What is UEBA?
User and entity behavior analytics (UEBA), or anomaly detection, is a cybersecurity technique that uses machine learning (ML) algorithms to detect the anomalous activities of users, hosts, and other entities in a network.
To detect anomalies, UEBA first learns about the expected behavior of all users and entities in a network and creates a baseline of regular activities for each of them. Any activity that deviates from this baseline gets flagged as an anomaly. UEBA solutions grow more effective as they gain more experience.
To understand how UEBA creates a behavioral profile for every user, let's go over an example and understand how humans do it first. Consider John, a newly hired marketing intern. On his first day of work, the security guard recognizes him as someone new and pays close attention to ensure that all his credentials check out. The guard also tracks the time John enters and exits the facility. He monitors John’s activity for a few days and gets to know his expected time pattern—arrival at 10am and exit at 6pm. Any deviation from this, such as John's arrival at 5am, will raise the guard's suspicion. This is how humans detect an anomaly.
Similarly, the ML algorithm in a UEBA-integrated SIEM solution will monitor the log data to establish patterns in your network. For instance, a user's logon and logoff time and their actions on particular devices will tell the SIEM solution about the activities that are expected from that user. Once it monitors activities for a few days, the UEBA engine will know the user's expected behavior, including any deviation from it. The user's risk score will increase to indicate the severity of the threat, and the SIEM solution will flag an alert to the security analysts.
"But if a human can already do that, why do you need UEBA?"
Because it is not humanly possible for your security team to constantly observe and analyze the behavior of the thousands of employees who work at your organization; generate reports on anomalous activities at different parts of the network; and take appropriate action immediately. Which brings us to the next question: What type of anomalies can UEBA identify?
What type of anomalies can the UEBA solution identify?
UEBA identifies anomalies associated with time, count, and pattern. Let's take a look at what each of these means.
Time anomaly: If a user or entity deviates from the expected baseline, it is termed a time anomaly. You can take John's login at 5am instead of his usual 10am as an example of a time anomaly.
Count anomaly: If a user or entity performs an abnormal number of activities within a short span of time, we call it a count anomaly. An example would be a user accessing the customer database 50 times in the hour between 11am and 12pm.
Pattern anomaly: If an unexpected sequence of events results in a user account or entity being accessed in an atypical or unauthorized manner, it is termed a pattern anomaly. An example of a pattern anomaly is a user account having a successful logon after eight consecutive login failures, followed by multiple file deletions, modifications, and data transfers made from that account.
Before we discuss how UEBA works behind the scenes, let's cover the basics in a bit more detail by understanding the three pillars and components of UEBA.
Three pillars of UEBA
Gartner's definition of UEBA involves three key attributes or pillars: use cases, data sources, and analytics.
Use cases
UEBA solutions hunt for anomalous deviations from normal behavior of users and entities to identify security threats. However, it's crucial for them to be suitable for numerous use cases such as insider threats, account compromise, data exfiltration, and zero-day attacks.
Data sources
The UEBA solution you use should be capable of collecting data from diverse data sources such as event logs, network traffic, and endpoint devices by fully integrating within a SIEM solution, or ingesting data from general repositories such as data warehouses or data lakes. They shouldn't require agents to be deployed in IT environments for collecting data.
Analytics
UEBA solutions employ advanced analytical techniques such as ML algorithms, statistical models, threat signatures, and rules for identifying the normal behavioral baseline of users and entities. A UEBA solution then analyzes behavior within the context of user roles, permissions, and typical activities to differentiate between normal and suspicious behavior accurately.
These three pillars collectively empower organizations to strengthen their cybersecurity posture and mitigate risks effectively.
Components of UEBA
A UEBA solution has three major components:
1. Data analytics
Data analytics in UEBA involves collecting and analyzing data from various log sources to study the "normal behavior" of all the users and entities. Whenever it detects any outlier events, it flags them as an anomaly.
2. Data integration
This involves integrating data collected from various sources—including logs, packet capture data, and other datasets—with existing security systems to make them more robust.
3. Data presentation
The presentation of data in UEBA helps security analysts and other stakeholders to easily interpret and make informed decisions based on the behavior patterns identified. This is done through visualizations, charts, graphs, or reports that highlight the patterns, anomalies, and risk scores derived from the data analysis.
How does UEBA work?
