- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Firewalls play a crucial role in network security. The complex network architecture of modern enterprises with multiple firewalls like a circuit-level firewall, an application-level firewall, and an advanced next-generation firewall (NGFW) requires an automated firewall management and centralized firewall monitoring tool to ensure security at the perimeter level. ManageEngine EventLog Analyzer is a comprehensive network firewall security and log management tool that helps you manage your firewall rules; detect malicious traffic that surpass your firewall defenses; and centrally collect, analyze, correlate, and archive your firewall logs.
Explore EventLog Analyzer's state-of-the-art features that support network firewall security management
Detect security incidents and troubleshoot firewall issues
With a processing rate of 25,000 logs per second, EventLog Analyzer can efficiently spot anomalies in the huge volume of events recorded in the firewall logs. Suspicious incidents such as multiple failed connections from a single source, insecure outbound connections, and IP spoofing are precisely detected and correlated to help security admins combat ongoing attacks.
Troubleshoot and fix firewall issues with the Device Severity Reports and System Events reports that record critical information on:
- Firewall interface statuses
- Firewall system shutdowns and reboots
- Failed commands, error events, warnings, and incidents to debug.
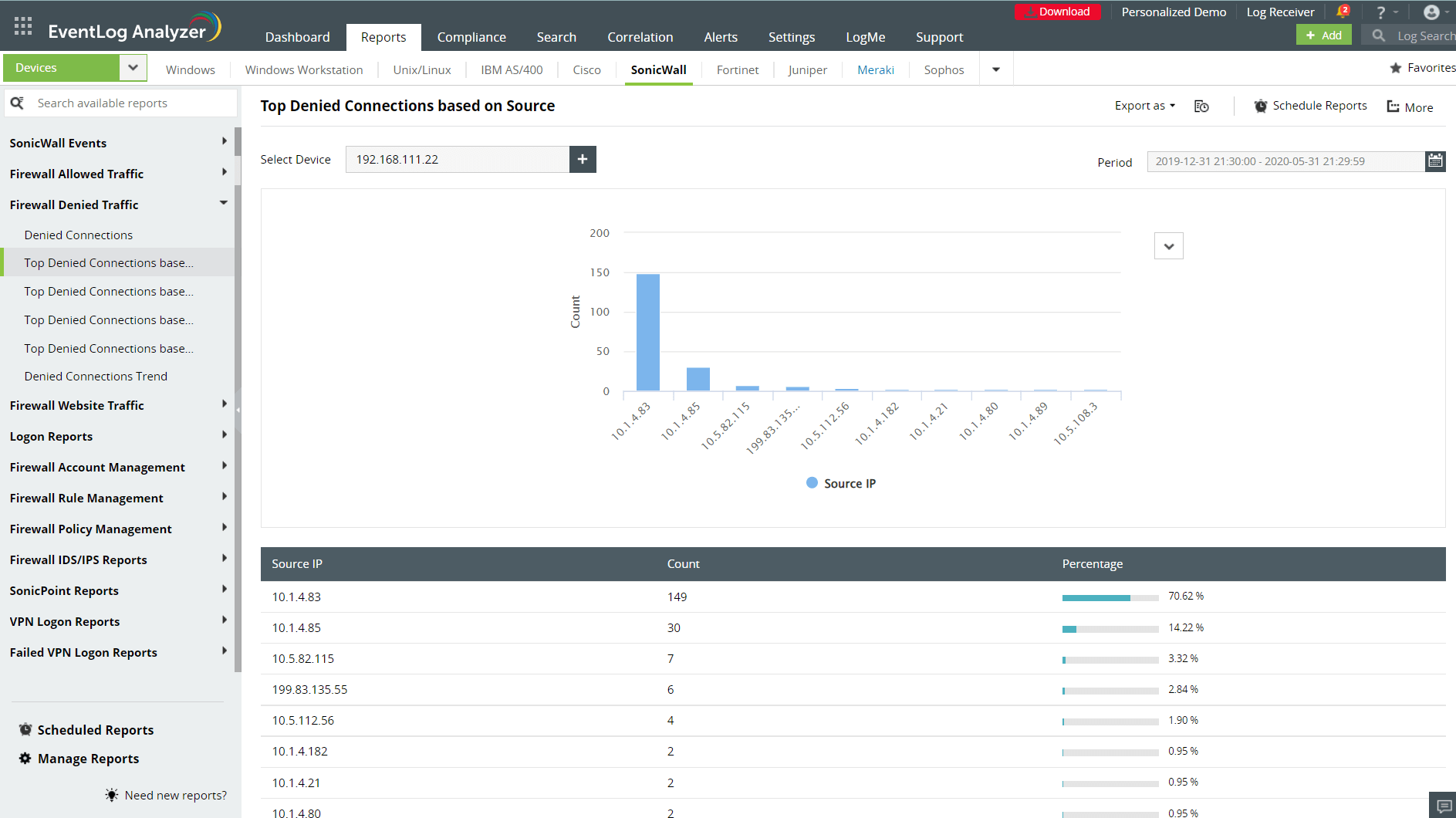
Oversee all changes made to firewall policies and rules
Get insights into firewall rules and policy modifications. Gain visibility into the recently added, deleted, and modified policies. Know who made the change, from where, and when. Additionally, you can set up alert profiles to receive real-time notifications on changes in firewall policies along with when these policies get enabled and disabled. Conduct investigations based on the reports mailed to you and check if the actions implemented on the firewall policies were legitimate or not.
