- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
Multi-factor Authentication
Multi-factor authentication (MFA) is the process of using multiple factors of authentication to verify a user's identity before giving them access to a particular resource. Guarding resources using only a single factor—traditionally usernames and passwords—leaves them vulnerable to breaches. Adding other factors of authentication grants ironclad protection for resources and reduces the likelihood of a cyberattack.
MFA plays an integral role in identity and access management (IAM), helping organizations take a step closer to creating a Zero Trust security framework. Adding other factors of authentication grants ironclad protection for resources and reduces the likelihood of a cyberattack. For example, enabling Active Directory MFA helps secure your core identity infrastructure. Similarly, Endpoint MFA reinforces security at the point of access through MFA for Windows logins, RDPs, and VPNs.
How does multi-factor authentication work?
An MFA solution works by verifying users using authentication factors other than their usernames and passwords. These authentication factors may be something they know (knowledge factor), something they have (possession factor), and something they are (inheritance factor).
Knowledge factor:
As the name suggests, the knowledge factor includes information that only the authorized user would know. Some common examples are passwords, PINs, passphrases, and answers to security questions.
Security questions are not usually recommended since attackers might easily crack them.
Possession factor:
Here, authentication is performed with something the user possesses, like a mobile phone, a physical token, or a smart card. For example, it could be a code generated via an app on the phone or communicated to the user through an automated call.
Inheritance factor:
The inherence factor, being the most secure of the three factors, involves verifying identities with the help of inherited biometric means, such as fingerprint scanning, facial scanning, retinal scanning, and voice recognition.
Emerging factors:
In recent times, the location factor and the time factor have also gained importance. The location factor verifies whether subsequent access attempts by a user are not from two completely different, impractical locations. The time factor checks the user's access request time and challenges them with additional authenticators if the access is requested at an odd hour.
Expert tips from NIST SP 800-63
While enterprises can select an MFA software based on their organizational policy and device support, they should refer to established regulations and standards like NIST SP 800-63 to ensure that the selected authentication factors provide adequate security for their specific risk profile. NIST Special Publication 800-63 establishes three Authenticator Assurance Levels (AAL) that organizations can implement based on their security requirements and risk tolerance. Each level builds upon the previous one, requiring progressively stronger authentication methods.
| Assurance level | Description | Authentication factors required |
|---|---|---|
| AAL1 | Basic security for low-risk applications. Single-factor authentication with some verification of the authenticator. | Single-factor authentication (typically password with complexity requirements, or biometric with liveness detection) |
| AAL2 | Enhanced security requiring two different types of authentication. Suitable for moderate-risk applications involving personal information. | Multi-factor authentication using two different factor types (e.g., password + SMS code, or password + biometric) |
| AAL3 | High security requiring hardware-based authentication. Used for high-risk applications involving sensitive data or critical operations. | Multi-factor authentication with at least one hardware-based phishing-resistant authenticator, such as FIDO2 passkeys. |
Why is multi-factor authentication important and why should you use it?
Securing resources using just passwords does only the bare minimum to secure identities. There are numerous attacks that a hacker can use to breach passwords—like brute-force attacks, phishing attacks, dictionary attacks, and web app attacks—which is why it's important to implement additional layers of authentication to secure resources.
Users happen to be the weakest links of an organization's security chain. They might unknowingly choose weak passwords, repeat passwords for multiple resources, store passwords in plain sight, or retain the same password for an extended duration. Implementing MFA protects against these user vulnerabilities. So, even if an unauthorized person obtains a user's password, they still cannot gain access to the privileged resources since they would need additional information to complete the subsequent MFA methods.
Privileged accounts, such as admin or C-level executive accounts, are often prone to attacks. If an attacker gets hold of the credentials of any of these accounts, they’ll have access to the most important data and resources in the network, and the repercussions could be irreversible. To reduce risk, organizations must protect their high-risk accounts with additional layers of security.
Deploying an MFA software not only helps organizations fortify access, but also helps them comply with data regulatory norms, like the PCI DSS, the GDPR, NIST 800-63B, SOX, and HIPAA.
