The MITRE ATT&CK framework is a globally recognized knowledge base of adversary TTPs, derived from real-world observations. It helps security teams understand attacker behavior, improve threat detection, and standardize incident response.
Correlate suspicious activity, anomalies, and cloud or on-premises events to tactics and techniques.
Detect complex attacks, including insider threats, ransomware, cloud misconfigurations, and multi-stage APTs with MITRE ATT&CK-aligned, context-aware rules.
Correlate global threat feeds with behavioral analytics across your endpoints, cloud, and network from a unified console, enriching alerts and reducing response time.
Use Zoho's Zia Insights to map alerts to the MITRE ATT&CK tactics, reconstruct attack timelines, verify patterns and correlate it with other events, and get remediation guidance.
The MITRE ATT&CK framework provides a structured taxonomy of tactics, techniques, and procedures (TTPs), for cyber adversaries. This enterprise MITRE ATT&CK matrix gives security teams a unified language to detect, investigate, and respond to attacks systematically.
Log360’s cloud-delivered detection library offers over 2,000 rules mapped to TTPs for enterprise, cloud, and ICS environments. By correlating multiple events across various log sources and leveraging anomaly-based insights, Log360 empowers SOC teams to detect, investigate, and respond to sophisticated threats with precision.
Benefit: Gain end-to-end visibility into adversary behaviors, reduce dwell time, and improve threat response.
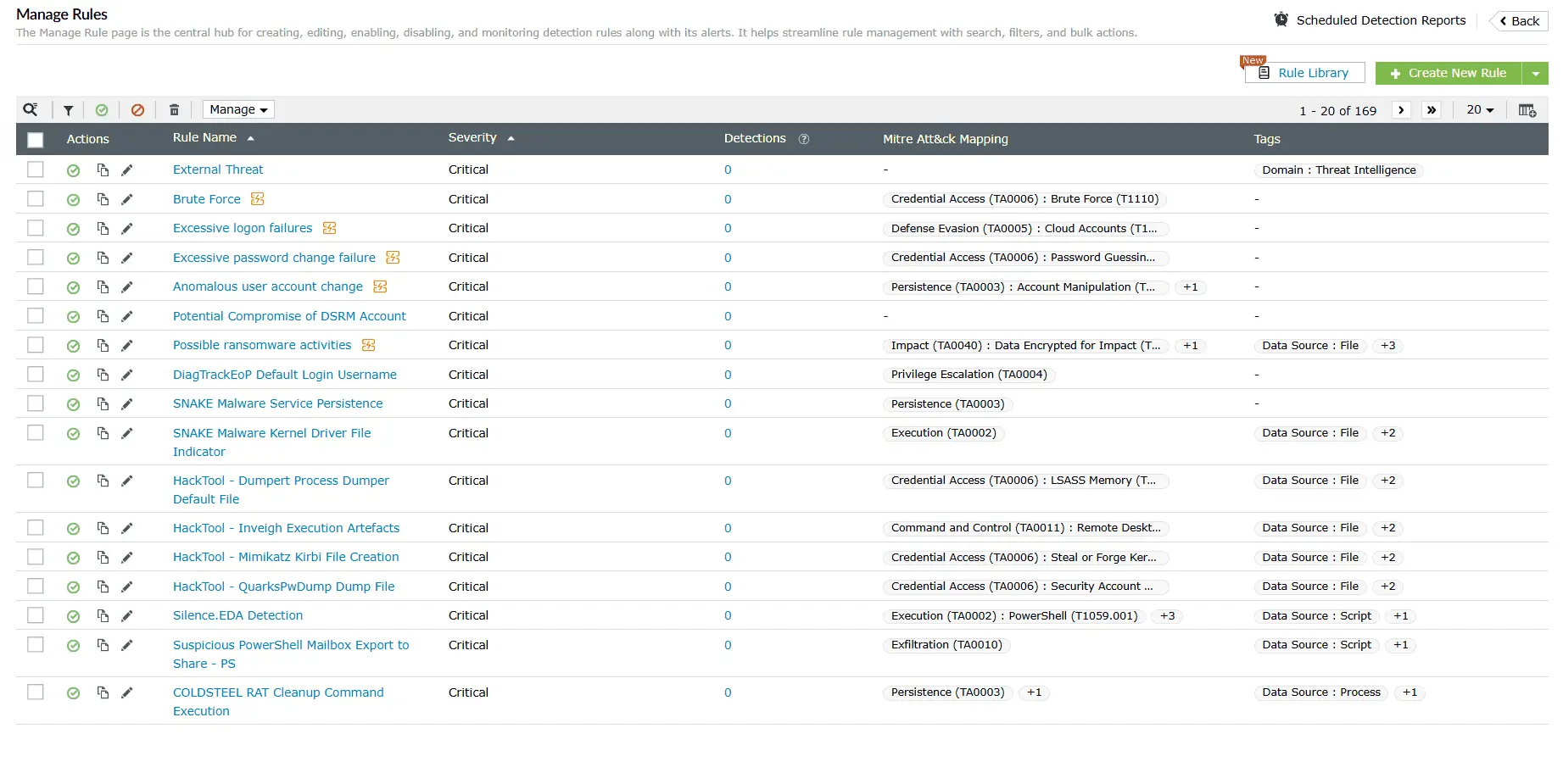
Log360’s AI-powered assistant, Zia, translates raw security data into actionable intelligence by mapping alerts, logs, and incidents to MITRE ATT&CK tactics and techniques. SOC teams can investigate threats faster with contextual summaries, attack timelines, and remediation guidance.
