Over 76% of ransomware attacks in April 2023 were carried out with the help of PowerShell. In turbulent times like these, it's important for organizations to be armed with the right cybersecurity measures, and cover all their bases. While most organizations focus on defending and securing the apparent entry points, cybercriminals target loopholes that help them stealthily stay ahead of the game. One such loophole is Windows PowerShell. A native tool that can be hacked and misused to execute malicious scripts, PowerShell is a hacker favorite. This is precisely why companies must invest in studying malicious PowerShell commands and learning how to detect and prevent their execution using the right security tools and measures.
In the first part of this two-part series, we will explore:
To incorporate better cyberdefense policies in organizations, defenders must study the anatomy and execution of cyberattacks. This will help them better understand the mindset of attackers and the possible loopholes present in their native network. This will in turn enable them to take proactive defense measures.
In the second part, we will explore how to set up Empire, a popular post-exploitation tool, and deconstruct an attack carried out using the tool. We will also see how a SIEM solution can help detect it.
PowerShell is a command line interpreter with the ability to execute scripts in the system's memory. It is a native tool offered by Microsoft that comes built-in with all Windows machines. In many organizations, users can access and run PowerShell as an administrator by default. This means that once a bad actor gains access to any user account in an organization's network, they can use PowerShell to run arbitrary commands to create and delete files, change configurations, and access and control remote machines.
Most PowerShell attacks involve file-less threats, which are executed without any malicious downloads in the system or writing anything onto the system's disk. A PowerShell attack typically involves the execution of certain scripts that can indicate malicious activity, like those which:
Organizations can set alerts to look out for such script executions and ensure that they are not carried out by putting relevant security mechanisms in place.
Attackers often use frameworks or tools like Empire, PowerSploit, Cobalt Strike, or Covenant C2 to execute PowerShell attacks. In this blog, we will look at Empire, a post-exploitation tool that can execute malicious PowerShell scripts in memory while executing a cyberattack.
Empire is an open-source tool used by threat actors and pen testers for post-exploitation purposes. It was created as a legitimate pen-testing tool in 2015 by security practitioners at Veris Group and is written in Python for Linux OS. Its post-exploitation agents are written in pure PowerShell script for Windows machines. In 2018, a joint report by cybersecurity authorities from five nations (Australia, Canada, New Zealand, the UK, and the USA) listed PowerShell Empire as one of the top five open-source tools commonly used by attackers for lateral movement.
In 2019, the development of PowerShell Empire was discontinued for two reasons: 1) the onset of better alternatives to Empire for pen testing, and 2) hackers increasingly using it to carry out cyberattacks. There was no way to stop the latter, so the development of the tool was paused. Chris Ross, one of the developers, stated that the ultimate purpose of the tool was fulfilled. It was created to exhibit how PowerShell could be used in various stages of an attack, especially for post-exploitation purposes. Some post-exploitation activities include creation of hidden files and folders, and starting processes. The PowerShell Empire framework is currently being maintained by BC Security. It continues to be a popular command and control framework for threat actors.
In this blog, we will cover step by step how either pen testers or threat actors can install the tool and use it to launch a PowerShell post-exploitation attack. But first, let's cover a few basic terms that'll help us understand the whole process a little better.
Let's try to understand how PowerShell Empire can be used as a post-exploitation tool by studying its role in the Frankenstein campaign, which involved several targeted attacks using other open-source tools as well.
From January to April 2019, a series of highly targeted attacks were executed using several open-source tools. Cisco Talos called the attack campaign "Frankenstein" because of the various tools stitched together to perform the attacks.
One of the open-source tools used was Empire. It was used to exfiltrate data through an encrypted C2 channel. Given below is a brief illustration of the attack's anatomy to help understand the use of Empire in the Frankenstein campaign better.
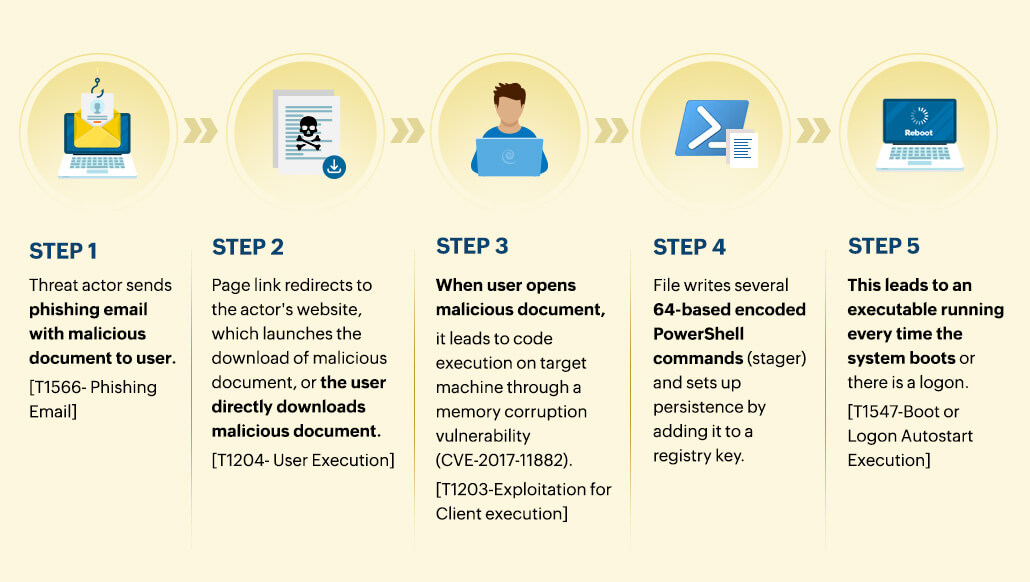
Source: AttacKG: Constructing Technique Knowledge Graph from Cyber Threat Intelligence Reports
Here, the adversary used four open-source services and files to execute the Frankenstein campaign. Along with a malicious file, which when downloaded tracks whether a file has been executed in the target virtual machine, there were three Github projects used. While two of them were to execute PowerShell commands and run a stager, the third was PowerShell Empire, used for its post-exploitation agents.
To learn more about detecting PowerShell attacks using Log360, you can request a personalized demo.
Stay tuned for this blog's second part in which you will read about launching a PowerShell attack using Empire and how to detect it using a SIEM solution like Log360.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.