Network monitoring with Windows Firewall logs
- Features
- Network monitoring
- What is Windows Firewall?
- Firewall profiles
- How do you analyze Windows Firewall logs?
- What are the key uses of a firewall log analysis tool?
What is Windows Firewall?
Windows Firewall, also called Windows Defender Firewall, is a built-in security feature that actively monitors and analyzes the network traffic that passes through the Windows Firewall on a computer running the Windows operating system. Its main purpose is to act as a barrier between your computer and the internet or other networks, allowing you to control which programs and services can communicate over the network.
Analyzing Windows Firewall logs is essential for gaining insights into network behavior and ensuring that the firewall is effectively protecting your computer. The Windows Firewall generates logs that record allowed and denied connections, along with other firewall-related details. These logs play a vital role in monitoring, troubleshooting, and identifying any potential security threats.
Firewall profiles
Windows Firewall is comprised of three firewall network profiles: Domain, Private, and Public. These profiles help define the level of security and access controls applied based on the type of network your computer is connected to.
- Domain profile The domain profile is designed so that the system is connected to a domain network of an organization and ensures that the host system can authenticate to a domain controller. This profile cannot be set manually. For example, a company laptop authenticating to the domain controller within the office network is selected automatically to allow more inbound connections for file sharing.
- Private profile The private profile is a user-assigned profile, and the system is connected to a private/ home network. It can be manually set by an administrator. For example, consider a remote employee's computer connected to a private home network.
- Public profile The default or public profile is designed for a public network; picture a laptop connected to an open Wi-Fi network in a coffee shop or an airport. The public profile might have stricter firewall settings compared to the private profile, limiting network visibility and preventing certain types of incoming connections.
How do you analyze Windows Firewall logs?
Analyzing Windows Firewall logs is necessary as this helps us understand network activity, identify potential security incidents, and maintain a secure computing environment. This can be accomplished by analyzing log data manually or using automated tools.
Manual Windows Firewall log analysis
Analyzing the firewall logs manually involves accessing the log files that are stored in the "%windir%\system32\LogFiles\Firewall\ directory", typically named "pfirewall.log". The Windows Firewall logs can be viewed either in a Notepad++ or a MS Excel file to extract fields and analyze them for troubleshooting. Understanding the log entry format is crucial, as each entry contains information such as:
- Date and time: Timestamp indicating when the event occurred.
- Action: Whether the connection was allowed or blocked.
- Protocol: The communication protocol used include TCP and UDP.
- Source and destination IP addresses: Identifies the source and destination of the network traffic.
- Source and destination port numbers: Specifies the ports used in the connection.
- Result: Provides additional details about the connection attempt.
To extract any information from the log files, filter out the logs based on timestamps, actions (allowed/blocked), source and destination IP addresses, and specific ports or protocols.
A sample firewall log entry looks like this:
2022-01-15 12:30:45 | Allowed | TCP | 192.168.1.2 | 203.0.113.5 | 80 | 443 | Successful Connection
The firewall log is divided into two parts: the header and the body. The header has fixed details about the log version and available fields. The body logs information about attempted traffic circumventing the firewall. The new entries are added at the bottom, and in instances where no entries exist for a particular field, it is denoted by a hyphen (-). This standardized format enables administrators to analyze and interpret the logs effectively, gaining insights into network activity and potential security incidents.
To extract specific information from log files:
- For action, protocol, source/destination IP, and Port numbers: Utilize text search functions or Excel formulas to extract relevant details.
- For result: Analyze the log entry message for additional information on the connection attempt.
Analyzing the logs manually is daunting as each log entry needs to be cross-checked. While manually troubleshooting issues related to Windows Firewall is important, it doesn't necessarily help with overall security monitoring due to the volume of network devices, data, or incoming traffic in an organization. Security analysts often need to rely on automatic tools.
