Protect business-critical data from accidental exposure and malicious activities—while also
ensuring IT compliance—by auditing permissions.
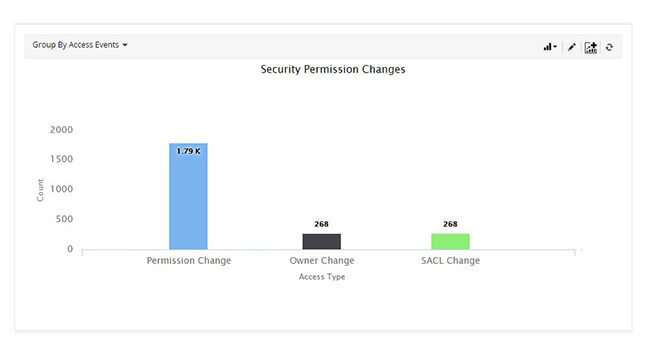
Track every permission change event occurring in your environment, in real time.
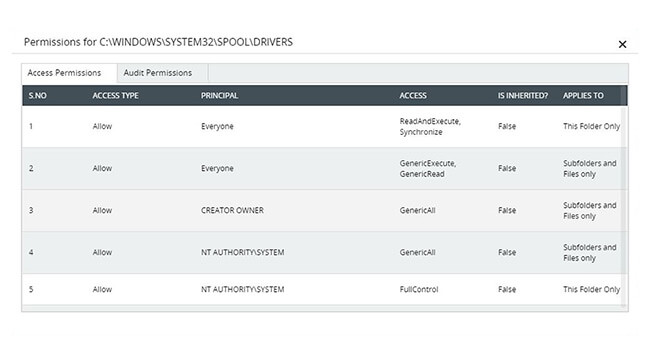
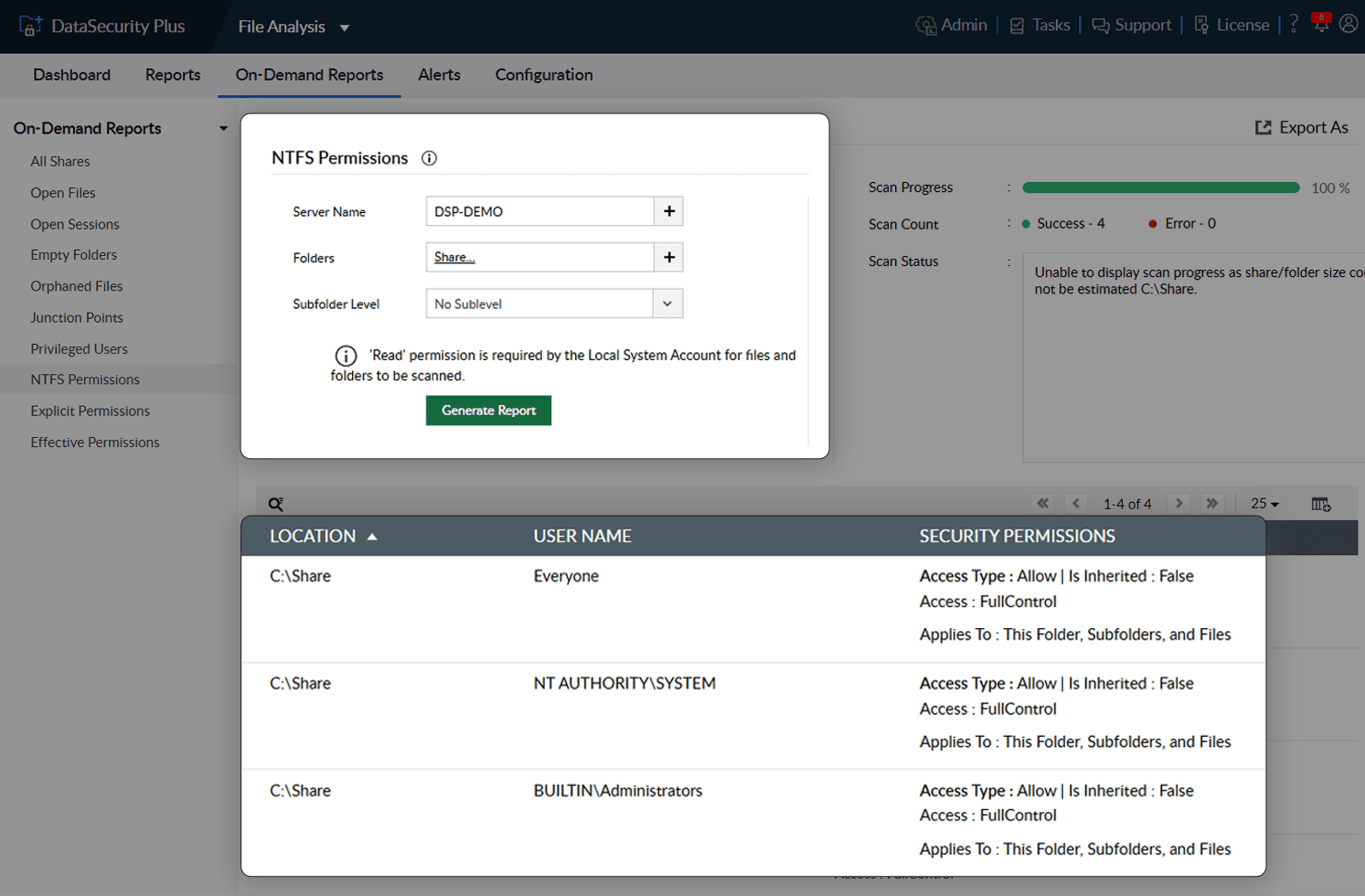
View permissions assigned to local and shared files in as much detail as required.
