The way we protect data has changed. In the cyber realm, there is a constant state of war fought between cybersecurity and cybercrime. Now, identities are transforming into the primary layer of security while at the other end, cyberthreats are growing in complexity and sophistication. In other words, identities are in the forefront and we need to make sure that we are doing everything in our power to protect them.
The volatile aspect of this perennial battle between cybersecurity and cybercrime is that you can never truly know who's winning until a newly developed and deployed weapon sets a clear distinctive superiority between the two sides. In the current state of this battle, a relatively new weapon has made its way into our arsenal: identity threat detection and response (ITDR).
According to the press release titled Gartner Identifies Top Security and Risk Management Trends for 2022 Gartner® introduced the term ITDR to describe the collection of tools and best practices to defend identity systems. Gartner Research Vice President Peter Firstbrook stated, "Organizations have spent considerable effort improving IAM capabilities, but much of it has been focused on technology to improve user authentication, which actually increases the attack surface for a foundational part of the cybersecurity infrastructure. ITDR tools can help protect identity systems, detect when they are compromised and enable efficient remediation."
With the arrival of ITDR and advances in data science fundamentals, businesses are now capable of harmonizing ITDR and identity and access management (IAM) within the realm of cybersecurity. But this capability will not be remotely enough if we want to leverage ITDR to the maximum extent. The IAM landscape has gone through an evolutionary shift, and therefore, traditional IAM solutions are no longer optimal.
Businesses need to discover and decipher a newfangled way of approaching IAM. Furthermore, with the slow passing of the fourth industrial revolution and the fifth industrial revolution looming over the world, organizations need to reiterate IAM to enable their business controls to keep up with the granular shift towards identity-driven and model-driven security. As an industry, we have to be willing to change our perspective on the cyberthreat and cybersecurity landscapes to achieve and maintain a pace equal to prevalent conceptual and theoretical identity-based frameworks and technologies.
Before we can dive into the practicable and functional mechanics of ITDR, we need to grasp how IAM has changed, what the causes of the change are, and what driving factors are in play towards a greater transformation.
The threat faced by identity and access is not new. They were under threat before the COVID-19 pandemic and even more so after. But there was another major transition experienced by almost every industry in the world, primarily owing to the pandemic, which was the shift from on-premises to cloud. The cloud is a place where the keys to the kingdom—and the keys to the fort protecting the kingdom—are the same: kingdom being the analog for organizational assets and fort being the analog for identity-based security layers of those assets.
Unsurprisingly, cybercriminals jumped on the opportunity to attack identities almost as soon as the rapid shift to remote work and the cloud began, and corroborating that fact is Verizon's Data Breach Investigations Report for 2023, which revealed that 61% of breaches involved credentials. As a response, fields of IAM like identity governance and administration (IGA), privileged access management (PAM), cloud infrastructure entitlements management (CIEM) and tools of authentication like multi-factor authentication (MFA) and single sign-on (SSO) are thriving, as they enable effective management of identities and thereby decrease the risk of credential theft.
While these fields have undergone considerable developments in the past two years, they are no longer considered state-of-the-art or even relatively modern solutions.
In the past, when it came to IAM, the focus was on security. According to Gartner "Sophisticated threat actors are actively targeting identity and access management (IAM) infrastructure, and credential misuse is now a primary attack vector." Moreover, Peter Firstbrook, VP Analyst at Gartner, had also stated, "Organizations have spent considerable effort improving IAM capabilities, but much of it has been focused on technology to improve user authentication, which actually increases the attack surface for a foundational part of the cybersecurity infrastructure." In simpler words, the infrastructure that we created for secure IAM is being used against us by threat actors.
In such situations, we can use powerful IAM tools, but if they are compromised, then they are susceptible to single point of failure (SPOF), which can have devastating effects. To ensure the reliability of our infrastructure, we should avoid systems that have vulnerabilities leading to SPOFs. Apart from security monitoring, the concept of separation of duties plays a crucial role in maintaining tight control over the security of identity and access. It achieves this by preventing any single individual or group from having full control over the system.
Overall, what we need is better infrastructure security for our systems to operate seamlessly. And that is what ITDR offers.
ITDR is one of the most significant elements of IAM. It detects and responds to identity-related threats, and it has been further emphasized by Gartner as one of the top security and risk management trends for 2022 and one of the top security trends of 2023. What's more is that the rise in identity-related threats and other types of data breaches have made industries realize that in the current state of security, ITDR is as crucial as it gets when it comes to the overall security strategy of an organization.
ITDR is a 360-degree process that involves ceaseless and real-time monitoring of all users' activities. The process involves pattern identification of unsuccessful login attempts, detection of access from odd or uncustomary locations, and identification of changes in the permissions of users. Once the process has been carried out and the threat has been detected and identified, a response phase is initiated, which dictates the appropriate action for risk mitigation in accordance to the type of threat.
The main advantage here is that the swift detection and identification of threats eventually results in a swift response, recovery, and remediation. This process of ITDR diminishes the level of damage a threat may have caused—plus, remediation capabilities block additional potential breaches that could've caused serious damage.
From a different beneficial perspective, ITDR also aids with achieving compliance with certain laws such as HIPAA and the PCI DSS. With compliance laws getting stricter and more rigid every year, solutions and processes that can help with getting compliant are truly an indispensable asset.
ITDR also works with infrastructure security. As identities are also fundamental to business, organizations’ reliance on their identity infrastructure to enable collaboration, remote work, and customer access to services has transformed identity systems into prime targets for threat actors, with credential misuse being the most popular path to security breaches in 2021.
There is an active Initial Access Broker (IAB) marketplace for stolen credentials. There are well-known attacks against MFA. Currently, advanced attackers are focusing on targeting the infrastructure of IAM itself. Refer the below image to understand how ITDR synergizes with infrastructure security.
