Last updated on: June 17, 2025
From inconsistent access provisioning during employee onboarding to unexpected outages induced by certificate vulnerabilities, potential security pitfalls often lurk in plain sight. When left unattended, these create opportunities for sophisticated cyberattacks, costing organizations an average of $4.88 million per breach. While adhering to privileged access best practices can help safeguard your IT infrastructure, operational silos and a fragmented tech stack might lead to slower detection and resolution of security incidents.
To overcome these challenges, it is vital to seamlessly blend ITSM and privileged access management (PAM) workflows. In this article, we'll explore how the contextual integration between ServiceDesk Plus and PAM360 makes it easier for organizations to improve their security posture while facilitating impeccable service experiences.
To begin with, let's explore the journey of a fictional organization, Zylker, and dive into its four key challenges due to ITSM-PAM silos.
Zylker, a reputed media streaming company, secured exclusive rights to air a high-stakes sporting event. To ensure an uninterrupted viewing experience, it began rapidly scaling its IT operations, mobilizing teams, and onboarding external contractors to keep its infrastructure running smoothly. However, due to disconnected ITSM and PAM workflows, it faced four key challenges.
- Unauthorized access to critical IT resources on account of standing privileges, leading to privilege misuse
- Juggling between multiple applications, delaying incident resolution
- Inconsistencies in provisioning routines while onboarding and offboarding contractors, leading to security threats
- Lack of visibility over certificate expiration and vulnerabilities, leading to service outages
Now, let's observe how Zylker leveraged the integration between the two solutions and overcame each one of these challenges.