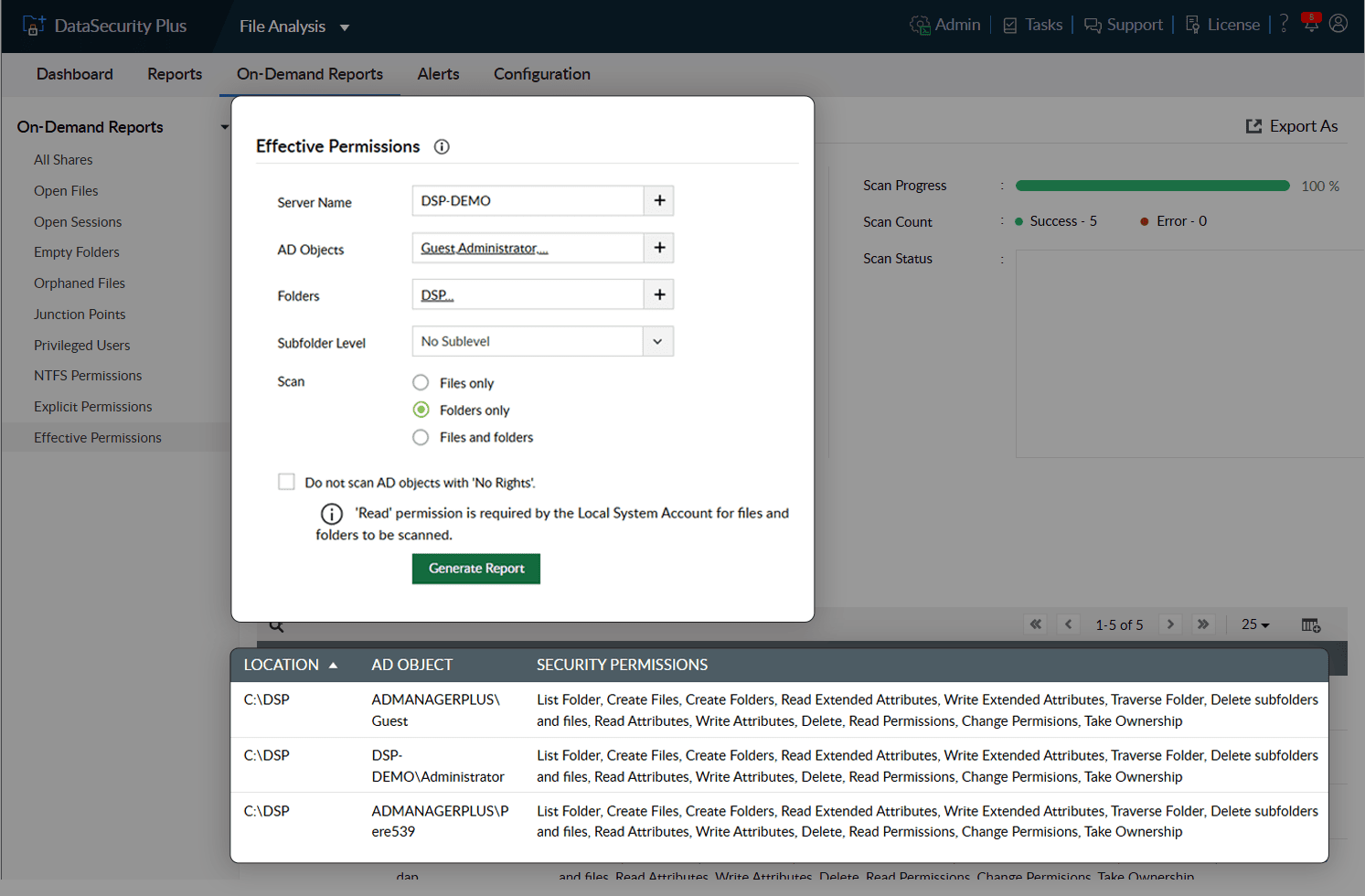
Ensure maintenance of least privilege with the effective permissions reporting tool.
