Secure data at rest, in use, and in motion with the help of this unified data visibility and security platform.
Monitor file activities, device usage, and data movement to detect potential insider activity.
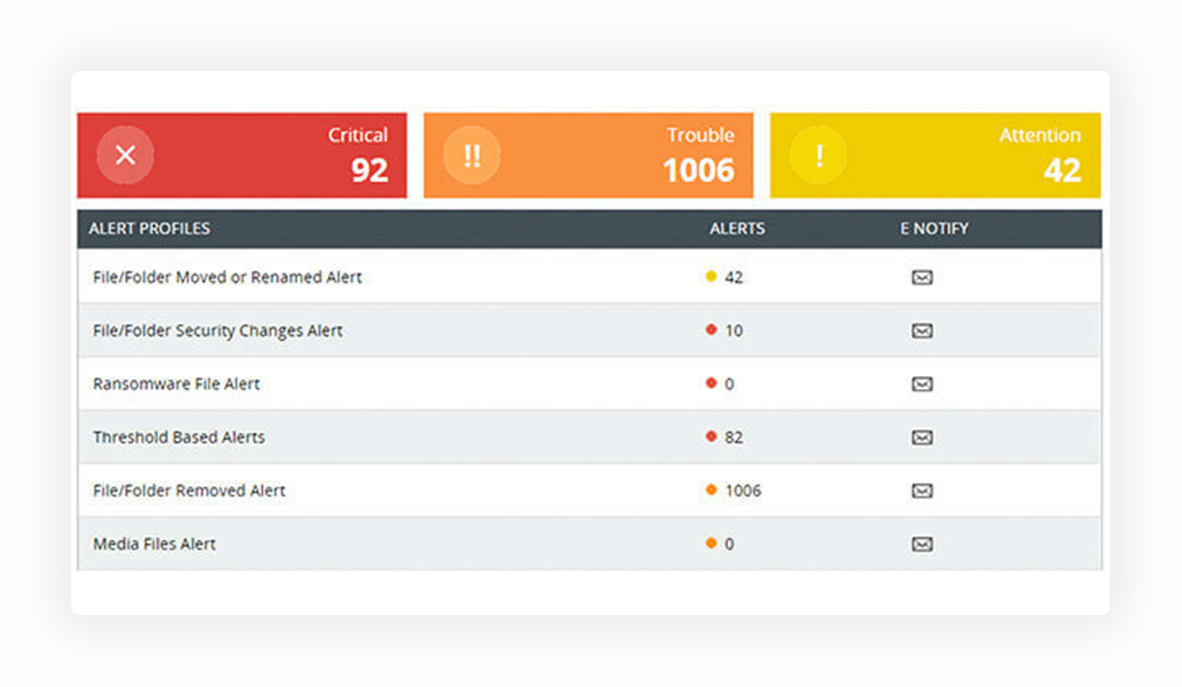
Maintain a detailed audit record of all file activities to reconstruct and analyze security incidents.
Scrutinize suspicious employee activities such as copying high-risk files to USBs, sudden spikes in file renames and deletions, or repeated file permission changes.
