Data in motion: What it is & How to protect it
What is data in motion?
Data in motion is a term used to label any digital information that is being transferred from one location to another. It is also commonly referred to as data in transit or data in flight. When the data is finally contained in one location, it becomes data at rest.
Data in motion examples
For data in motion, the information can be moved to various locations within the same computer such as copying files from one app to another, or downloading from a web browser to a local app. It can also be transferred between different computers through cloud services such as email or physically across short or long distances via portable storage devices like USB flash drives.
Why is it important to secure data in motion?
Data protection is a central aspect to an organization's welfare and performance. All data generated by or entrusted to an organization should be handled carefully, and this rule especially applies to data in motion security. If data in motion is ever exposed to malicious actors, the ramifications can be potentially fatal to business continuity as well as reputation, which can result in significant monetary loss.
Data in motion security with respect to organizations
Data in motion can be broadly classified into two categories. The first is virtual information transferred within the boundaries of a private network. This information, to an extent, is protected by firewalls and other internally established data protection measures. The second category is information being transported outside of the organization. Data in motion is the most vulnerable in the instances where it is transferred out an organization or private network as it's sometimes processed across unreliable networks like the internet or using peripheral devices that, if handled improperly, can become exposed to unauthorized viewers.
How to protect data in motion?
Identify and classify the types of data
Within an organization, numerous types of data can exist, such as personal identifiable information (PII), financial records, employee or clientele data, intellectual property, etc. The first step to enacting data in motion security is to identify what kind of information is contained within an organization's data reservoirs, and consistently track all newly accumulated data as well.
Define strategies for data protection and conduct
After all the data is categorized, handling instructions have to be associated with each information type according to the amount of privacy it requires. For example, some data can be confidential and should only accessible to a select few authorized personnel, while other information can be protected with relatively lenient standards. For customer or employee information especially, it's critical to adhere to specific compliance regulations such as GDPR, HIPAA, PCI, DSS, etc. as not to incur financial penalties or brand attrition.
