IT admins are often tasked with applying fine-grained password policies in AD to enforce different password requirements for various users or groups based on their security needs, roles, or departments. This can be accomplished through several methods: the native Active Directory Administrative Center (ADAC), PowerShell, or self-service password management solutions like ManageEngine ADSelfService Plus. Let's explore these different approaches below.
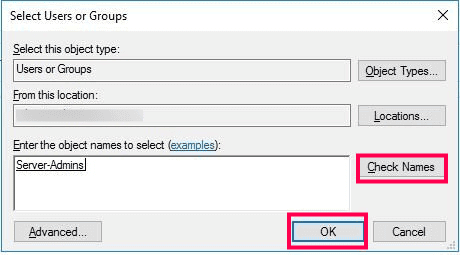
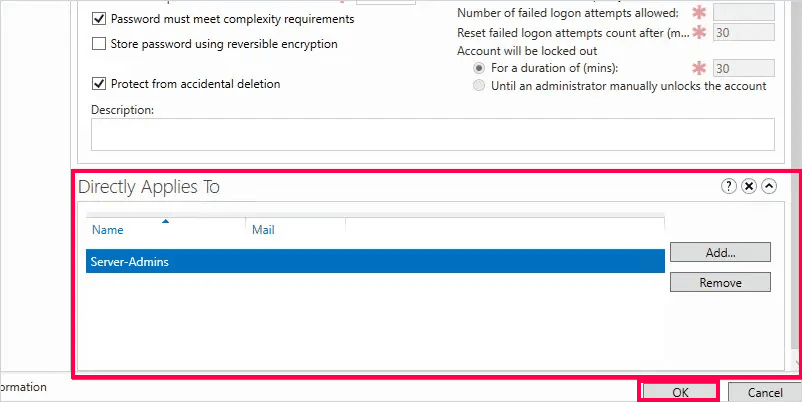
Before using the Add-ADFineGrainedPasswordPolicySubject cmdlet, please verify that the following prerequisites are satisfied:
The Add-ADFineGrainedPasswordPolicySubject cmdlet can be used in PowerShell to assign an existing fine-grained password policy to users or groups in AD. The syntax for it is given below:
Add-ADFineGrainedPasswordPolicySubject
[-WhatIf]
[-Confirm]
[-AuthType <ADAuthType>]
[-Credential <PSCredential>]
[-Identity] <ADFineGrainedPasswordPolicy>
[-Partition <String>]
[-PassThru]
[-Server <String>]
[-Subjects] <ADPrincipal[]>
[<CommonParameters>] The following table contains some parameters that can be used along with the Add-ADFineGrainedPasswordPolicySubject cmdlet to assign fine-grained password policies to users or groups in AD efficiently.
| Parameter | Description |
|---|---|
| -Identity | This specifies the fine-grained password policy to be assigned. You can identify the policy using its distinguished name, globally unique identifier (GUID), security identifier (SID), or policy name. |
| -Subjects | This specifies one or more users or groups that will receive this password policy. It accepts user or group distinguished names, GUIDs, SIDs , or Security Account Manager (SAM) account names. You can provide multiple subjects as a comma-separated array. |
| -AuthType | This defines the authentication method for connecting to AD. The valid options are Negotiate (the default, which uses Kerberos or NTLM) or Basic (basic authentication, which requires SSL). Most environments use the default Negotiate. |
| -Credential | This provides alternate credentials for running the cmdlet if you need to use a different account than the one currently logged in. Use the Get-Credential command to create a PSCredential object, which is useful when running the cmdlet from a workstation or with a non-admin account. |
| -PassThru | This returns the fine-grained password policy object after the assignment is complete, showing you what was modified. Without this parameter, the cmdlet runs silently with no output. |
| -Server | This specifies which domain controller to connect to for executing this command. It can be a fully qualified domain name, Network Basic Input/Output System name, or IP address. If no server is specified, the cmdlet uses the default domain controller. |
| -WhatIf | This performs a simulation showing what would happen if the command were to run, without making any actual changes. This is useful for verifying your command before applying it to the production environment. |
| -Confirm | This prompts you for confirmation before executing the command, adding an extra safety check before making changes to your password policy assignments. |
Assigning a fine-grained password policy to a security group
To assign a fine-grained password policy to a security group, use the following cmdlet:
Add-ADFineGrainedPasswordPolicySubject -Identity <'policy_name'> -Subjects <'group_name'> For this cmdlet, replace policy_name with the name or distinguished name of your fine-grained password policy and replace group_name with the security group that should receive this policy.