Benefit: Accelerate investigations by reducing hours of log analysis to minutes with AI-driven summaries and guidance.
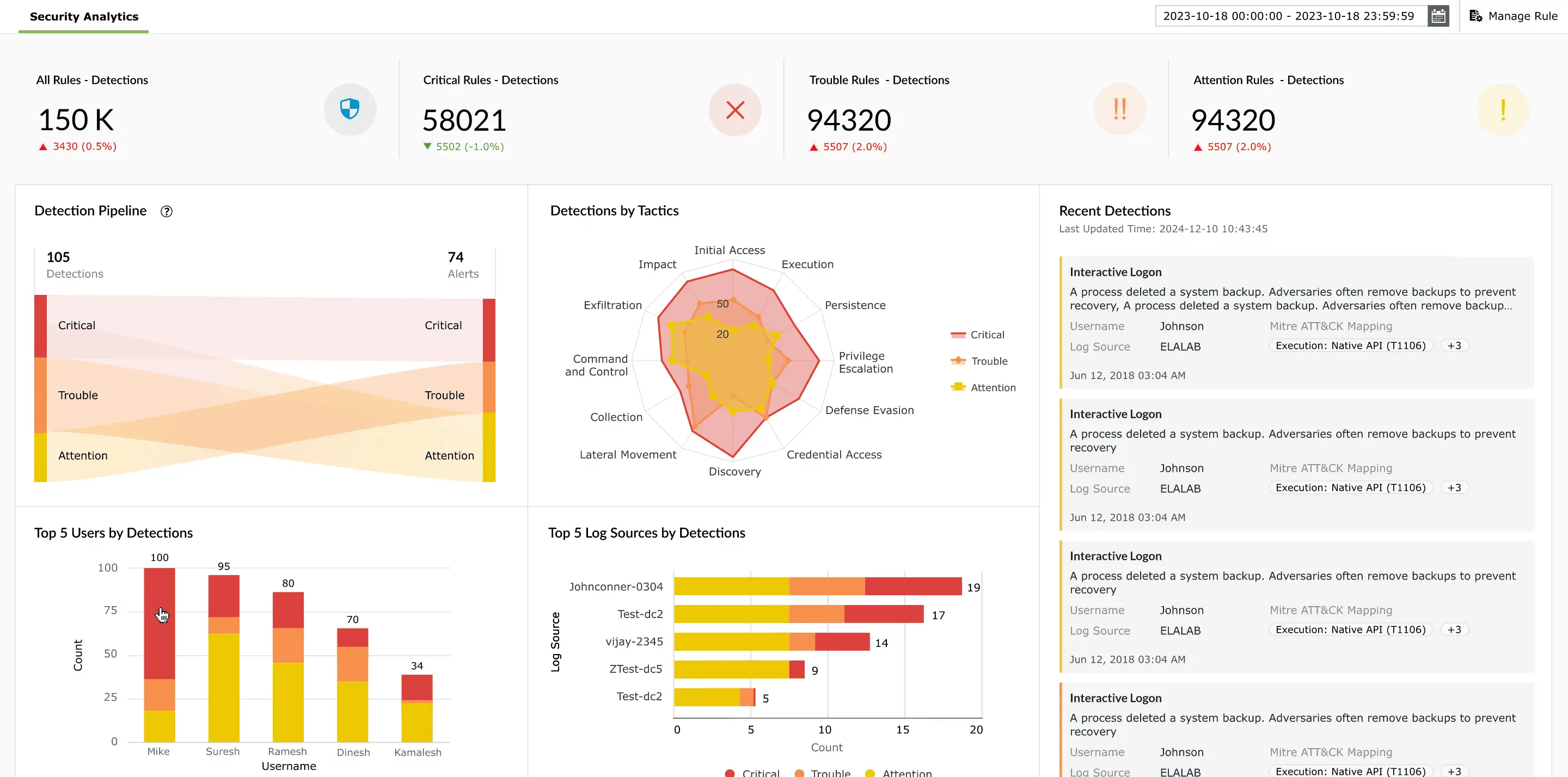
Leverage Log360’s dashboards to gain real-time visibility across endpoints, cloud, and network devices. By correlating events with MITRE ATT&CK tactics and techniques, analysts can visualize attack chains, identify high-risk activities, and prioritize responses efficiently.
