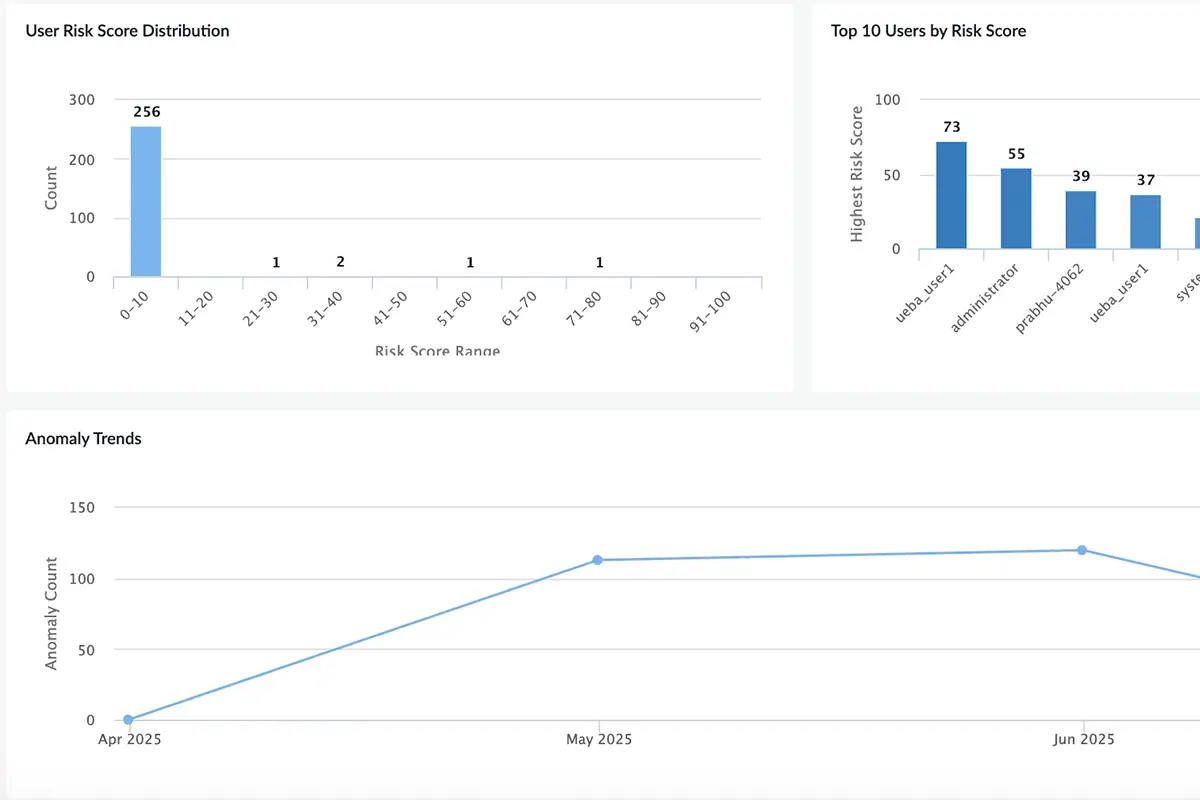
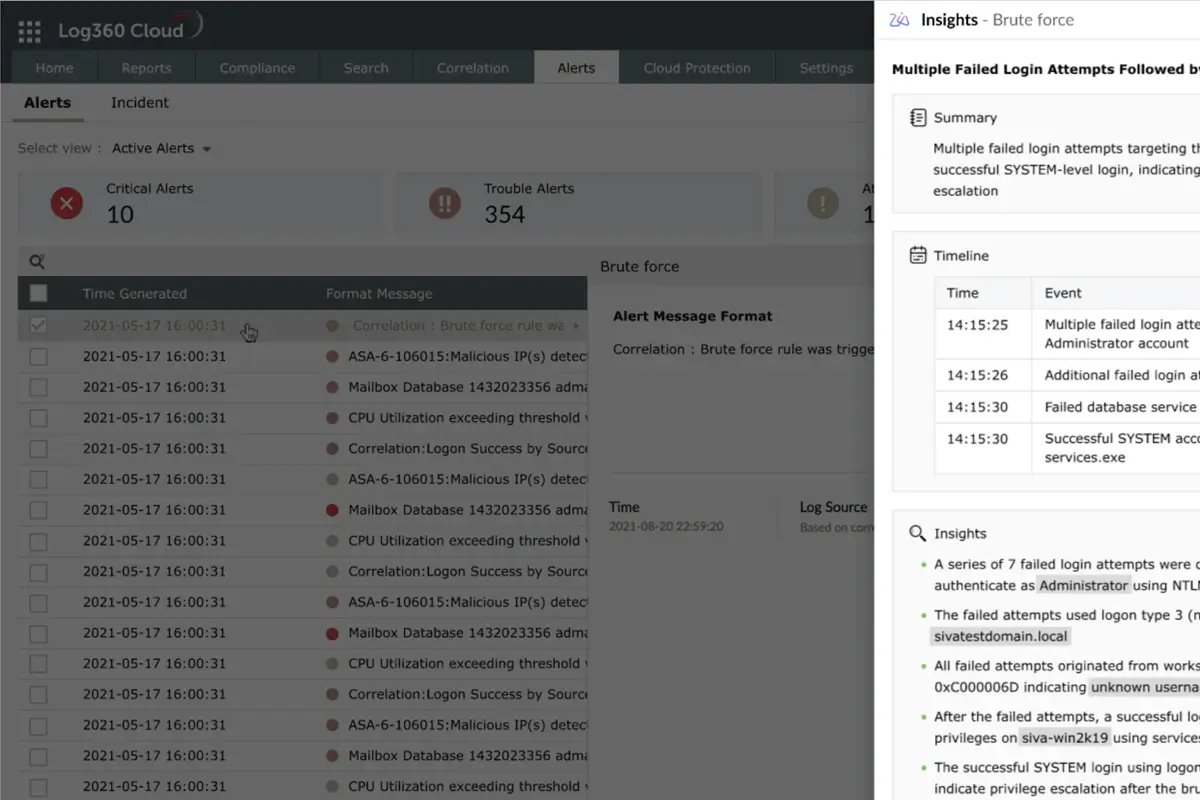
Example: Suspicious bulk file activity
This detection logic identifies unusual file modification activity using Log360’s anomaly-based rule set, which correlates behavioral deviations across users, hosts, and file types. It is mapped to the MITRE ATT&CK framework techniques for Defense Evasion (TA0005) and Privilege Escalation (TA0004).
Example: Excessive software update attempts
This detection logic identifies anomalous software update activity using Log360’s anomaly-based rule set, which correlates deviations across users, hosts, and update patterns. It is mapped to the MITRE ATT&CK framework techniques for Defense Evasion (TA0005) and Privilege Escalation (TA0004).
Abnormal password change patterns
The detection logic used for identifying this activity is part of Log360's comprehensive anomaly rule library, which is mapped to the MITRE ATT&CK framework (Defense Evasion (TA0005), Privilege Escalation (TA0004), and Modify Authentication Process (T1556.001).