What is data at rest?
Data at rest is one of the three states of digital data and it refers to any digital information that is stationary and contained within permanent storage devices, such as hard drives and tapes, or information reservoirs such as off-site backups, databases, archives, etc. The other states of digital data are data in motion, and data in use. Once data is transported and settles in its final destination, it is called data at rest during the entire period it remains inactive. If the data needs to be utilized for whatever purpose, and is being processed, it is then classified as data in use.
Threats to data at rest
By leveraging various exploit tactics, attackers can eventually trace their way to classified data. The integrity of data at rest will be threatened if the systems which have direct access to the data at rest are vulnerable, the networks in which the data is stored become contaminated or if the control over the various devices containing the data is hijacked.
Importance of data at rest security within organizations
Organizations often have conventional perimeter barricades that safeguard their data at rest, such as firewalls, password protection, anti-virus software and disk encryption. While these data security measures can prevent more conspicuous intrusions, malicious attackers often infiltrate networks through more discreet exploitation techniques, such as employee deception through phishing scams, or corporate espionage by infiltrating peripheral devices.
How to enhance data at rest security for effective attack prevention
Because subterfuges are constantly evolving, it is crucial to optimize network protection beyond the traditional security framework. The industry recommends adopting the Zero Trust model approach to data at rest security which entails that all devices and users attempting to access data at rest, remain blocked until they provide credentials that can be used verify their authority and hence classify them as trusted.
Strategies to protect your data at rest
Construct lists of trusted devices
Easily build lists of trusted devices and corresponding users to ensure that only verified, credentialed members of the organization, who have made their usage purpose transparent to the IT administrator, have access to specific data.
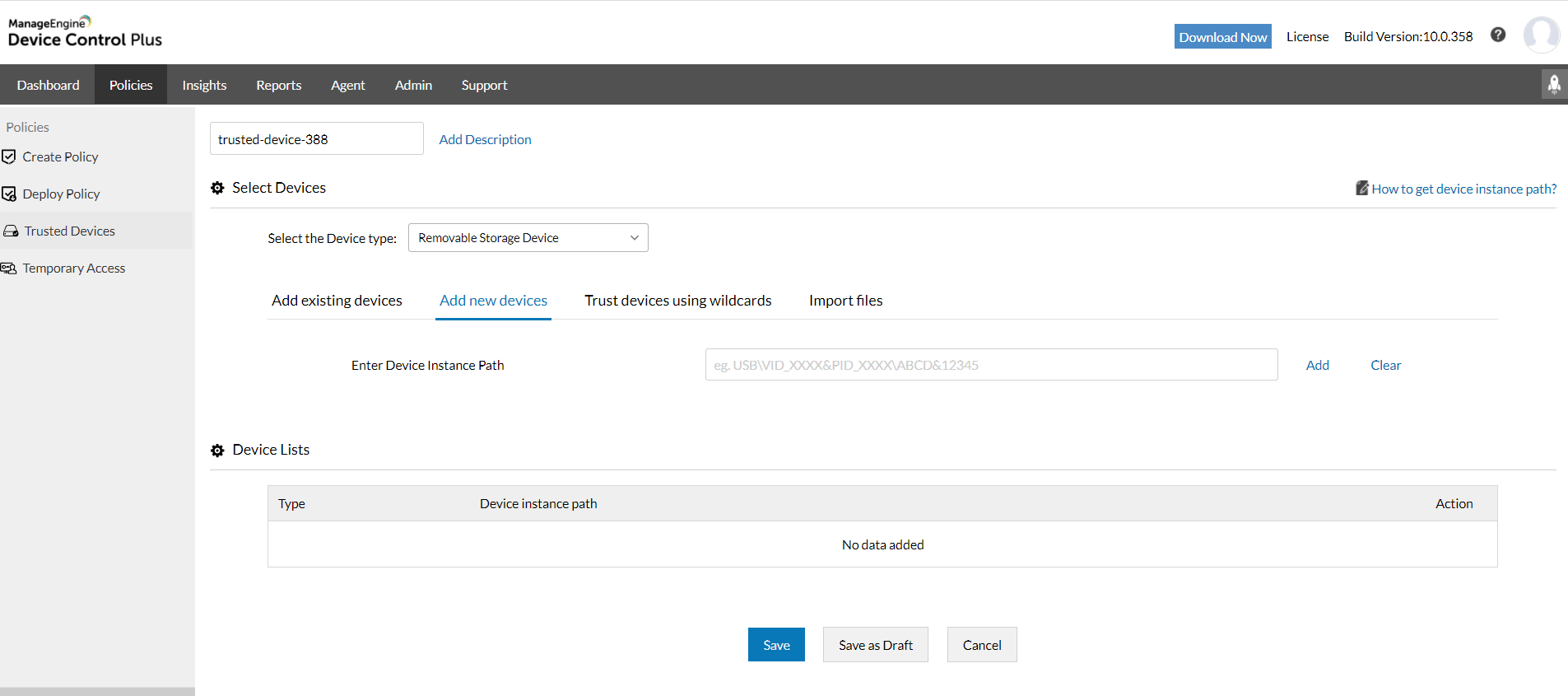
Double down on your control over computer ports by creating groups of computers based on their functions and identifying which peripheral devices are used on an adjunct basis for each of those groups.