Bulk assignment of a fine-grained password policy using PowerShell
To assign a single password policy to multiple users and groups simultaneously, use the following cmdlet:
# Define the policy to be assigned
$PolicyName = <'policy_name'>
# Define multiple users and groups that need this policy
$Subjects = @(
<'subject_1'>,
<'subject_2'>,
<'subject_3'>,
<'subject_4'>,
<'subject_5'>
)
# Apply the policy to all subjects at once
Add-ADFineGrainedPasswordPolicySubject -Identity $PolicyName -Subjects $Subjects
Write-Host "Successfully assigned $PolicyName to $($Subjects.Count) users and groups" -ForegroundColor Green For this cmdlet, replace policy_name with the name of your fine-grained password policy and replace subject_1 through subject_5 with the distinguished names, SAM account names, or group names that should receive this policy.
Assigning different policies to different groups based on organizational requirements
To assign different policies to different groups based on organizational requirements, use the following cmdlet:
# Define department-to-policy mappings
$PolicyAssignments = @(
@{Policy=<'policy_1'>; Group=<'group_1'>},
@{Policy=<'policy_2'>; Group=<'group_2'>},
@{Policy=<'policy_3'>; Group=<'group_3'>},
@{Policy=<'policy_4'>; Group=<'group_4'>}
)
# Loop through each assignment and apply the policies
foreach ($Assignment in $PolicyAssignments) {
try {
Add-ADFineGrainedPasswordPolicySubject `
-Identity $Assignment.Policy `
-Subjects $Assignment.Group
Write-Host "Successfully assigned $($Assignment.Policy) to $($Assignment.Group)" -ForegroundColor Green }
catch {
Write-Host "Failed to assign $($Assignment.Policy) to $($Assignment.Group): $_" -ForegroundColor Red }
} For this cmdlet, replace policy_1 through policy_4 with your fine-grained password policy names and replace group_1 through group_4 with the corresponding groups or users that should receive each policy.
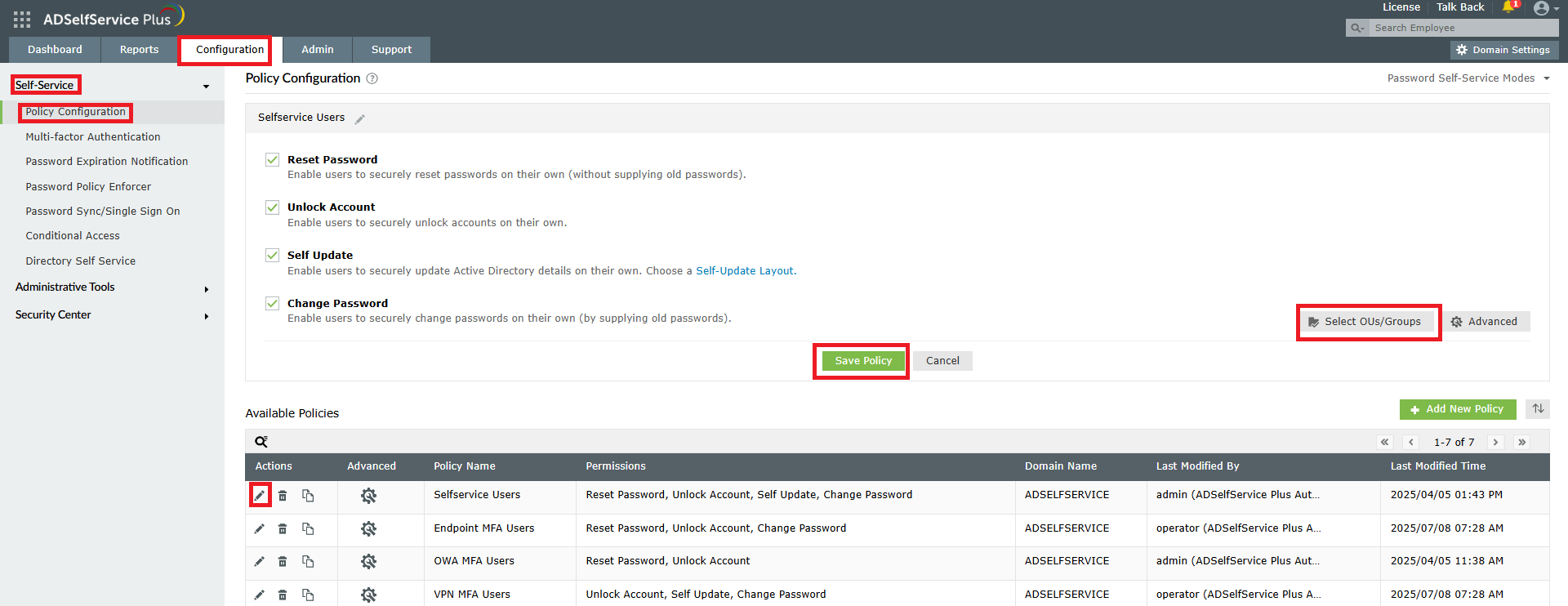
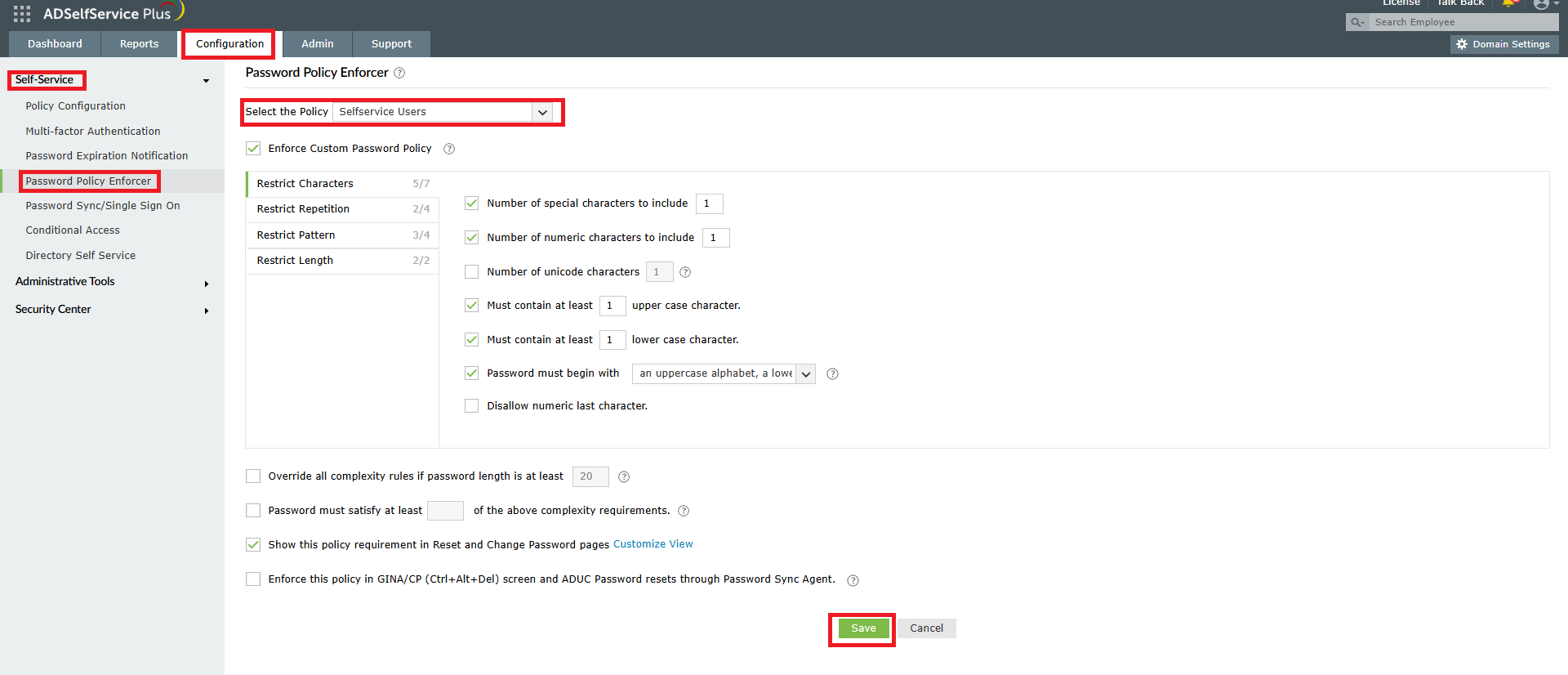
ADSelfService Plus' Password Policy Enforcer helps ensure password compliance throughout your organization by enforcing custom password policies during self-service password resets and changes, preventing weak passwords, and maintaining consistent security standards across your AD environment.