According to global statistics:
- 32% of black hat hackers admit privileged accounts are their number one way to hack systems.
- 95% of cybersecurity breaches are due to human error.
- 43% of cyberattacks target small businesses.
- Hackers create 300,000 new malware variants daily.
- Every 39 seconds, a hacker tries to steal data.
- The average cost of a data breach is approximately $3.9 million.
Source Web tribunal, Cybint
What is the difference between 2FA and MFA?
2FA
Two-factor authentication (2FA) is quite synonymous to MFA. However, as the name suggests, 2FA includes a total of only two authentication factors, whereas MFA does not have any restriction on the number of authentication factors involved.
MFA
MFA is more widely used, as it secures resources better with multiple authentication methods. But for a legitimate user, having to prove their identity daily using multiple authentication methods can cause MFA fatigue. For simple and intelligent MFA, AI and machine learning have been integrated with MFA, birthing adaptive MFA.
What are the types of MFA?
Here are some common types of MFA that enterprises can benefit from:
Adaptive MFA
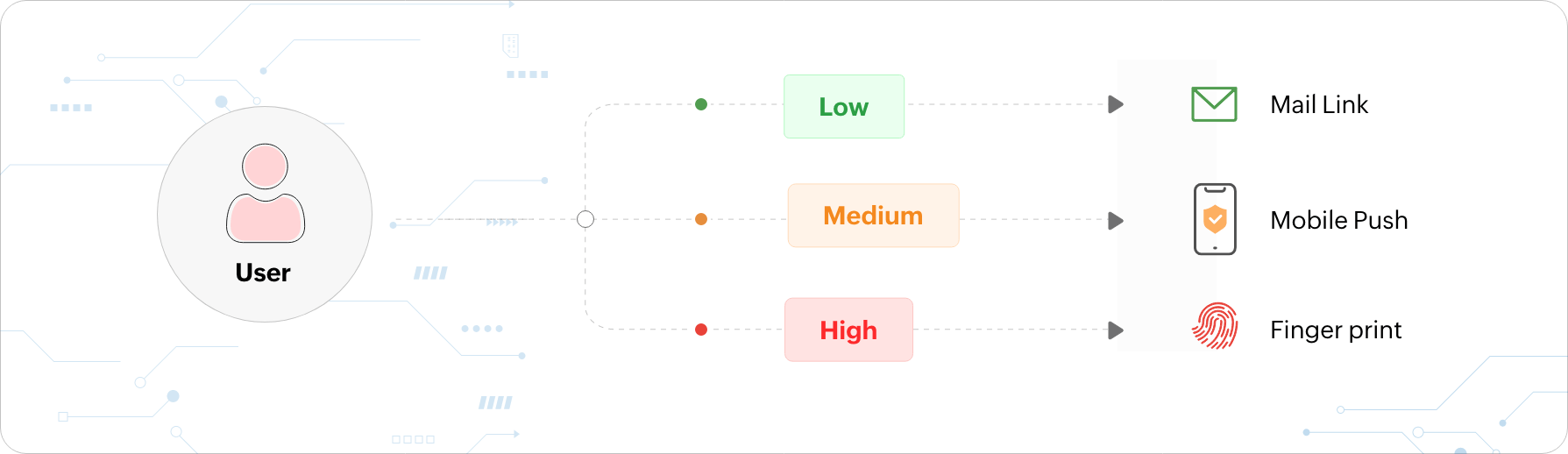
Adaptive MFA, otherwise known as risk-based MFA, provides users with authentication factors that adapt each time a user logs in depending on the AI-determined risk level of the user based on contextual information. Contextual information includes the following:
- The number of consecutive logon failures
- The user account and user role category
- The physical location (geolocation) of the user requesting access
- The physical distance (geo velocity) between consecutive logon attempts
- The resource to which access is requested
- The type of device
- Third-party threat intelligence data
- The day of the week and the time of the day
- The operating system type
- The IP address
The authentication factors presented to the user are based on the risk level that is calculated using the above contextual factors. For instance, consider a user trying to log in to their work machine at an untimely hour while on a vacation. The user behavior analytics (UBA) tool recognizes that the user's location and time of access are different, and they are automatically prompted with additional authentication factors to prove their identity.