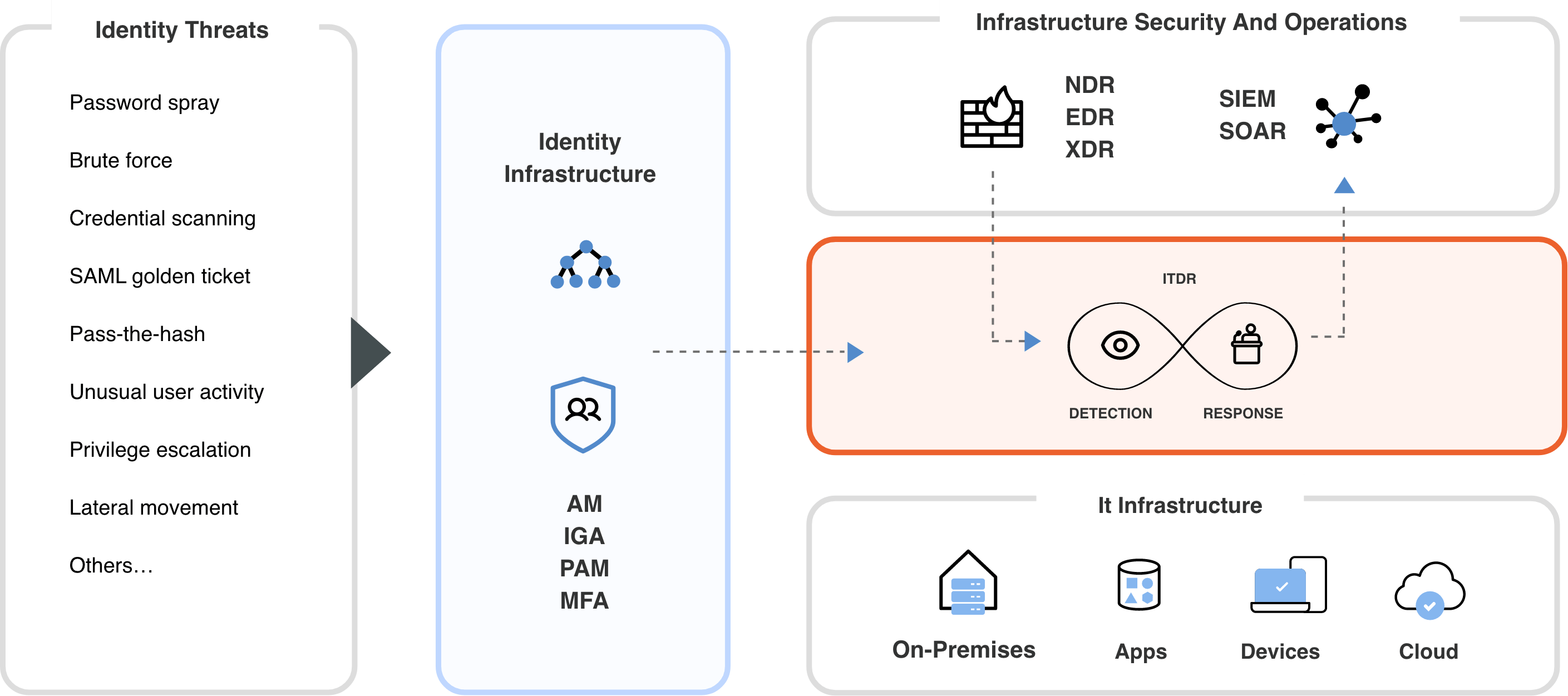
The problem is that as more and more IoT devices are used to connect to the internet, the total volume of data grows simultaneously. Subsequently, since there are more devices and more data, the probability of cybercrime or cyberattacks goes up as well. This implies that to some extent, cyberattacks are directly proportional to the number of devices connected to the internet and/or the volume of available data. That being the case, it is highly likely that ITDR will play an even more significant role in the future, and organizations will need to follow through with futuristic ITDR advancements while also analyzing the accelerating threat landscape.
The current threat landscape is volatile, as it is experiencing a continuous discovery of change. In recent years, there has been a surge in phishing, data breaches, leaks, socially engineered campaigns, attacks on supply chains, and golden ticket attacks. With every passing day, the number of digital identities is increasing exponentially, and thus, sensitive data protected by identity security tools are in the crosshairs of threat actors.
Let's briefly discuss two cases from last year. During the early months of 2022, the U.S. Department of Labor was the victim of a new, highly sophisticated phishing campaign, which was, according to what was reported, going on for many months. The purpose of the phishing attack was to steal Microsoft 365 credentials by requesting unsuspecting recipients via emails, to submit bids. A network of more than ten phishing sites impersonating the government agency were used to carry out this criminal campaign.
The degree of impersonation was sufficiently accurate and the composition of the spoofed pages were persuasive, well made, and seemingly dependable. Furthermore, the email content was error-free, which otherwise could have hinted to recipients that something was wrong.
The next case involves the multinational fintech company PayPal. At the end of 2022, PayPal informed its users that their accounts and personal information had been compromised through a credential stuffing attack. In this method of attack, bots are utilized by threat actors to pair enormous directories of usernames and passwords with each other and are subsequently stuffed into the login portal. Impacting approximately 35,000 account holders, threat actors gained visibility and access to their complete names, dates of birth, email addresses, Social Security numbers, and tax identification numbers.
There was a sizable amount of identity-based attacks in 2022. In fact, they accounted for a considerable chunk of security incidents that were reported. A surge in digital identities and the work-from-home trend continues to expand the attack surface further as more and more cyberattacks target identities.
There is no better way to scrutinize the identity threat landscape than the inference from actual statistics. Reported in the Identity Defined Security Alliance's (IDSA's) 2022 Trends in Security Digital Identities, the following findings were highlighted:
The key implication of these statistics is that the focus on identities is accelerating, from both a cybersecurity and a cybercrime perspective. Now we need to understand what's driving the acceleration. It can be ascribed to two key factors:
Rise in the use of third-party technology and services, cloud-based applications, and Internet of Things (IoT) devices
The increasing adoption of third-party technology and services, as well as the proliferation of internet of things (IoT) connections and cloud-based applications, is resulting in a rise in the number of digital identities for both humans and machines. With each identity representing a potential vulnerability, the sheer volume of identities means that some are likely to be inadequately protected or monitored, providing an attractive entry point for attackers seeking to exploit these weaknesses.
Complex extension and security of work perimeter
Owing to the COVID-19 pandemic and work-from-home trend, the perimeters of work are no longer just on-premises; industries as a whole had to adopt to these two causal factors as an inevitable reality and extend the perimeters far beyond on-premises offices or even smaller off-site locations. Incorporating the new reality in their infrastructure via policies (for example, work-from-home policies) has allowed for a robust and convenient system of workflow management, as it even enables third-party service providers, vendors, contractors, and partners to access network resources remotely whenever they need to, but it has also increased the complexity when it comes to securing those perimeters or working spaces.
Digital identities are now essential to function in our daily lives, for both humans and machines. However, these identities are vulnerable to attack, resulting in a significant digital identity crisis that impacts everyone. This is a serious problem that needs urgent attention. The following are some of the prominent challenges faced by businesses, when it comes to the security of digital identities.
Insufficient investment in identity management systems
Although the adoption of cloud-based identity architecture is growing, small to medium-sized businesses are expressing a disinclination to it's adoption, the primary causal factors being financial constraints, distress over delays with onboarding, and absence of change management undertakings.
Identity-responsibility fragmentation
Executive leaders, multiple IT teams, human resources (HR), and sales typically share the responsibilities of identity management and security. This fragments its management and leads to problems like a divided workforce and lack of synergy between the teams managing it.
Varying data privacy regulations and controls
Every now and then, data privacy regulatory laws are amended, additional stipulations are added, and the goal posts are shifted by the regulatory entities. This complicates the management of digital identities, as identities and data privacy are closely linked with each other and tend to overlap in most situations. So it falls upon organizational leaders to guarantee that the data associated with digital identities adhere to regulatory obligations, as mandated by laws such as the European Union's GDPR, ISO/IEC 27701:2019, the NIST Privacy. Framework, and the Personal Information Protection and Electronic Documents Act (PIPEDA).