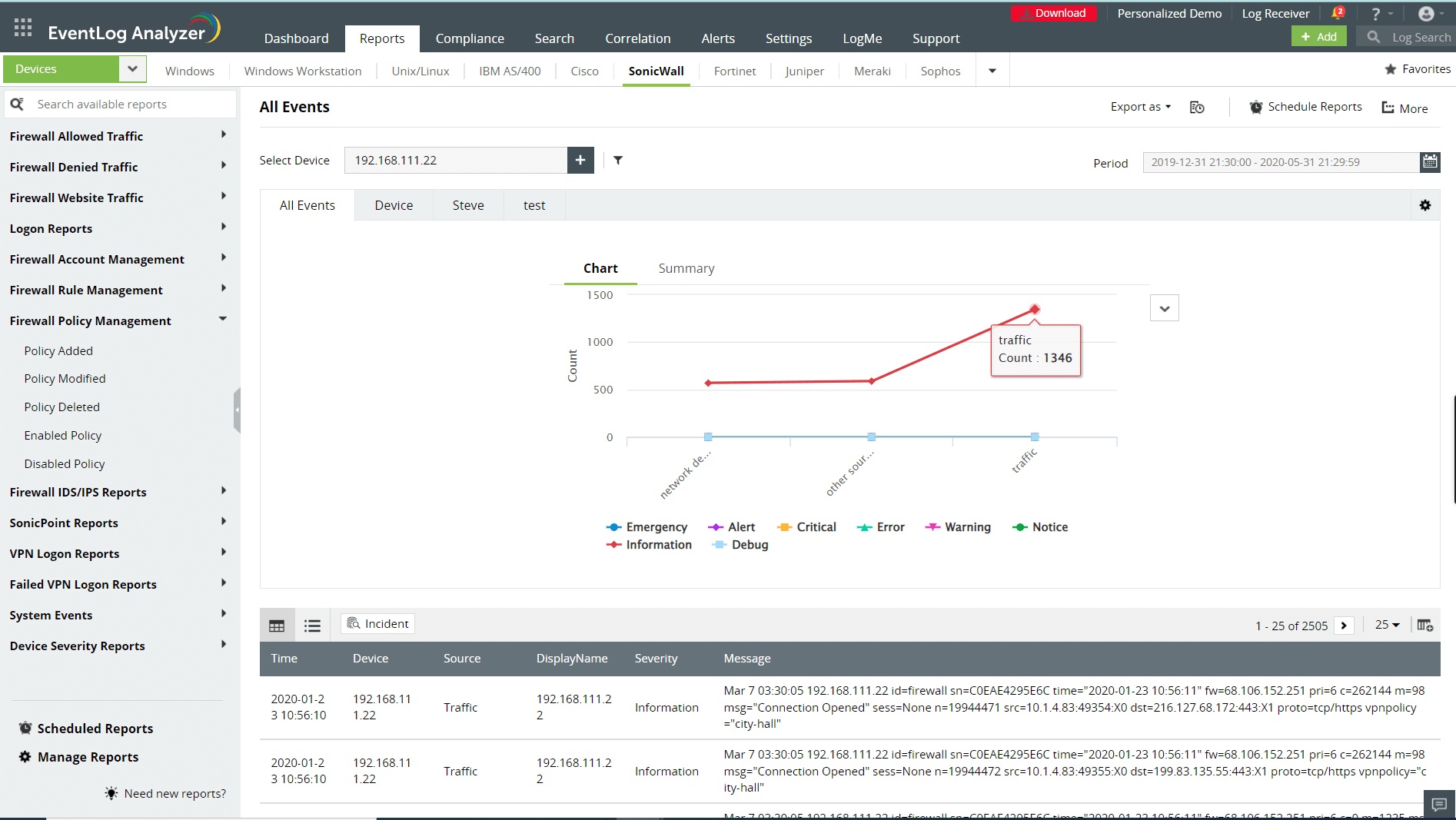
Monitor admin activities and user accounts
Monitor your network admin activities on firewalls to prevent privileged access abuse. Get detailed audit reports on the accounts used to access firewalls and the changes implemented. Secure your firewall from malicious insider access by tracking recently added, deleted, and modified admin accounts; newly added groups; and unauthorized escalations in user privileges.