Closely monitoring the behavior of a person can reveal a lot about their true intentions. This is the concept that UEBA works from. UEBA solutions closely monitor the activities of every user and entity inside the network and learn their characteristics. A UEBA solution often works along with a SIEM solution by using activity logs to study the usual behavior of users and entities.
A risk score is calculated for each user and entity in the organization after comparing their actions to their baseline of regular activities. The risk score usually ranges from anywhere between zero and 100 (indicating no risk to maximum risk, respectively). The risk score for deviating actions are dependent on factors such as the allotted weight of the action, the extent to which an action deviates from its baseline, the frequency of each kind of deviation, and the time elapsed since a deviation of that type occurred. To learn more about how risk scoring in anomaly detection works, read this blog.
There are two methods to set up a UEBA system:
Supervised ML
In this method, the UEBA system is fed a list of known good and bad behaviors. This list is limited and therefore might lack proper knowledge for it to detect anomalous behavior. The system builds up these inputs further and detects anomalous behaviors in the network.
Unsupervised ML
In the unsupervised ML method, the UEBA system undergoes a training period to learn the normal behavior of every user and entity. This method is unarguably the best because the system studies the everyday behavior of users and entities on its own.
The working mechanism of UEBA
UEBA employs statistical models such as robust principal component analysis (RPCA) and Markov chains to establish behavioral baselines. These anomaly detection models help detect time, count, and pattern anomalies.
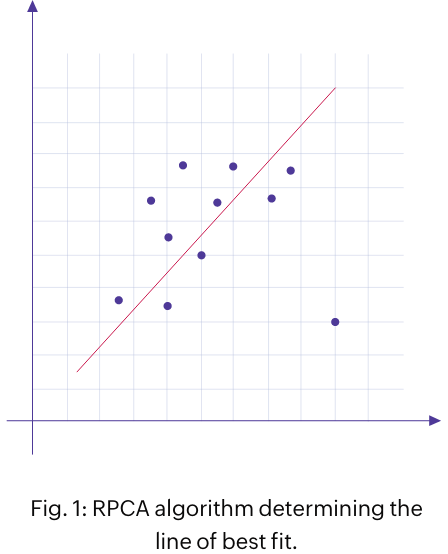
RPCA
This method is a variation of a popular technique, principal component analysis. Here, the ML algorithms look at the historical data to determine the line of best fit (as shown in the figure 1). The observed events are considered as the matrix summation of expected and outlier events. The outliers that deviate from the predicted line of best fit are considered to be anomalous. The RPCA method is used for identifying time and count anomalies.
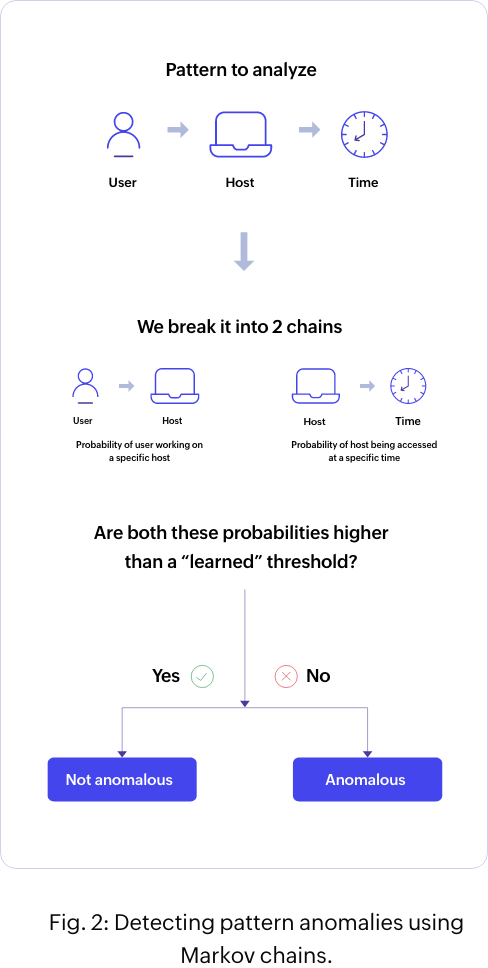
Markov chains
A Markov chain is characterized by a sequence of events in which the probability of the next event is entirely dependent on the state of the current event. Here, the algorithm compares each action of the user or the host against a list of possible actions, and over time, identifies each event with low probability as an anomaly. You can determine pattern anomalies using this method.
