NIST compliance means adhering to standards or rules set by the National Institute of Standards and Technology (NIST) to secure information systems used by federal agencies. These standards or rules, known as Federal Information Processing Standards (FIPS), provide guidelines and controls for protecting sensitive data and systems. NIST develops these standards to ensure consistency and security across government operations. Compliance involves implementing recommended security measures outlined in NIST's Special Publications (SP) to safeguard against cyber threats and meet regulatory requirements effectively. This is often part of a comprehensive NIST compliance checklist and verified through a NIST compliance audit to ensure adherence to NIST compliance standards.
Firewall Analyzer's out-of-the-box reports helps you in developing, configuring and managing firewall policies that are abiding to the industry best practice guidelines on security control - the NIST 800-53 Version.
NIST SP 800-53 comprises guidelines and standards established by the National Institute of Standards and Technology (NIST). They address critical areas such as mobile and cloud computing security, insider threats, application security, and supply chain integrity. These guidelines are organized into 18 distinct families, including access control, audit and accountability, and configuration management. They advocate a structured approach to risk management through compliant controls. They have also introduced the concept of security control baselines to address prevalent threats in information systems. Implementing these controls effectively can be part of Firewall NIST compliance and aligns with Firewall best practices NIST.
| Rules | Description | How Firewall Analyzer meets requirement |
|---|---|---|
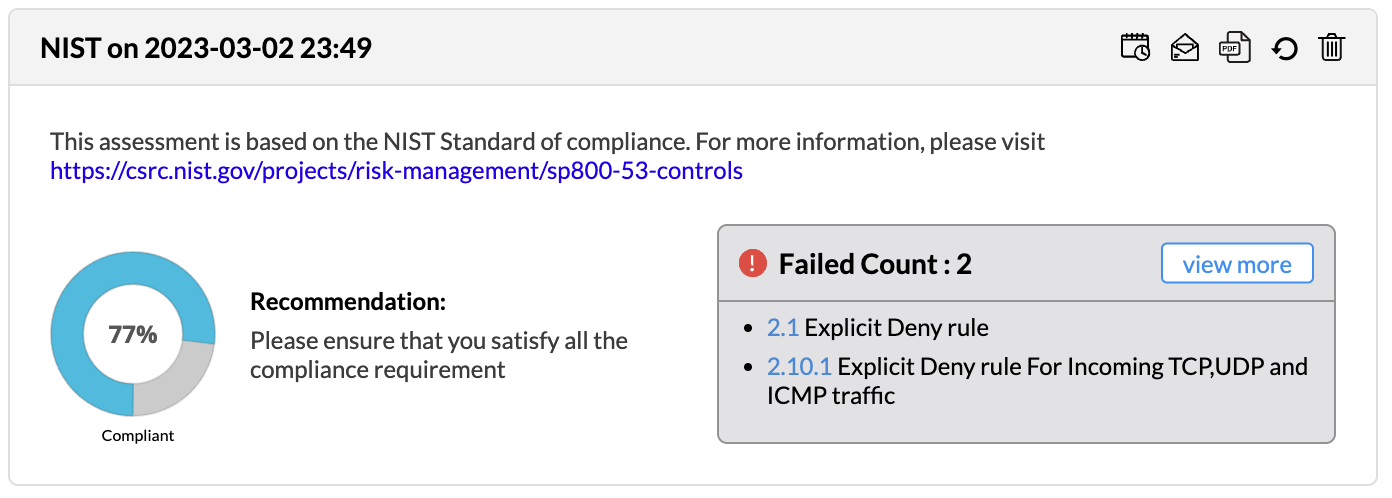
| 2.1 | All inbound and outbound traffic not specifically permitted should be blocked | Firewall Analyzer helps you to block the unauthorized/malicious traffic by allowing you to configure Explicit Deny rules. It also provides detailed report on all allowed traffic that provides better insights on all inbound and outbound traffic of your network |
| 2.2 | Permit only necessary Internal Protocol to pass through | Firewall Analyzer provides categorized exhaustive reports on allowed traffic across your network that helps in easy interpretation. It also provides you a detailed report on Insecure Service Audit. Both these reports provide better insights on Internal Protocols and help you to permit only the necessary protocols to pass through |
| 2.3 | Firewall policies should only permit appropriate source and destination IP addresses to be used | Firewall Analyzer's Traffic report gives you details on Source, Destination, Service and interface of all configured policies & rules that facilitate you to analyze them and permit the usage of necessary Source and Destination IP address |
| 2.4 | Avoid using localhost addresses in security policies | Firewall Analyzer provides you details on allowed rules with Local IP address that helps you to analyze and block the usage of local addresses in security policies |
| 2.5 | Avoid using invalid addresses in security policies | Firewall Analyzer gives you out-of-the-box report on all allowed traffic to your LAN/ DMZ via WAN interface. This detailed report helps in analyzing security policies at an ease and allows you to avoid the usage of invalid addresses in your security policies. |
| 2.6.2 | Do not allow Outside world to connect directly to LAN/DMZ Networks | Firewall Analyzer's extensive report on Direct connections from Untrusted network helps you to block untrusted connections from outside to your LAN/DMZ network |
| 2.9 | Block the Incoming Traffic to broadcast address | With Firewall Analyzer's report on 'Allowed Traffic' you can identify the incoming network traffic that broadcasts address from untrust Zone and block it |
| 2.10.1 | Be stringent in allowing services for TCP,UDP and ICMP protocols for Incoming Traffic | Firewall Analyzer's out-of-the-box reports on all allowed Incoming TCP,UDP and ICMP traffic provides better insights and facilitates quick decision on allowing services for TCP,UDP and ICMP protocols |
| 2.12.1 | Policies based on User-Identity should be logged | Firewall Analyzer provides you report on all policy logs based on user identity that helps meeting this requirement out-of-the-box |
| 2.13 | Remote Firewall Management Access | Firewall Analyzer provides you instant report on HTTP, Telnet, SSH access details along with the User access details that helps you to analyze and comply to the Remote firewall Management Access requirement |
| 3.1 | Maintain proper documentation for all the changes done to the firewall policies | Firewall Analyzer provides you a detailed report on all configuration change records over period of time that serves as proper documentation of all changes done to the firewall policies |
Refer Firewall compliance management software page for more details about other firewall security standards compliance.
Featured links
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.