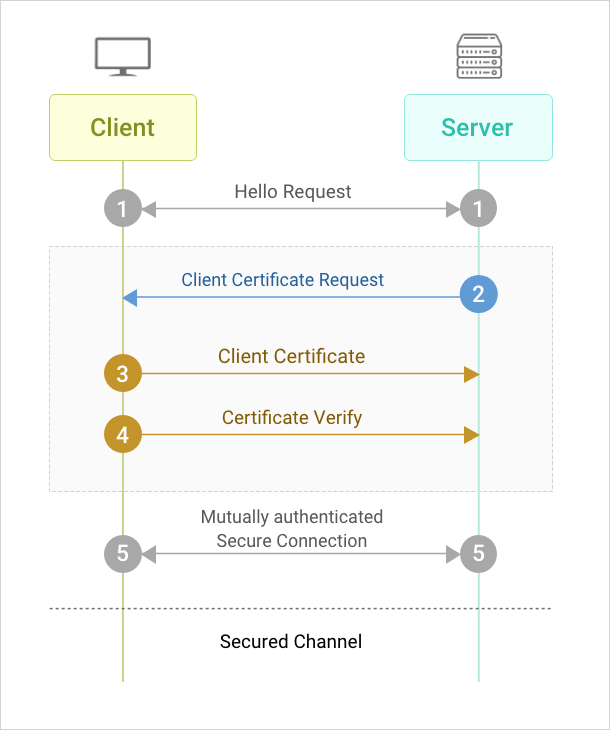
Endpoint Central server uses client certificate authentication to authenticate agent installed computers that try to establish a connection with the server. Each agent will have a unique certificate and a corresponding private key signed by the server's trusted root certificate authority. Upon the successful validation of the certificate and the key, the server will connect to the agent. If the validation fails, the connection will be dropped. This is done to ensure security and keep away unauthorized clients from connecting to the server.
Note:Client certificates are different from server certificates. A server certificate is provided by the server at the start of a session, which is used by the agent to authenticate the server's credibility. A client certificate, on the other hand, is provided by the agent during the SSL handshake and is used by the server to authenticate the agent.
Client certificate authentication should be manually enabled by navigating to Admin tab > Security and Privacy > Security Settings. This option is available only on Endpoint Central build 100647 or higher.
Note:
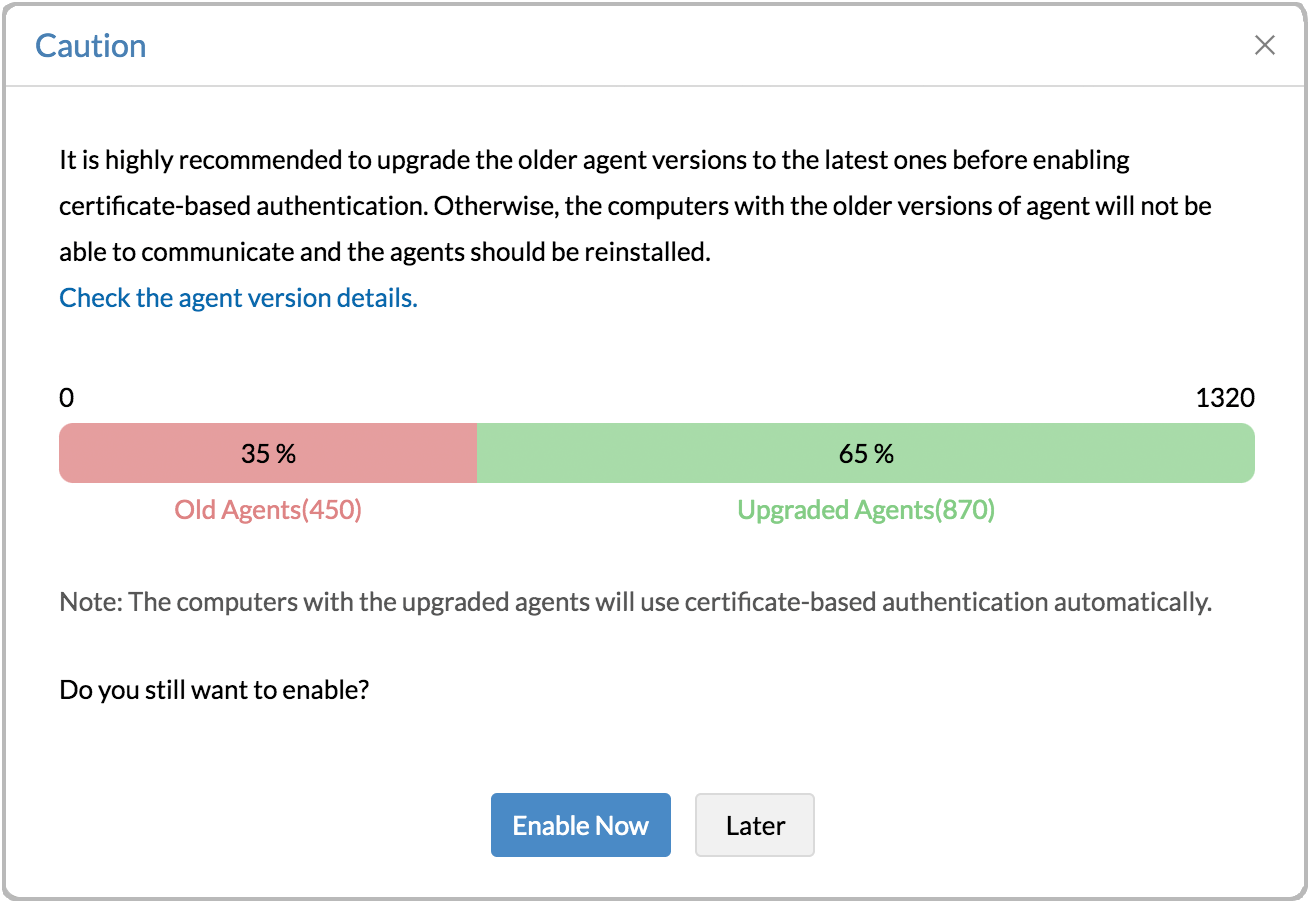
When you enable this authentication, you will receive the number of agents that are not upgraded to the above mentioned agent version. If you fail to upgrade, those agent-installed computers will no longer be managed under Endpoint Central.
A client certificate restricts access to the agent authorized with certificates. Assuming that your certificates are managed and distributed securely, it is difficult for an unauthorized client to connect to the server since you need more than just a username and password.
There are some limitations while using client certificate authentication, such as:
Client certificate authentication via HTTPS TLS handshake is not possible if an SSL-intercepting proxy server is configured between the agent and the server because the proxy breaks the HTTPS connection and connects on behalf of the agent. Therefore, if client certificate authentication is enabled, an SSL-intercepting proxy server cannot be configured for the distribution server and vice versa.
When client certificate is used for authentication between agent and central server communication, and the central server is behind a firewall which has a certificate inspection policy enabled or a load balancer, the agent server communication will fail.