Ensure that users are not given excessive access to files by reviewing permission changes happening in your file server environment in real time.
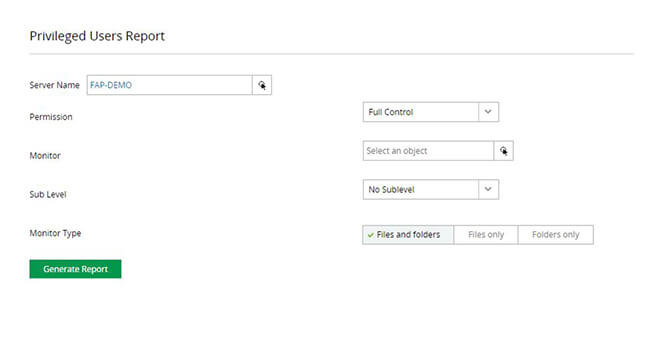
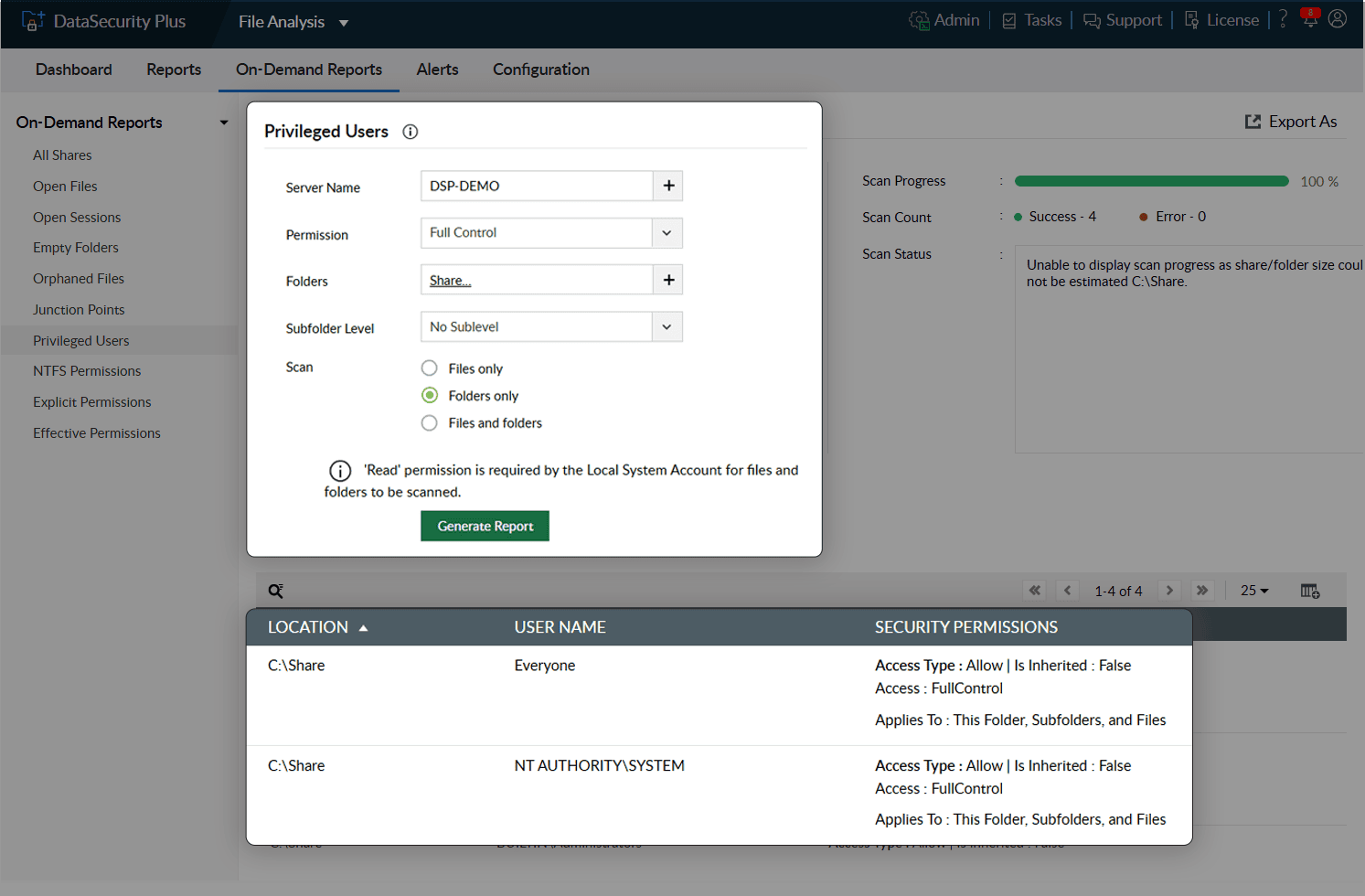
Spot elevated privileges by continuously auditing users' access rights. Verify whether they only have the permissions they need for their work.