The 2023 Trends in Securing Digital Identities report by the Identity Defined Security Alliance (IDSA) revealed that 90% of organizations encountered an identity-related breach in the past year, marking a 7.1% increase from the previous year's 84%. Notably, 68% of these organizations that experienced identity breaches also suffered direct business consequences, with recovery costs being the most substantial impact.
Identity-based attacks are not only rising, but they are expanding. Active Directory (AD) is a popular attack vector and, as a response, we need to recognize the importance of adopting solutions that can protect AD credentials as well. Based on analyst research, a significant majority of security breaches involve the compromise of credential data. This suggests an ongoing, persistent effort by attackers to obtain valid credentials and leverage them to move stealthily within networks without detection. Plus, the number of ransomware breaches is also increasing as attack tactics, such as Ransomware 2.0, are further enabled owing to rising cases of credential misuse.
Credentials stolen via phishing or purchased on the dark web are leveraged by most ransomware attacks as the beginning of their offensive campaign. And subsequently, to elevate privileges and carry out a privileged credentials dump, attackers utilize a large spectrum of tools like Mimikatz. The most common identity technique used in attacks is the theft of credentials from system memory.
On the one hand, IAM systems inherently contrive the principle of least privilege, but on the other hand, once a user is authenticated, the systems are aimed towards minimizing friction. These two goals of IAM systems are well directed, but at the same time, they are divergent. The consequence of this divergence of goals is the difficulty in detecting when user credentials are compromised by a threat actor, which in turn has caused account takeovers (ATO) attacks to become a top attack vector.
The dubious notion in this case is that we believed that the deployment of PAM, MFA, and other various IAM solutions, to a great extent, would address the type of threat discussed above. But according to Illusive's research, one in six enterprise endpoints have identity risks that are exploitable.
Furthermore, ransomware is not the only technique used by attackers. Gaining access to account credentials and leveraging open source tools of attack allows cybercriminals to compromise identities in a way that makes it easy for them to conceal their crime while quickly traversing through all the attack stages.
Therefore, the detection of such nuanced techniques of attacks can be a huge advantage for organizations. So how can ITDR can help with this? ITDR can study and identify behavior patterns, check for login attempts from unusual or suspicious locations, and even enable real-time monitoring capabilities. ITDR can be dynamic and formulated according to a business's organizational structure. Without further ado, let's dive into the mechanics of ITDR.
There are a few core features of ITDR, around which all it's capabilities revolve, namely detection of credential theft and misuse of privileges, AD attacks, and creation of attack paths due to risky entitlements. We need to realize that ITDR is different in comparison to the contemporary tools of identity protection like IAM, PAM, or IGA, which are directed towards secure authorization and authentication.
ITDR solutions are directed towards protecting identities, entitlements, and their management systems. They also ensure that the right resources are accessible by the right people. What's more, ITDR solutions allow and provide transparency in identifying misuse of credentials, exposures due to entitlements, and escalation activities of privileges or privileged accounts, which can include from endpoints, multi-cloud infrastructures, and AD.
ITDR solutions have similar capabilities to endpoint detection and response (EDR), but the unique aspect of ITDR is that it focuses on multiple things. For example, an EDR solution seeks and monitors the endpoints for attacks, and then analyzes the data it collects while an ITDR solution seeks identity-targeted attacks. Another key difference in operations is that you will need to provide EDR with a response plan of action if it is to stop the process of attack, isolate the system, or help with the investigation.
On the other hand, ITDR will add a defensive layer as soon as it detects an attack. The defensive layer will redirect the attacker to a fake network environment comprised of fake data, essentially acting as a decoy. Additionally, when an identity-based attack occurs, an ITDR solution is capable of completely isolating the breached system from the main network, which limits the attack's interaction to the fake network environment.
While there are clear functional differences between EDR and ITDR solutions, both gather forensic data and collect telemetry on the operative processes utilized by the attackers while the attack is taking place. A comparative advantage of ITDR is that it provides great exposure, visibility, and transparency, as some ITDR solutions are capable of identity attack surface management as well. Greater transparency is crucial to identity management, as enterprises will be able to measure the degree of risk posed due to exposures.
Examples of exposure include the following:
ITDR is the collection of best tools and practices; therefore, apart from the best solutions, it is substantial to recognize how exposures (owing to specific practices) are leading to an increasing number of attacks taking advantage of exploiting on-premises systems in order to target the cloud. This can be ascribed to a few underlying factors:
The misuse of machine identities has increased over 1,600% over the last five years. Specifically, an abundance in API insecurities is a major representative of a network's most exposed aspect. Consider this an assault on APIs.
As pointed out earlier, this is a key driving phenomena that is accelerating the adoption of the cloud and the work-from-anywhere trend. From a statistical point of view, 94% of enterprises use cloud services, 92% of businesses have a multi-cloud strategy in place or in the works, and 67% of enterprise infrastructure is now cloud-based."
Owing to the increasing number of digital identities, the number of access rights and permissions has dramatically increased over the last few years. This also leads to policy drift due to multiple configurations for an increasingly high volume of identities that may require specific sets of permissions or conditional access rights.
This issue has emphasized the need to prevent attackers from obtaining excessive rights or the privileges to move across domains and cloud environments. For identities, including users, applications, containers, serverless functions, and other assets, ITDR solutions can effortlessly expand into the cloud, providing comprehensive visibility into entitlements.
Note that many capabilities provided by ITDR solutions are dependent on the provider. Nevertheless, the following are the key features that a solution needs to offer in order to be considered an ITDR solution:
The identity infrastructure, which includes components like access management (AM) tools, certificate authorities (CAa), directory servers, and other various IAM stores and systems, faces what we call identity threats. Identity threats enable cyberattackers to outmaneuver, bypass, or abuse identity networks and systems. Therefore, every cyberattack preparedness plan or phase should have prevention as an elementary component.
It's the responsibility of security and risk management (SRM) leaders to ensure the documentation of every essential aspect of their identity infrastructure and the assessment of appropriate preventive controls in place. The alignment of the security posture (configuration hygiene) of the essential identity infrastructure-related aspects with the organization's inclination towards the level of fathomable risk and business goals will warrant both legacy IAM controls and contemporary ITDR-triangulated controls.
Moreover, SRM leaders should ensure that there is synergy between the legacy and contemporary controls if they seek to minimize the gaps left open for exploitation.
Preventive controls can bolster identity security posture management by mitigating or avoiding:
Systems that can offer foundational preventive controls include the following:
Continuous modernization of IAM infrastructure by evaluating and adopting contemporary and emerging preventive measures like OAuth 2.0 and Continuous Access Evaluation Protocol (CAEP) should be one of the high-priority goals set by SRM leaders. The use of outdated and legacy protocols like Internet Message Access Protocol (IMAP) and Post Office Protocol (POP) can prove to be unsafe and should be avoided.
