On this page
An Algerian hacker group identifying as Jabaroot initiated a cyber defacement campaign in April 2025 against the website of Morocco's Ministry of Economic Inclusion. The group stated that this act was a retaliation for Moroccan hackers allegedly compromising the X account of the Algeria Press Service (APS). But the Moroccan ministry downplayed the incident, asserting that no sensitive data was compromised. In response, the group published over 3,000 documents, purportedly employee payslips, challenging the ministry's claims.
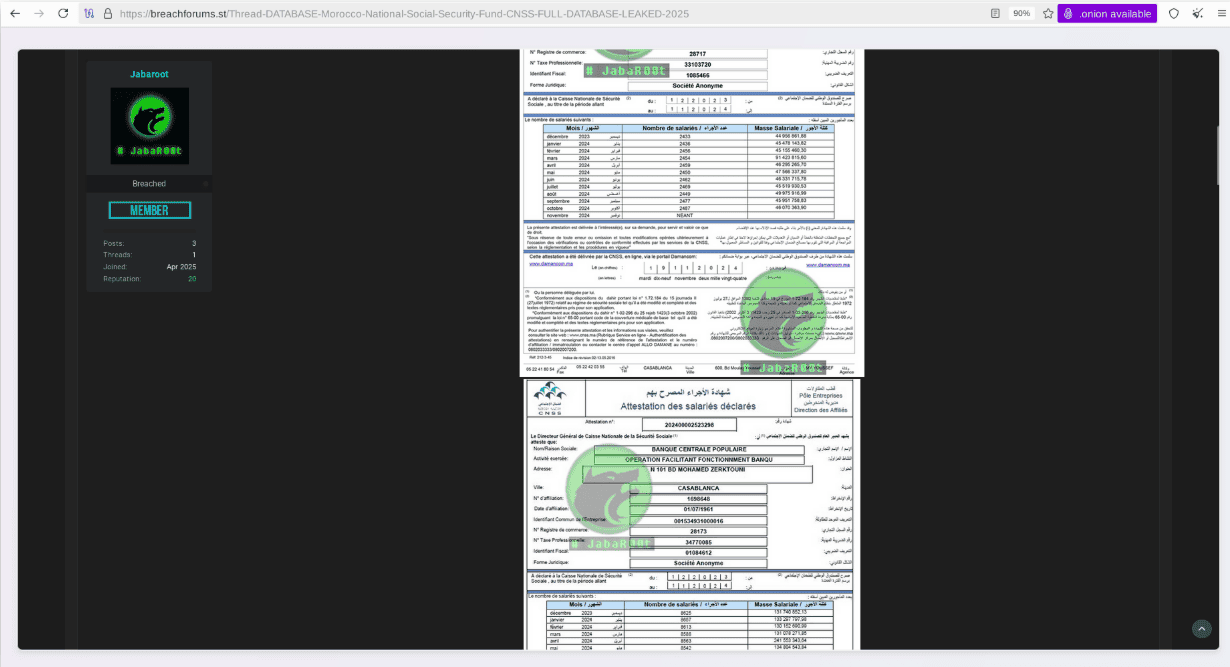
Source: Resecurity
A step-by-step breakdown of the attack
In early April 2025, tensions in cyberspace between Algerian and Moroccan hacking groups escalated dramatically, culminating in a series of targeted cyberattacks. The catalyst appears to be the alleged compromise of the APS’s X account by Moroccan hackers. In retaliation, a cyber group identifying as Jabaroot launched a coordinated campaign against Moroccan government institutions, including the Ministry of Economic Inclusion and the National Social Security Fund (CNSS). The attackers created a Telegram channel to disseminate their motives and leak data, declaring the APS incident as the primary trigger for their offensive.
Well before the breach occurred, Moroccan cybersecurity expert Hassan Kherjouj raised concerns about vulnerabilities in the ministry’s digital infrastructure. In a detailed Facebook post shared on Apr. 3, 2025, he outlined several critical issues, including:
- The critical weaknesses in the ministry's website infrastructure.
