Historically, a major part of security investments have been allocated to preventive security controls. Although this may seem like a good strategy in theory, preventive controls are not always effective against data breaches all the time.
This is primarily because network boundaries are vanishing as companies adopt cloud.
This shift made digital identities the center of network security. The extended network perimeter poses a huge challenge for security teams especially in protecting the integrity of data and threat detection. To tackle these challenges, they need a new age behavioral analytics tool. This article elaborates
User behavior analytics, or UBA, is a technology used to detect anomalies in user behavior patterns to spot threats within the network. According to Research and Markets, the global security analytics market size is projected to grow to USD $18.1 billion by 2024 at a compound annual growth rate (CAGR) of 18.2 percent. This growth will be fueled by the demand for insider threat and compromised account detection capabilities that traditional security systems lack.
UBA solutions use data analytics and machine learning (ML) algorithms to create a baseline behavior specific to each user. They detect deviations from this baseline thus helps to detect potential security threats at its early stage.
But how is UBA really different from traditional security solutions? What does it offer that they can't? Let's take a look.
While existing security solutions use static threshold values to differentiate between what is normal and what is not, UBA solutions use an analytical approach—a combination of data analytics and machine learning—to implement dynamic thresholds based on real-world user behavior.
UBA collects information on what users across the organization are doing over an extended period of time, then creates a baseline of "normal" activities specific to each user. Whenever there is a deviation from the established baseline, the UBA solution considers this abnormal and alerts the administrator.
The cornerstone of UBA solutions is the premise that behaviors are hard to mimic. So, when an external entity does try to break into the network, it's going to be easy to spot.
The various stages of how UBA works:
AD360, ManageEngine's real-time Active Directory change monitoring software, doesn't stop with just auditing your domain controllers. It goes a step further by incorporating UBA to detect insider threats more efficiently. Its built-in UBA engine helps you:
Let's take a use case. Assume a disgruntled employee departing from the organization wants to steal critical financial information. The employee copies 200 documents containing corporate financial data. Since the user normally accesses around 10 documents a day, this behavior is abnormal. The UBA solution recognizes this abnormal behavior, and triggers an alert to the administrator.
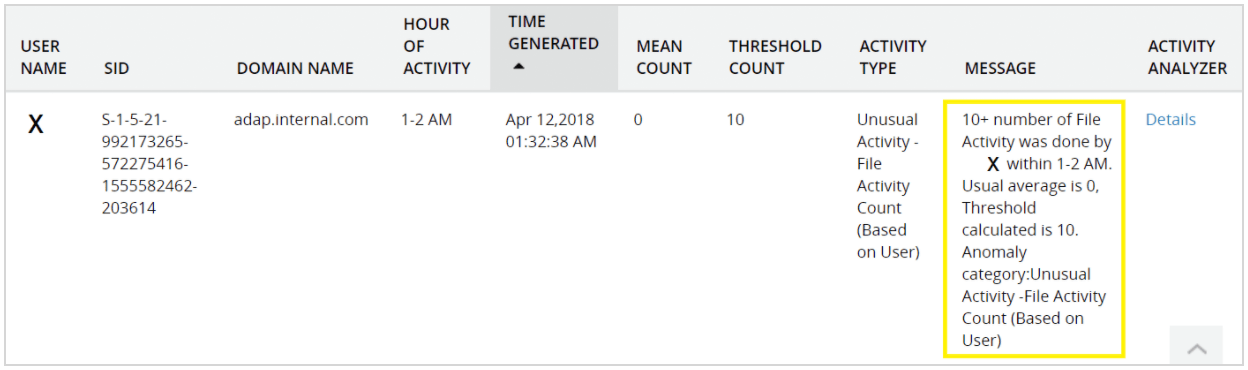
A traditional security without UBA capabilities can't establish a baseline of normal user activity to spot abnormalities, and would not see this level of file access as strange. However, this is a clear case where the user's activity is abnormal and requires an administrator’s attention.