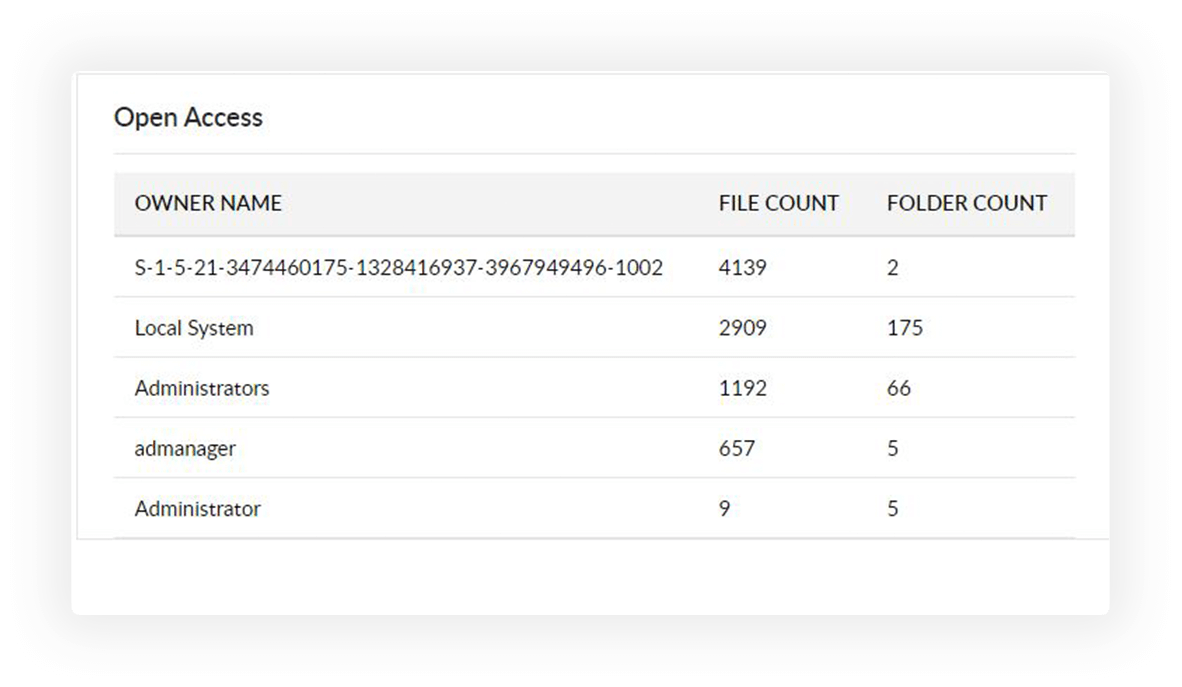
Identify employees with elevated levels of access, like full control and files accessible by everyone, to mitigate instances of permission misuse.
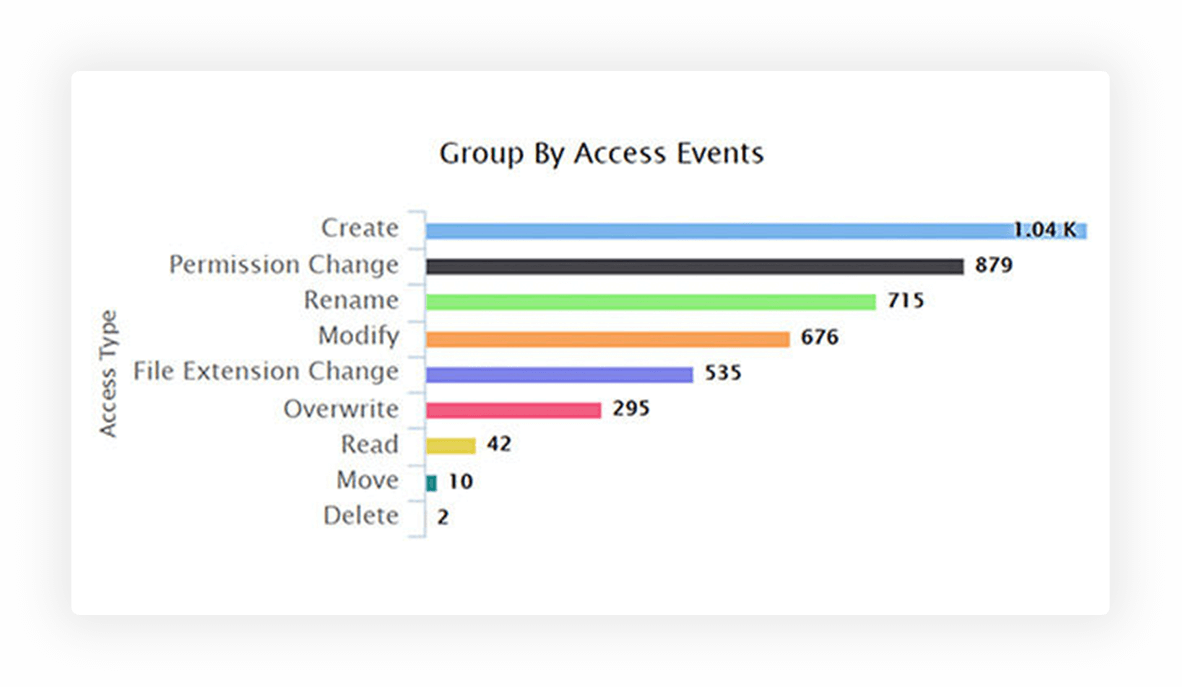
Determine how your users interact with data by monitoring file accesses and data movement across file servers, USBs, and local systems.



