The attack was publicly confirmed in late April 2025, but threat actors are believed to have gained access to internal systems as early as February 2025, indicating a prolonged dwell time before ransomware deployment.
On this page
April 2025 saw many retail chains plagued by cyberattacks, including Co-op, Harrods, and Marks & Spencer (M&S), with the latter being hit the hardest. The retail giant M&S admitted and apologized to its customers for a "cyber incident" which happened during the Easter weekend. The incident was identified to be a high-impact ransomware attack and attributed to the Scattered Spider group, the cybercriminals who've allegedly claimed responsibility for the attacks on Co-op and Harrods as well.
The M&S incident exposed critical lessons in identity security, social engineering resilience, and incident preparedness. Despite having multi-factor authentication (MFA) in place, attackers bypassed protections by targeting service desk personnel through convincing impersonation tactics, ultimately gaining access to Active Directory (AD) and deploying ransomware that disrupted online operations, payment systems, and customer services.
For the retail sector—which operates in a fast-paced, customer-driven environment—the cost of such disruption goes far beyond IT downtime, impacting brand trust, customer retention, and financial performance. Cybersecurity in the retail sector is also crucial because it deals with multiple third-parties—each with a different level of cyber hygiene—increasing the attack surface and breach likelihood. This underscores the need for CISOs to reassess the security of privileged credentials, help desk protocols, endpoint monitoring, and proactive threat detection.
M&S cyberattack 2025: An overview and timeline
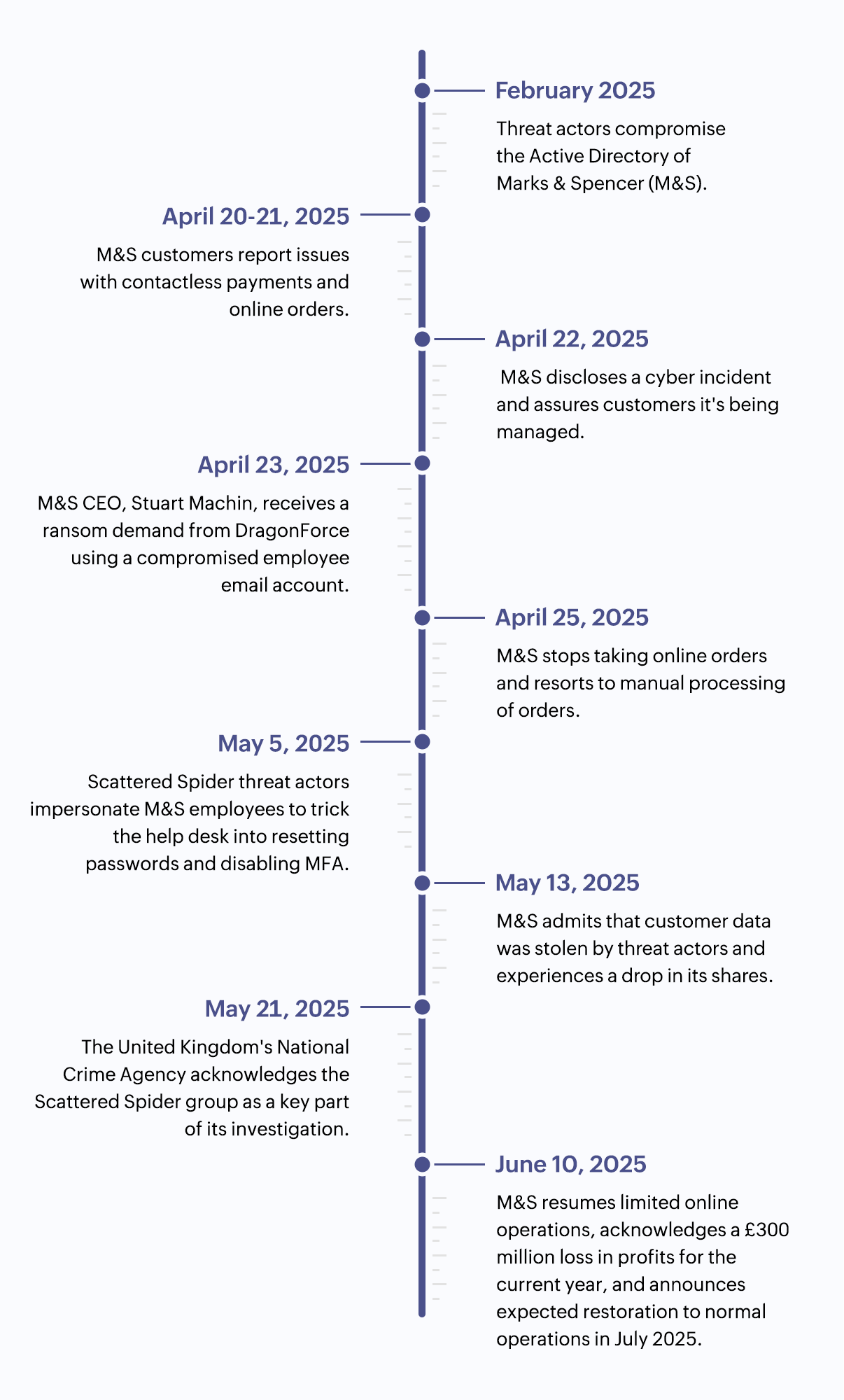
Figure 1: Marks & Spencer ransomware attack timeline
During the Easter weekend 2025, M&S customers reported issues with contactless payments, online orders, and its Click and Collect service in stores. Following this, M&S disclosed the incident via a London Stock Exchange press release (on April 22, 2025) that it had been "managing a cyber incident over the past few days." The very next day, M&S CEO Stuart Machin, received an abusive email from hackers who claimed to have stolen customer data and demanded a ransom payment via a darknet link included in the mail. The hackers seem to have leveraged the DragonForce ransomware-as-a-service model to execute the attack. By April 25, 2025, M&S stopped taking online orders (see Figure 2), resorted to pen and paper to continue business operations, and said that the disruption may last till July.