Now, once the foundational measures of prevention mentioned above are put in place, ITDR can start it's job; which is to behave and perform as secondary and tertiary defensive layers. ITDR is needed based on the grounds of:
Firstly, assuming preventive controls are solely adequate in stopping a cyberattack is a falsification of confidence and thereby should be avoided.
Secondly, cyberattacks should not be underestimated or underplayed, as they can harm the identity infrastructure to unexpected degrees.
On top of that, there is always a possibility that IAM preventive controls can be bypassed or neutralized by identity threats. That's why it is crucial to understand the difference between prevention (identity security posture steps taken before an attack takes place) and detection and response (scanning for attacks and halting the attacks in their progress) as a function of ITDR. Grasping this difference can allow organizations and SRM leaders to focus on identity security as a whole and deploy in-depth defenses. The inherent risk of having a SPOF should also be assessed if the tool being adopted claims to be a single tool offering prevention, detection, and response.
Now that we've covered what ITDR is and how it positions itself within the identity security infrastructure, we need to know what ITDR is not. ITDR is not:
One may assume that the responsibility of ITDR should not be shared, as that would create discrepancies in information sharing and management, but that is not completely true. IAM and infrastructure security teams should be the ones sharing the responsibility of ITDR, and SRM leaders should select someone as a sponsor who is vision-oriented, and can recognize stakeholders and their expectations to lead a synergistic initiative.
There is a difference between AD threat detection and response (AD TDR) and ITDR. Firstly, AD TDR is a part of the ITDR discipline. Secondly, AD TDR's primary objective is to focus on AD threats, while on the other hand, ITDR also performs detection and response pertaining to a wider spectrum of identity threats to other systems and tools of IAM (AM, IGA, PAM and authentication). It's noteworthy that there's a substantial contrast in the adoption rates of AD TDR and ITDR. Approximately one-third of organizations have embraced AD TDR, whereas the adoption of ITDR is still in its early stages.
Although tools like security orchestration, automation, and response (SOAR), security information and event management (SIEM), and extended detection and response (XDR) are crucial to a balanced and symmetrical ITDR strategy, it is necessary to realize that, currently, a huge chunk of vendors or providers in pertinent markets do not offer ITDR capabilities based on contextual user behavior in place of tactics, techniques, and procedures (TTPs). The required depth to counter attacks on identity is lacking in SOC tools, but this does not render them useless—not even close. SOC tools are pivotal in building a cohesive ITDR strategy via integration.
ITDR cannot do everything. To steer clear of misconfigurations, exposures, and vulnerabilities, other preventive controls need to complement ITDR. The focus on prevention addressed by various IAM looks (AM, IGA, PAM, CIEM, and authentication) should not blur your vision towards other kinds of protective layers. Detection and response demands runtime threat intelligence analysis and expansive protective layers that go beyond the preventive features of IAM tools.
To expand the layers of protection:
One of the essential parts of ITDR is IAM. IAM involves setting up policies and procedures to ensure that only authorized users can access sensitive information and systems. One way to achieve this is by implementing two-factor authentication, where users have to provide two forms of identification before accessing sensitive data.
For instance, if you work in a healthcare organization that stores patient information, IAM protocols like role-based access controls and MFA can help prevent unauthorized access to patient data and keep it secure. IAM is a vital component of ITDR, which helps organizations protect their identities and access controls. By adopting strong IAM protocols, regularly monitoring and maintaining access controls, and having a robust password policy, organizations can reduce the risk of data breaches and unauthorized access.
The distinction between ITDR and other identity protection solutions needs to be clear. Primarily centered on authorization and authentication, current identity protection tools such as IAM, IGA, and PAM aim to guarantee that individuals have the appropriate access to the necessary files and applications. However, IAM can become a significant security risk if compromised and used in isolation. This is where ITDR comes in. ITDR is about segregation of functional systems like IAM, IGA and PAM to secure the overall infrastructure and ensure that it works as intended (to avoid SPOF).
The importance of ITDR in the world of Zero Trust, which is a fundamental principle that's embedded in the leading IAM, PAM, and IGA systems out there today, is invaluable. These systems are constructed to validate and grant authorization for each identity request during any session, whether it pertains to a human or a machine-based identity.
As we move towards multi-cloud and container-based infrastructures, ITDR providers are prioritizing least-privileged access by detecting entitlement exposures, identifying privileged escalations that could indicate a breach, and spotting credential misuse before it's too late.
Cyberattackers love to take advantage of the isolated nature of IAM, PAM, and IGA systems. If they can breach one of these systems, they can essentially take over an entire enterprise network. Plus, there's the added challenge of ensuring proper identity orchestration across multiple cloud platforms. Fortunately, ITDR and SIEM providers are working hard to provide solutions for these issues.
CISOs recognize the value of ITDR from a Zero Trust perspective for multiple reasons. Firstly, it can help consolidate tech stacks and reduce the burden of legacy systems and their associated costs of maintenance. Additionally, it plays a role in filling gaps within multi-cloud infrastructure by bolstering trust in additional aspects. This action works towards eliminating any implicit or assumed trust throughout both the infrastructure and technology stacks.
Furthermore, implementing ITDR solutions offers CISOs the chance to advance their Zero Trust strategies without the need to introduce additional applications to address diverse identity-related weaknesses in their network. This is of utmost importance given that cyberattackers have demonstrated their ability to exploit malware to compromise AD configurations, thereby obtaining unauthorized access to privileged accounts and critical identity management information.
The underlying security controls of ITDR are mainly comprised of prevention, detection, and response controls.
ITDR Works as Second and Third Layers of Defense After Prevention
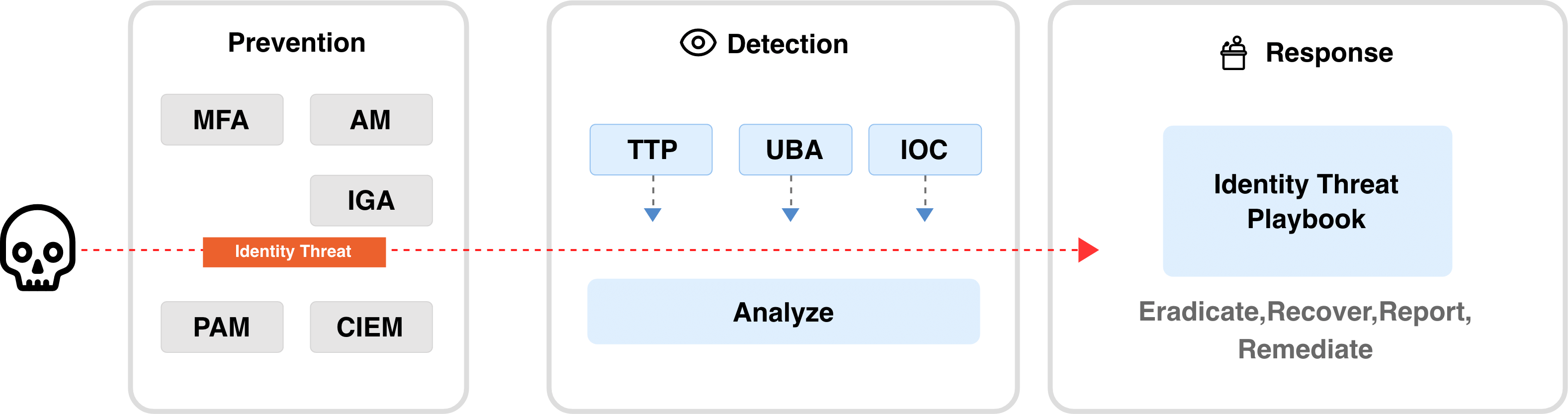
Enhance Your Cyberattack Preparedness With Identity Threat Detection and Response” by Henrique Teixeira, Peter Firstbrook, Ant Allan, and Rebecca Archambault
Preventive controls of ITDR are aimed at discovering and remediating vulnerabilities related to identities prior to their exploitation by threat actors. Not unlike legacy vulnerability and risk management systems, an ITDR solution's discovery capabilities allows organizations to recognize and mark risks associated with their identity assets.
