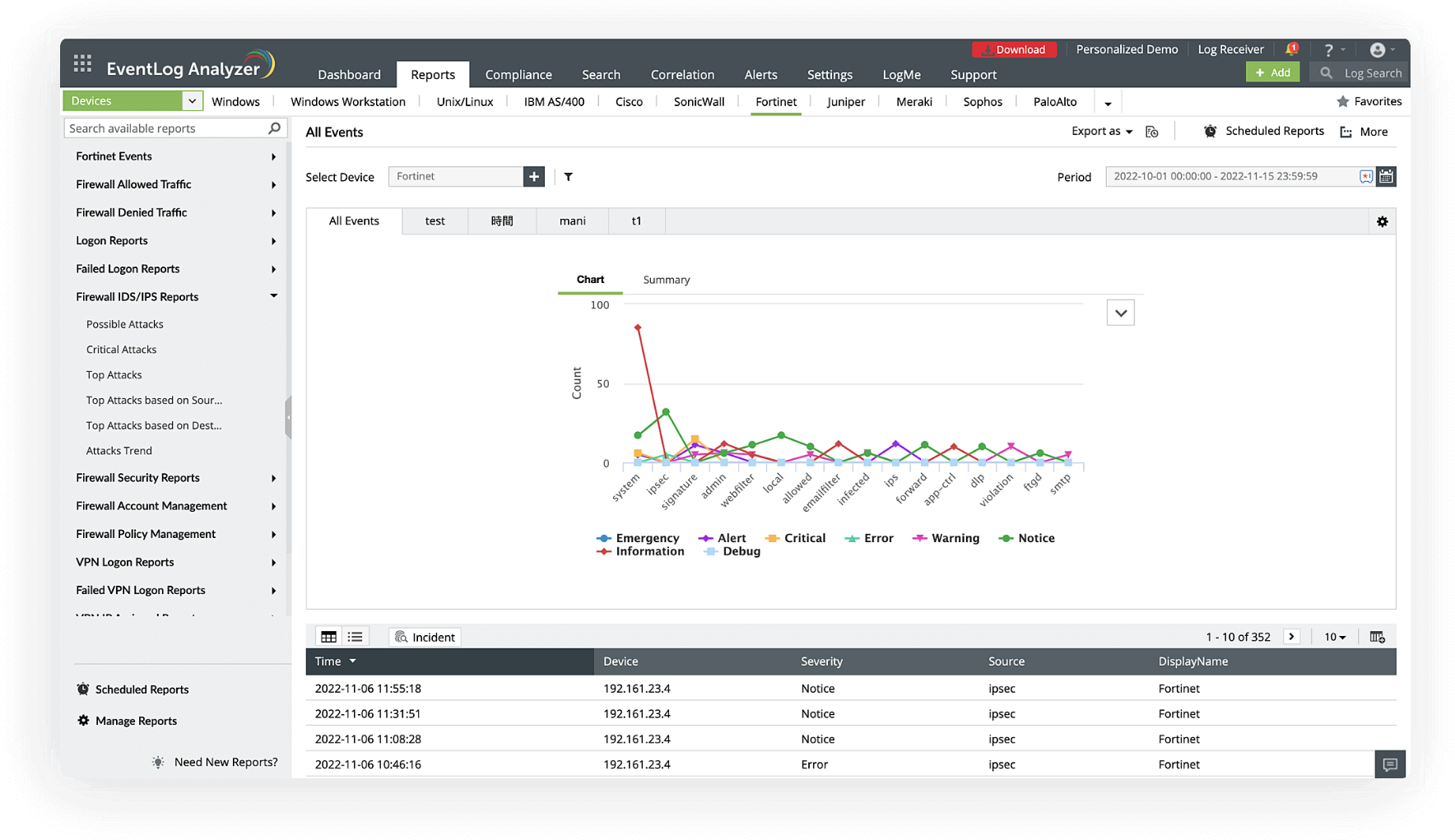
Firewalls offer visibility into the source and type of network traffic entering your organization's network. This makes firewall logs a vital source of information, including details such as source addresses, destination address, protocols, and port numbers for all connections. This information can provide insights into unknown security threats and is a vital tool in threat management.