- Issues within the WordPress configuration, specifically the file public_html/wp-includes/class-wpdb.php, which manages database interactions.
- The key threats identified, such as:
- Remote code execution.
- File modifications via malware and backdoors.
- SQL injection attacks.
- The observation that even merely revealing the database file’s name posed a serious security risk, as it would greatly ease exploitation for attackers.
Soon after these warnings, Algerian hackers executed a large-scale breach, temporarily disabling access to the ministry’s services. Algerian media claimed that millions of data points were exfiltrated. Investigations revealed that the compromised data was stored on unencrypted and poorly secured servers, allowing unauthorized access to sensitive financial and personal information. Preliminary investigations suggested the leak resulted from hackers bypassing the ministry's security systems.
The cyber offensive by Jabaroot on April 8 marked the beginning of a wave of attacks. In response, Moroccan hacker groups—including Phantom Atlas and Moroccan Cyber Forces, launched counterattacks on April 10. These groups claimed responsibility for breaching Algeria’s Social Security Fund for Postal and Telecommunications Workers, leaking 13–20GB of data, including ID numbers and administrative documents. Additionally, they claim to have accessed internal systems belonging to Algeria's Ministry of Labor.
The conflict didn’t stop there. On April 12, another Moroccan hacktivist group named Evil Morocco announced via Telegram that they had hacked into an Algerian university’s website and leaked academic data. This action is consistent with previous patterns in which hacktivists target educational and governmental platforms, which are typically protected by low- to mid-tier security protocols.
Cybersecurity firm Resecurity confirmed the authenticity of the leaked data, noting that it was not offered for sale, since the the stolen data had been uploaded to an underground forum on the dark web for free , suggesting motives beyond financial gain.
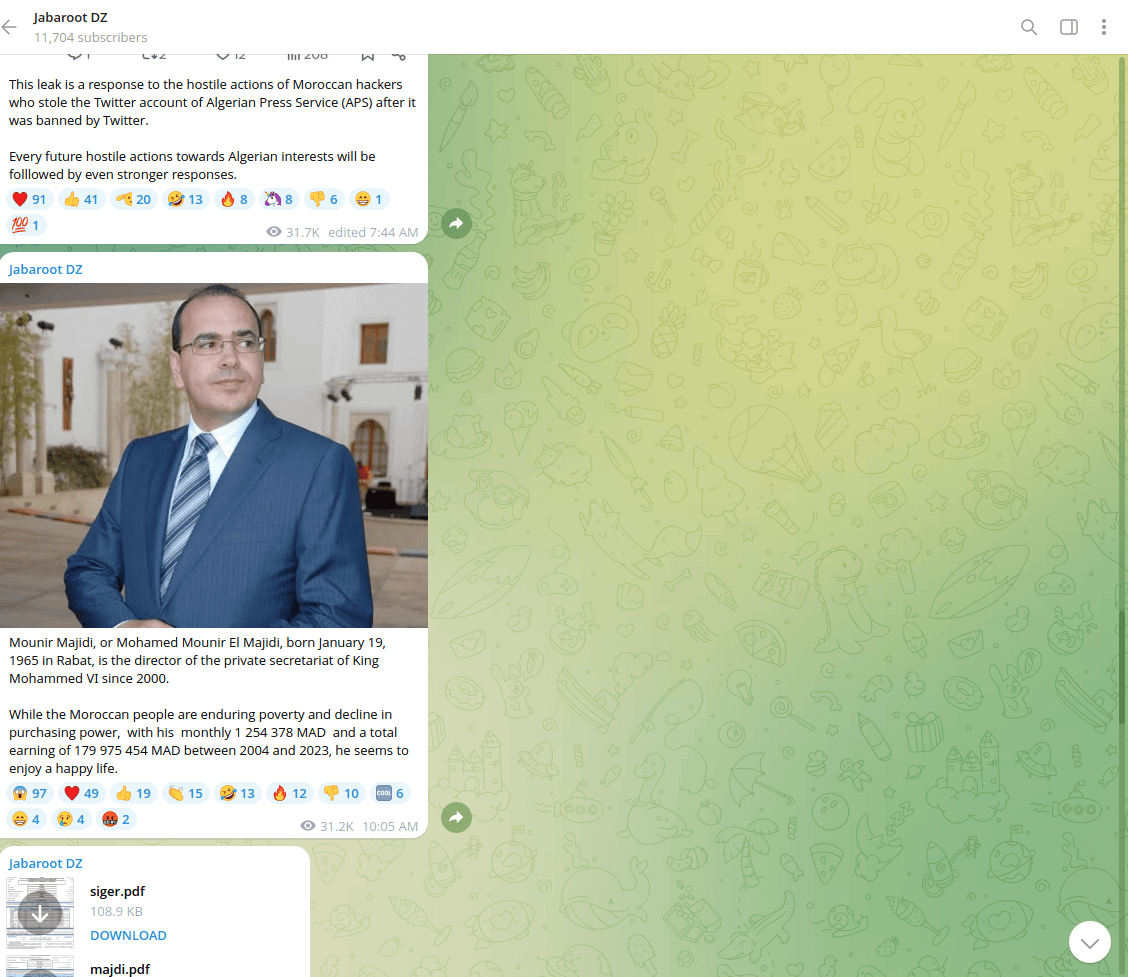
The threat actors leaked the salary records of several government officials, accusing them of attempting to downplay the incident.
Source: Resecurity
After this, the CNSS acknowledged the breach but claimed that many of the leaked documents were "misleading, inaccurate, or incomplete." Also, Morocco's National Control Commission for the Protection of Personal Data pledged to investigate complaints from individuals affected by the leak.