An ideal and effective ITDR solution should carry out automated, continuous, and extensive identity discovery alongside the capability of providing transparencies in vulnerable and privileged accounts. Transparencies in vulnerable and privileged accounts equips the IT department to make effective decisions in regard to risk mitigation in heterogeneous identity management systems with big, multi-infrastructure and multi-phased utilization like MFA, SSO, IGA, PAM, and more.
Continuous improvement is a constant factor in every technological advancement, and in the context of identity security, continuous monitoring for threats and issues is a constant factor in managing a complex and intricate security system.
Upon detection of any signs of a threat actor or identity hijacking attempts within an organization's system, the ITDR system promptly activates its detective controls, subsequently issuing alerts as advance warnings. These controls possess a distinctive capacity to mitigate risks that may not be entirely preventable, allowing designated teams to be promptly notified and enabling them to respond swiftly in the event of an attack. This underscores the crucial role of an ITDR solution's detective controls in bolstering security measures.
Identity threat detection is not just about placing controls in place; it's also about acknowledging the fact that an absolute prevention of identity threats is challenging owing to the following problems:
This implies that a stronger and more accurate form of detection is needed when it comes to privileged accounts that have been compromised. This need can be extended to other types of privileged accounts as well, for example, Domain Admin accounts and Local Admin accounts.
An ideal execution of this strategy would be to deploy bait for the attacker. The bait should be based on the attacker's methods and tools to ensure that they don't realize the strategy or identify any hints that they are walking into a trap.
According to Gartner's playbook, "Enhance Your Cyberattack Preparedness With Identity Threat Detection and Response" by Henrique Teixeira, Peter Firstbrook, Ant Allan, and Rebecca Archambault, there are diverse aspects of the identity infrastructure probed by attackers using a myriad of techniques. From highly technical exploits such as zero-day attacks and infamous "info stealer" malware to social engineering, attackers employ different types of attack techniques depending on the targeted IAM aspect.
It is clear that defenders must keep pace with attackers in adapting to new techniques, much like how attackers constantly evolve their TTPs. One way to achieve this is for SRM leaders to possess the ability to identify multiple SSO sessions from the same user across various non-mobile operating systems.
Detecting TTPs may pose greater implementation challenges, yet it offers increased resilience, a dynamic approach, and the capacity to detect multiple threat actors and malicious tools—characteristics often associated with multifaceted identity-based attacks or threat events.
While focus on TTPs satisfies adversarial security requirements, security service edge (SSE) and cloud access security broker (CASB) technology can be used "in line" for administration console users, for instance, to manage devices and enable endpoint protection. In other words, deploying or integrating SSE and CASB technologies directly into the pathway or flow of users accessing an administration console, in particular, to ensure that security measures are applied directly to the user's devices as they interact with the console.
The cross-integration of the PAM, IGA, and MFA triad makes it possible to ensure that only fully authenticated users, operating on securely managed devices, retain the ability to make changes to the IAM infrastructure.
As stated in Gartner's playbook, Enhance Your Cyberattack Preparedness With Identity Threat detection and Response, "In addition to detecting unauthorized changes, an effective way of improving detection controls for identity threats is to use the MITRE ATT&CK® knowledge base of TTPs. Gartner’s How to Use MITRE ATT&CK to Improve Threat Detection Capabilities describes how TTP-based threat detection focuses on adversarial behavior in the form of specific techniques used during attacks. Industry research has confirmed that it is an effective way of detecting malicious activity."
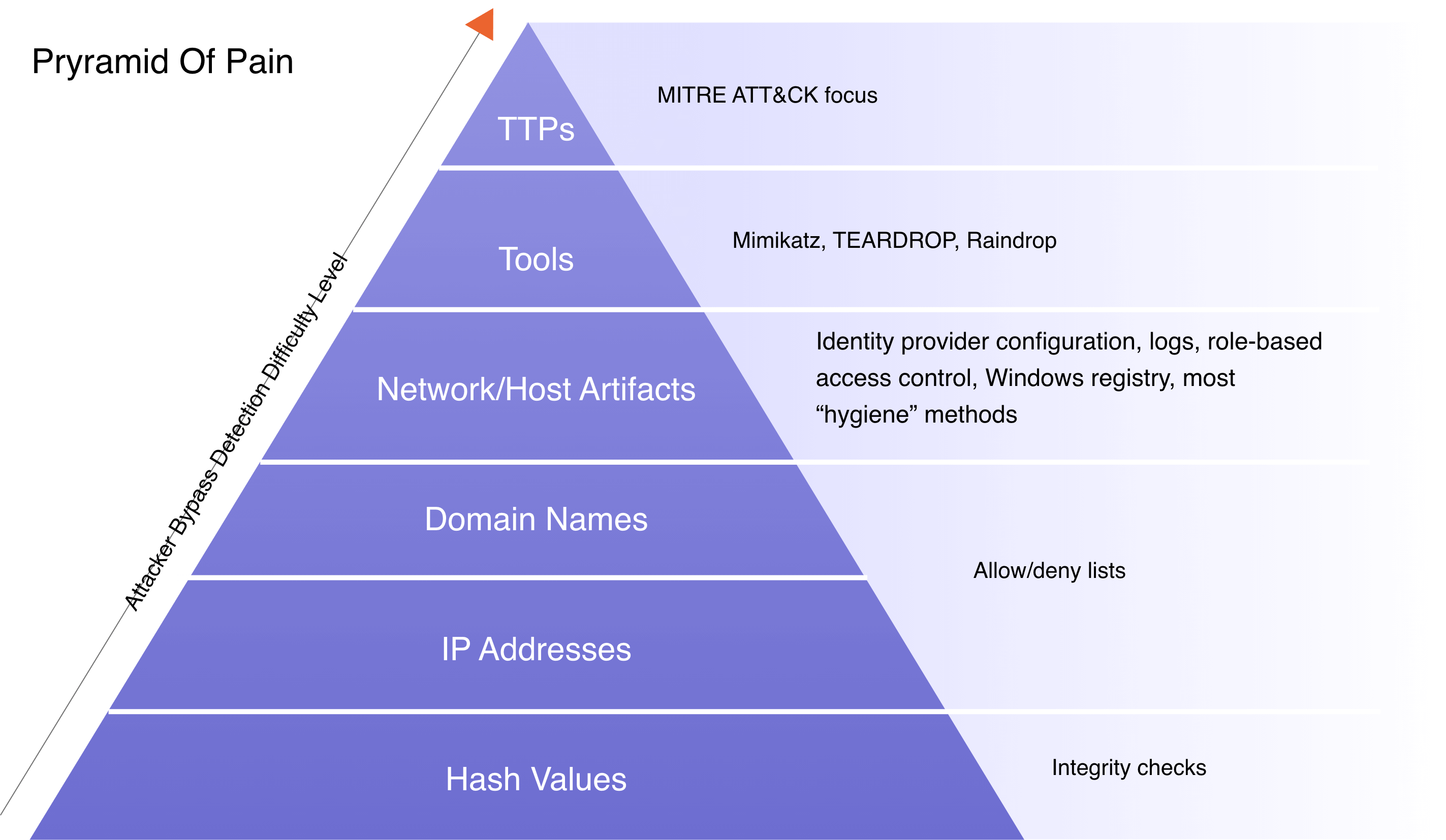
Enhance Your Cyberattack Preparedness With Identity Threat Detection and Response” by Henrique Teixeira, Peter Firstbrook, Ant Allan, and Rebecca Archambault
To enhance interoperability between ITDR (incident response) and IAM tool sets, particularly in the response phase, it is imperative to integrate procedures and security operations (SecOps) tools. This integration facilitates seamless investigations and enables automated response actions, ensuring a more efficient and effective response process.
