ManageEngine Identity360 is a cloud-native solution that helps enterprises address workforce IAM challenges. The application is accessible over the internet without the need for any software installation.
Identity360 is built upon a resilient SaaS framework, embracing best practices to provide a scalable, highly accessible, and identity-first security solution in the cloud.
The firewall secures all inbound communication to Identity360 service, shielding your applications accessing Identity360 service from malicious or unnecessary network traffic.
The Web Application Firewall (WAF) strengthens application security by filtering HTTP requests. It protects web applications from attacks such as cross-site forgery, cross-site scripting (XSS), file inclusion, and SQL injection.
The Web app cluster is a collection of application servers which is responsible for handling all incoming requests from an external network. This layer is designed with multiple nodes to handle many requests efficiently and to ensure minimal downtime for individual nodes.
The Job server manages backend tasks and plays a crucial role in processing scheduled jobs such as directory sync, bulk operations, etc. without affecting the performance of the main App server cluster.
It securely stores Identity360 data and archives database data for disaster recovery as a precaution against potential risks.
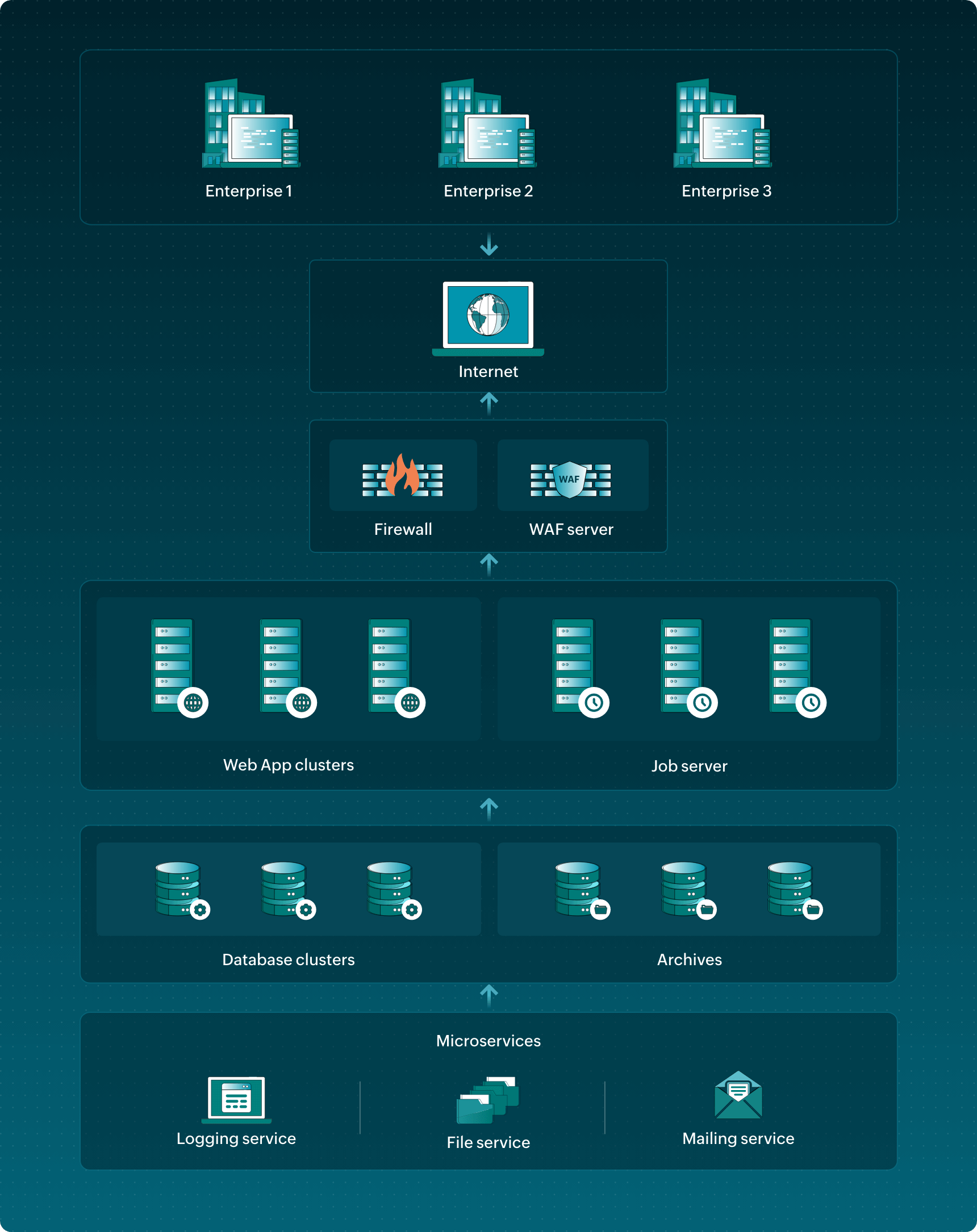
Identity360 is securely hosted within data centers, ensuring that all communications between the user's web interface and the central server are safeguarded by high-level enterprise encryption protocols. Meticulously engineered to provide utmost security at every phase, Identity360 delivers fortified security for user authentication, data transmission, and access through the entire workflow. All sensitive data is securely stored in an encrypted format within the data centers.
The data centers housing customer data were carefully designed to adhere to security best practices at all levels–physical, technical, people, and processes.
The inherent live replication, scheduled backup, and high availability architecture prevents data loss and ensures business continuity.
All customer data is logically partitioned at the software level.
Upon signup, a segmented database is provisioned for your organization by default.
To get started with Identity360, all you need is a standard web browser such as Firefox, Microsoft Edge, or Chrome.