Image source: BleepingComputer
Figure 2: Marks & Spencer pausing online orders after the ransomware attack
Experts predicted that such a disruption will cost them £300m in lost profit. By May 13, 2025, when the company admitted to having customer data stolen, they were already ceding £43m a week in lost sales and their shares were down by 12% since the attack. The stolen customer data includes names, dates of birth, telephone numbers, home addresses, household information, email addresses, and online order history.
By April 28, 2025, Bleeping Computer reported that while the DragonForce encryptor was deployed on VMWareESXi hosts on April 24, the threat actors may have breached M&S back in February. The attackers—suspected to be in a group of threat actors called Scattered Spider—allegedly exfiltrated the company’s NTDS.dit AD database, which contains hashed credentials, allowing them to escalate privileges and gain widespread access. M&S is reported to be collaborating with various organizations—including the UK’s National Cyber Security Centre, law enforcement, CrowdStrike, and Microsoft—to track threat actor behavior, assess data exposure, conduct forensics, and recover from the breach.
On May 5, 2025, BleepingComputer reported that the Scattered Spider attackers posed as employees or IT personnel, contacting M&S’s service desk to request password resets and even disable MFA. The same report said that such tactics were often employed by the Scattered Spider group. These suspicions were officially acknowledged by the National Crime Agency (NCA) on May 21, 2025, in an announcement stating that Scattered Spider was a key part of their investigation. By June 10, 2025, M&S started taking limited online orders in certain countries, but reiterated that it might be July before they started operating normally. While M&S is yet to specify if or when in July their services will be fully resumed, on July 10, 2025, the NCA announced they have apprehended four suspects believed to be a part of the M&S and Co-op cyberattacks.
How does the Scattered Spider group operate?
The usual modus operandi (M.O.) of the Scattered Spider group—as per the joint cybersecurity advisory from the FBI and CISA—includes the following:
- Social engineering: Actors impersonate IT or help desk staff to deceive employees into granting access or resetting MFA devices via calls, texts, and phishing.
- Credential theft techniques: They rely on phishing, push bombing MFA fatigue, SIM‑swap attacks, and remote access tools to harvest credentials.
- Use of legitimate tools: Once inside, threat actors use authenticated remote-access software and tunneling tools to maintain persistence and move laterally.
However, the Scattered Spider threat actors have refined their approach since this advisory was released. In the M&S attack, they initially began by first compromising the company's AD before using phone-based attacks to bypass MFA and facilitate a full ransomware deployment:
- Early Active Directory compromise: Threat actors gained initial access in February by extracting the NTDS.dit file, enabling offline password cracking.
- Service desk targeting: Instead of technical exploits, they used high-pressure phone-based social engineering aimed at IT support staff to reset MFA and passwords, bypassing technical controls.
- Escalation and encryption: With elevated privileges, they deployed DragonForce ransomware to encrypt VMware ESXi hosts and disrupt operations. While these threat actors typically use BlackCat/ALPHV ransomware (or variants associated with RansomHub and Qilin), they deployed DragonForce ransomware service in the M&S attack, evolving their M.O. further.
Retail sector cybersecurity: Key takeaways for CISOs
To detect and prevent a breach like the one at M&S, it's crucial for CISOs to implement the following measures.
1. Harden help desk security
Why it matters
Scattered Spider bypassed MFA by impersonating employees and convincing help desk agents to reset credentials. This shows how attackers exploit human vulnerabilities to breach even technically protected systems.
Best practices
- Enforce strict help desk identity verification using call-back procedures or secure identity workflows.