Benefit: Gain complete situational awareness, detect complex attack patterns, and proactively monitor multi-stage threats.
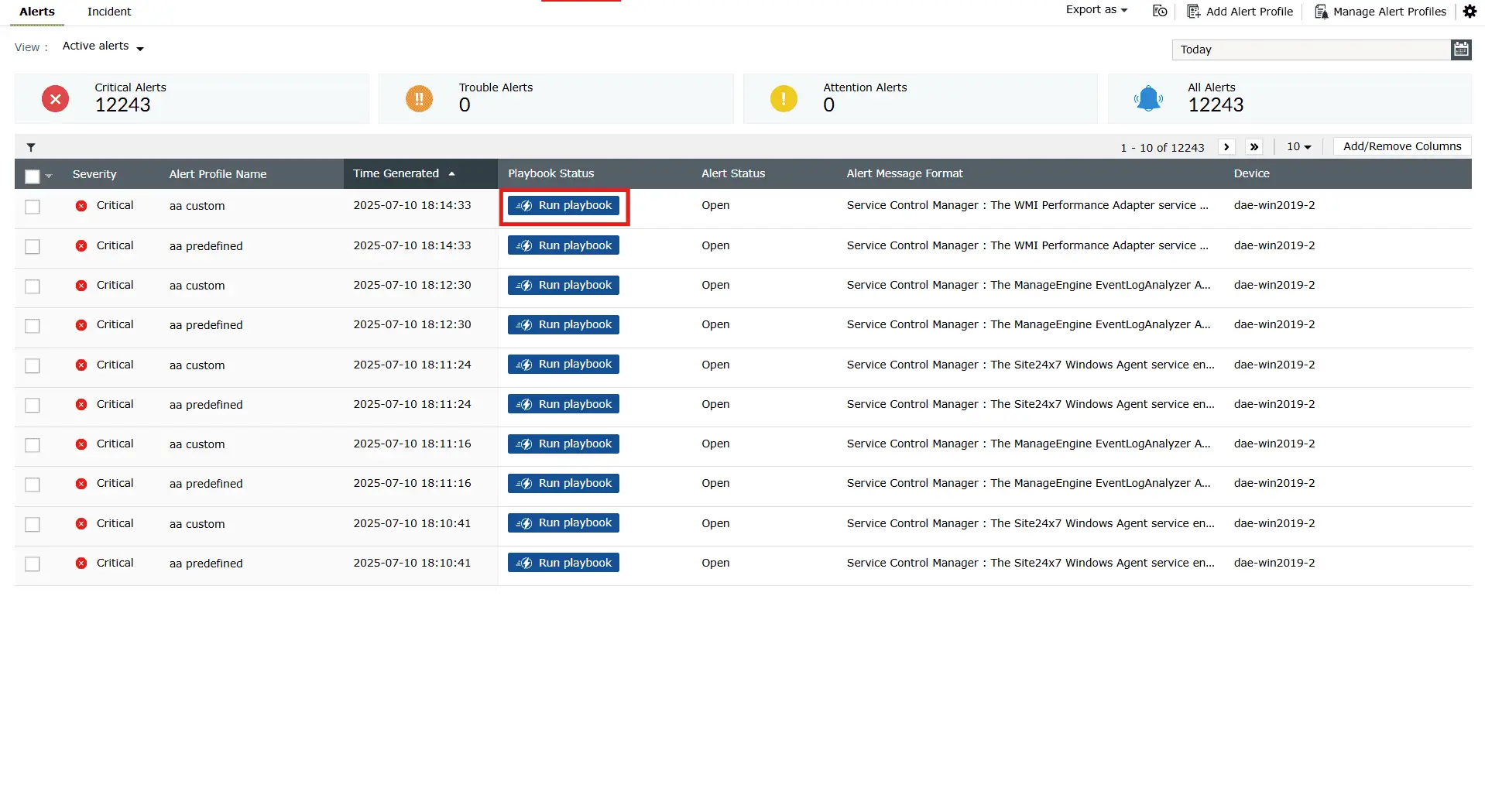
Log360’s playbooks enable SOC teams to orchestrate automated, MITRE ATT&CK-informed responses to security incidents. By integrating detection, contextual insights, and remediation steps, playbooks ensure consistent and efficient handling of high-priority threats.
