On this page
Digital payment fraud caused $32 billion in losses in 2023, and businesses are expected to lose $343 billion more between 2023 and 2027.
As digital finance ecosystems expand through online banking, FinTech apps, and modern payment platforms, the attack surface for cybercriminals grows wider. To safeguard sensitive data and ensure transaction integrity, enterprises need advanced security measures like SIEM and IAM that deliver real-time visibility, detection, and control.
The convergence of digital finance and cyber risk
The rapid growth of digital finance has created a highly interconnected ecosystem of banks, FinTech platforms, and third-party payment services. While this expansion enables seamless transactions, it also exposes organizations to a widening cyber risk threat landscape. Attackers are increasingly targeting digital payment security gaps to steal sensitive financial and personal data. Weaknesses in online payment security can lead to large-scale fraud, regulatory fines, and loss of customer trust. Enterprises must therefore adopt proactive defenses that combine real-time monitoring, identity governance, and compliance-driven controls to safeguard the digital finance ecosystem.
The foundation: Protecting PII and PCI data across platforms
In today’s digital payment ecosystem, protecting sensitive data such as personally identifiable information (PII) and payment card information (PCI) has become a critical priority. PII includes customer names, addresses, and account details, while PCI covers card numbers, CVV codes, and transaction credentials. Cybercriminals often target these datasets because of their high resale value in underground markets. A single breach exposing PII or PCI can lead to identity theft, financial fraud, and long-term reputational damage for businesses. Non-compliance with the PCI DSS or other data protection regulations can also result in hefty fines and legal liabilities.
Moreover, the interconnected nature of the digital payment ecosystem amplifies risks, as attackers exploit vulnerabilities in third-party providers and integrations. Phishing, credential stuffing, and malware remain common methods used to steal PII and PCI from organizations. Even a minor lapse in data security can disrupt customer trust, which is difficult and costly to rebuild. This makes it essential for enterprises to implement strong encryption, continuous monitoring, and access controls. Utimately, safeguarding PII and PCI is not just about compliance; it’s about ensuring trust and resilience in the digital payment ecosystem.
Identity at the core: Credential abuse and account takeovers
When it comes to the security of digital payments, credential abuse has emerged as one of the most pressing risks. Attackers exploit weak or reused passwords, phishing campaigns, and stolen login data to launch account takeover attacks. Once inside, they can initiate fraudulent transactions, steal sensitive customer information, or move laterally within systems.
Vulnerable points often include online banking portals, FinTech apps, e-commerce platforms, and third-party integrations.The growing use of mobile wallets and APIs further expands the attack surface for credential-based threats.
For customers, account takeover can mean drained accounts and identity theft; for enterprises, it leads to chargebacks, financial losses, and reputational damage. Credential abuse is especially dangerous because it often bypasses traditional security tools by using legitimate login credentials. Attackers also employ bots and automation to scale these attacks, making detection more challenging.
To counter these threats, enterprises must strengthen authentication, monitor login anomalies, and adopt Zero Trust access controls. Safeguarding against credential misuse and unauthorized account access is essential to maintain confidence in digital transactions and strengthen the overall security framework of payment systems.
Transaction layer security: Defending wallets and contactless payments
The rise of digital wallets and contactless payment methods has transformed convenience but also expanded the attack surface for cybercriminals. Weak online payment security controls expose users to risks like phishing, SIM swapping, and manipulator-in-the-middle attacks. Inadequate mobile payment security measures make smartphones a prime target for malware and unauthorized access.
Threats such as credential abuse allow attackers to exploit stolen login data to gain access to digital wallets. This often leads to account takeover, enabling fraudsters to perform unauthorized purchases or transfer funds. Vulnerabilities in NFC technology, insecure apps, or poorly protected APIs further increase exploitation risks.
The speed and anonymity of contactless transactions make fraudulent activity harder to detect in real time. For businesses, breaches in mobile or contactless systems result in financial losses, regulatory scrutiny, and erosion of customer trust. Customers, on the other hand, face identity theft, drained accounts, and long-term financial consequences. Ensuring strong online payment security and mobile payment security is therefore essential to protect digital wallets and contactless payments from evolving threats.