In Markov chains, the pattern of interest is divided into two consecutive actions, and the algorithm checks to see if the probability of the second action occurring after the first is reasonably probabilistic. The algorithm relies on historical behavior to determine this probability.
For example, John has performed a software installation at an unusual time. In this case, the pattern to be analyzed is: Username > Host name > Time.
To implement Markov chains for this scenario, you'll need to split the pattern into two parts:
Part 1: Username > Host name
Part 2: Host name > Time
The algorithm first checks whether the probability of the user (John) accessing the host (server) is probable, and then checks whether it's acceptable for the host to be accessed at that particular time (see figure 2). If the algorithm identifies either of these actions as unexpected, then this pattern is deemed anomalous.
For further reading, you can download this free e-book:
Convergence of SIEM and UEBA
Gartner considers UEBA as a feature or capability within SIEM solutions, and modern SIEM solutions are designed this way. While there are standalone UEBA solutions, in recent years, security vendors have predominantly integrated UEBA capabilities into their security analytics or SIEM solutions. This convergence represents a formidable synergy in modern cybersecurity.
SIEM platforms collect, correlate, and analyze security event data from various sources, offering insights into potential threats. UEBA enhances SIEM by focusing on user and entity behavior, leveraging advanced analytics to detect anomalies and insider threats. By integrating UEBA capabilities into SIEM, organizations gain a proactive defense mechanism against sophisticated cyberattacks, thereby enabling faster threat detection, efficient incident response, and overall risk mitigation in today's dynamic threat landscape.
UEBA use cases
UEBA can help organizations identify various threats such as malicious insiders, compromised accounts, data exfiltration, and anomalous logons. To do that, they look for the following signs:
Signs of an insider threat
- New or unusual system accesses
- Unusual access times
- Unusual file accesses or modifications
- Excessive authentication failures
Signs of account compromise
- Unusual software running for a user
- Multiple instances of software installed on a host
- Numerous logon failures on a host
Signs of data exfiltration
- An unusual number or type of file downloads
- Multiple removable disk creations by users
- Unusual commands executed by users
- Abnormal host logons
Signs of logon anomalies
- Multiple login failures
- Successful login after multiple login failures
- Login attempts at unusual times
- Logins from unusual locations
- Unauthorized logins or login attempts
Benefits of UEBA to security operations
- It can offer better protection against zero-day exploits for which there are no known signatures yet.
- The activities of each user and entity are compared to their corresponding typical, average, or baseline behavior. As such, the number of false positives and false negatives will be reduced when compared to rule-based alerting mechanisms.
- Traditional SIEM solutions treat security mishaps as isolated incidents and send alerts, while UEBA solutions look at security holistically and calculate risk scores for each user, reducing false alerts as a result.
- A UEBA-integrated SIEM solution can detect long-term, malicious lateral movements more effectively than traditional security solutions, and risk scoring helps to keep this in check.
- There is less reliance on IT administrators to develop thresholds or correlation rules to identify threats.
- Risk scoring makes it possible for security experts to focus on the most credible, high-risk alerts.
UEBA today
UEBA continues to evolve as a solution to the growing challenges faced by organizations in identifying and mitigating user-based threats. New techniques and approaches are being developed to stay ahead of emerging threats. Here are some of the newest techniques in UEBA which make it all the more efficient.
Peer group analysis
Peer grouping analysis in UEBA is a technique wherein statistical models are employed to categorize users and hosts that share similar characteristics as one group. The idea behind peer grouping is that, by comparing a user's behavior with that of a relevant peer group, the risk scoring accuracy will increase. There are two different types of peer groups: static and dynamic.
Static peer grouping involves grouping users or entities based on predefined attributes such as department, role, or location. By comparing the behavior of individuals within these static groups, anomalies can be detected. For example, if a user's behavior significantly differs from their peer group, it could indicate a potential security issue, and their risk score will increase accordingly.
Dynamic peer grouping analysis involves dynamically forming groups based on behavioral data collected over time. Unlike the static method, dynamic peer groups are created and analyzed based on patterns of similar behavior rather than grouping based on broad categories such as location. This approach allows for more accurate anomaly detection and reduces the chances of false positives.