Benefit: Respond to threats quickly, reduce manual effort, and maintain MITRE ATT&CK-aligned operational consistency.
ManageEngine Log360 leverages the MITRE ATT&CK framework to provide end-to-end detection across the entire attack life cycle. By mapping real-world threat behaviors to MITRE ATT&CK tactics and techniques, Log360 empowers security teams to proactively identify and stop threats at every stage, ensuring comprehensive, framework-aligned protection across the enterprise.
Log360 identifies adversary attempts to maintain long-term access and elevate privileges by monitoring account changes, authentication mechanisms, and privileged group modifications.
Example scenario: An attacker resets the Directory Services Restore Mode (DSRM) password without approval.
Learn moreLog360 helps detect and block attempts to bypass security controls, tamper with logs, or steal or misuse credentials, safeguarding high-value accounts and critical systems.
Example scenario: A firewall policy is deleted after hours, followed by multiple failed logins and a successful authentication on a privileged account.
Log360 detects and blocks adversary reconnaissance and propagation attempts within the network, preventing attackers from mapping the environment or moving laterally to high-value assets.
Example scenario: A compromised user initiates multiple RDP sessions to sensitive servers while performing Active Directory enumeration.
Log360 monitors sensitive data access and transfer, helping prevent attackers from collecting or exfiltrating valuable information.
Example scenario: SQL server backups are executed after hours and transferred to cloud storage or USB drives without approval.
Log360 doesn’t just align detections with the MITRE ATT&CK framework; it equips organizations to uncover hidden threats, automate responses, and gain actionable insights for faster, smarter security decisions.
Handles growing log volumes with distributed, high-availability architecture for uninterrupted log collection, indexing, and analysis.
Learn moreProvides centralized visibility across endpoints, networks, and cloud security events, enabling faster threat detection and response with actionable insights.
Learn morePrebuilt playbooks automated alerts, notifications, and remediation, reducing response times and limiting potential overall damage.
Learn moreDetects brute-force attacks, phishing, port scans, and monitors the dark web for leaked credentials or compromised data.
Learn moreWe wanted to make sure that one, we can check the box for different security features that our clients are looking for us to have, and two, we improve our security so that we can harden our security footprint.
Carter Ledyard
The drill-down options and visual dashboards make threat investigation much faster and easier. It’s a truly user-friendly solution.
Sundaram Business Services
Log360 helped detect insider threats, unusual login patterns, privilege escalations, and potential data exfiltration attempts in real time.
CIO, Northtown Automotive Companies
Before Log360, we were missing a centralized view of our entire infrastructure. Now, we can quickly detect potential threats and respond before they escalate.Log360 has been invaluable for improving our incident response and ensuring compliance with audit standards. It’s a game-changer for our team.
ECSO 911
The MITRE ATT&CK framework is a globally recognized knowledge base of adversary TTPs, derived from real-world observations. It helps security teams understand attacker behavior, improve threat detection, and standardize incident response.
Yes. Log360’s no-code rule engine allows you to build custom rules aligned with any MITRE ATT&CK tactic or technique. Advanced correlation rules let you map entire multi-stage attack chains across multiple log sources.
Log360 supports over 750 log sources including Windows/Linux servers, cloud platforms (AWS, Azure, Microsoft 365), network devices, databases, applications, and security tools. All sources are automatically mapped to relevant MITRE ATT&CK techniques.
Yes. Log360 provides full MITRE ATT&CK coverage for SaaS, IaaS, and hybrid environments. Cloud-specific attack techniques are monitored alongside on-premises data, giving analysts unified visibility across the entire infrastructure.
Absolutely. Contextual threat intelligence and MITRE ATT&CK-aligned correlation distinguish routine activity from adversary behavior, enabling SOC analysts to focus on high-priority alerts and reduce investigation overhead.
By linking alerts, detections, and remediation steps to recognized MITRE ATT&CK tactics and techniques, Log360 simplifies structured monitoring and audit readiness. This aids regulatory compliance for standards like the GDPR, HIPAA, the PCI DSS, and more.
Explore how Log360 detects attacks, maps them to the MITRE ATT&CK framework, and automates containment enabling SOC teams to focus on what truly matters.