Cross-platform fraud protection
In today’s interconnected financial landscape, attackers rarely confine themselves to a single platform. A breach in a SaaS billing system can expose customer PII or PCI data, which is then weaponized to fuel credential stuffing attacks against online banking portals. Once attackers gain entry, the same stolen credentials or payment data can be repurposed to exploit digital wallets and contactless payment systems, completing the fraud cycle.
This cross-platform fraud thrives on weak identity practices, poor monitoring across ecosystems, and the reuse of credentials. For example, a compromised billing account may enable fraudulent invoicing, while the same login details open doors to unauthorized banking transactions. In another scenario, banking portal breaches provide stolen card details that are instantly injected into digital wallets for high-velocity, hard-to-trace payments.
By exploiting these silos, attackers orchestrate multi-vector attacks:
Billing breach → Credential stuffing → Fraudulent wallet use
These attacks bypass traditional, platform-specific defenses. CISOs must therefore design unified monitoring, identity-first security, and fraud intelligence strategies that connect the dots across all digital finance touchpoints.
The regulatory landscape and compliance as security drivers
The regulatory landscape has become a key driver of financial security, compelling organizations to adopt stronger controls beyond basic compliance. Frameworks such as the PCI DSS, the PSD2, the GDPR, and regional mandates like the RBI guidelines set minimum standards for protecting PII, PCI data, and digital transactions.
These requirements push enterprises to encrypt data, implement strong authentication, and monitor high-risk activities continuously. Compliance also fosters accountability by enforcing regular audits, breach disclosures, and access governance. While often seen as a burden, regulations serve as a catalyst for building resilience against evolving fraud tactics. In practice, they align security strategy with trust, making compliance both a shield and a market differentiator.
Features of SIEM that help enhance the security posture
The following are SIEM features that help:
| Feature | Benefit | Financial benefit | Example scenario | What it resolves |
|---|---|---|---|---|
| Centralized log collection | Provides a unified view of security events across billing, banking, and wallets. | Reduces the need for multiple monitoring tools, which lowers operational costs. | Logs from SaaS billing show anomalous invoice changes correlating with failed MFA attempts in online banking. | Missed attack patterns due to siloed monitoring |
| Real-time threat detection | Identifies suspicious activities instantly (e.g., credential stuffing or unusual transaction velocity). | Prevents fraud losses by stopping attacks mid-stream. | The solution detects 1,000 failed login attempts in a short span from multiple IPs against banking portals. | Delayed response to brute-force attacks and credential stuffing |