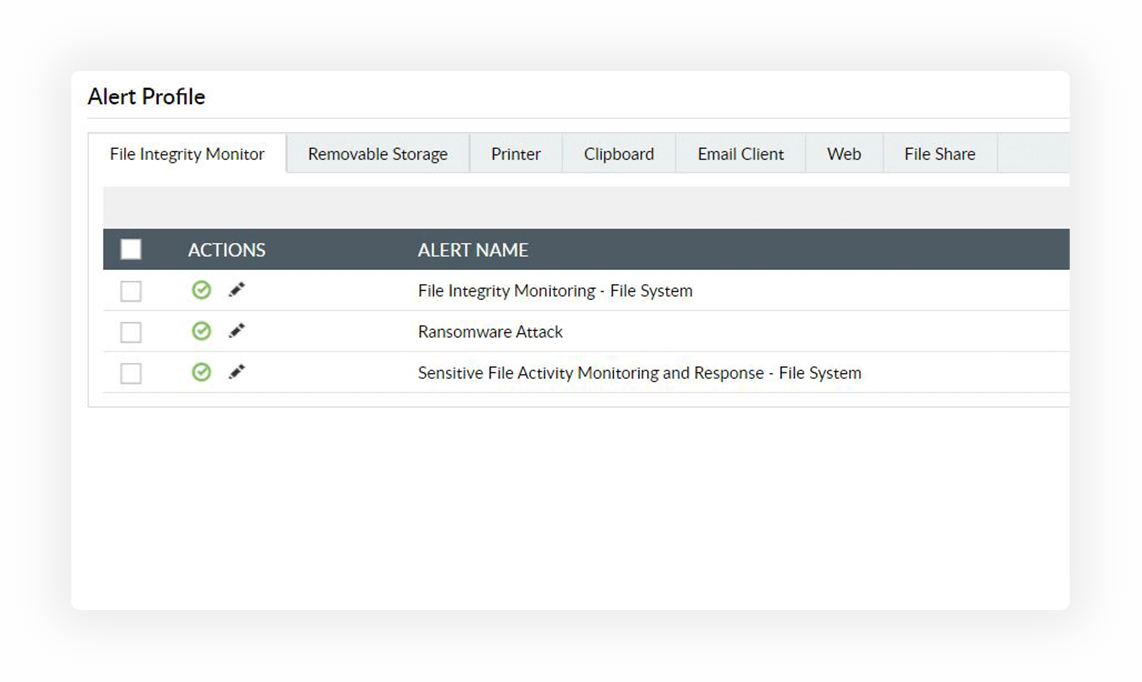
Detect and stop data theft via exit points such as the clipboard, USBs, or email (Outlook) to deter employees with malicious intent.

Use preconfigured data leak prevention (DLP) policies to proactively recognize and respond to signs of compromise such as data exfiltration attempts or failed attempts to access critical data.