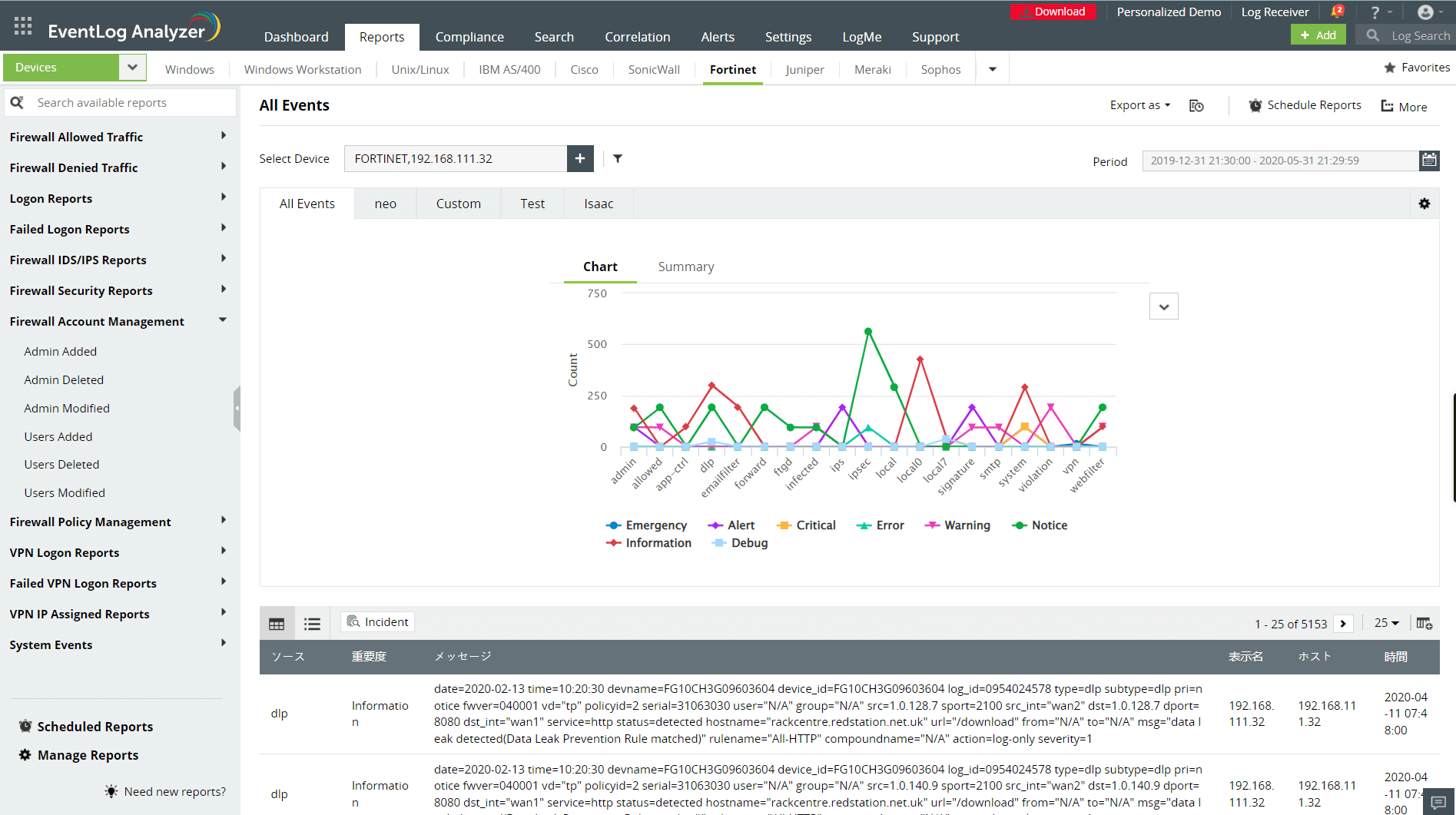
Detect and mitigate external threats
Analyze and investigate external attack attempts such as port scan attacks targeting open ports, malware trying to reconfigure firewall rules, SYN attacks, and denial-of-service attacks by correlating firewall logs with our built-in threat databases. EventLog Analyzer's firewall security analytics dashboards help you get insights into allowed and denied firewall traffic based on users, devices, IPs, ports, and protocols.
Access hundreds of pre-enabled alert profiles, add additional criteria, and categorize and set priorities based on the severity of the event. You can also respond to the detected firewall security incidents and remediate threats by automating standard response measures through workflows.