What began as a tit-for-tat cyber retaliation has now evolved into a wider digital skirmish tied closely to regional geopolitical tensions. The breaches have not only exposed glaring vulnerabilities within national systems but also underscored the growing importance of cybersecurity readiness in the face of digital warfare.
What was the impact of the attack?
Here's how the attack affected Morocco's ministries, citizens, and beyond:
- The main target of the attack was Morocco's CNSS, which is responsible for managing pensions and insurance for millions. Personal records of thousands of Moroccan citizens have been exposed, including:
- Names, addresses, phone numbers, and emails.
- Salary slips and CNSS salary declaration certificates.
- ID numbers and employment details.
The volume of data exposed is:
- Over 53,000 PDFs.
- A compromised Excel file containing data on nearly 500,000 companies.
- 13–20GB of sensitive data was leaked in retaliatory attacks by Moroccan groups.
- The threat actor has leaked a CSV file containing personal information of 1,996,026 employees from various enterprises operating in Morocco. Notably, the CNSS has more than 40,000 reporting companies and over 3.9 million employees in its system; so the data breach could be interpreted as large-scale. High-profile organizations included in the data:
- SIGER, the Moroccan royal family’s holding company.
- Major banks and media outlets.
- The Israeli Liaison Office in Morocco.
This exposed the data of not only citizens but also state-affiliated and international organizations, risking diplomatic and financial fallout.
- The Ministry of Economic Inclusion’s digital platform became inaccessible, affecting services relied upon by job seekers, employees, and companies. This hindered day-to-day public service operations. Citizens reported an inability to access services like:
- CNSS account management.
- Salary certificate retrieval.
- Government job applications.
- The attack is seen as a digital front of the long-standing political tensions between Algeria and Morocco.
- The incident revealed systemic security lapses in Moroccan government institutions. This has undermined citizen trust in the government's ability to protect personal and financial data.
What are the vulnerabilities that led to the attack?
As cybersecurity specialist Kherjouj highlighted in his Facebook post, several critical vulnerabilities existed in the ministry's digital infrastructure. Here are the vulnerabilities that led to the attack:
- Unsecured WordPress configuration: The ministry’s website was reportedly running on WordPress, a platform often targeted by attackers if not properly hardened. A major vulnerability was found in the public_html/wp-includes/class-wpdb.php file, which handles database interactions.
Misconfiguration in this file can lead to:
- SQL injection attack.