EventLog Analyzer is a central log management solution that collects logs from your firewall devices and organizes them in a single location. This solution is also a firewall auditing tool that makes it easy for security admins to monitor firewall logs, conduct firewall analysis, and detect abnormalities. EventLog Analyzer uses correlation and real-time alerts to actively detect and mitigate potential threats.
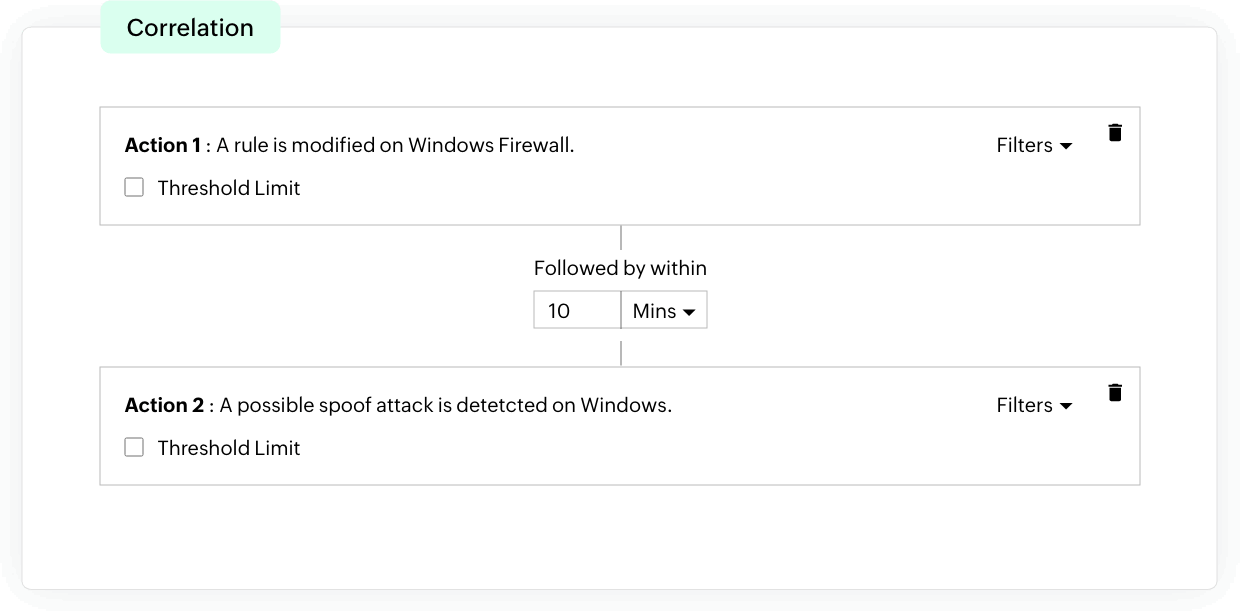
EventLog Analyzer offers an effective incident detection process through event correlation. With the help of built-in correlation rules, you can detect security threats in firewall events. When any suspicious activity is spotted, instant alerts are sent out to security admins. This helps speed up the response process, alerting your admins to possible threats at their earliest stages so they can effectively protect your organization's network from experiencing major damage.
