While PowerShell allows you to set passwords to never expire, this practice should be limited to exceptional cases, like service accounts or legacy applications. Having users in your Active Directory (AD) with perpetual passwords can expose your organization to brute-force attacks and audit failures. Once you identify AD users with non-expiring passwords, enabling expiration will urge them to change passwords periodically, thereby reducing risks and ensuring compliance.
The PasswordNeverExpires property determines whether a user's password follows the domain's policy. Setting it to False ensures the password will expire according to the domain's policy. In rare cases like service accounts, hardcoded credentials, or legacy apps that may break if passwords change, you may need to set PasswordNeverExpires to True so the password never expires.
Prerequisites
Import the AD module (if not done already) using this command:
Import-Module ActiveDirectory
Using the Set-ADUser cmdlet to configure password expiration
Run the commands below to enable password expiration. If you'd like to set the password to never expire, replace $false with $true.
Get-ADUser -Filter 'PasswordNeverExpires -eq $true' -Properties PasswordNeverExpires |
Select-Object Name, SamAccountName, PasswordNeverExpires
Set-ADUser -Identity "username" -PasswordNeverExpires $false
Get-ADUser -Filter * -SearchBase "OU=Users,DC=domain,DC=com" |
ForEach-Object { Set-ADUser $_ -PasswordNeverExpires $false }
Get-ADUser -Filter * | ForEach-Object {
Set-ADUser $_ -PasswordNeverExpires $false }
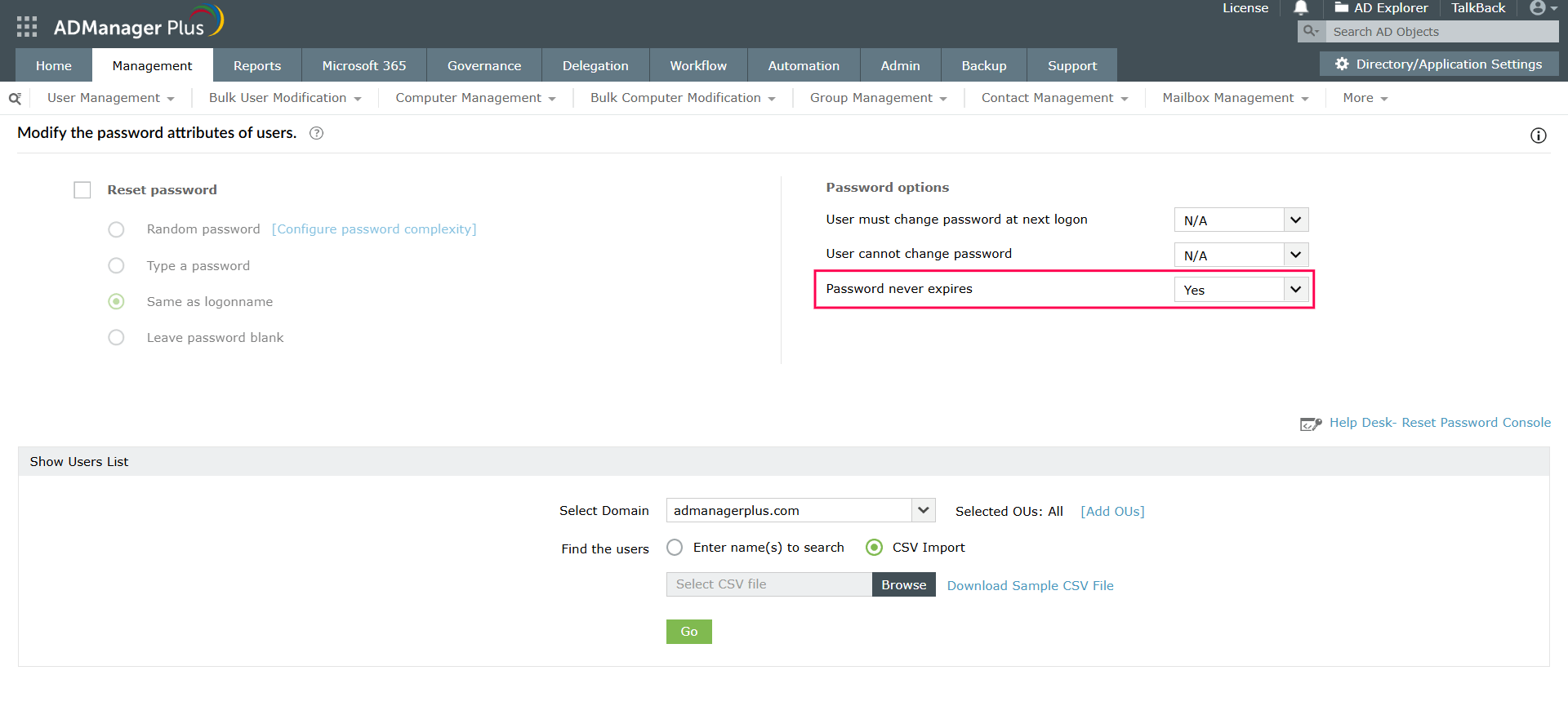
Note: To list users in your AD whose passwords are set to never expire, follow these steps.
Set-ADUser -Identity "james" -PasswordNeverExpires $true
Get-ADUser -Filter * -SearchBase "OU=Users,DC=domain,DC=com" |
ForEach-Object { Set-ADUser $_ -PasswordNeverExpires $true }
$GroupName = "Audit Non-Compliant Accounts"
Get-ADGroupMember -Identity $GroupName |
Get-ADUser |
ForEach-Object {
Set-ADUser -Identity $_ -PasswordNeverExpires $false
Write-Host "Set password for group member $($_.SamAccountName) to expire according to policy."
}
$UserList = Import-Csv -Path "C:\Temp\UsersToExpire.csv"
foreach ($User in $UserList) {
Set-ADUser -Identity $User.SamAccountName -PasswordNeverExpires $false
Write-Host "Set password for user $($User.SamAccountName) to expire according to policy."
}
The following are essential parameters to perform password expiration tasks in PowerShell:
| Parameter | Description |
|---|---|
| -Filter | Finds users matching password policy conditions. |
| -Properties | Displays extended properties (PasswordNeverExpires). |
| -SearchBase | Limits scope to an OU or container. |
| -Identity | Specifies the account to modify. |
| -PasswordNeverExpires | Enables or disables password expiration for target user. |
| -Path | Output file path for exported report. |
ADManager Plus is a web-based AD and Microsoft Entra ID management and reporting tool that simplifies AD password management and more from a centralized interface:
To disable password expiration for a local user in PowerShell, you can use the Set-LocalUser cmdlet. Open PowerShell as an administrator and run the following command by replacing <username> with the actual name of the local user account:
Set-LocalUser -Name "<username>" -PasswordNeverExpires $true
Historically, organizations were discouraged from setting passwords to never expire, as doing so could increase the risk of long-term compromise and non-compliance with security standards. However, password expiration can sometimes backfire, as users may choose simpler passwords. In environments that rely on service accounts or legacy applications, non-expiring passwords may be necessary to avoid disruptions, but they should be safeguarded with strong complexity and monitoring.
Current cybersecurity best practices recommend setting strong passwords with a significant length and then setting them to never expire. This approach is more effective when combined with other security measures, such as multi-factor authentication.
Ultimately, the key is to balance security with practicality, using extra safeguards when passwords can’t expire.