When user login conditions are checked using AI and no risk is detected, the MFA process can be bypassed for the user. Sometimes, if the user's activity seems suspicious, they can also be denied access to the requested resource.
Phishing-resistant MFA
Phishing-resistant MFA addresses the vulnerabilities of weaker MFA methods by using cryptographic protocols that create a binding between the authentication factor and the specific service being accessed. Technologies such as FIDO2/WebAuthn, smart cards, and hardware security keys implement public-key cryptography and challenge-response mechanisms, where the user's device proves possession of a private key without transmitting sensitive information. This method effectively counters real-time phishing and man-in-the-middle attacks because the cryptographic binding ensures that credentials generated for one service cannot be replayed or used for another, even if an attacker intercepts the authentication session.
Passwordless MFA
Passwordless MFA eliminates traditional passwords while maintaining multiple authentication factors through biometrics, hardware tokens, mobile push notifications, or cryptographic keys. This approach addresses fundamental password weaknesses like reuse and weak complexity while streamlining user experience. Common setups include biometrics paired with push notifications or cryptographic challenges, and hardware-based authentication that combines biometric verification with secure elements. By removing passwords entirely, organizations significantly reduce their attack surface while improving user productivity and reducing help desk burdens associated with password management.
What are the pros and cons of multi-factor authentication?
| Pros | Cons |
|---|---|
|
|
Best practices for implementing MFA in your enterprise
Selecting an authentication method
- Employ strong authentication methods: Prioritize phishing-resistent FIDO2 passkeys and app-based TOTP authenticators. Avoid weak methods like security questions and SMS codes, which are prone to phishing and SIM-swapping attacks.
- Implement contextual authentication: Adjust authentication requirements based on IP address, device, location, and time of access, and behavior patterns.
User adoption strategy
- Provide comprehensive training: Raise end-user awareness of the need for MFA. Address user concerns and demonstrate MFA benefits.
- Offer multiple authentication options: Enable authentication methods based on user device policy and risk-level. Accommodate different preferences and accessibility needs.
- Streamline enrollment process: Encourage user enrollment using reminder emails and login scripts. Provide clear documentation detailing the enrollment process.
Technical implementation
- Provide backup options: Implement backup recovery codes to help end-users complete authentication when their authentication device isn't available.
- Monitor usage patterns: Track authentication attempts using audit reports and detect suspicious activities.
Choosing the right MFA solution: ManageEngine ADSelfService Plus
ManageEngine ADSelfService Plus is an identity security solution to ensure secure and seamless access to enterprise resources and establish a Zero Trust environment. With capabilities such as adaptive multi-factor authentication, single sign-on, self-service password management, a password policy enhancer, remote work enablement, and workforce self-service, ADSelfService Plus provides your employees with secure, simple access to the resources they need.
The solution offers comprehensive, context-aware Endpoint MFA to secure all points of contact in your enterprise. Its Active Directory MFA capability significantly lowers the attack surface by protecting AD-integrated access points with advanced authentication methods such a biometrics, hardware tokens, and TOTPs.
Here are the multi-factor authentication capabilities ADSelfService Plus offers:
MFA for Windows, macOS, and Linux systems
Secure local and remote logins by enforcing MFA directly at the OS level across Windows, macOS, and Linux machines. ADSelfService Plus prompts users for additional verification methods before granting desktop access.
MFA for RDP
Add an extra layer of protection to Remote Desktop Protocol connections by requiring users to authenticate with additional factors during both RDP client and server authentication. This prevents unauthorized remote access even with compromised passwords.
MFA for VPN
Integrate MFA into VPN login flows to authenticate users accessing the network remotely. Compatible with popular VPN solutions, this ensures only verified users can establish secure tunnels into the corporate network.
OWA MFA
Protect access to OWA and Exchange Admin Centre by configuring MFA prompts during enterprise email access. This helps prevents phishing and session hijacking attacks targeting email accounts.