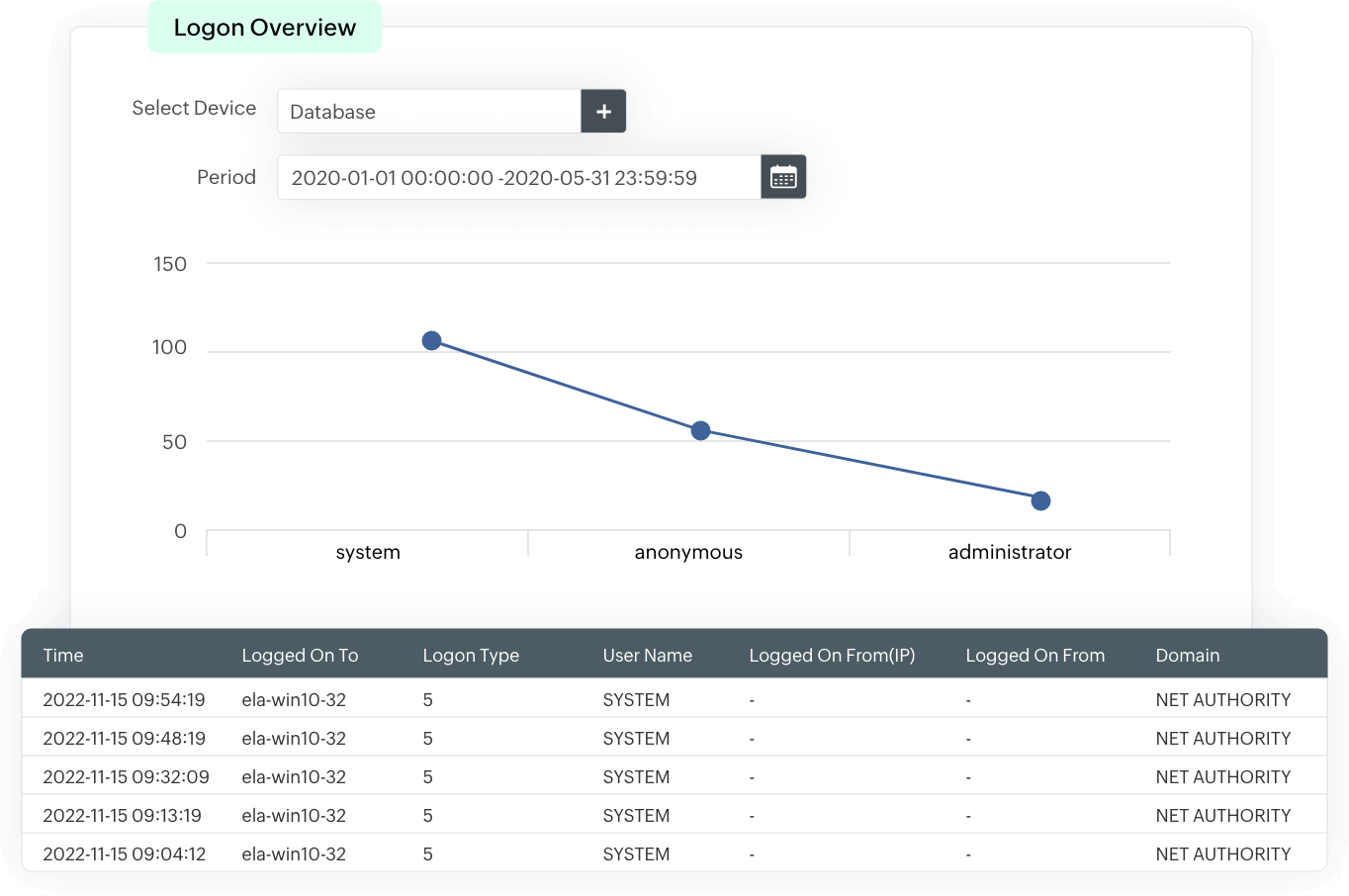
The solution provides insights to successful and failed user logons in the form of analytical reports. These reports include information on the source of a logon event, time of occurrence, and more. Events are consistently monitored to identify login patterns, and used as a baseline to detect suspicious login attempts that could indicate an attack or an insider threat.