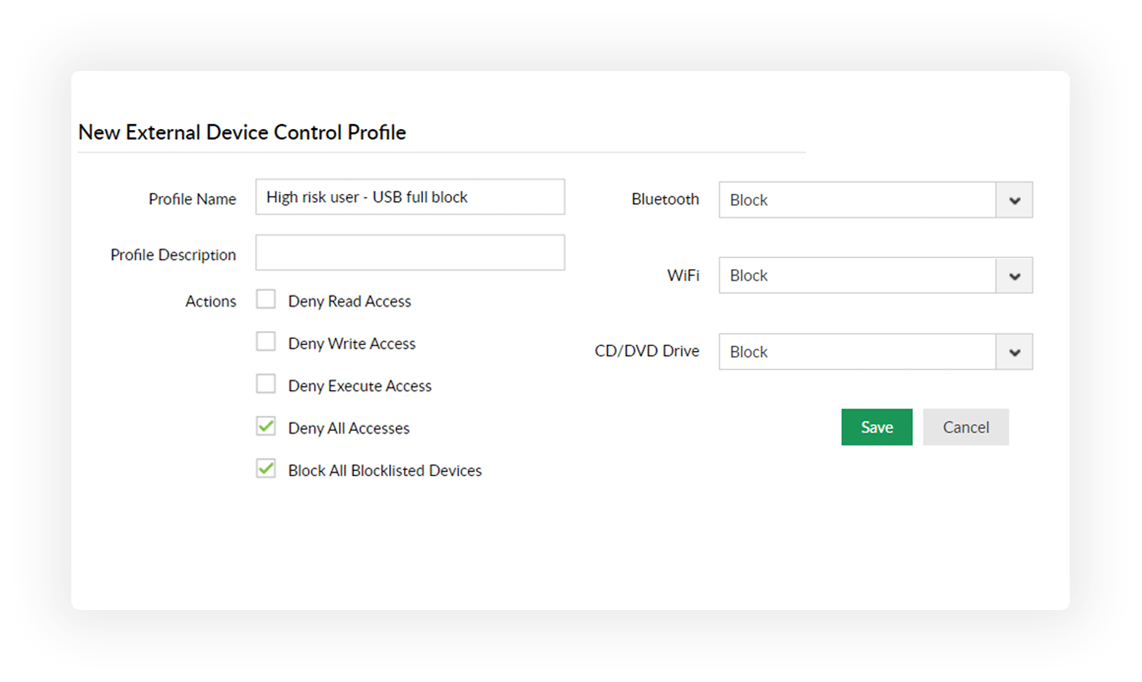
Block the use of high-risk USB sticks by blocklisting them. Also restrict unknown applications and processes within removable storage devices from running.

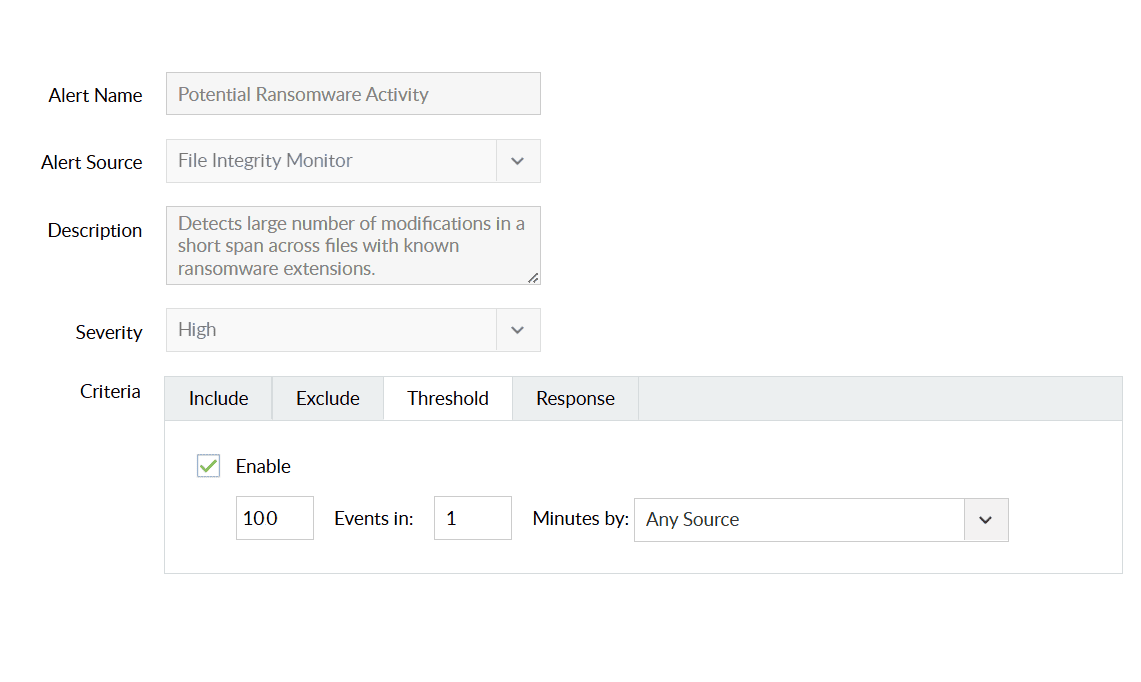
Tackle phishing security threats like ransomware by detecting them in real time and cutting off the infection by isolating the infected devices.