While it may seem like the dynamic method of peer grouping is better than the static method, a UEBA-integrated SIEM solution that is capable of building peer groups based on both methods is the most effective option for precise risk assessment and scoring. You can learn more about static and dynamic peer grouping here.
Seasonality
If an activity occurs with a specific degree of regularity—such as hourly, daily, weekly, or monthly—it's considered seasonal. If this seasonal activity occurs out of routine, then it should be considered an anomaly, and your UEBA solution should be able to detect it. For instance, a database that is typically only accessed at the end of the month being accessed mid-month would be considered an anomaly.
If seasonality is not factored in, you may miss vital clues that could have helped you detect and stop an attack, or your security analysts may be inundated with numerous false alerts resulting in alert fatigue. Taking seasonality into account in your UEBA solution will enhance your risk scoring accuracy and reduce false positives. To learn about seasonality in-depth, read this blog.
Custom anomaly modeling and custom risk scoring capabilities
Custom anomaly modeling in UEBA refers to the ability to create personalized models for detecting anomalies specific to an organization's unique environment and requirements. It allows organizations to tailor the UEBA system to their specific needs and better identify deviations from normal behavior. Based on the parameters you choose, the algorithm will analyze behavior and establish the baseline. Anomaly modeling can be customized for time, count, and pattern anomalies.
Custom risk scoring in UEBA involves tailoring the risk scoring methodology to the specific needs and context of an organization. It allows organizations to define their own risk factors and assign appropriate values for the weightage and decay factor of anomalies based on their unique security requirements.
User identity mapping
User identity mapping (UIM) is the process of mapping different user accounts in an enterprise to a base account, such as Active Directory, by matching common attributes. With UIM, the activities of discrete user accounts from different sources are attributed to the one user who is actually performing them. The user accounts that were considered separate and had individual risk scores will now have only one representation and one risk score. The consolidated risk score is calculated from the individual's actions across various accounts (e.g. Windows, Linux, and SQL). You can learn more about UIM here.
UEBA in healthcare
UEBA plays a crucial role in the healthcare industry by providing advanced threat detection and insider threat monitoring capabilities. Healthcare is a popular target of cyberattacks. Attackers are increasingly exploiting medical IoT devices to carry out ransomware attacks. UEBA solutions detect the signs of ransomware (file renames, file accesses, and unusual process executions) in its early stages, and alerts the analysts for effective mitigation. UEBA can be used in the healthcare industry to safeguard confidential patient information, guarantee regulatory compliance, and improve overall security posture. To learn more, read this blog.
UEBA in BFSI
Money is one of the most powerful motivators behind cyberattacks; and the banking, financial services and insurance (BFSI) industry that handles money and monetary transactions more than most other institutions make them a prime target for malicious threat actors. UEBA empowers IT security managers by providing advanced insights into user activities and entity behaviors, allowing them to trace suspicious activities of employees and customer accounts. By leveraging SIEM solutions with UEBA capabilities, financial organizations gain real-time visibility into their IT ecosystems that can help them stay ahead of threats and prevent financial crimes. This approach strengthens fraud detection and insider threat monitoring, while also ensuring regulatory compliance within highly regulated financial environments. To learn more about combating threats with UEBA in the BFSI industry, read this blog.
UEBA in the education sector
Educational institutions store a plethora of sensitive data—including student records, names, addresses, Social Security numbers, medical conditions, financial data, and intellectual property—necessitating robust cybersecurity measures. By leveraging UEBA technology, IT security managers in educational institutions can proactively address evolving cyber threats, bolster overall cybersecurity, and ensure a safe learning environment for all stakeholders. Continuous monitoring and analysis of user behavior facilitated by UEBA makes early threat detection and mitigation possible, enabling educational institutions to mitigate financial, reputational, and legal risks associated with cybersecurity breaches. For more insights, explore our blog.
How to choose the right UEBA solution
Real-time alerts
With alerts, you can receive notifications about anomalies that happen in the network in real time. For example, you might receive a notification email as soon as an anomaly is identified. With real-time alerts, you won’t have to log on to your UEBA solution to check for alerts whenever there is a new risk your network is exposed to.
Data collection and analysis
A UEBA solution should properly collect and analyze the data of users, machines, and other entities in a network, like event logs and packet capture data. Continuous monitoring and analysis of data from different sources will help to detect anomalies easily and instantly.