Supported firewall vendors
EventLog Analyzer provides out-of-the-box support for built-in firewall systems like Windows firewall and third-party security solutions from leading vendors. The tool can read and analyze logs in any human readable format, enabling it to monitor a diverse set of devices and applications.
Supported firewall vendors
Access the custom log parser to add additional fields for log analysis, utilize the reports exclusively created for different security solutions, and navigate through the centralized dashboard with an easy-to-use interface.
Related solutions offered by EventLog Analyzer
Network perimeter monitoring
Along with firewall monitoring, EventLog Analyzer also supports auditing network devices like switches, routers, IDSs and IPSs, vulnerability scanners, and more. Use the custom reporting features to group multiple devices and generate consolidated reports on your network perimeter security.
Real-time visibility into firewall VPN activities
Monitor remote access to your enterprise resources by analyzing your firewall VPN logs. Detect anomalous user behavior from the VPN trend reports like successful and failed logons categorized by source, users, and remote hosts.
Forensic analysis on firewall logs
The firewall analyzer and the high speed search engine with flexible querying functions support security incident mining and thorough inquiry on network intrusions. The advanced search option lets you correlate multiple query results to investigate firewall attack attempts and get a detailed time line of related events.
Compliance reports
Stay compliant with IT security standards such as HIPAA, the NERC, the ISLP, SOX, and FISMA with EventLog Analyzer's automated firewall audits and predefined report templates.
Secure firewall log storage
Manage archived firewall logs securely and protect them from being tampered with using EventLog Analyzer's encryption and time stamping techniques. These logs are vital sources for forensic analysis and IT compliance audits.
5 reasons to choose EventLog Analyzer as your syslog viewer tool
1. Centralized log management system
EventLog Analyzer's centralized log collection, analysis, correlation, and reporting features solve the complexity of monitoring layered firewall architectures in modern enterprises and ensures comprehensive firewall management.
2. In-depth auditing and reporting
EventLog Analyzer's exhaustive audit reports help you examine the effectiveness of your firewall security rules, any existing loopholes, and your network traffic trends.
3. A powerful correlation engine
Correlate firewall traffic logs with suspicious events detected across your network using EventLog Analyzer's predefined correlation rules and filters. Define new attack patterns with the custom rule builder and set parameters to raise alerts.
4. Augmented threat intelligence
Standardized information exchange with international threat databases enable EventLog Analyzer to immediately identify millions of globally blocklisted IPs and malicious sources. Access the insights from the threat analytics reports to reconfigure your firewall rules and strengthen the perimeter security.
5. Automated incident management
Automate your security incident response with emergency measures like isolating affected systems and adding new inbound and outbound rules to firewall devices. You can use the workflow management page with an easy drag-and-drop UI to configure the flow of steps to be implemented.
Frequently asked questions
Firewall logs record details of the traffic interacting with your network and the actions implemented by the firewalls.
They mainly include the:
- Source and destination IP address of the traffic.
- Port numbers.
- Protocols used.
- State of the connection.
- Packets allowed and dropped by the firewall.
- Dates and time stamps of events.
- Firewall user account and configuration changes.
Here's a list of commonly used firewall systems and the default firewall log storage paths:
- Windows: C:\Windows\System32\LogFiles\Firewall
- Cisco: Go to the Cisco web interface. Then go to Device Management > Logs > View Logs.
- Barracuda: Log into the Barracuda web firewall interface. Go to Advanced tab > Syslog settings > Export Logs.
- Fortinet: Go to the Fortinet web interface and navigate to System Settings > Event Log. Use filters to extract the required logs.
- PaloAlto: Go to the PaloAlto Networks UI and then go to Monitor > Logs > Log type.
- Go to Group Policy Management Console > Forest > Domains. Select your domain > Group Policy Object, then right-click and select Edit.
- Expand Computer Configuration in the Navigation pane and go to Policies > Windows Settings > Security Settings > Windows Firewall With Advanced Security > Windows Firewall Properties.
- Select the network location type (domain, private, or public) > Logging > Customize.
- Toggle to Yes next to Log dropped packets and Log successful connections. This will enable logging of firewall events.
Enterprises use a combination of hardware-, software-, and even cloud-based firewalls (Firewall as a Service). This creates an environment with a heterogeneous set of network entities. To monitor them manually, security admins need to enable logging, manage log storage, and study and analyze the logs in different formats.
Considering the massive amount of logs generated by firewalls, these laborious tasks need to be automated with a firewall security log management tool like EventLog Analyzer, which offers a wide range of useful features to secure networks, like dynamic threat handling, real-time alerting, log storage management, firewall-specific reports, and analytical dashboards.