Quickly identify suspicious activities by users with unrestricted access before they can irreparably affect the security of critical files and folders.



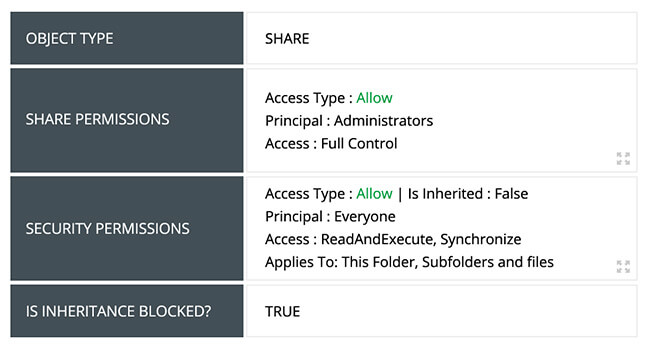
Keep a close eye on files containing sensitive data with accurate reports on their share and NTFS permissions and whether inheritance is allowed.

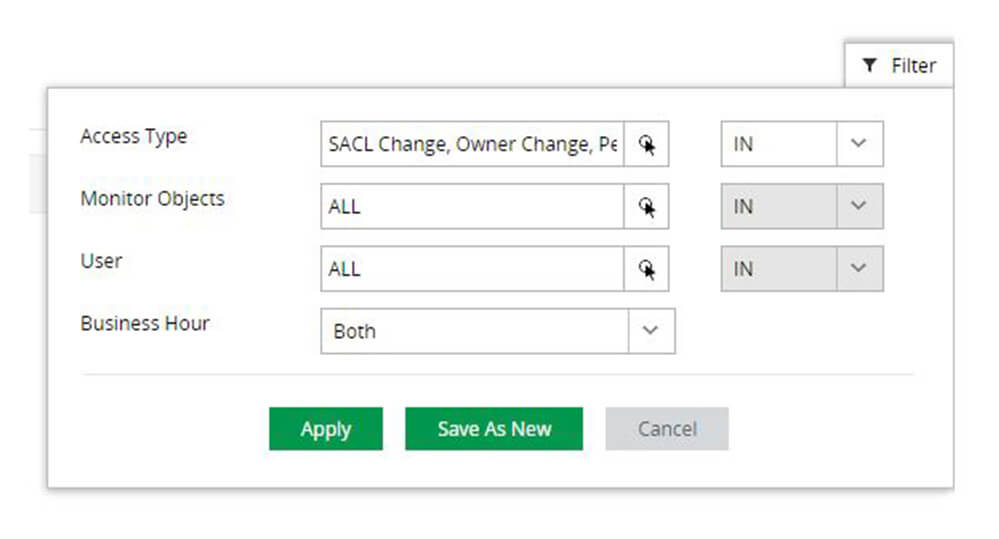
Stay on top of changes that are most important to you by filtering reports to view permission changes in specific files, or by particular users.

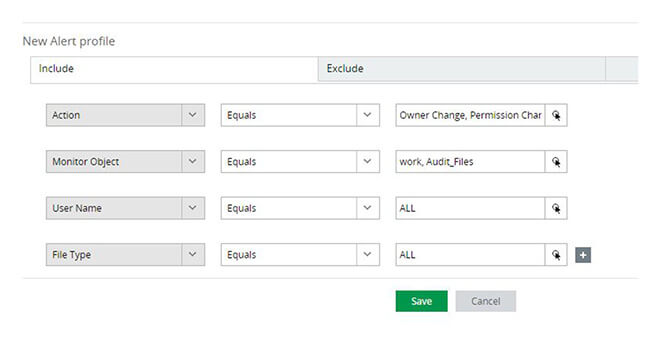
Spot security incidents such as privilege escalations with real-time alerts for important events such as permission or ownership changes to sensitive files.