The countdown to the sporting event began, and Zylker's engineers swung into action to perform routine maintenance on critical application servers. Privileged access requests flooded in via emails, and its IT team, using manual ticket creation and assignment, wasn't prepared for the sudden surge. Also, due to disjointed ITSM and PAM workflows, approvals were granted without a robust vetting mechanism. This led to unauthorized access to the application server, resulting in privilege misuse, weakening its security posture. Zylker also faced challenges when it came to auditing privileged access requests, being unable to map them to specific tickets and not knowing whether they were approved or not.
The integration advantage
To scrutinize incoming privileged access requests and verify their authenticity, Zylker leveraged the ServiceDesk Plus-PAM360 integration.
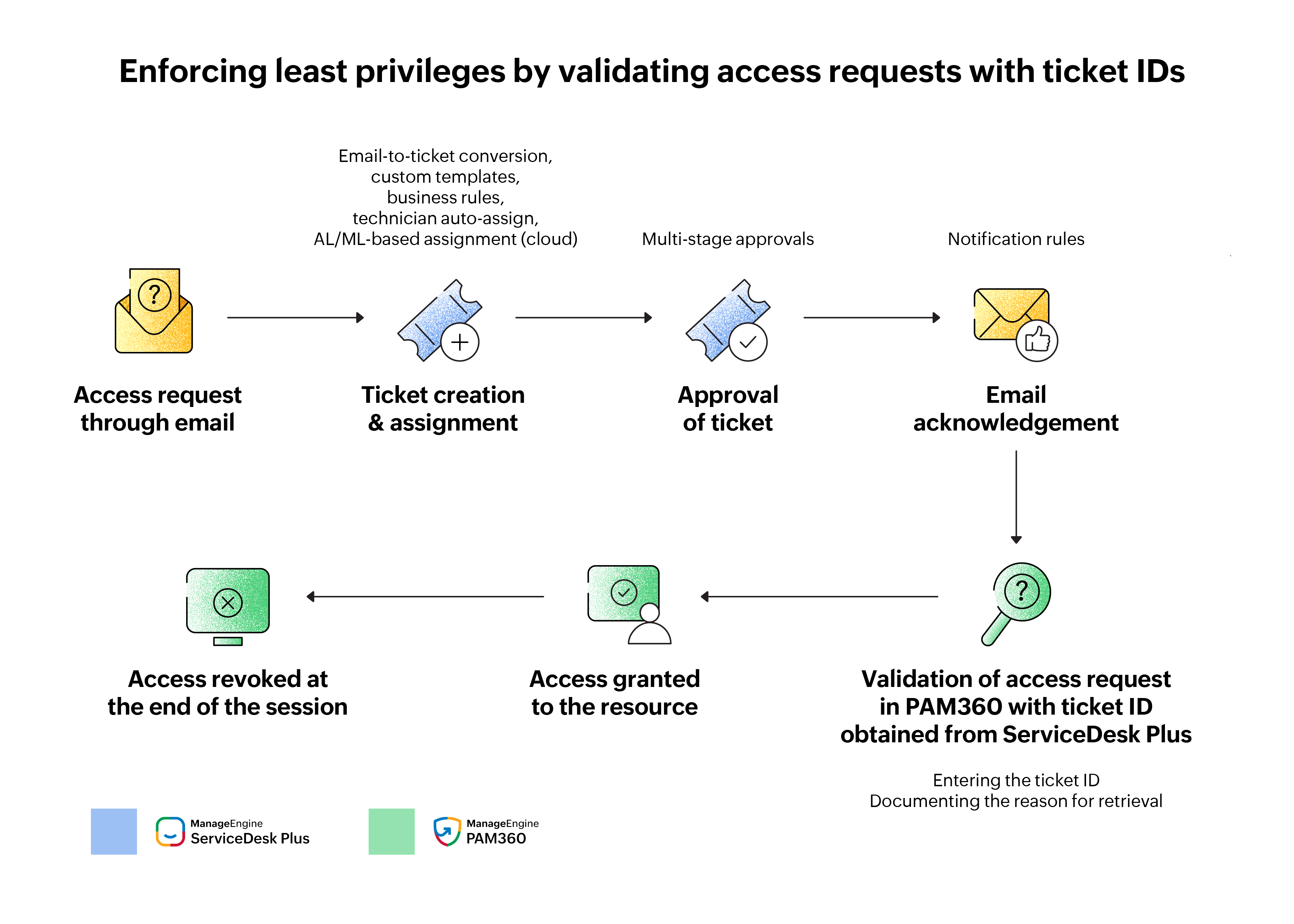
Instead of manually sifting through numerous emails, the integration enabled Zylker to automate email-to-ticket conversion while also applying custom templates to standardize requests and capture precise contextual details specific to privileged access requests. This ensured a structured, trackable process right from the start. Tickets were then efficiently assigned to the appropriate technicians using smart automations like business rules and tech auto-assign. Additionally, factoring in technician expertise with predictive intelligence in ServiceDesk Plus (Cloud) helped expedite ticket fulfillment.
Once assigned, a multi-stage approval workflow introduced layered checks and balances, ensuring each request was scrutinized before granting access. Throughout the ticket life cycle, notification rules kept stakeholders well-informed of request statuses, maintaining transparency.
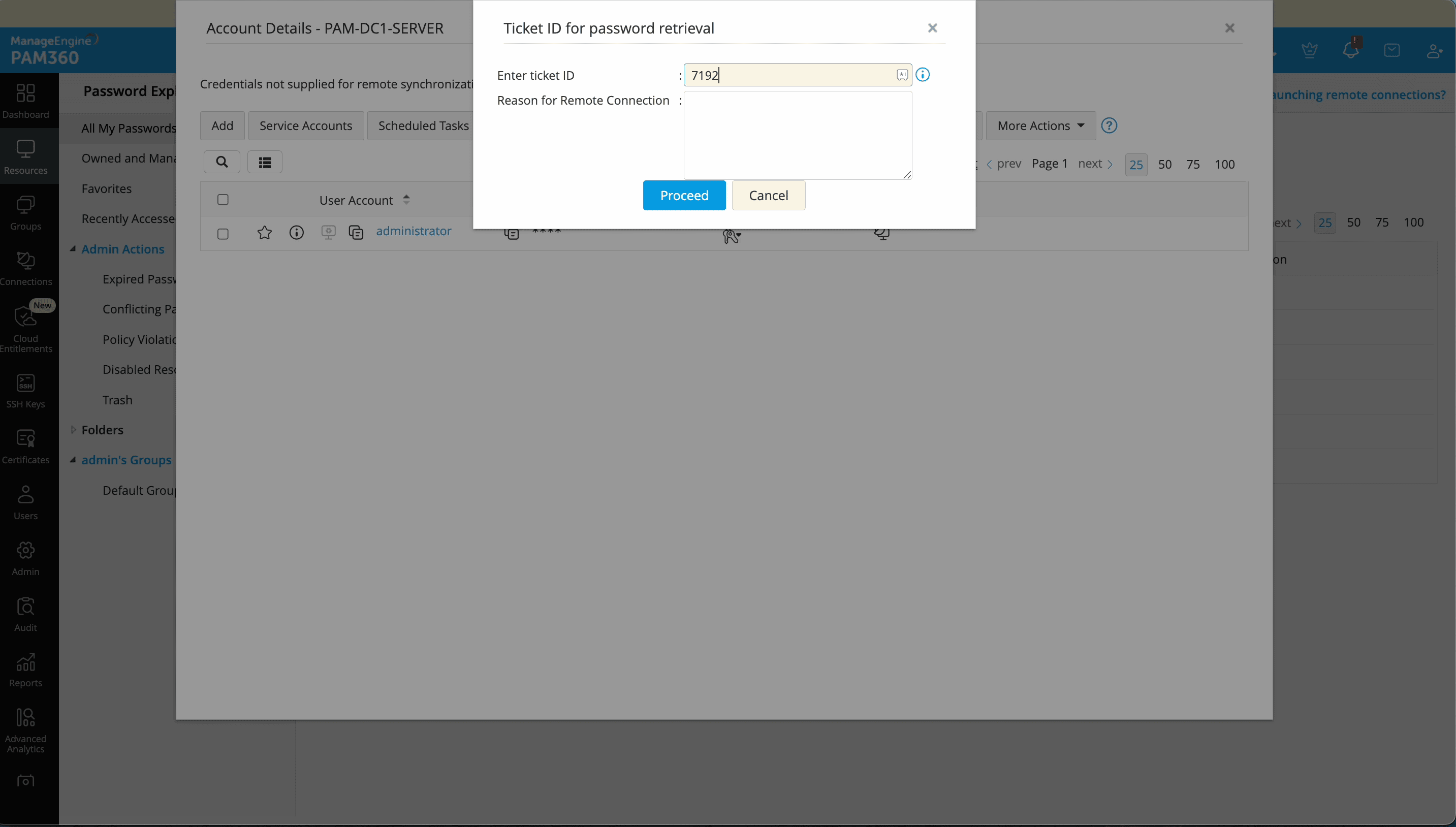
Upon approval, Zylker's engineers could gain just-in-time access to sensitive systems, like application servers, by validating requests with ticket IDs and documenting the reason in PAM360. Simultaneously, Zylker enforced the principle of least privilege by restricting privilege to engineers, preventing any possible misuse.
To further enforced fine-grained access control, Zylker leveraged ticket attributes to refine and set access criteria. For instance, access requests to critical resources like application database servers could be restricted to engineers from a specific department. Once the maintenance operation was complete, access was automatically revoked at the end of the session, preventing standing privileges and mitigating insider threats.