Impose stringent control over data transfer
As a precautionary measure, it's important to allow data to be transferred out of the organization only when necessary. Because some business-critical information cannot be sent through work stream collaboration platforms, cloud storage services, or public networks, users often carry such data in a myriad of peripheral devices.Organizations should enforce device transfer restrictions based on file name, extension, and size for data in motion so only the information required for the task at hand is extracted by trusted users. .
Implement real-time tracing of all data in motion
If files are to be elicited from the organization's vaults, all pertinent details regarding the operation should be recorded for increased visibility into how the data will be used and for what purpose. These details should include the original locations of the files, the destination to which the data in motion will eventually arrive, the users who are performing the movement, the devices used in the process, and the computers involved. Before the file extraction receives the green light, for preventative data protection, the IT administrator should also be immediately notified through alerts to confirm that the specific file transference is indeed an authorized activity.
Shadow files and consolidate copies in password-protected shares
As an additional measure to recover from potential liabilities that may arise due to human error, hardware or network malfunctioning, or even lost or stolen devices, file shadowing can be performed. File shadowing, also referred to as data mirroring, is the process of producing copies of all content transferred via USB devices and storing it in a network share accessible only to users with admin-delegated credentials. If at any point the data in motion is rendered vulnerable to threats in the wild, the shadow copies of critical documents can be reviewed to help set up remediation strategies that can significantly reduce downtime and preserve brand value.
Securing data in motion can be implemented by Device Control Plus
ManageEngine Device Control Plus is a comprehensive file and device security solution that can be leveraged to easily implement all of the aforementioned steps to safeguarding data in motion. After the file action is completed, the operation should be logged and the audit data should be made available for easy analysis.
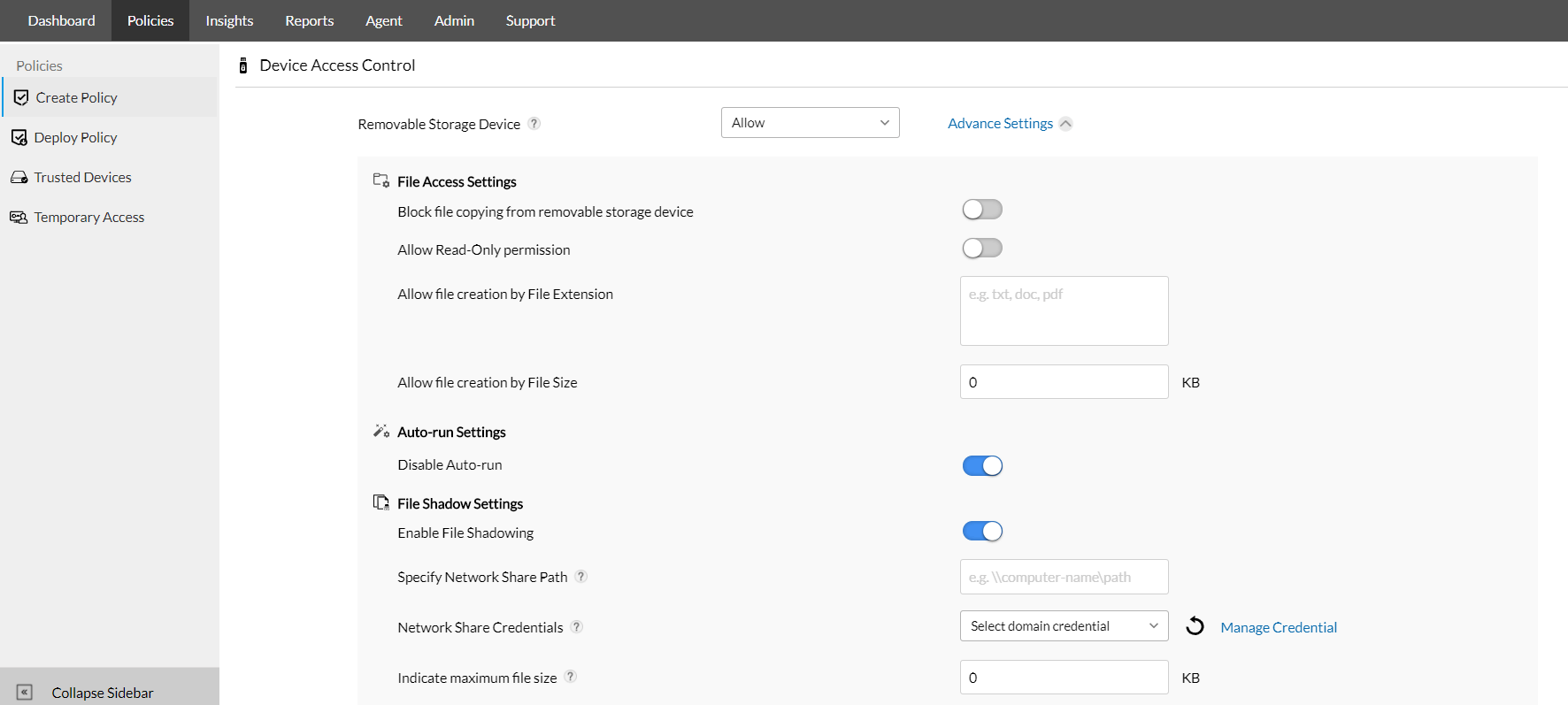
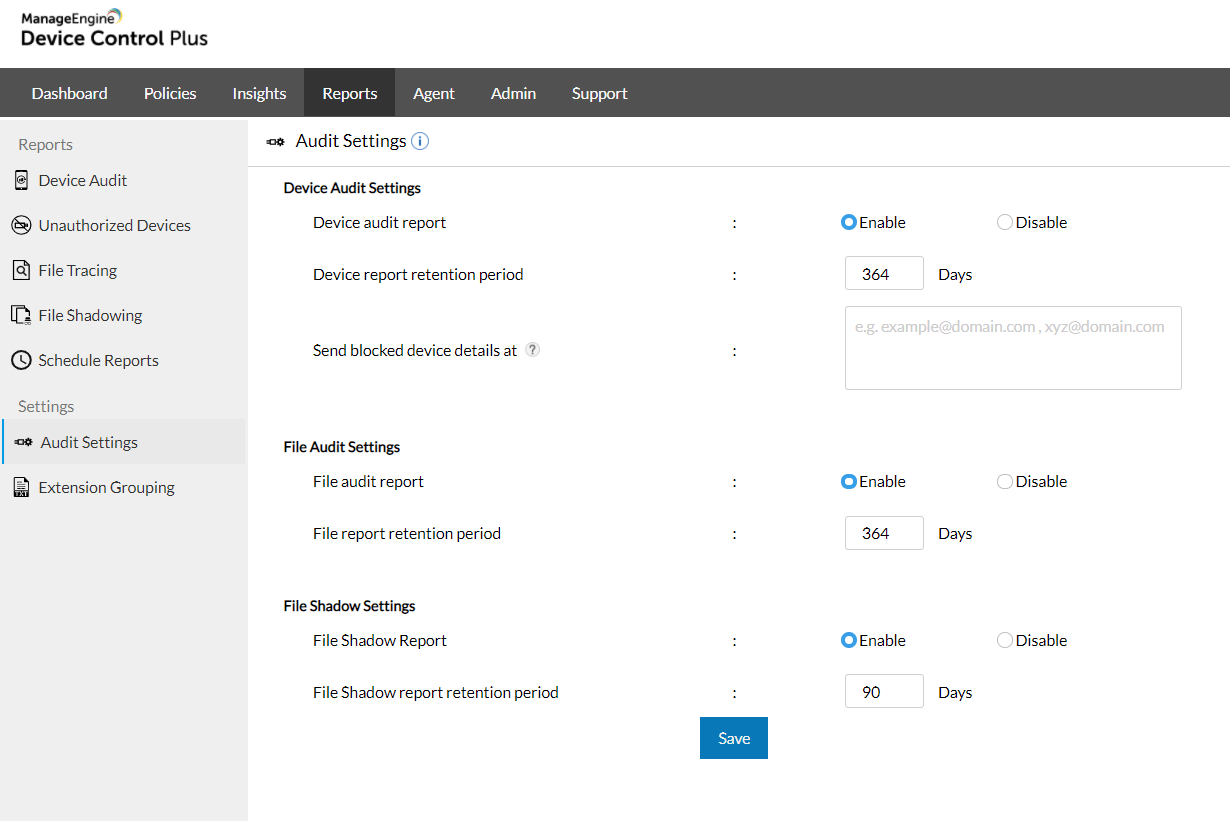
The integrated combination of features such as file tracing and file shadowing can aid administrators in establishing flexible but extensive control over file operations, as well as help them apply protocols to manage and effectively protect all data traveling within or across network perimeters.
Download a 30 day free trial and get started on securing all of your organization's integral data in motion.