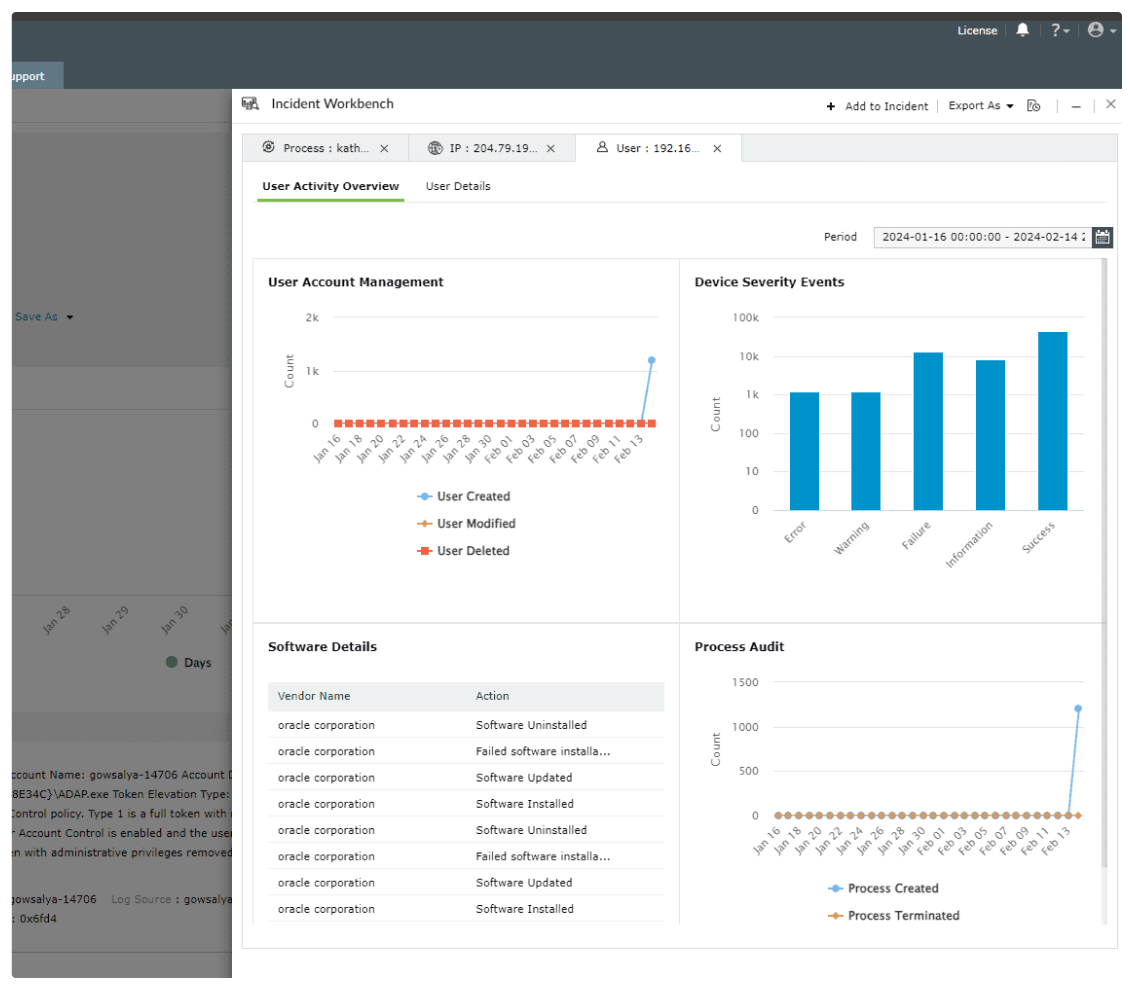
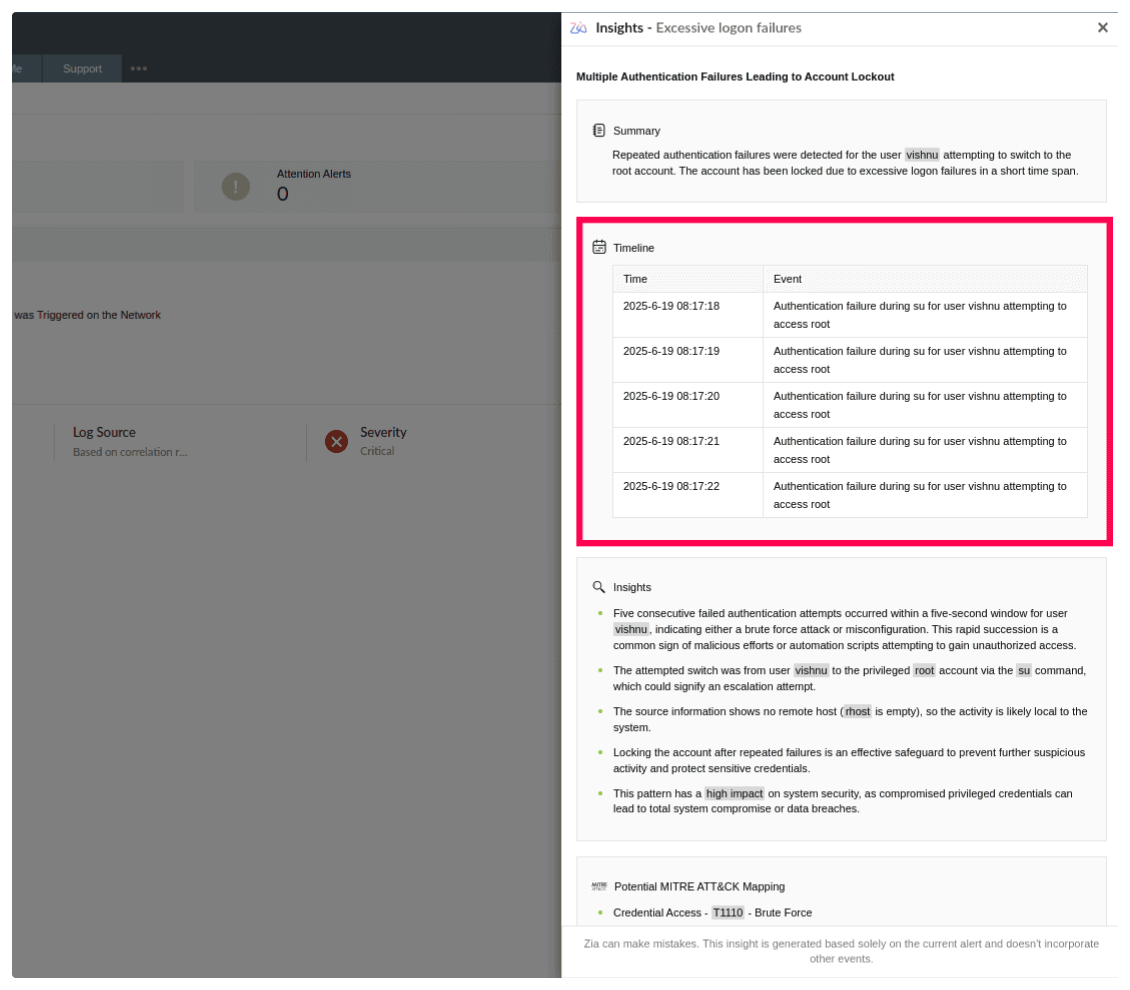
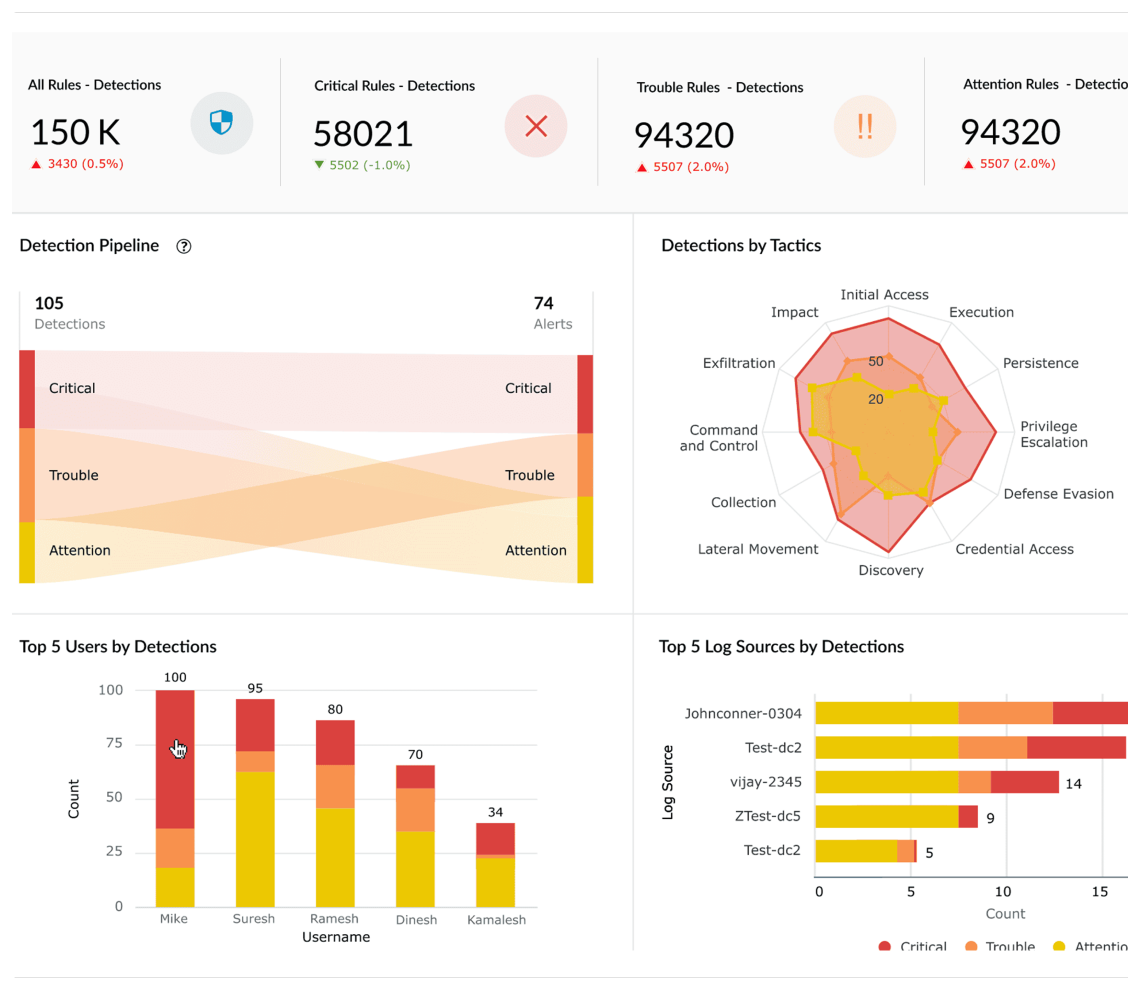
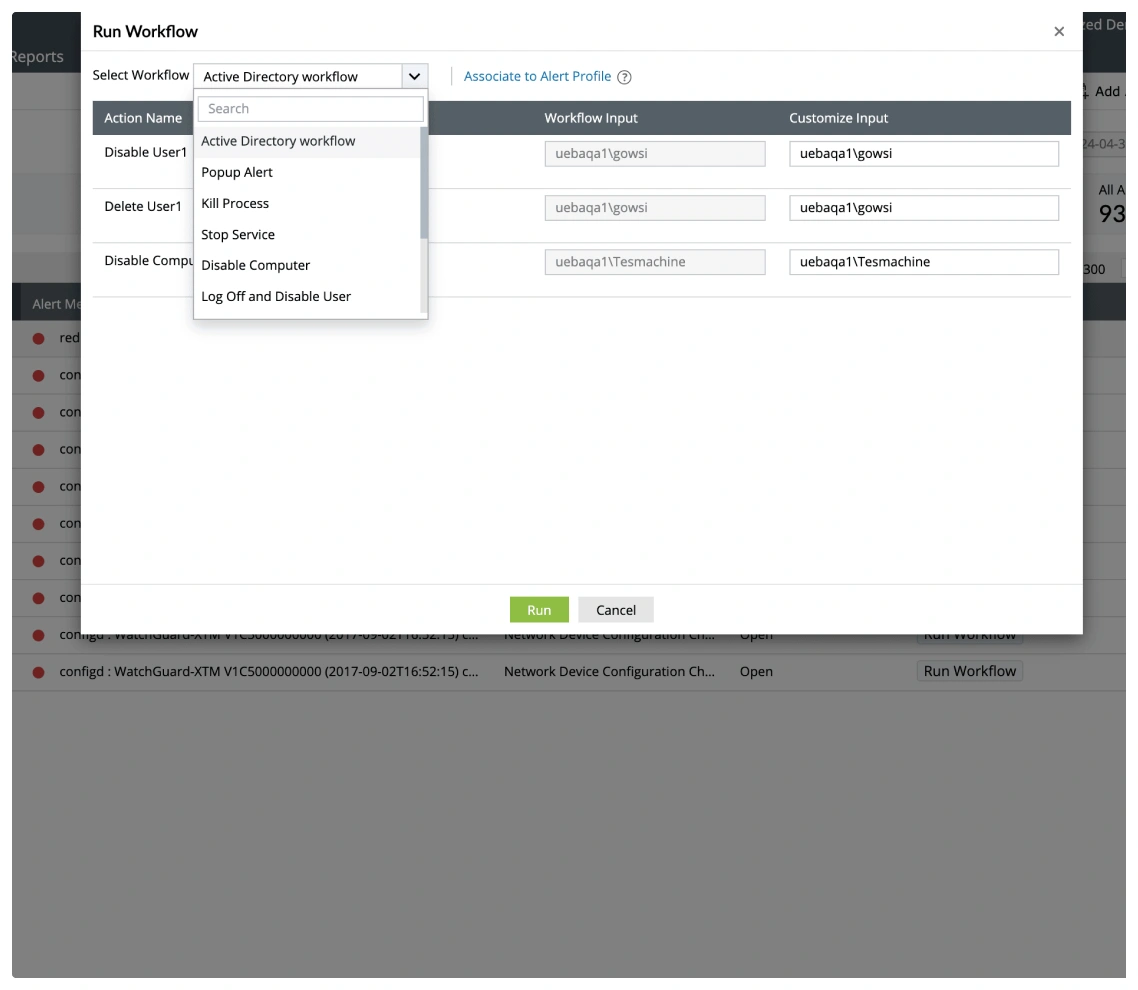