Customizable anomaly models
All anomaly detection systems offer built-in anomaly models. These are machine learning algorithms that learn the baseline of expected activity for every user and host in the network. If the UEBA solution allows you to train your own anomaly model, it’s called a customizable anomaly model. This enables you to cater to the specific security situation of your company in a better way. You can learn more about anomaly modeling here.
Actionable reports
Gathered data should be consolidated efficiently into easy-to-view reports, and generating actionable reports is another critical function of a UEBA solution. Regularly reviewing reports helps admins spot false flagging within the network and provides insights on how to customize a UEBA solution to comply with an organization’s security norms.
Accurate risk scoring
The UEBA solution must be able to assign a risk score to every user and host in the network to represent the degree of risk posed by an entity. The risk score depends on the extent and type of anomalies that the user or host triggers.
Peer grouping analysis
Peer grouping is the process by which you group users and hosts into distinct peer groups based on their past behavior. If your security analytics platform adopts peer group analysis, it will be able to determine whether a user or host behaves as expected based on the groups it is in. If it doesn’t behave as expected, the system triggers an anomaly alert. By doing this in addition to comparing a user’s or host’s behavior to its own baseline, peer group analysis helps reduce the number of false positives. You can learn more about peer group analysis here.
FAQ
- What is the difference between UBA and UEBA?
-
While user behavior analytics (UBA) and user and entity behavior analytics (UEBA) may look similar, they differ in their focus and scope. UBA primarily focuses on analyzing the behaviors of individual users within an organization's network. UBA typically does not extend its analysis to non-human entities like servers or networking devices. UEBA, on the other hand, leverages machine learning algorithms to correlate and analyze behaviors across users and entities (servers, applications, devices), enabling more comprehensive threat detection and response capabilities.
- What is the difference between NTA and UEBA?
-
Network traffic analysis (NTA) involves monitoring and analyzing network traffic patterns and behaviors to identify suspicious or malicious activities. This includes inspecting network packets, flow data, and metadata to detect intrusions or indicators of compromise (IoCs) within the network infrastructure. Simply put, NTA identifies threats only at the network level, whereas UEBA works more holistically. UEBA detects deviations from normal behavioral patterns at a higher level, helping identify insider threats, compromised accounts, zero-day attacks, and abnormal access patterns across users and entities.
- What is the difference between UEBA and EDR?
-
UEBA and endpoint detection and response (EDR) serve different purposes but are complementary in a layered security strategy. UEBA excels at analyzing behavior across users and entities to detect broader, more strategic threats, while EDR focuses on endpoint-level detection, response, and remediation of threats specifically targeting endpoints such as laptops, desktops, servers, and mobile devices. Together, they enhance an organization’s ability to detect and respond to both external and internal threats effectively.
- How does UEBA or anomaly detection contribute to threat mitigation?
-
Anomalies often serve as early warning signs of potential cyberattacks. By identifying deviations from normal behavior, UEBA can help organizations detect threats—like abnormal logon behavior, malware, credential theft, insider threats, unauthorized access, and privilege abuse—before they escalate. Such quick detection will enable security teams to achieve faster resolution, thus decreasing the mean time to respond (MTTR) to security incidents.
- What is the difference between UEBA and traditional security tools?
-
Unlike traditional rule-based tools, UEBA leverages machine learning to adapt to evolving threats and user behavior, reducing false positives and detecting sophisticated attacks that bypass predefined rules. A security information and event management (SIEM) solution with UEBA capabilities can leverage the advantage of both predefined and custom correlation rules to identify known cyberattacks, as well as detect zero-day threats and advanced persistent threats, making it the ideal solution for enhancing the security posture of organizations.
- Will UEBA replace other security tools?
-
No, UEBA complements existing tools like firewalls, SIEM, and endpoint detection by providing an additional layer of behavioral analytics. So, organizations should use at least a UEBA solution—if not a UEBA-integrated SIEM solution—in tandem with other cybersecurity tools to fortify their security.
- Does UEBA generate false positives?
-
While UEBA is designed to minimize false positives compared to traditional threat detection tools, occasional false alerts can occur, especially during the initial learning phase or when abrupt user behavior changes are legitimate. UEBA solutions usually require two weeks of training (learning users' behavioral patterns) to establish the baseline and discern anomalies in user behavior.

Click here to download this content in PDF format