By referring to the audit logs in PAM360, Zylker could further establish the relationship between the privileged routines undertaken in PAM360 with the tickets raised in ServiceDesk Plus, eliminating audit gaps while establishing authenticity.
With these measures, Zylker ensures controlled privileged access, mitigating security risks while maintaining transparency in critical operations and establishing an audit trail.
The sporting event was in full swing, thrilling fans worldwide. Unfortunately, Zylker suffered a global streaming outage due to an outdated patch on its application server. Frustration spread like wildfire, and the IT team was thrown into crisis mode without an incident response playbook to guide them.
The chaos began when the IT team learned about the outage from a flood of emails and phone calls. Scrambling to respond, they relied on outdated and manual triaging methods, creating unnecessary confusion. Making matters worse, fragmented communication channels blurred the context between teams, leading to back-and-forths. Without complete visibility into application dependencies, pinpointing the root cause—an outdated patch—became a Herculean task.
When the IT team finally identified the issue, a disjointed ITSM-PAM tech stack set the perfect concoction for reactive incident resolution. Access was granted haphazardly by manually sharing sensitive passwords. Meanwhile, remote troubleshooting from external applications only worsened the situation, breaking context and leaving no clear audit trail. By the time the issue was resolved, the damage was done. Viewership plummeted, frustrated fans vented online, and Zylker's reputation suffered a major blow−all because of disjointed tool sets that turned a fixable problem into a crisis.
The integration advantage
To surmount this obstacle, Zylker took advantage of one-click, remote access capabilities, enabled by the integration, to accelerate incident resolution.