- Remote code execution.
- Backdoor or file modification.
- Exposed database file paths: Kherjouj emphasized that exposing internal file names and structures (such as class-wpdb.php) is a serious danger. The fact that other actors were aware of file paths implies that directory indexing or debugging information was unintentionally disclosed to the public, providing attackers with a path to further compromise.
- Lack of data encryption: The breached data was reportedly stored in unencrypted formats. This means that there was no protection at rest, which is a critical security failure for sensitive governmental records.
- Delayed response despite early warnings: Although Kherjouj's warning was given five days before the attack, apparently nothing substantial was done to mitigate the vulnerabilities. Since there was no proactive response, attackers were able to take advantage of known vulnerabilities without encountering any resistance.
What are the key lessons for CISOs?
When it comes to cyber readiness, the attacks against Morocco offer a lot of lessons. Here are the key takeaways for CISOs:
- Conduct regular vulnerability assessments: Continuously scan and patch public-facing systems like WordPress to eliminate unpatched vulnerabilities and prevent overlooked security gaps.
- Adopt secure-by-design development practices: Ensure that all government platforms are built with security integrated from the core, rather than treated as an afterthought during deployment.
- Enforce mandatory encryption standards: Implement encryption for all critical databases and data flows—both at rest and in transit—to safeguard sensitive personal and financial information.
- Deploy layered, intelligent threat detection: Incorporate application-layer protection and behavioral analytics into your SIEM or security stack to catch sophisticated, multi-stage attacks.
- Leverage behavioral analytics for threat detection: Monitor and flag anomalies like large data transfers, off-hour access, or sudden privilege escalations, enabling proactive rather than reactive responses.
- Implement role-based access and network segmentation: Limit lateral movement by enforcing micro-segmentation and access control based on user roles and the principle of least privilege.
- Establish regular cybersecurity drills: Conduct red-teaming exercises and tabletop simulations to evaluate incident response readiness and improve coordination during real attacks.
- Account for geopolitical threats in risk models: Update risk assessments to include politically motivated cyberattacks, especially for the public sector and government-adjacent organizations.
- Foster strategic cybersecurity collaboration: Partner with national CERTs, peer agencies, and global threat intelligence communities to gain early warnings and trace cross-border threats.
- Promote a culture of shared cyber responsibility: Train end users, developers, and administrators regularly on cybersecurity best practices to build a strong human firewall alongside technical defenses.
Security guidelines CISOs should consider to protect critical data
Here are our policy-making recommendations for CISOs:
1. Proactive vulnerability management
Policy recommendations:
- Mandatory vulnerability scanning of all public-facing systems, especially those built on platforms like WordPress.
- Enforce preemptive patching schedules for high-risk components (for example, class-wpdb.php).
- Implement bug bounty or coordinated vulnerability disclosure programs for ethical hackers and researchers.
CISO decision-making considerations:
- Budget for continuous threat intelligence subscriptions and bug bounty programs.
- Evaluate tools that automate open-source software vulnerability detection.
2. Public sector cyber hygiene policy
Policy recommendations:
- Develop and enforce cyber hygiene standards for all government departments.
- Enforce the use of encrypted servers, MFA, and access control lists for sensitive employee data.
- Conduct annual cyber audits of national institutions (e.g., education, labor, social security).
CISO decision-making considerations:
- Assign security liaisons within each ministry or department.
- Integrate cyber audit findings into national cybersecurity maturity benchmarks.
3. Incident disclosure and response protocols
Policy recommendations:
- Create a centralized breach notification framework that mandates transparent, timely disclosures of cyber incidents.
- Enforce a deny only with evidence approach: If a breach is denied, technical justification should be presented.
- Include public messaging guidelines to prevent downplaying incidents without verification.
CISO decision-making considerations:
- Train crisis communication teams in tandem with incident response (IR) units.
- Establish a partnership with independent third-party assessors to verify breach claims.
4. Geopolitical cyberthreat modeling
Policy recommendations:
- Mandate geopolitical threat modeling exercises for national cyber defense teams, particularly in politically sensitive regions.