Automatic analysis using log analyzer tools
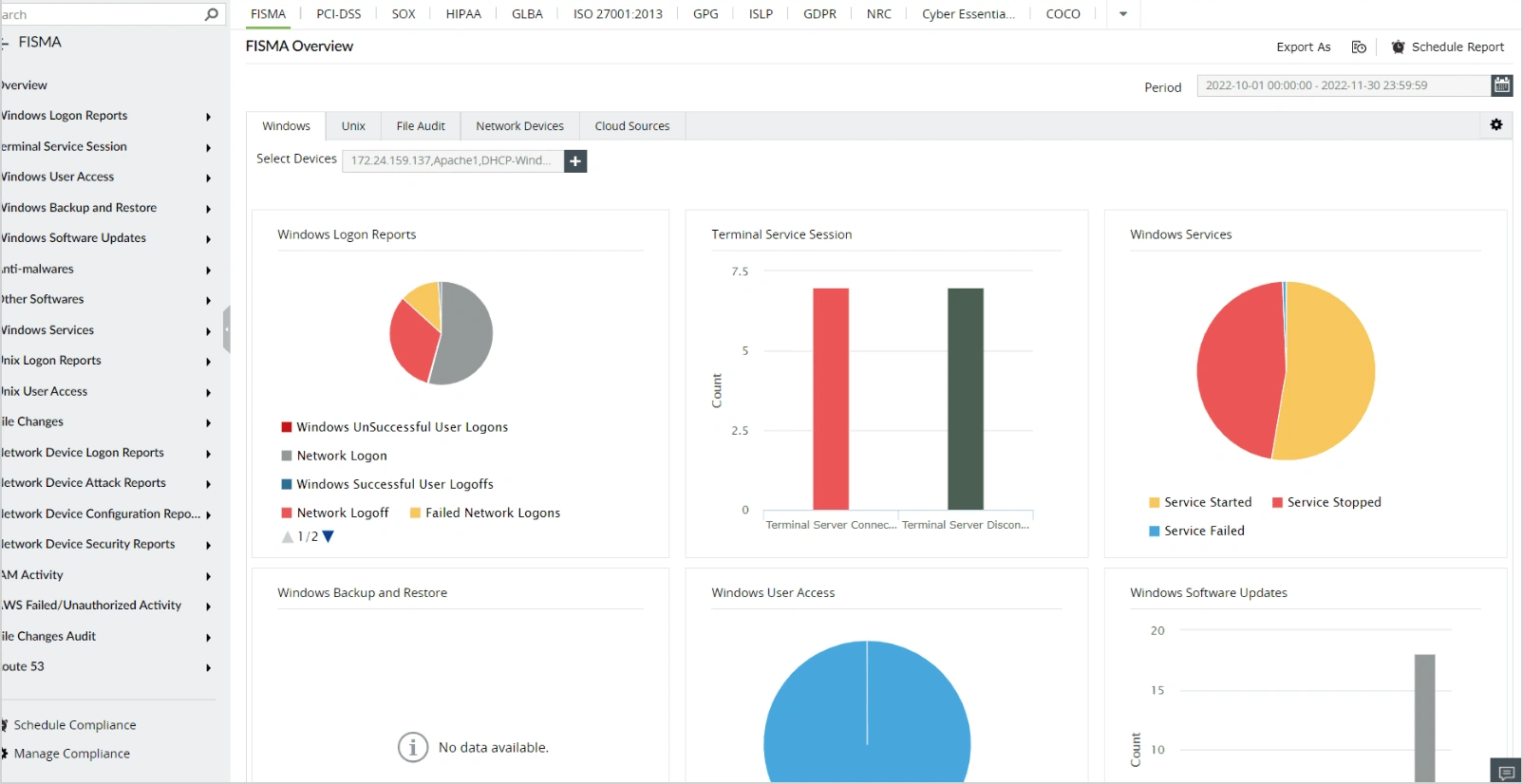
Using a Windows Firewall log analyzer, such as ManageEngine EventLog Analyzer, you are empowered to monitor Windows Firewall activity and receive comprehensive, predefined graphical reports, as well as analyze this information to gain useful insights. Auditing changes made to firewall configurations allows you to gain full control over the firewall settings and policies. In addition, with the real-time security alerts via SMS or email, any attack on the network can be quickly identified and mitigated.
What are the key uses of a firewall log analysis tool?
A firewall rule change, be it by mistake or with malicious intent, might inadvertently grant access, putting your systems at risk. It is ideal to keep an eye on all firewall rule changes, including rules that are added, deleted, or modified. With the help of EventLog Analyzer, organizations can efficiently conduct Windows Firewall audits and track changes made to settings and configurations, including configuration resets and group policy changes.