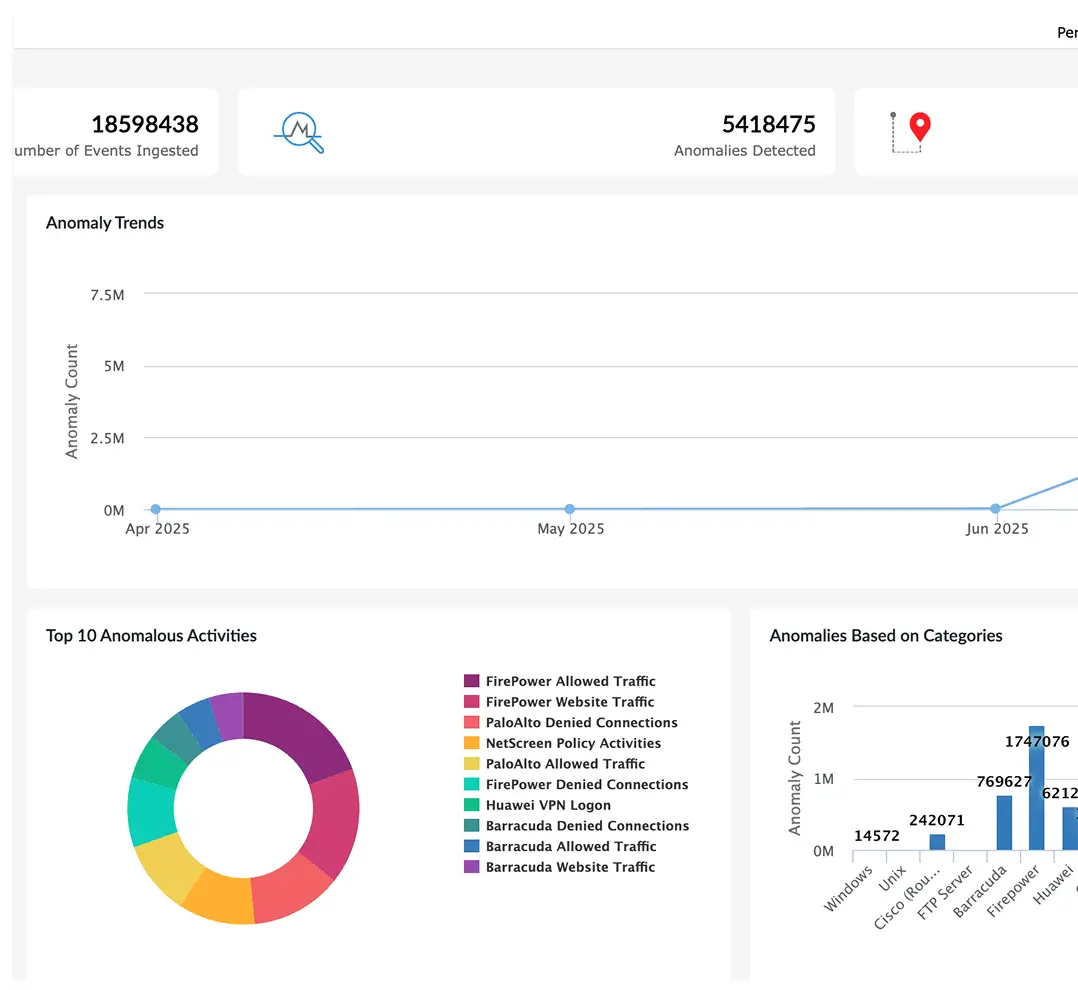
A continuously updated catalog of more than 2,000 cloud-delivered detection rules equips teams to defend against evolving tactics. These rules are categorized by log source and mapped to attacker behaviors, ensuring rapid deployment without manual configuration overhead. Analysts can tailor detections through rule engineering, linking them with alert workflows and customizing thresholds to match the unique threat surface of their environment while maintaining high coverage across MITRE tactics, techniques, and procedures.