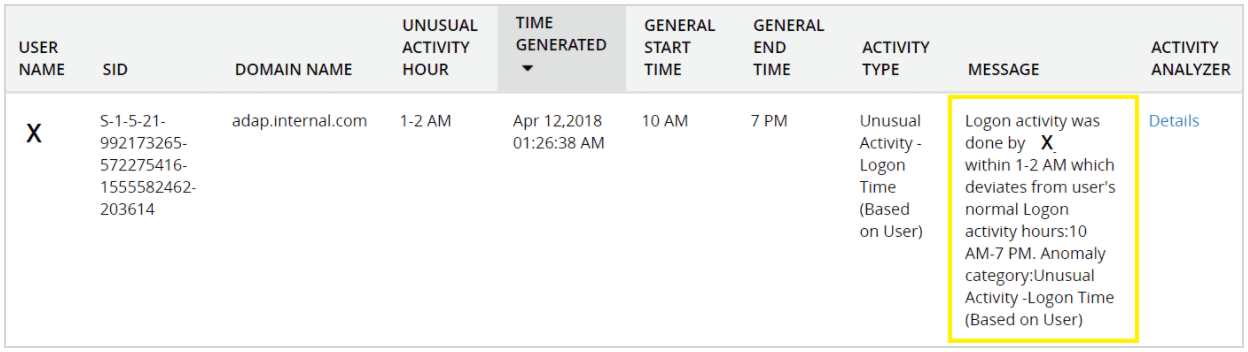
A disgruntled employee wants to steal important information by using a coworker's credentials. After the coworker goes home for the day, the attacker attempts to log on from the coworker's computer to avoid flagging a logon event from the wrong computer. After several incorrect guesses at the coworker's password, the attacker successfully enters the correct password and logs on.
Having calculated the typical logon time of the coworker for the past months, the UBA solution detects an abnormal logon time. With UBA, not only is the unusual logon time detected, but an alert is raised and sent immediately to the administrator.
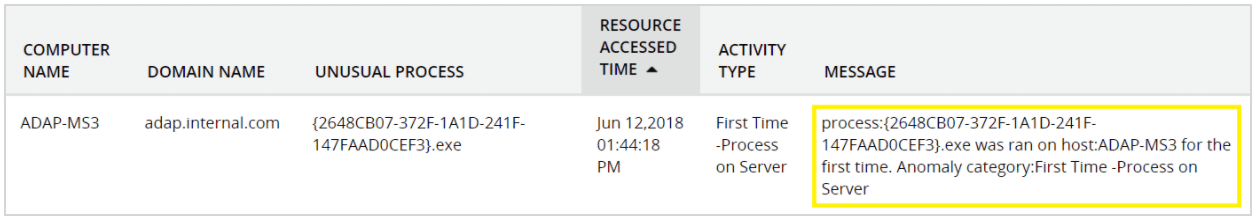
An employee gets a malicious application installed when browsing the internet. They then connect to the server, where they have administrator privileges, to perform administrative tasks. The UBA solution detects this new action on the server and triggers an alert. More quickly detecting an attack enables administrators to mitigate its impact.
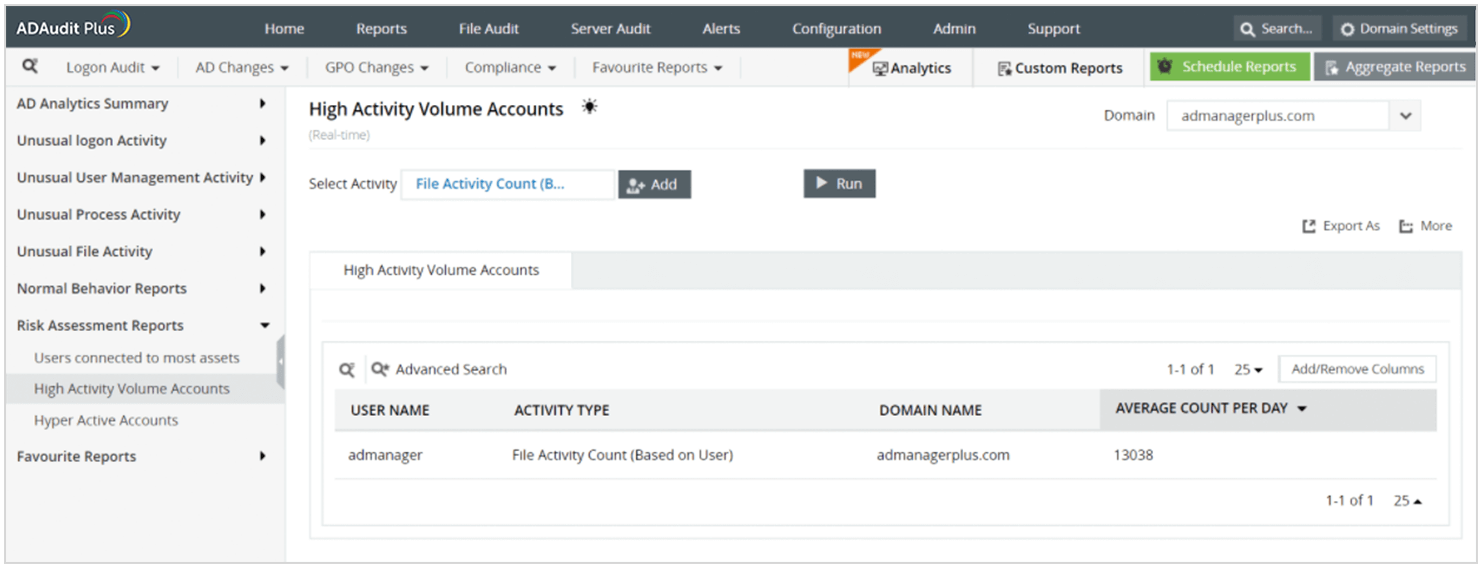
AD360’s UBA module detects abnormal user behavior of privileged users to protect sensitive data. For instance, if a privileged user tries to access a critical file or folder and perform an unusually large volume of file modifications, AD360 will flag this event and send an alert about the possible threat.