Threat detection
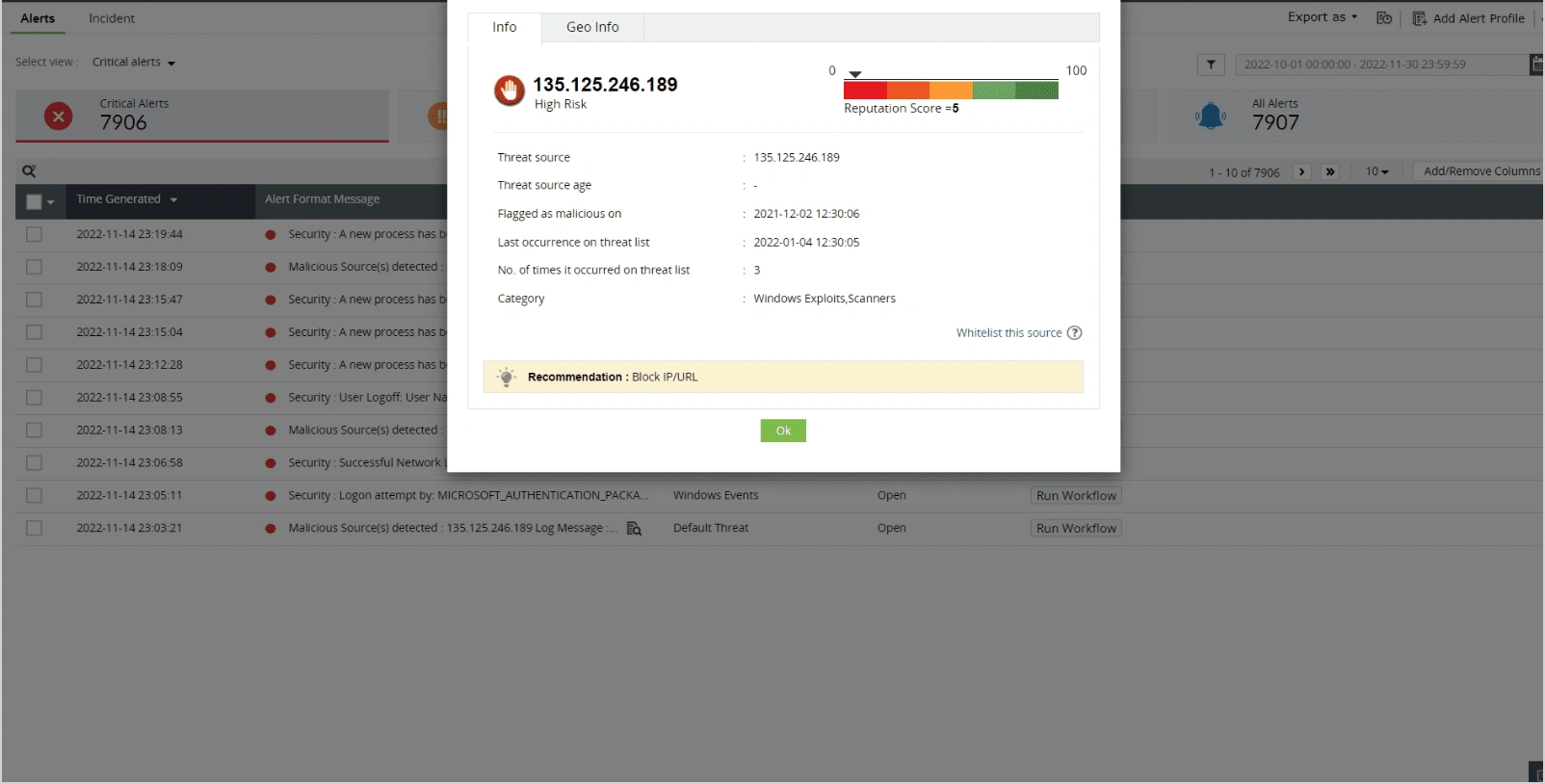
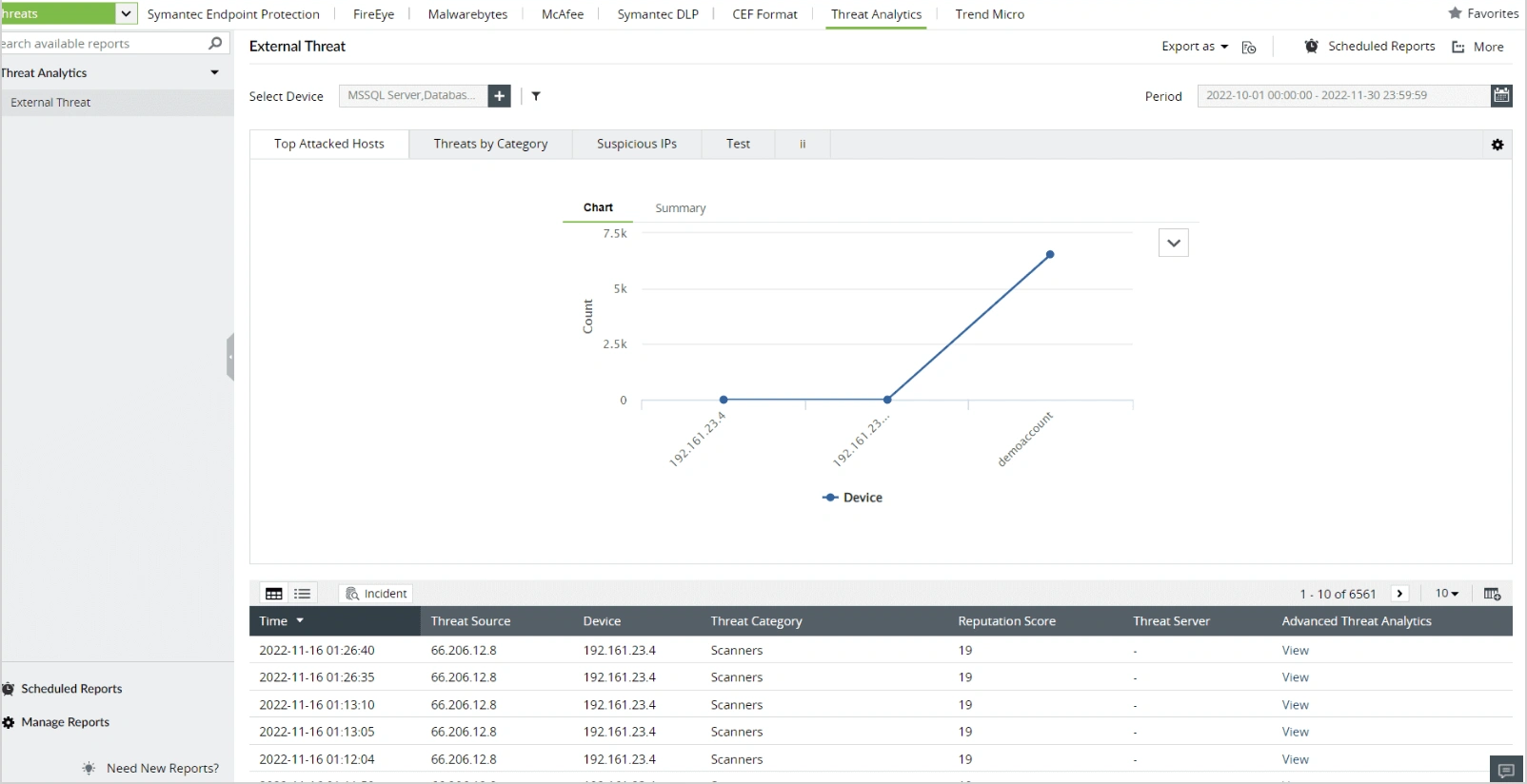
By analyzing the firewall logs for any malicious IP addresses using EventLog Analyzer, organizations can detect cyberattacks like flood attacks, spoof attacks, SYN attacks, DoS or DDoS attacks, Ping of Death attacks, and half scan attacks. Organizations can take necessary actions to avoid further damages. For example, let's look at a DDoS attack, which aims to overwhelm the target system or network by flooding it with an excessive amount of traffic.
With EventLog Analyzer, administrators receive an alert indicating a potential DDoS attack when it detects an unusually high number of connection attempts within a short timeframe from different IP addresses. Administrators can then take immediate actions, like implementing firewall rules to block the malicious IP addresses, or diverting traffic through DDoS mitigation services, thus mitigating the impact of the attack.
Forensic analysis
Utilizing EventLog Analyzer, Windows Firewall logs are collected, archived, and subject to forensic analysis. This process enables security analysts to detect the root cause of cyberattacks, refine firewall configurations to reduce false positives, and assess the performance of security rules.