- Develop country-specific threat profiles based on historical cyber conflicts and hacktivist group behavior.
- Implement intelligence-sharing agreements with trusted nations and organizations (via CERTs or Information Sharing and Analysis Centers).
CISO decision-making considerations:
- Allocate budget for regional intelligence feeds.
- Develop cyber drills that simulate retaliation-based digital attacks.
5. Dark web monitoring and data leak prevention
Policy recommendations:
- Invest in dark web monitoring solutions to detect leaks of national, employee, or citizen data.
- Enforce data-at-rest encryption policies and DLP tools in government IT environments.
- Establish a response playbook for dark web data leaks, including victim notification and damage control.
CISO decision-making considerations:
- Partner with cybersecurity vendors offering threat intelligence and data leak Detection as a Service.
- Build rapid internal workflows for validating leaked data and initiating mitigation steps.
6. Media and social platform monitoring
Policy recommendations:
- Monitor social platforms like Telegram, Facebook, and X for breach claims or coordinated attack chatter.
- Establish early warning systems based on social media chatter from regional hacker groups.
CISO decision-making considerations:
- Integrate open-source intelligence capabilities into security operations centers (SOCs).
- Partner with tech platforms to flag and assess potential threats.
7. Cybersecurity education and awareness
Policy recommendations:
- Launch mandatory cybersecurity training for all government personnel, including non-technical staff.
- Special training for administrators managing WordPress, public portals, and national databases.
CISO decision-making considerations:
- Work with national IT training institutes or international partners (e.g., United Nations, European Union) to create localized programs.
- Use gamified simulations to improve engagement and retention.
8. Retaliation policy and ethical cyberdefense
Policy recommendations:
- Define a national ethical stance on retaliatory hacking—what constitutes defense versus offense.
- Create policy guardrails to avoid escalation into uncontrolled cyber warfare.
CISO decision-making considerations:
- Collaborate with national legal and policy bodies to ensure all cyberdefense activities remain within legal frameworks.
- Assess potential legal risks and diplomatic implications of retaliatory cyber actions.
Why should CISOs consider a SIEM solution to mitigate nation-state threats?
Here are the features of SIEM and the key metrics that can be presented to the board by the CISO to prevent nation-state threats:
| SIEM feature | Key metric | Benefit | Financial impact |
|---|---|---|---|
| UEBA | The number of unusual login/access patterns identified. | Flags compromised admin accounts or suspicious behavior. | Prevents data exfiltration and lateral movement, reducing potential breach fines. |
| Log collection from Cloud and SaaS apps | Percentage of coverage of cloud platforms and SaaS APIs integrated. | Expands visibility into communication channels like X and email. | Prevents blind spots in hybrid environments, reducing the risk of undetected data leakage. |
| Automated incident response (SOAR) | Mean time to respond to social engineering-based attacks. | Speeds up containment by automating actions like account lockouts. | Cuts response time by hours or days, reducing operational downtime and security staffing costs. |
| Alert risk scoring and prioritization | Percentage of high-fidelity alerts handled first. | Helps analysts focus on critical incidents. | Increases SOC productivity, saving analysts time. |
| Historical forensics and timeline mapping | Time to root cause analysis. | Quickly reconstructs how an attacker gained access. | Shortens forensic investigations, cutting third-party IR costs and regulatory penalties. |
| Compliance and media policy auditing | Percentage of monitored policy violations or account exposures reviewed. | Ensures public communication tools meet internal and regulatory standards. | Avoids fines and ensures public trust by maintaining accountability post-breach. |
Related solutions
ManageEngine Log360 is a SIEM solution that combines DLP, CASB, machine learning, and MITRE ATT&CK® mapping to deliver real-time threat detection, automated response, streamlined incident management, and compliance across hybrid IT environments.
Sign up for a personalized demoManageEngine AD360 is a unified IAM solution that simplifies identity, access, and security management across on-premises and cloud platforms with features like user provisioning, SSO, self-service password management, and auditing.
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