| UEBA | Learns normal user behavior and flags anomalies. | Reduces fraud reimbursements by detecting insider misuse and account takeovers early. | A wallet user suddenly initiates large overseas transactions inconsistent with their history. | Insider fraud, account takeovers, and privilege misuse |
| Threat intelligence integration | Enriches alerts with global attack data (e.g., known malicious IPs). | Cuts investigation time, reducing SOC workload and costs. | The solution detects login attempts from IPs linked to dark web credential dumps targeting online banking. | Blind spots to evolving external threats |
| Automated incident response (SOAR integration) | Executes predefined playbooks (e.g., lock account, block IP, or alert CISO). | Minimizes downtime, which prevents revenue loss. | The SIEM solution auto-suspends the account before any anomalous wallet transaction occurs. | Slow, manual response to fast-moving fraud |
| Compliance reporting | Generates audit-ready reports for the PCI DSS, the GDPR, and more. | Avoids regulatory fines and reduces compliance audit costs. | The solution prepares real-time PCI DSS compliance dashboard for SaaS billing systems. | Gaps in compliance reporting that can lead to penalties |
| Cross-platform threat correlation | Connects fraud patterns across billing, banking, and wallets. | Prevents cascading fraud losses across ecosystems. | The solution links a billing account breach to credential stuffing in a banking app, which led to wallet misuse. | Multi-vector fraud that evades isolated defenses |
Features of IAM that help enhance the security posture
The following are IAM features that help:
| Feature | Benefit | Financial benefit | Example scenario | What it resolves |
|---|---|---|---|---|
| MFA | Strengthens login security across billing, banking, and wallets. | Prevents fraud-related chargebacks and customer loss. | Even if stolen credentials are used in credential stuffing, the second factor stops unauthorized logins. | Credential theft and brute-force login attempts |
| Adaptive or risk-based authentication | Adjusts authentication based on user context (e.g., location, device, and time). | Reduces friction for genuine users while lowering fraud costs. | A banking login attempt from a new country triggers step-up authentication. | Sophisticated fraud using stolen but valid credentials |
| PAM | Controls and monitors high-level access to billing databases and payment APIs. | Prevents insider fraud and data leaks, which avoids reputational damage. | Restrict admin access to PCI data in SaaS billing only during working hours. | Insider threats and privilege abuse |
| Single sign-on (SSO) | Simplifies secure access across multiple platforms. | Reduces help desk costs for password resets. | Employees use one identity to securely access both billing and wallet management apps. | Password fatigue leading to weak or reused passwords |
| Life cycle management (joiner-mover-leaver) | Automates provisioning and deprovisioning of user access. | Prevents license wastage and reduces fraud risk after employee exits. | Ex-employees' access to SaaS billing is automatically revoked on exit. | Orphaned accounts vulnerable to misuse |
| RBAC | Grants only necessary access based on roles. | Limits fraud exposure, which reduces breach impact costs. | Call center agents can view billing info but cannot modify payment methods. | Excessive permissions leading to data misuse |