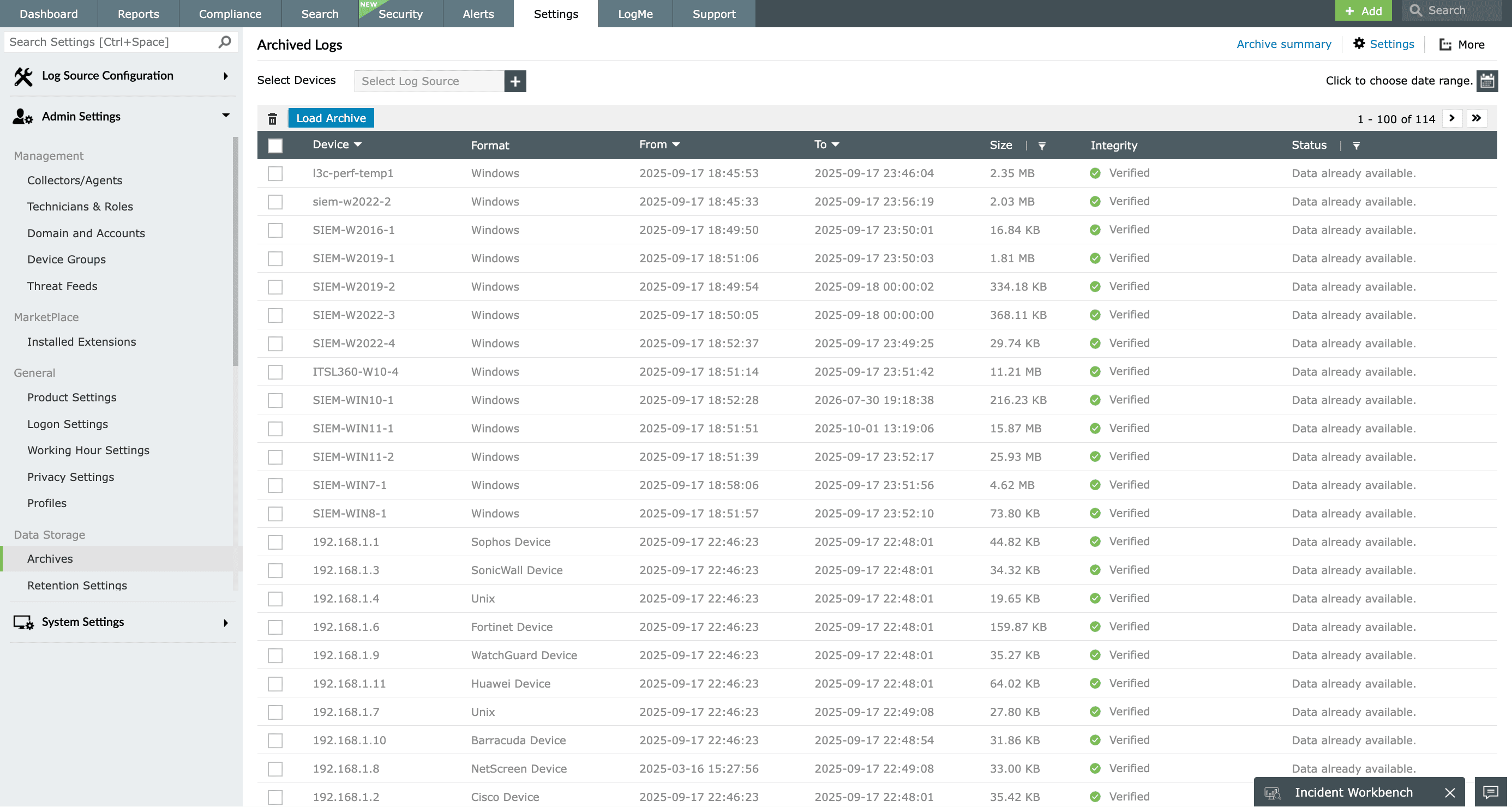
Incident response and real-time alerts
The Windows Firewall log analyzer acts as a vital tool for incident response and real-time alerts. The event correlation engine identifies malicious activity taking place in your Windows Firewall with its built-in correlation rules. Security analysts can monitor for any patterns that might indicate a data breach or any cyberattacks like repeated denied connections or unexpected access attempts.
EventLog Analyzer helps automated incident workflows get executed once the alerts are triggered. This helps security analysts save time, ensure all incidents have been addressed, and protect the organization from any damage.
Compliance
EventLog Analyzer, which also acts as a firewall auditing tool, ensures it is easy to monitor network traffic and security events, as well as access control. Organizations can not only protect sensitive data, but also maintain the records and audit trails required to prove compliance during regulatory assessments and audits. This proactive approach to security aligns with the objectives of compliance mandates like PCI DSS, GLBA, HIPAA or SOX, ultimately reducing the risk of data breaches and penalties associated with non-compliance.