
See every device, every user, every risk at any given instant. With complete visibility at a glance, blind spots don't stand a chance.

Define exactly how your endpoints behave. Keep tabs on your device fleet with no guesswork and surprises, ensuring secure operations.

Ensure threats don't get through. Spend less time worrying about security and more time growing your business.
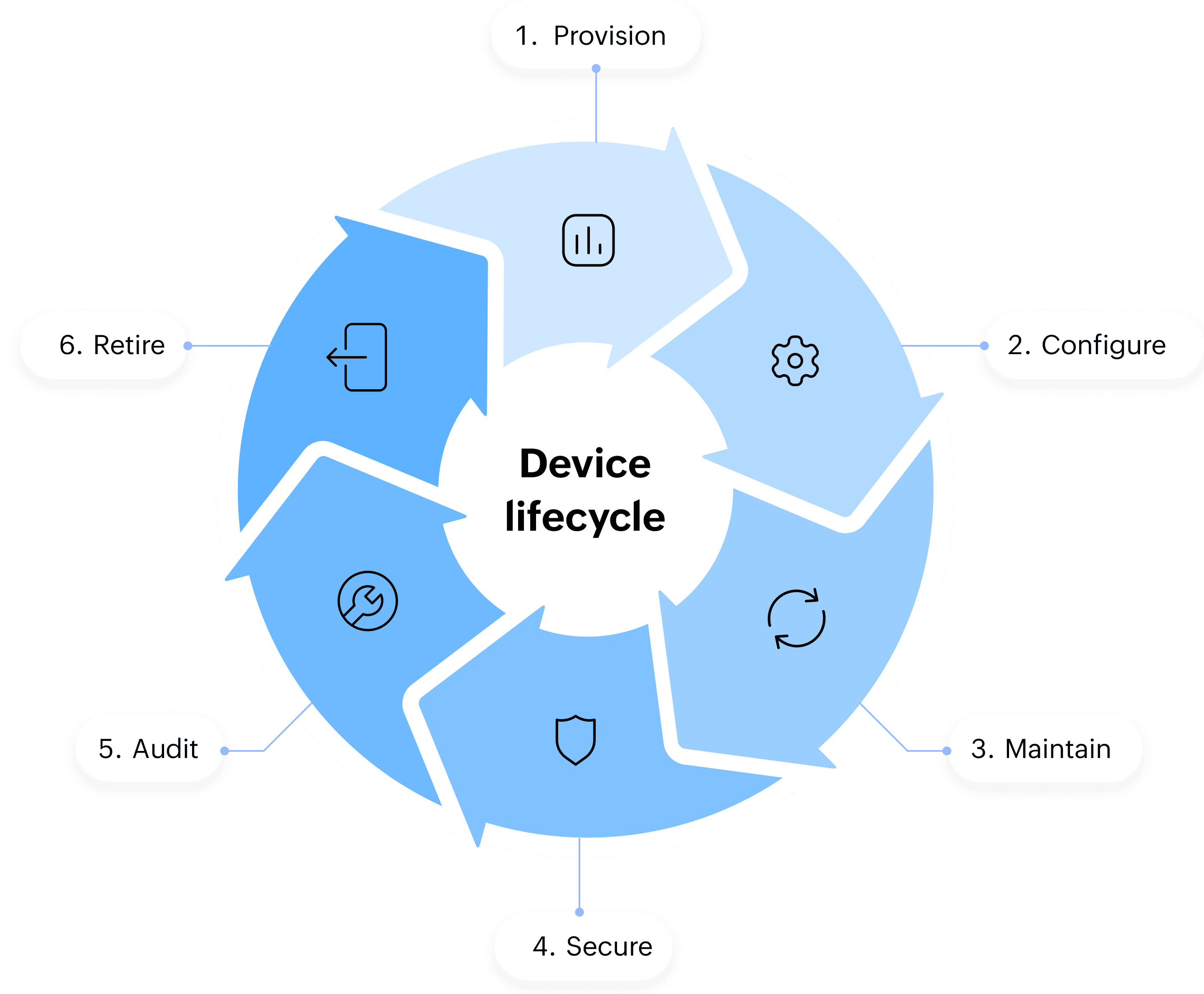
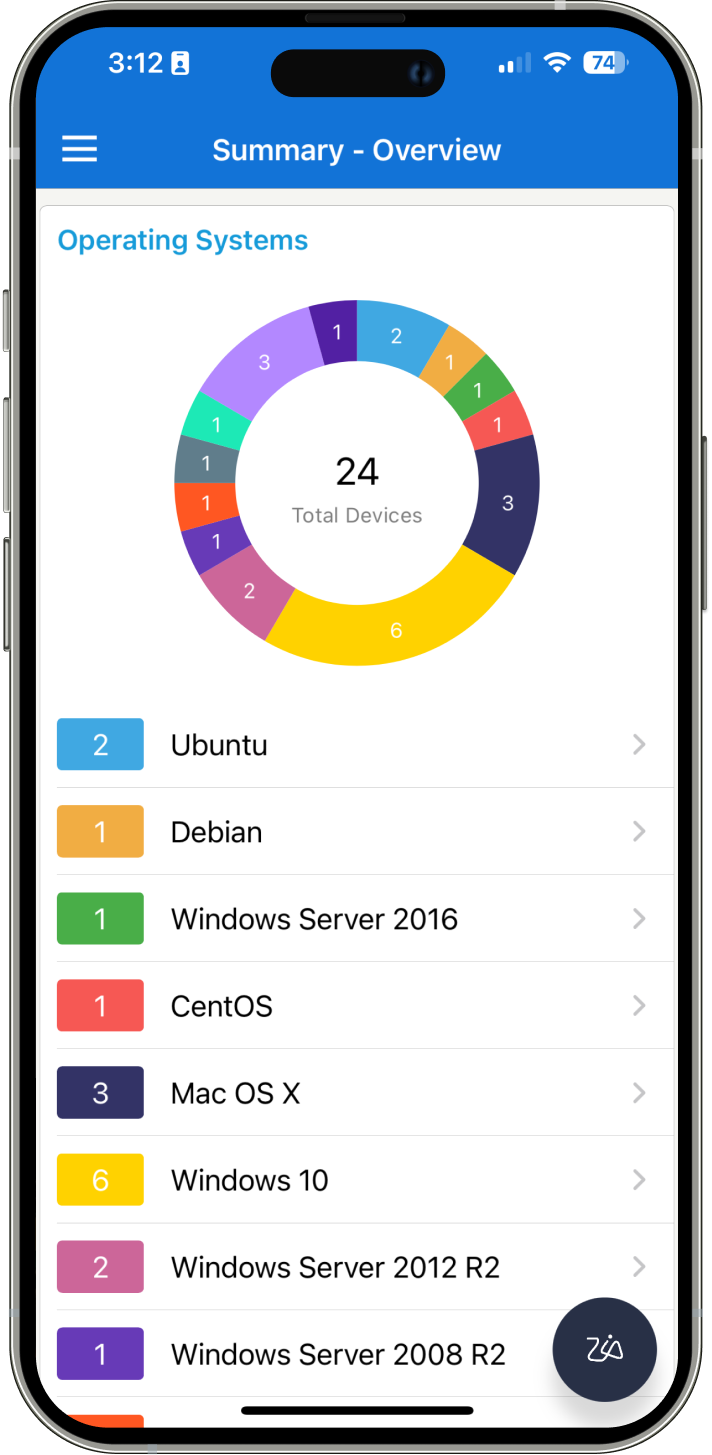
A 'handy' way to take care of your fleet while away from the desk. Experience the comfort of true mobility with the Endpoint Central mobile app.
Keep every endpoint secure, updated, and under control, from one central platform. Take the complexity out of device management.