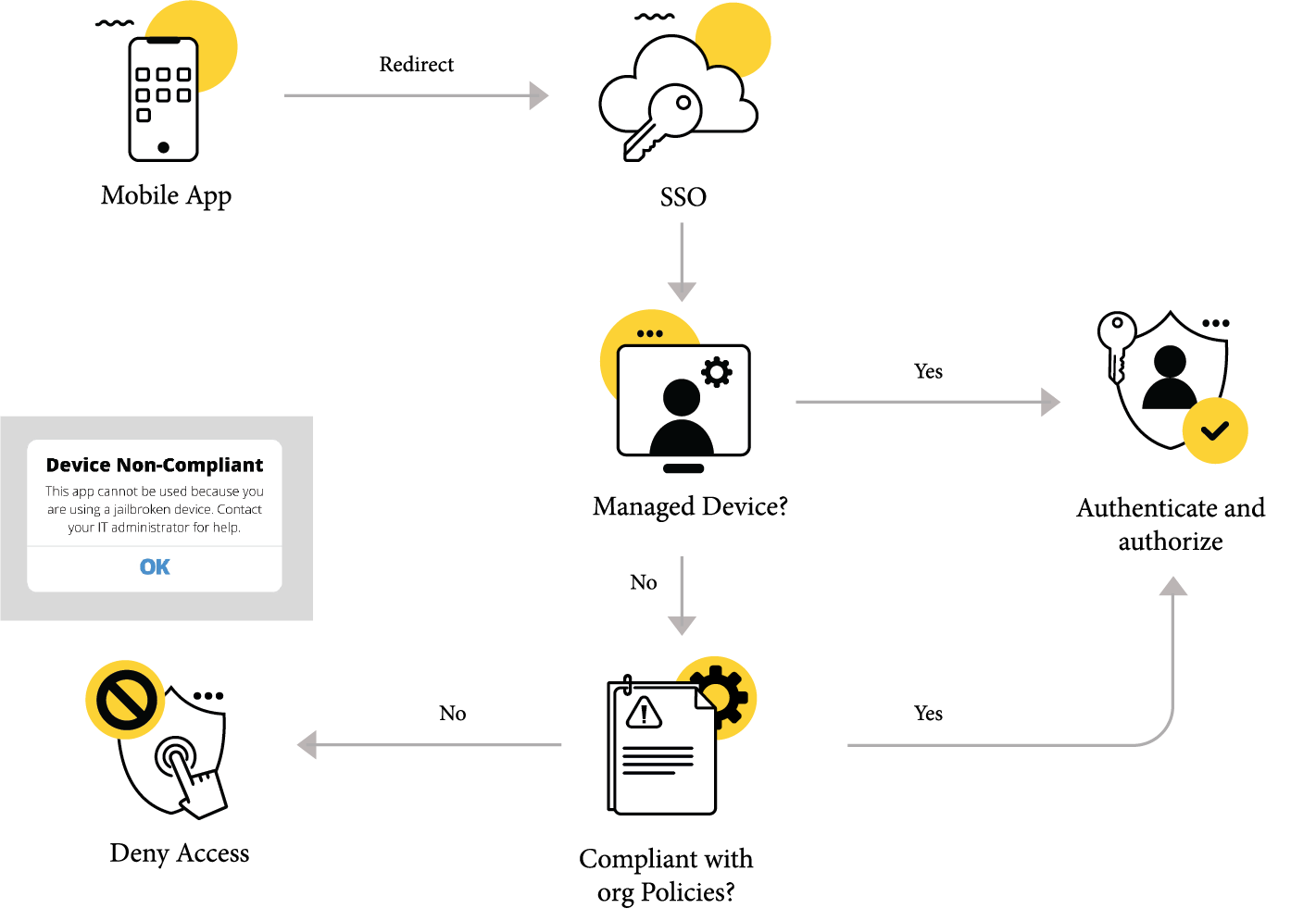
Use case 4: Access from a non-compliant device
Imagine that a member of the administrative staff is trying to log in to a corporate application from their personal mobile device, which is jailbroken. By integrating a Zero Trust system with an IAM tool, you can verify user identity and detect anomalies, if any. An endpoint management tool verifies device identity.
Attributes |
User Info |
Risk Posture |
Actions to Improve Security |
||
Evaluate Dynamic User Attributes |
User |
User ID |
Managed |
Low |
N/A |
Behavior |
No Anamalies |
||||
-Time |
Usual |
||||
-Locations |
Usual |
||||
-Frequency |
Usual |
||||
Device |
Device ID |
Unmanaged |
High |
The Device is Non-compliant, So Deny Access |
|
Device Status |
High Risk |
||||
Network |
Network ID |
Unmanaged |
Medium |
||
Status |
Secured |
||||
Evaluate Enterprise Resource Attributes |
Application |
App ID |
Managed |
Low |
|
Status |
Secured |
||||
App Access |
Authorized (temp) |
||||
Data |
Data Type |
Secured |
Medium |
N/A |
|
Data Access |
Authorized |
||||
Overall |
High |
Deny Access |
|||
In this case, the device is not managed and violates the organization's policies, so access is denied.
Use case 5: Malware-infected employee devices
In the event of an employee's system being infected by malware, the objective is to isolate the system quickly and stop all the user's active sessions. Usually, a systems security engineer would have to use our MDM tool to initiate actions to cut off access to resources, which takes time.
With 0Trust, we can avoid that situation entirely. An agent is constantly monitoring the security posture of each device. When the session score falls below the required number, it is terminated immediately. If there are other ongoing sessions, they can also be terminated regardless of trust score. This action is carried out from the 0Trust management dashboard by a systems engineer.
Use case 6: Customized policies for different teams
Product teams consist of members with different roles and varying requirements. Some members need access to servers or databases, while others need access to local or production builds. Resources are often hosted on different internal networks. Here, we need to enforce one of the cornerstones of Zero Trust: least privilege. Employees need minimal access to specific resources based on their roles.
Without 0Trust, product owners would have to configure access permissions individually. This might work for small teams but not for an enterprise with hundreds of members on a product team.
With 0Trust, product owners can create a policy group for each team in the central 0Trust panel and distribute each configuration. While this capability is not available in our system now, it is on our roadmap, and we hope to implement it soon.