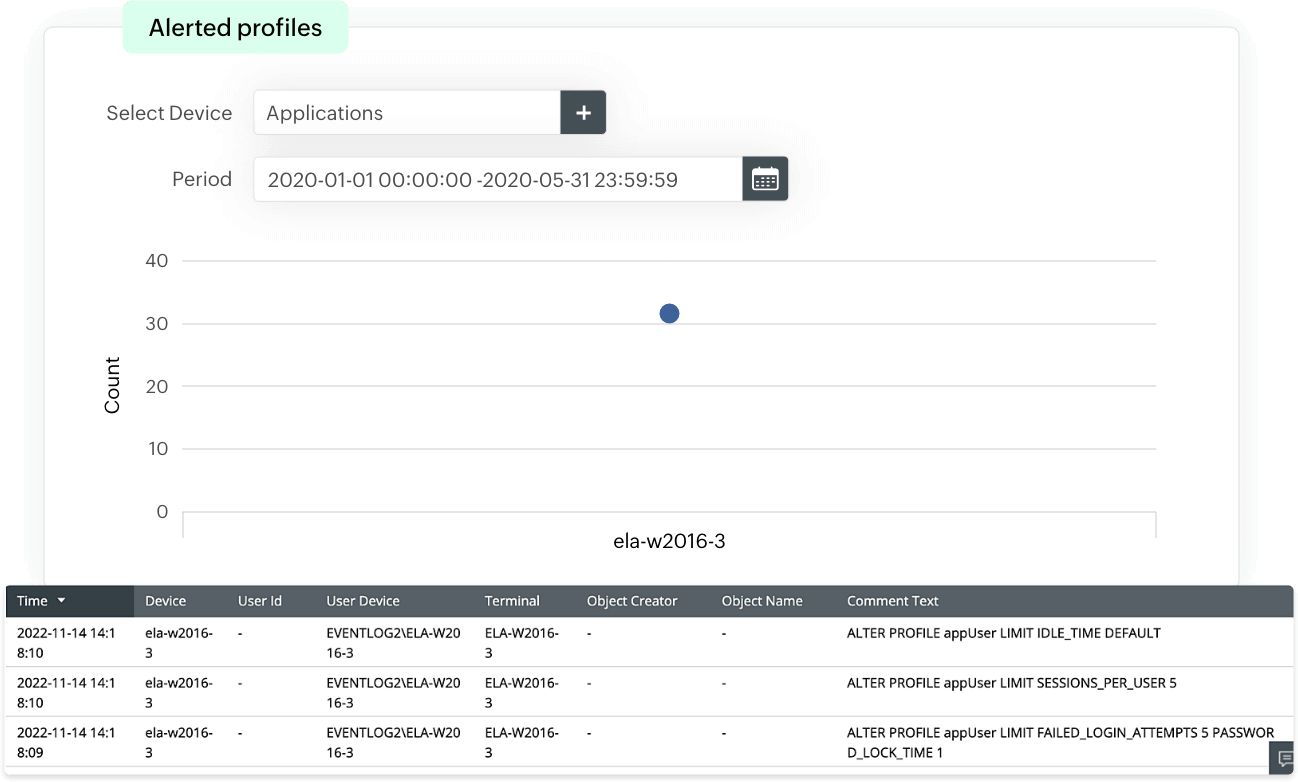
These reports provide insights into the addition, modification, disabling, or deletion of users along with user privilege level changes, which provides visibility into user account activities. EventLog Analzyer uses this information to detect any suspicious or unusual user account activity, and identify any insider threats or privilege escalation attempts.