If a user accidentally opens the door for a breach or damages data by mistake, AD360’s UBA engine can spot this anomaly immediately. Consider a user who accidentally grants everyone in the organization permission to access a sensitive file. AD360 will detect the unusual volume of file activity and trigger an alert. An admin can then take a look into why this file was suddenly accessed so many times, and detect the data breach.
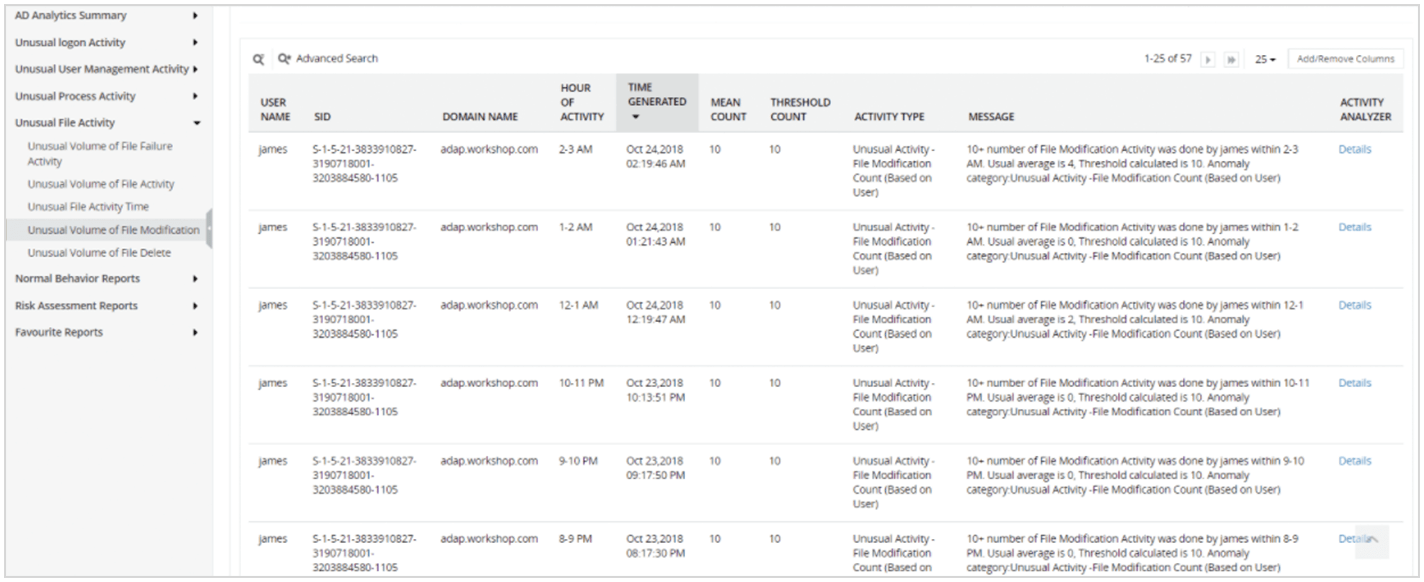
You can identify the weak points in your network by filtering the users connected to the most assets, as well as hyperactive accounts. AD360 offers risk assessment reports for monitoring these vulnerable accounts. For instance, you can find out which accounts have the highest activity count (e.g. high file activity) by running a query in the risk assessment reports.