Utilizing IAM controls like step-up authentication or session termination is valuable for mitigating ATO risks. The most prevalent automated response to contain compromised administrative credentials involves implementing risk-based adaptive access. In cases where the IAM infrastructure or its data is compromised, ITDR responses may initiate manual or semi-automated processes, such as disabling identity synchronization jobs. It is highly advisable to consult response playbooks when analyzing prevalent forms of identity attacks. Ideally, these playbooks should be crafted based on TTP use cases for a more comprehensive and effective approach.
According to Gartner's recommendations, ITDR playbooks should include guidance in the following areas:
Containment and eradication: Rapidly contain and eradicate threats by disabling command and control traffic, halting ID sync jobs, freezing automated provisioning, and stopping account changes in IGA and PAM. Implement risk-based adaptive access for automated threat containment, quarantine suspicious users through Azure AD, and deploy SSE to secure SaaS apps and prevent unauthorized access during an attack.
Recovery: This process involves restoration from backups and the collection of evidence for investigative and preservative purposes (inclusive of AM, IGA, and PAM logs).
Reporting: Early notification and communication is crucial, encompassing executives, legal staff, and response teams. For maximum transparency and accountability, it's advisable to have and exchange excessive information. This approach allows for prompt circulation of information, ensuring preparedness for any scenario and providing the flexibility to retract details if the security incident is not as severe as initially perceived. Additionally, strict adherence to applicable regulations is imperative. Furthermore, events should be promptly sent to endpoint tools for incident response processing, enhancing them by adding pertinent details to facilitate a comprehensive and efficient response.
Remediation: Essential actions at this final sub-stage include resetting affected credentials, eliminating rogue and excessive accounts, patching systems, and rotating security keys. To fortify the response framework, it is crucial to update the playbook and TTP knowledge base. Additionally, enhancing preventive and detective controls is paramount to improve overall security measures.
In the current day and age, AD is the most prevalent form of storing and managing identities and permissions. But that also makes AD a primary cyberattack vector. Attempted ransomware attacks targeting AD can be catastrophic. Once an attacker gains access to AD, they can steal organizational and user data along with intellectual properties by leveraging pertinent escalated privileges that will then allow this type of cybercrime to enable the cybercriminal to lock down or even completely tear down the system.
Gartner recognized the necessity and importance of identity security last year when it introduced the term ITDR. Several other organizations have also acknowledged identity security as being a priority and as the adoption of ITDR escalates, organizations are gradually realizing that it not only plays a separate role, but also melds strongly with endpoint security and hybrid AD (AD and Azure AD), and fulfills a critical role in the protection of identities.
What needs to be inferred from the above information is the evaluation methods of ITDR solutions. We need to decipher how ITDR plays in alignment with the stages of the AD attack cycle. But before we discuss ITDR's alignment with the AD attack cycle, we need to grasp what types of identities are considered vulnerable and the comprehension of preventive and detective controls in managing those vulnerable identities.
In any system involving accounts (i.e., identities), evaluating and recognizing the potentially vulnerable accounts is a primary step towards appropriate prevention and detection of threats. Vulnerable identities that need to be protected can be categorized into the following:
Settling on tools for the protection of the identity infrastructure should be done following the identification of gaps in the environment. Mentioned below are three steps that can be followed to identify environmental gaps:
Review of access privileges and the identification of stale accounts, excess privileges, and paths created due to escalation of privileges can allow you to examine the level of identity risk. Obscure, unused, and excessive access is often a result of expansion in identities and identity-related assets alongside the cloud's dynamic nature.
Reviewing actual access privileges and identifying stale accounts, excessive privileges, and privilege escalation paths allows you to assess the risk level of identities in your cloud environment. The dynamic nature of the cloud, combined with the proliferation of identities and assets, frequently results in concealed, unused, and excessive access.
Gartner stated that, “by 2024, organizations running cloud infrastructure services will suffer a minimum of 2,300 violations of least privilege policies, per account, every year.” Additionally, in the same report, it stated that, "the vast majority of granted entitlements in [Infrastructure as a Service] IaaS are unnecessary. More than 95% of accounts in IaaS use, on average, less than 3% of the entitlements they are granted, which greatly increases the attack surface for account compromises.”
It can take considerable time and effort to review every single cloud service and application for unusual or illicit activities. What's more, the review can be strongly prone to error as there is a high degree of human element involved. The use of CIEM solutions is recommended for assistance with the identification of excess privileges in IaaS; and if you're looking for complete coverage of all the bases, reviewing cloud applications and IAM tools for discovering and marking obsolete access including privilege escalations across all systems (shadow admins and federation) will prove beneficial.
To enable the detection of threats and risks (like exposed credentials, impersonation of users, and unauthorized changes), review the configurations, deployments, and enforcement of the IAM tools, including for SSO, IdP, IGA, and PAM. There's always a chance that the IAM solutions deployed (including the mature ones) may face identity-based threats owing to misconfigurations or inherent design.
Conducting a point-in-time assessment can help you determine your level of exposure and guide the adoption of ITDR measures for ongoing protection. By identifying areas where you are vulnerable, you can also determine which department or individual should take responsibility for ITDR within your organization.