- Train help desk personnel and other technical staff to validate identity requests through multi-layered verification before resetting MFA or passwords; alternatively, restrict resets without secondary approval.
- Conduct regular phishing and vishing simulations and provide continuous social engineering awareness training to support teams.
- Implement recommendations provided in the Guide to Securing Remote Access Software to prevent malicious use of remote tools.
2. Secure identity infrastructure, especially your AD
Why it matters
Attackers exfiltrated M&S’s NTDS.dit file—AD’s core credential database—allowing them to crack passwords offline and escalate privileges rapidly.
Best practices
- Enforce phishing-resistant MFA (for example, FIDO2 keys and biometrics).
- Monitor for abnormal access to AD components like NTDS.dit or replication behavior.
- Implement just-in-time access for privileged accounts and enforce the principles of least privilege.
- Use secured admin workstations and separate admin credentials from standard accounts.
- Regularly audit and rotate service account credentials.
3. Strengthen endpoint detection and threat hunting
Why it matters
Scattered Spider remained undetected for weeks, blending in by abusing legitimate tools. Traditional detection tools and techniques are no longer sufficient since they can't detect anomalous behavior from legitimate users and entities.
Best practices
- Leverage UEBA solutions to detect deviations in user behavior and access patterns, and to identify lateral movement and privilege escalation.
- Integrate behavioral analytics (UEBA) into SIEM/XDR platforms for contextual correlation.
- Deploy EDR solutions that can detect fileless and command-line-based attacks. Integrate UEBA, SIEM, and EDR for more effective threat detection.
- Conduct regular threat hunting for anomalous activities in endpoints and cloud workloads.
- Tag and prioritize high-value assets (for example, AD servers and POS systems) for continuous monitoring.
4. Control third-party and supply chain access
Why it matters
Retail environments rely on multiple external partners and SaaS vendors, expanding the attack surface through loosely monitored integrations.
Best practices
- Maintain an up-to-date third-party risk inventory.
- Enforce Zero Trust principles across all vendor access.
- Continuously assess third-party compliance with your security policies (for example, MFA, encryption).
5. Build a proactive incident response and breach communication strategy
Why it matters
M&S’s delayed threat detection impacted customer trust and business operations. Their initial disclosure of the attack was also vague, using terms like "cyber incident" instead of admitting that it was a ransomware attack. This emphasizes the need for rapid containment and transparent communication during security incidents in the retail industry.
Best practices
- Run red team and tabletop exercises focused on identity-based and social engineering attacks.
- Pre-draft internal and external communication templates for breach scenarios.
- Establish clear breach disclosure timelines to meet regulatory and reputational requirements.
6. Maintain segmented, tested backups
Why it matters
Ransomware actors like Scattered Spider often delete or encrypt backup data before launching encryption payloads. If backups are accessible from the main network, they’re at risk.
Best practices
- Maintain encrypted, immutable, and offline backups of critical systems and Active Directory.
- Segment backup systems from production environments using access controls.
- Test disaster recovery procedures regularly against ransomware-specific scenarios.
7. Align cybersecurity with business continuity
Why it matters
The M&S ransomware attack disrupted core operations—shutting down online ordering, payment systems, and customer service—resulting in losses exceeding £300 million. Apart from data loss, operational downtime is yet another damaging consequence of breaches in the retail industry.
Best practices
- Integrate cybersecurity and business continuity planning to ensure resilience across digital and operational systems.
- Prioritize ransomware recovery in disaster recovery and business impact assessments.
- Ensure redundancies for mission-critical services (e.g., POS, order fulfillment, payment processing).
- Conduct joint incident simulations involving IT teams, operations personnel, and executive leadership to align recovery objectives.
Frequently asked questions
The attacks on M&S has been attributed to the Scattered Spider group, known for advanced social engineering tactics and targeting of identity infrastructure, especially in large enterprises This group has also claimed responsibility for attacks on Harrods and Co-op.
M&S suffered Active Directory compromise. Threat actors reportedly exfiltrated the NTDS.dit Active Directory file, enabling them to crack password hashes offline and escalate privileges. They also used social engineering to trick M&S IT help desk staff into resetting MFA and credentials.
The stolen information includes names, dates of birth, addresses, telephone numbers, and purchase histories, but no financial data or passwords seem to be leaked. The extent of exfiltration is still under investigation.
M&S experienced financial losses estimated at £300 million, and its market value fell by over £500 million. With the company issuing notice that normal operations may resume some time in July, the actual loss could be more.
M&S paused online orders in response to the ransomware attack that compromised critical parts of its IT infrastructure in April 2025. To contain the breach and prevent further damage, the company proactively shut down systems supporting e-commerce operations, Click & Collect, and returns processing.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement the principles of least privilege with AD360. To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect compromised credentials, reduce breach impact, and lower compliance risk exposure with Log360. To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