| Federated identity management | Securely connects third-party FinTech apps with enterprise identity systems. | Enables safe integrations, which reduces compliance risks. | Customers access wallets using banking credentials without storing sensitive data in multiple places. | Weak authentication in third-party integrations |
Building a unified defense with SIEM and IAM
The following is how SIEM and IAM together can help enhance the security posture of a digital finance ecosystem.
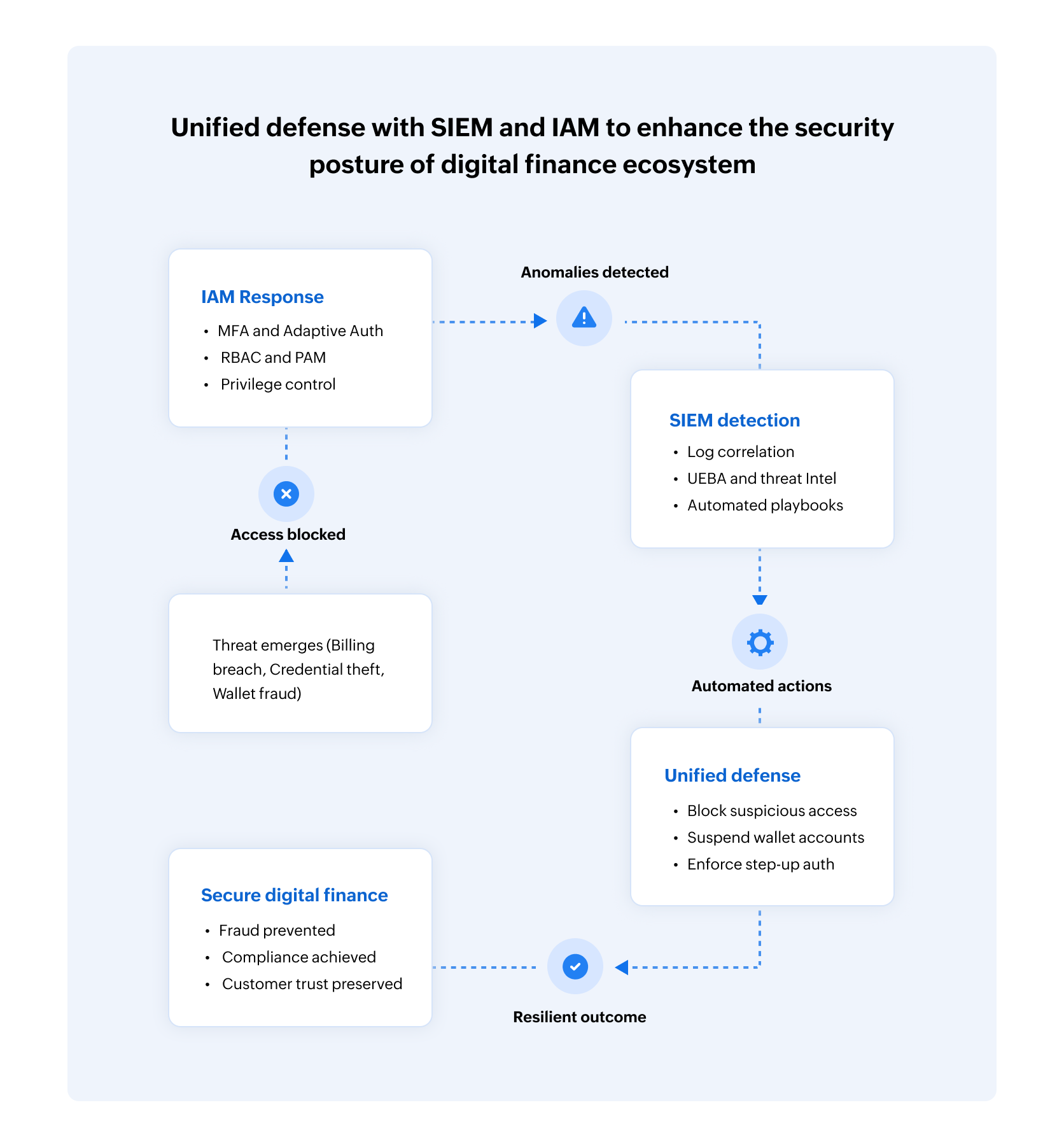
Figure 1: The unified defense of SIEM + IAM.
Strategic priorities for CISOs in protecting digital finance
The following are some security policies CISOs should consider:
- Identity-first security: Enforce MFA, adaptive authentication, and least-privilege access to reduce credential-related fraud.
- Centralized monitoring with SIEM: Aggregate and correlate logs across billing, banking, and wallets to detect anomalies in real time.
- Third-party and API risk management: Secure FinTech integrations with strict IAM policies and continuous API monitoring.
- Data protection and compliance alignment: Encrypt PII and PCI data, and ensure ongoing compliance with the PCI DSS, the PSD2, the GDPR, and regional mandates.
- Cross-platform incident response: Establish unified playbooks that trigger defense actions across all connected financial systems.
- AI- and ML-driven fraud analytics: Deploy behavioral analytics to detect unusual transactions and evolving fraud tactics.
- Security awareness and culture: Train employees and educate customers to recognize threats like phishing and fraudulent apps.
- Zero Trust architecture: Apply continuous verification of every user, device, and transaction to eliminate implicit trust.
Future-ready digital finance security
Future-ready digital finance security demands a unified, proactive approach that goes beyond patching individual risks. By combining SIEM’s real-time visibility with IAM’s identity-first controls, enterprises can create a resilient defense that adapts to evolving fraud tactics. Zero Trust principles, AI-driven analytics, and cross-platform monitoring will be central to safeguarding data, identities, and transactions. For CISOs, the priority lies in balancing customer convenience with uncompromising protection and compliance. A secure digital finance ecosystem not only prevents financial and reputational loss but also builds lasting customer trust. In the end, security becomes more than a safeguard; it is the foundation for sustainable growth in digital finance.
Related solutions
ManageEngine Log360 is a SIEM solution that combines DLP, CASB, ML, and MITRE ATT&CK® mapping to deliver real-time threat detection, automated response, streamlined incident management, and compliance across hybrid IT environments.
Sign up for a personalized demoManageEngine AD360 is a unified IAM solution that simplifies identity, access, and security management across on-premises and cloud platforms with features like user provisioning, SSO, self-service password management, and auditing.
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