Incident response for security infrastructure is handled by SIEM, SOAR, and XDR tools. While it is probable that some of the playbooks you use for incident response can also be used for identity risk and threat detection, it is recommended to review your existing playbooks and analyze whether they can be used to address identity and access incidents (some playbooks may have a direct implementation while others may require tweaks or adjustments).
Automated remediation capabilities like the removal of overflowing access permissions are also offered by some ITDR solutions. The determination of urgency and automation of your playbooks in use is directly proportional to the level of danger and impact of incidents on your organization. Therefore, leaders in SRM should focus on implementing best practices for maintaining the security of preventive IAM infrastructure hygiene. Additionally, they should consider exploring the ITDR solutions offered by various vendors from a broad spectrum of markets, which can help them be better prepared and responsive in the event of an attack on their infrastructure.
The strategy. behind ITDR can be leveraged by breaking it down into four key steps:
Access management has seen identities become its new operational base owing to the fractured nature of perimeters. Complete visibility or transparency regarding information on identity-related attack activities has become a crucial factor in understanding the risks associated with the attack surface and detecting security anomalies.
It just takes a single credential to be exposed for an attacker to welcome themself into your identity environment. As discussed earlier, one of the first steps to get started with ITDR is the discovery and removal of exposed, misconfigured, and unmanaged credentials. Moreover, the prevention of credential misuse can be achieved through policy-based controls, which secure credentials by associating them with credential stores. Organizations can thwart theft and misuse by employing concealment and deception technology, thereby protecting credentials via employing deception lures and fake artifacts.
For organizations using AD, admins can configure access and management for PCs, laptops, and other Windows-based services by implementing policy enforcement during the initial creation of new users, groups, and domains. Consequently, cyberattackers realized and started targeting AD in order to gain and exert control over the domain. Considering the long-standing vulnerabilities of AD, the rate of success for exploits is high more often than not.
When malicious actors strike, their main objective during their dwell time as they laterally traverse across the enterprise's network is the escalation of privileges and entitlements. This privilege-based element of a threat actor's attack strategy is a reason strong enough to warrant your main focus, both in terms of ITDR and incident detection and response (IDR), as the detection of an anomaly will require you to take an apposite security action.
When the detections from ITDR and cyber deception are synchronized, XDR platforms can acquire supplementary attack data, enabling incident response actions to be initiated in response to that information.
The key is to draw the attention of an attacker in the early stages of the cyberattack. Achieving this is possible using deception technology that offers an extensive detection fabric that uses deceptive credentials, bait, shares, and various kinds of decoys to cloak the network effectively.
Deception is one of the strongest methods to dupe attackers into exposing themselves. Pairing legacy deception technology with concealment technology (vanishing real objects and leaving solely the decoys for attackers to drive their attention towards), can hide and deny access to assets related to the production network, and put a stopper in place so that attackers are unable to leverage credential stores, AD objects, and information.
Guiding the attacker toward a decoy and sharing TTPs and indicators of compromise (IoCs) with an XDR platform offers effective detection alerts and secure interaction.
To understand threat detection and response, one needs to first understand how a cyberattack progresses, what the key phases involved in performing a successful attack are, and the role played by ITDR in counteracting it.
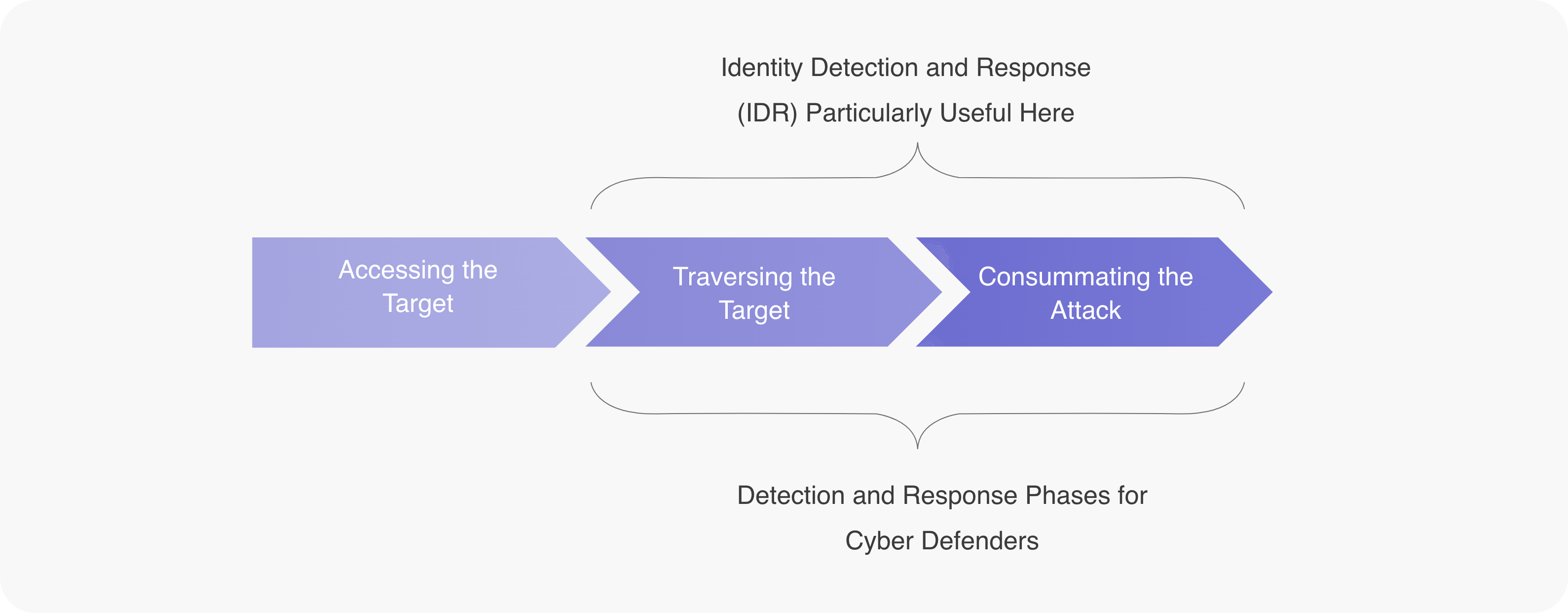
Numerous strategies for cyberattacks have been introduced, such as the MITRE ATT&CK framework and the Lockheed Kill Chain. The following three-step approach simplifies these intricate models into the three core phases that underlie almost every offensive cyber campaign.
The first phase of any given cyber breach necessitates identifying vulnerabilities in a target's defense system to gain entry to a secured network, domain, or system. When breaching the perimeter, this access is termed a north-south connection, and firewall-based measures are implemented to avoid such access by enforcing certain policies. While physical boundaries have been replaced with software-defined ones in recent times, the control goal remains the same.