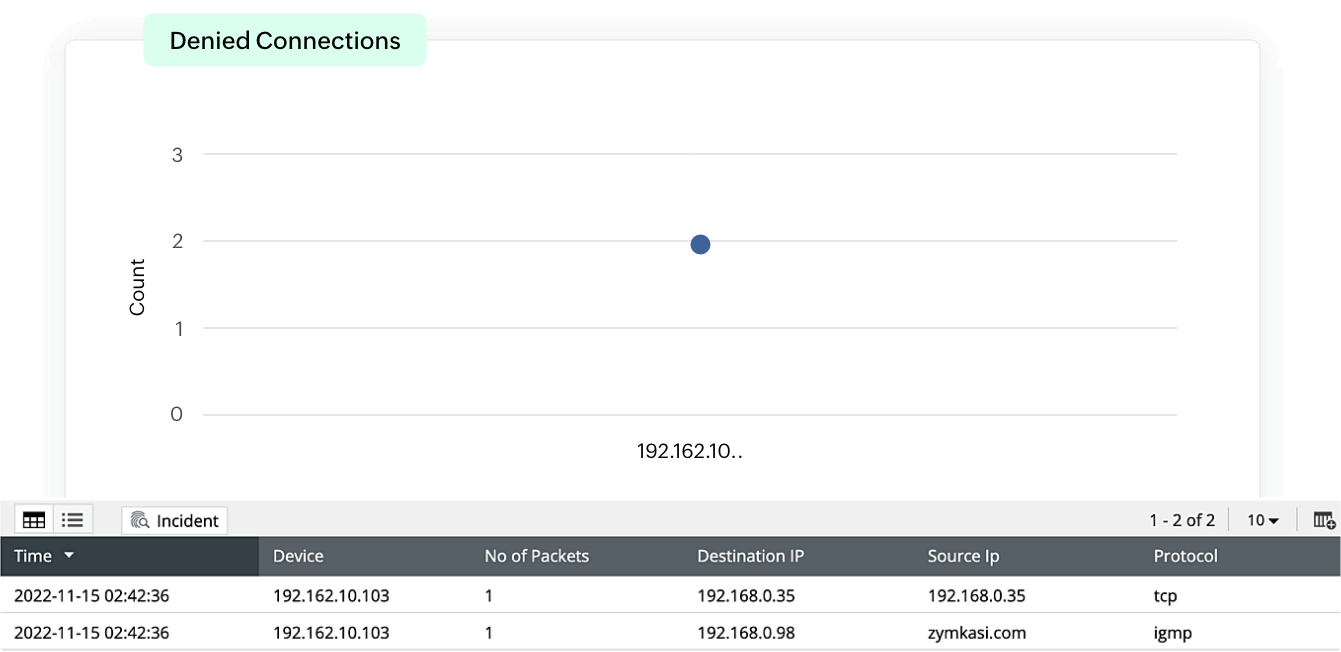
EventLog Analyzer provides traffic information from allowed and denied connections. The detailed information provided by these reports is categorized and visually represents the traffic based on sources, destinations, protocols, and ports along with timestamps, enabling security admins to track network traffic. This helps identify trends in abnormal traffic from suspicious sources, and prevents threat actors from gaining access to the network.

EventLog Analyzer offers an effective incident detection process through event correlation. With the help of built-in correlation rules, you can detect security threats in firewall events. When any suspicious activity is spotted, instant alerts are sent out to security admins. This helps speed up the response process, alerting your admins to possible threats at their earliest stages so they can effectively protect your organization's network from experiencing major damage.

The solution provides insights to successful and failed user logons in the form of analytical reports. These reports include information on the source of a logon event, time of occurrence, and more. Events are consistently monitored to identify login patterns, and used as a baseline to detect suspicious login attempts that could indicate an attack or an insider threat.
Firewall logs contain information on an event such as:
The firewall logs are parsed and analyzed by either a firewall analyzer or a log management solution to identify patterns or anomalies to detect an attack, and generate reports. The information contained in the firewall logs are analyzed to provide insights into network traffic patterns, security events, and connection statistics.
Monitoring firewall logs provides insights into network activity and potential security threats. It helps with:
When a firewall log analyzer monitors and analyzes the logs automatically, it helps detect threats in real-time and takes immediate actions to minimize the incident's impact. Automation of firewall log monitoring can be achieved with a firewall log management solution, such as EventLog Analyzer. The solution correlates suspicious events and uses automated workflows to mitigate threats immediately.
EventLog Analzyer offers out-of-the-box support for firewalls, next-generation firewalls (NGFWs), intrusion detection systems (IDS), and intrusion prevention systems (IPSs) from leading vendors.
EventLog Analyzer is a centralized log management tool that monitors firewall logs and activity to