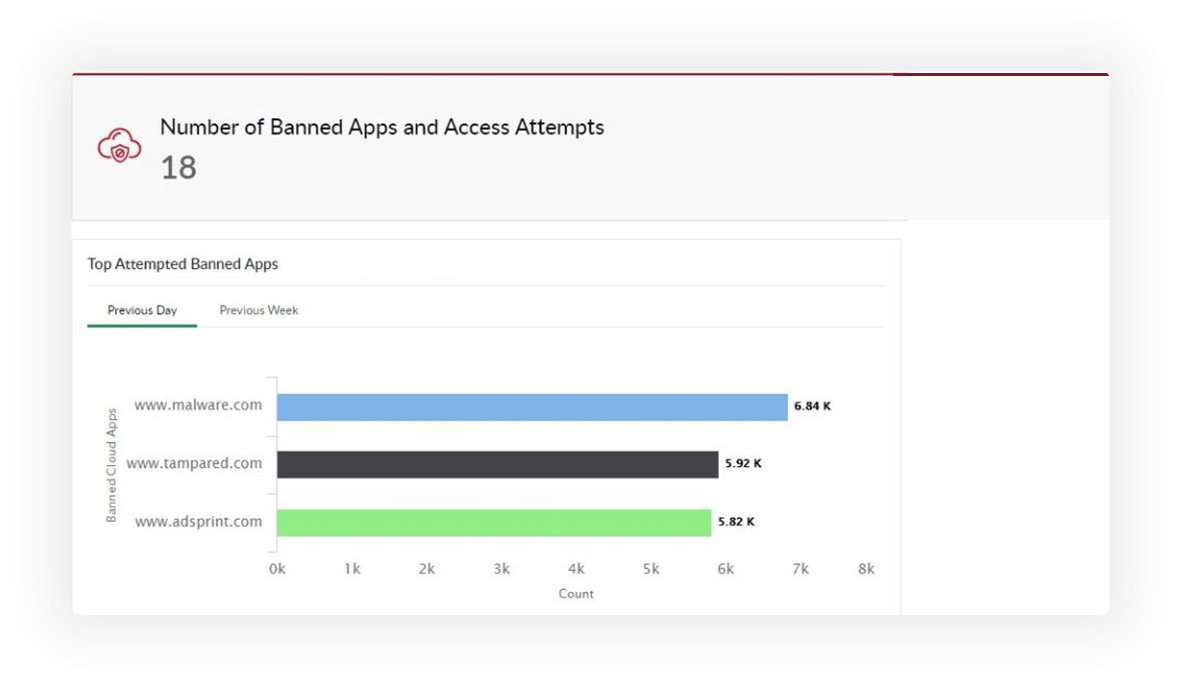
Analyze the various cloud services accessed by your employees, and block requests made to unsafe websites such as spam, malware, and phishing sites.
Identify and classify files with sensitive personal data—such as PII, ePHI, and PCI—and strengthen data security measures across its locations.