The second phase in a cyber breach includes lateral movement (horizontal traversal) within the system and privilege escalation (elevating account/user privileges), often accomplished by credential theft and credential misuse to gain access to resources like AD. When this progression occurs gradually, it's known as dwelling, and one of the most challenging tasks for system defenders is reducing the time attackers spend in this phase. Dwell time of attackers can be reduced by incorporating ITDR controls like real-time anomaly detection and alerts and notifications.
The final phase entails the attacker concluding the attack, which could involve successfully leaving the targeted domain with stolen data or taking any necessary actions to achieve the intended outcome of a given attack. After this happens, system defenders are left with the crucial task of response, which is also one of the key roles fulfilled by ITDR.
Stage 1: Pre-cyberattack identity security (before)
During the 2022 Gartner Identity & Access Management Summit in Las Vegas, a poll conducted by the Identity Defined Security Alliance revealed that over three-quarters of respondents anticipated a severe impact on their organization in the event of a cyberattack. This aligns with the 2022 Trends in Securing Digital Identities research, which indicated that 78% of organizations experienced business consequences due to an identity-related breach. Despite many respondents having a disaster recovery solution, a notable gap emerged, as they lacked a specific plan or solution to defend and recover their AD.
Comprehensive and meticulously tested identity security solutions and procedures are of utmost importance as components of a successful recovery plan. A proactive stance towards contingency measures such as identity security evaluations, AD backups, and AD recovery protocols is key for effective restoration of the identity store.
One of the major issues surfaced in recent times is the fact that numerous contemporary cyberthreat TTPs are crafted to bypass conventional security monitoring and detection tools that are based on security and event logs. Because of this, SIEM solutions are facing challenges in detecting attacks like DCShadow, causing them to be ineffective.
To overcome this challenge, the detection component of ITDR should encompass various approaches to monitor different data sources, such as the AD replication stream, in order to identify signs of vulnerability or compromise that might otherwise remain unnoticed. Therefore, consistent assessment of the hybrid AD environment's security posture is required and worthwhile considering the shift in TTPs.
Stage 2: Active cyberattack identity protection (during)
The poll by IDSA revealed that while over three-quarters of interviewees function in a hybrid identity setting, confidence in remediating an on-premises attack is voiced by only about one-third of respondents. Additionally, just a little over one-quarter of participants conveyed a similar level of confidence in defending Azure AD.
The interconnected nature of identity management systems in a hybrid environment, particularly for organizations using Microsoft 365 and Azure AD alongside maintaining on-premises AD, was the key highlight. The vulnerability arises from the synchronization between on-premises AD and Azure AD, potentially providing attackers with a pathway to move between on-premises and cloud environments.
This underscores the requirement of appropriate security measures, as demonstrated by the SolarWinds cyberattack in which Azure AD was exploited to access the on-premises identity store. The interconnectedness of these systems corroborates the need for comprehensive cybersecurity strategies that address potential breaches and the seamless integration of cloud and on-premises security protocols.
To deal with cyberattacks actively, organizations should accommodate automatic remediation capabilities for their AD to cease unusual changes and dodge threat actors and events that have penetrated the identity environment. It's essential to remember that a delay of only a few minutes can completely eliminate any opportunities available to thwart the attack.
Notably, in 2017, Maersk fell victim to the NotPetya attack, which infiltrated the entire network within a matter of minutes. Out of all the responses in the 2022 Gartner Summit, a good chunk of people wished to prioritize automated remediation of malicious changes when it came to their initialization of remediation capabilities.
Stage 3: Post-cyberattack identity restoration (after)
The concept of ITDR has affected the consistent focus on recovery. With considerable attention towards detection and response, businesses deviated from a true ITDR solution that also includes identity restoration.
There are challenges associated with post-cyberattack recovery, such as the potential drawbacks of manual recovery processes, especially when relying on system-state backups that can lead to the reintroduction of malware during recovery depending on the duration of the attackers' presence in the environment. This can result in substantial downtime, spanning days or even weeks, leading to significant losses in both data and business revenue.
Introducing an automated, multi-forest AD recovery solution can prove to be a positive measure, not only for expediting the recovery process but also to save valuable time, resources, and to safeguard the organization's reputation. The advice to organizations is to not to overlook this final stage of the ITDR equation, as it plays an equally important role in restoring their original status before the cyberattack effectuated.
To reduce cyber risk, SRM teams will need to strategize and devise a plan that can take full advantage of ITDR solutions. Based on the internal and external systems and infrastructure, the context of every single enterprise will differ, but following the below-mentioned steps can lead to a beneficial outcome for most divisions or teams.
Step one: Analyze identity-related exposures and collect data
To assess exposures, attack statuses, and posture, the enterprise team needs to conduct an inventory of the current management of identity-related vulnerabilities and live attack activity information. It is highly probable that many of the enterprises do not perform this action.
Step two: Assess vendors and analyze
The subsequent action for the enterprise team is to conduct a review of a commercial IDR platform. Tests typically involve simulations of a realistic environment or live networks in production to prove that the concept works (formally known as proof-of-concept testing).
Step three: Formulate the implementation plan
IDR should be implemented in phases in order to detect identity-based exposures and lateral movement within an enterprise efficiently. Large and complex organizations especially should implement IDR in phases. The objective is to quickly deploy IDR and roll out its detection capabilities.
According to Paul Furtado, VP analyst at Gartner, “ITDR is the crux of your network, the core of your network, and you need to have very strong identity discipline in your environments.”
One of the main reasons organizations face data breaches is still, most likely, due to fragile identity security discipline, which is an open invitation for threat actors to carry out an attack, such as credential compromise.
Paul Furtado recommends:
Analysts at Gartner also stated, “We’re seeing more and more organizations struggling simply from the fact that they don’t do a good job with fundamentals. They don’t do a necessarily good job of adapting their current models to be leveraged across their entire environment.”
The intricate realm of identity threats in the ever-evolving cybersecurity landscape demands a multifaceted approach. The synergy of IAM and ITDR not only attempts to address the challenges posed by a surge in third-party technologies and complex work perimeters but also harnesses the explosive growth of digital identities. ITDR, modeled after the foundation of preventive and detective security controls, is becoming the linchpin in preserving an organization's digital soul.
The initiation of ITDR involves a thorough categorization of vulnerable identities, addressing those that are unmanaged, misconfigured, or exposed, and systematically identifying the gaps in identity infrastructure. This strategic orchestration, combined with ITDR's alliance with Zero Trust principles and XDR, offers a robust defense mechanism against the phases of an offensive campaign, safeguarding identities before, during, and after a cyberattack.
The ITDR life cycle, encompassing pre-cyberattack identity security, active cyberattack identity protection, and post-cyberattack identity restoration, deems it imperative to follow a meticulous action plan, including exposure analysis, vendor assessment, and implementation formulation. By adopting such a comprehensive approach, organizations can fortify their cybersecurity posture, demonstrating a commitment to mitigate identity threats proactively and ushering in an era where digital identities remain secure, unblemished, and resilient.