Audit user access rights, and gain visibility into your file servers with DataSecurity Plus' comprehensive NTFS
and shared folder permissions tool.
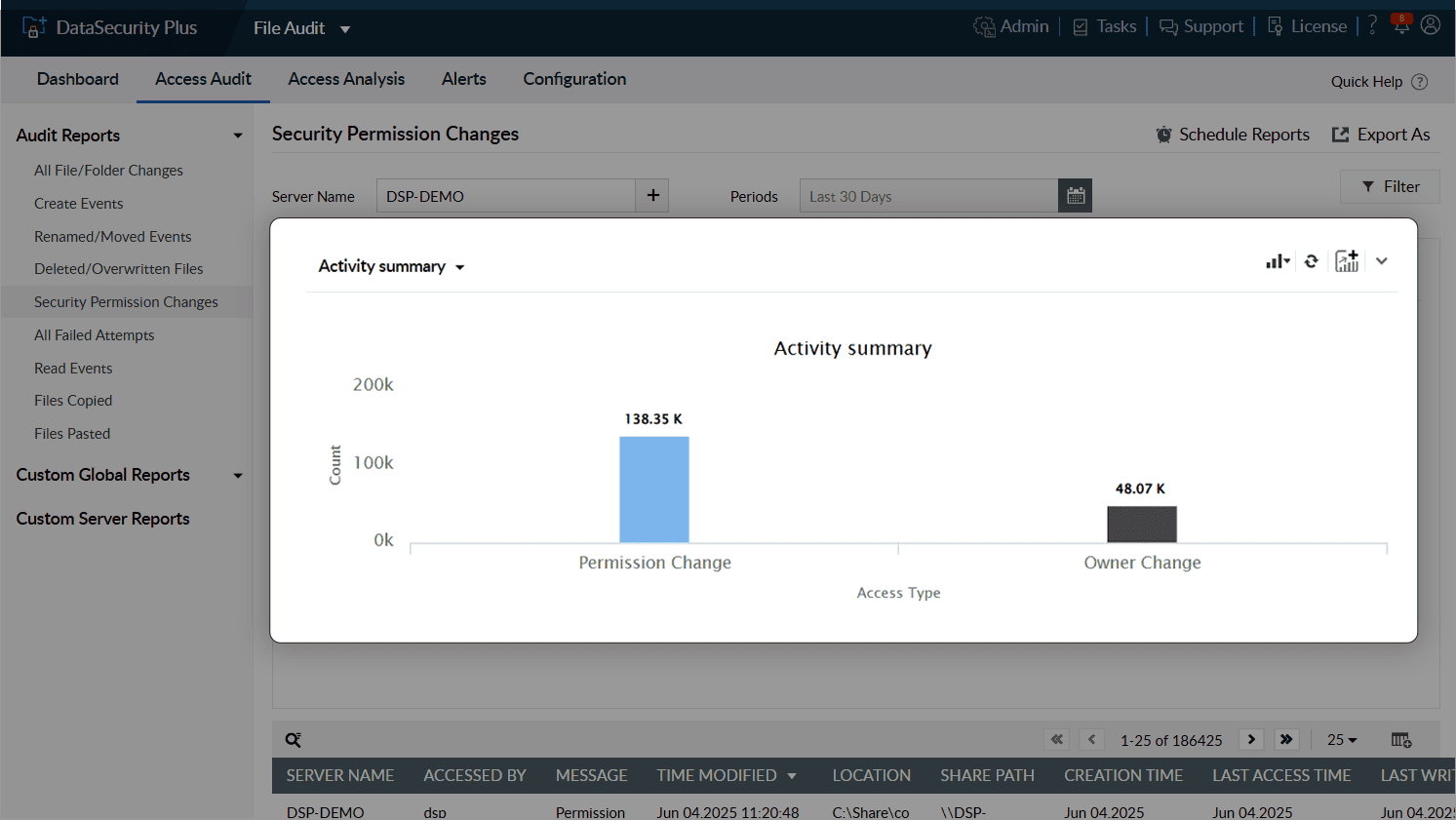
Identify inappropriate user activities faster by auditing all permission and ownership changes on your file servers.

Get full visibility across your file servers by viewing all user access rights. You can easily see the permissions assigned to shared and local folders with the Windows file share permissions audit utility.

Generate instant, detailed, and accurate reports showing the effective permissions of multiple users. Make sure no user has more privileges than needed.

Detect any instances of privilege misuse or other anomalous accesses by monitoring the activities of users who have privileged access.