Allow only encrypted devices to access data at rest. This additional security rule ensures that the data will remain protected from unauthorized viewers if it is transported and processed.
Assign granular file access policies for data at rest
Enforce varying levels of permissions, such as read-only, allow creation of files within computers, enable transporting of files via devices, or completely block the device from performing any file-related actions. Since transporting most data at rest can increase the risk of inadvertent data disclosure, implementing read-only file access for most employees who require access to certain data at rest is recommended.
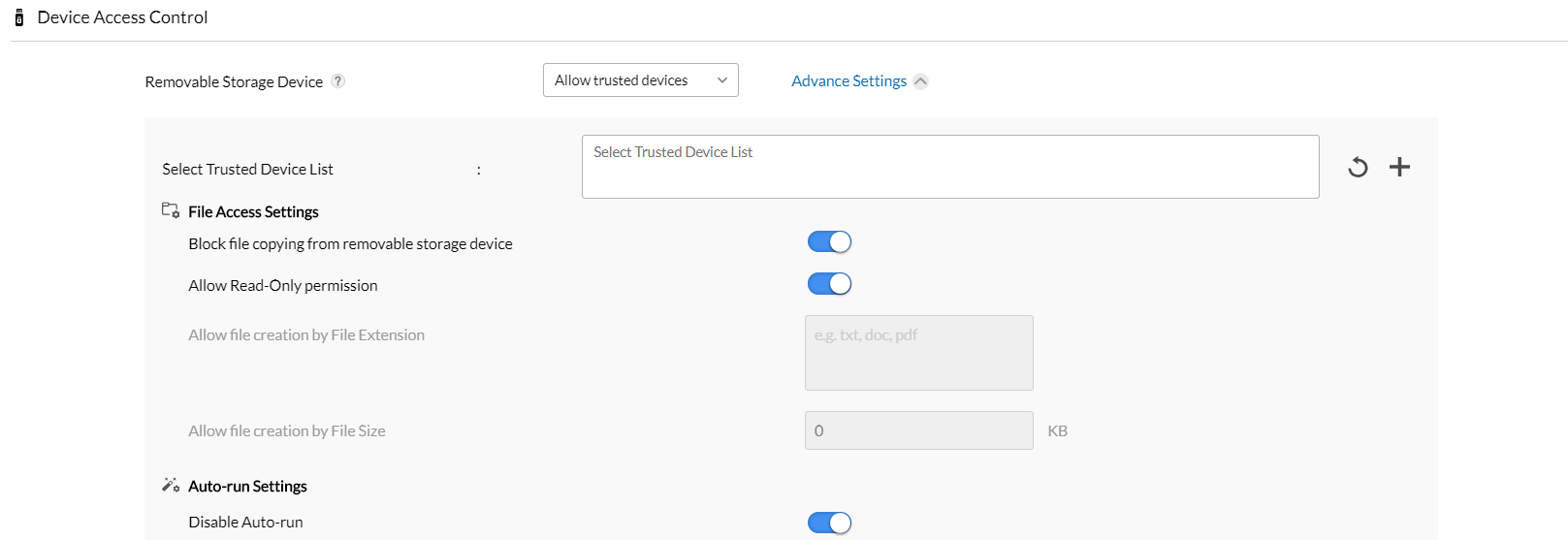
You should also consider the role of the user and their tasks when implementing role-based access control. High-level employees can be given better privileges, but if they are third-party users, they can be restricted to temporary access.