Yes, DataSecurity Plus allows you to restrict high-risk file copy actions across local and network shares. Besides blocking, you can also use system prompts to warn employees against making unwarranted copies of business-critical files.
Yes, you can selectively limit the functionalities of USBs, such as making them read-only, stopping executables in USBs from running, and more.
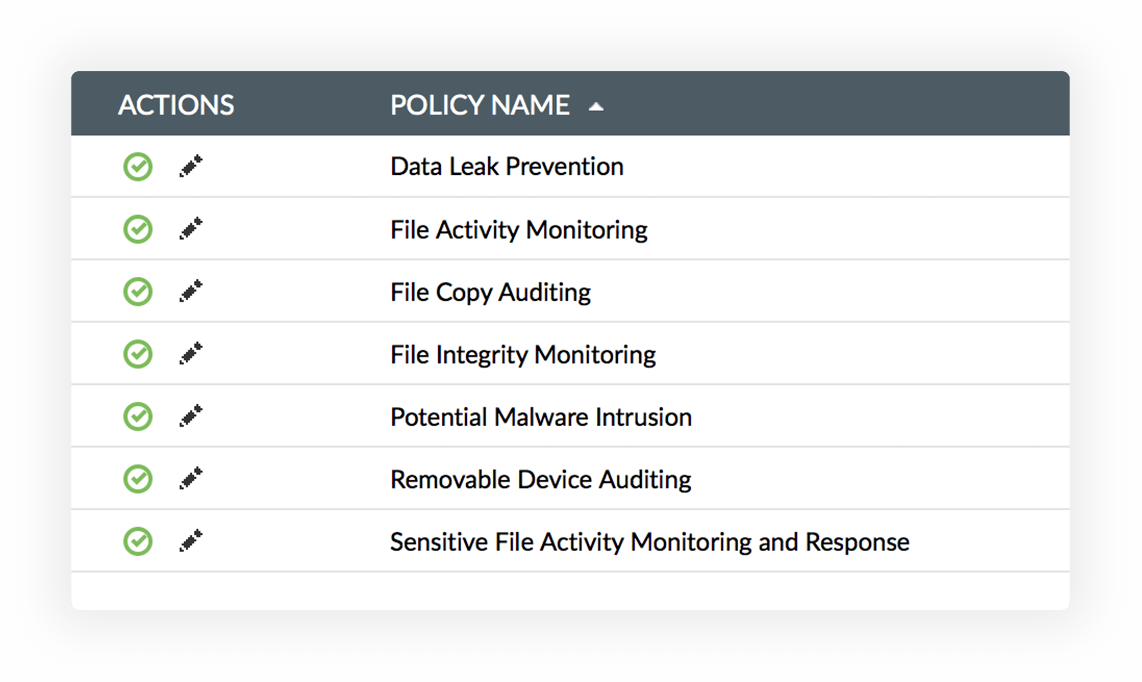
DataSecurity Plus helps monitor the following for potential illicit behavior:
DataSecurity Plus can restrict the use of low-reputed cloud apps, i.e., known domains that host exploit kits, deliver malicious payloads, and more by adding them to blocklists.
DataSecurity Plus promptly identifies any potential ransomware infections with the assistance of threshold-based alerts that are triggered by telltale indicators of a ransomware attack.
No problem! Just fill out this form with as much information as possible, and we'll contact you with the necessary information.
Audit and control the use of USBs and other peripheral devices to mitigate the risk of data theft.
Lear morePrevent sensitive data leaks via USB devices, emails, web applications, printers, and more.
Lear moreTrack all file modifications made with details on who accessed what, when, and from where.
Lear moreSpot and shut down potential ransomware attacks instantly with automated threat response.
Lear moreLocate and classify files containing sensitive personal data such as PII, ePHI, and PCI.
Lear moreTrack the use of cloud applications, and block websites with unsafe and inappropriate content.
Lear moreHave a question about features, trials, or licensing?Go ahead, ask us anything.