MFA for UAC
Enforce multi-factor authentication for User Account Control (UAC) elevation prompts on Windows machines. This ensures that privileged actions like software installation or system changes require additional identity verification, reducing the risk of misuse or privilege escalation.
MFA for enterprise applications
Enable MFA for cloud and on-premises business applications accessed via single sign-on (SSO). ADSelfService Plus acts as an identity provider, enforcing MFA policies before granting app access.
Additionally, the solution also caters to unique authentication scenarios such as offline MFA for on-the-go users away from the network and device-centric MFA to protect business-critical machines accessed by multiple users.
These are achieved using the following MFA methods
- Biometric authentication (fingerprint or facial recognition)
- FIDO2 passkeys
- Duo Security
- RSA SecurID
- Microsoft Entra ID MFA
- RADIUS
- Microsoft Authenticator
- Google Authenticator
- YubiKey Authenticator
- Email verification
- TOTP using the native app
- SMS verification
- Custom TOTP authenticators
- Zoho OneAuth TOTP
- Push notifications
- QR-code-based authentication
- SAML authentication
- Smart card authentication
- Security questions and answers
- AD-based security questions
Top benefits of deploying ADSelfService Plus for MFA
- Granular MFA configuration: Apply tailored MFA settings to specific domains, OUs and groups for fine-grained user access control.
- Assured user enrollment: Guarantee user onboarding with self-service or admin-enforced enrollment, without disrupting user productivity.
- Conditional access: Trigger MFA based on access factors like IP address, device type, geolocation, and time of access for contextual authentication
- Backup verification codes: Empower users to generate and securely store backup codes for authentication when primary methods are unavailable.
- Comprehensive MFA reports: Gain insights into authentication activity, success or failure trends, and user enrollment with detailed audit-ready reports.
FAQs
MFA stands for multi-factor authentication. It simply means verifying a user's identity using multiple authentication factors, apart from the traditional and less secure username and password authentication method. MFA can be used to guard user access to any type of resource in the network.
Signing into your Gmail account from a new device is a good example to highlight the MFA process. Upon signing into your Google account from a new device, you are asked to verify your identity either using verification codes sent to your email ID or through TOTPs in addition to entering your password. Once your identity is verified, you are logged in. This sums up the MFA verification process that Google has enabled to secure user accounts.
MFA can be used to fight against common yet powerful cyberattacks like credential stuffing, dictionary attacks, brute-force attacks, reverse brute-force attacks, phishing, and man-in-the-middle attacks.
Changing passwords alone regularly without using MFA does not stop hackers from stealing passwords. They can still use a password that was stolen through advanced hacking techniques to barge into the system. Instead, when MFA is used, hackers have no use for a stolen password since there will be other authentication factors that they will have to pass through to gain access to the resources.
Implementing MFA techniques in your business is highly recommended to improve security in your networks. The username and password method of authentication, as outdated as it is, cannot withstand today's advanced cyberattacks on its own. MFA secures your organizational resources and gives the right access to the right individuals. It helps create a Zero Trust environment within your business.
ADSelfService Plus single-handedly takes care of all your MFA needs with features like adaptive authentication, conditional access, and passwordless authentication. Start a free trial
With MFA in place, your organization can meet various regulatory compliance standards including NIST SP 800-63B, PCI DSS, SOX, and HIPAA.
Conditional access is taking authentication decisions to verify a user's identity based on a few pre-configured conditions. That is, users are provided with authentication factors depending on whether certain set conditions are fulfilled or not. An example of a condition would be verifying a user with an additional authentication factor if they have requested resource access from a geolocation that is different from the configured ideal geolocation.
Adaptive MFA utilizes AI to calculate the risk level of users, based on which relevant authentication factors are provided to them for identity verification. This risk level is calculated based on users' contextual information, such as the number of consecutive logon failures, the physical location of the user requesting access, and the type of device used. Adaptive MFA is effective in creating the ultimate Zero Trust environment.