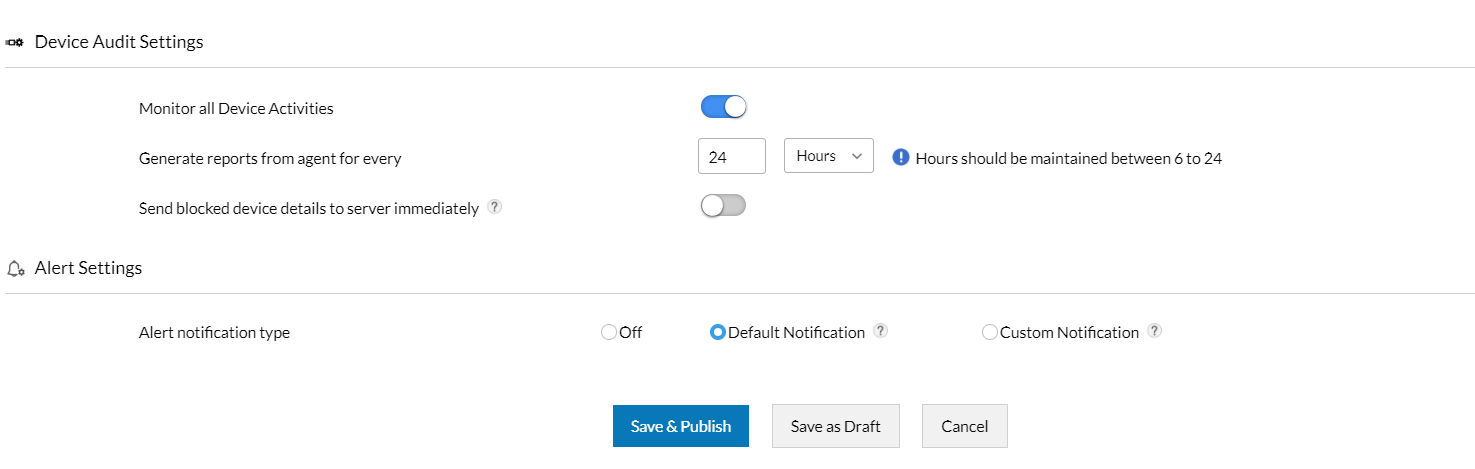
Review consistent reports and audits
To continuously monitor the volume of information contained within the network, it is important to identify the type of information by considering which departments and employees usually request access, where the information is stored, its classification in terms of sensitivity and confidentiality, as well as which compliance and privacy regulations it abides by. Utilizing software with meticulous reporting capabilities can grant the IT admin insight into all the characteristics of data at rest which can aid in building policies appropriate for the organization's standards and user requirements.Ensure you can configure settings to consistently receive reports as well as audits in case of an attempt to view data at rest.
Benefits of data at rest protection
- Prevent insider attacks that can potentially lead to data disclosure.
- Avert discreet attempts at data exfiltration through devices.
- Ensure that only trusted users can access data at rest.
- Satisfy both user and organizational requirements by assigning specific file access permissions.
- Achieve compliance by incorporating additional security measures for highly sensitive information.
- Gain better visibility over network data at rest through extensive auditing.
How can you protect data at rest with Device Control Plus?
Device Control Plus is versatile device and file security software for effortlessly implementing a Zero Trust-centric model across your network while enhancing data at rest security. Its robust features, such as building a trusted devices list, flexible file access control configurations, and smart auditing capabilities can be utilized to effectively mitigate both overt and clandestine threats to the organization.
Schedule a live demo, or download a 30-day free trial for Device Control Plus to get starting on securing your data.