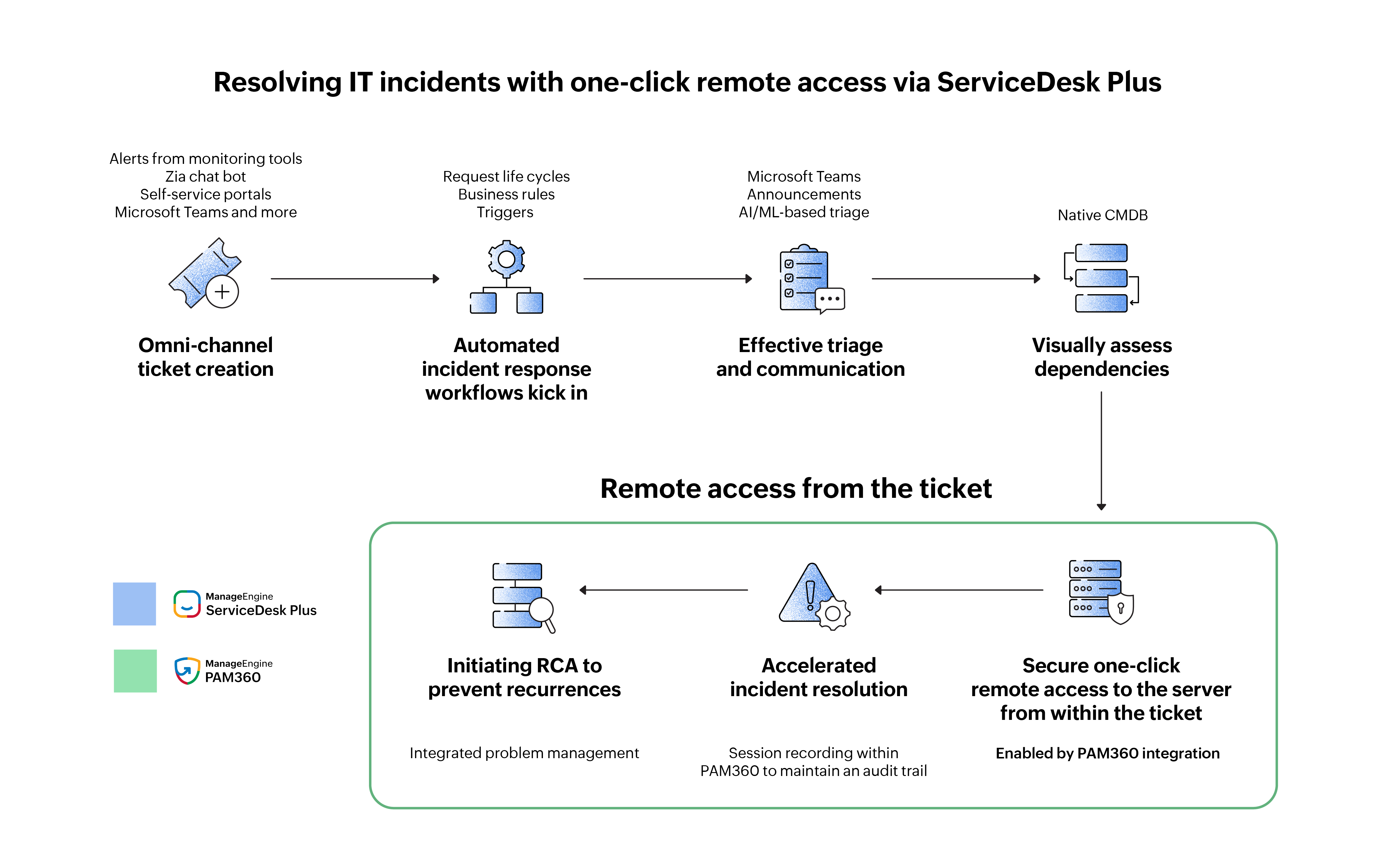
With omnichannel ticket creation, alerts from monitoring tools and issues raised by end users from other channels, including AI-powered virtual agents like Zia, self-service portals, and Microsoft Teams, no longer remained unnoticed. Automated incident response workflows then kicked in, streamlining resolution efforts. While smart automations like business rules, triggers, and AI- and ML-driven engines optimized triaging efforts, SLAs set the expectations for timely resolution. With request life cycles, Zylker could visualize the entire incident response strategy, guiding technicians through every step. This way, it automated various actions, from information collection to delivering contextual notifications, ensuring process adherence. Additionally, it established clear communication channels by leveraging external collaboration platforms like Microsoft Teams and publishing automated announcements within ServiceDesk Plus.
Zeroing in on the root cause
To identify the cause of the outage, Zylker leveraged the native CMDB and visually assessed dependencies between the streaming service and the underlying IT components, including the application server, databases, and network components. By digging deeper, it discovered an outdated version of a patch installed on the application server. By analyzing past similar incidents and correlating their root causes, it could establish that the streaming outage was indeed caused by the outdated patch.
Zylker had to upgrade the patch on the application server to resolve this issue. Here, it leveraged the contextual integration with PAM360 to remotely access the application server, building a solid security layer.
By employing custom actions associated with PAM360, Zylker's IT team could enable secure remote, one-click access to the affected server directly from within the ticket while enumerating the reason. This way, they eliminated the need for sharing privileged credentials via insecure channels or switching between multiple applications. They also maintained a record of the privileged actions performed during the session within PAM360, creating an audit trail and simplifying post-incident review.
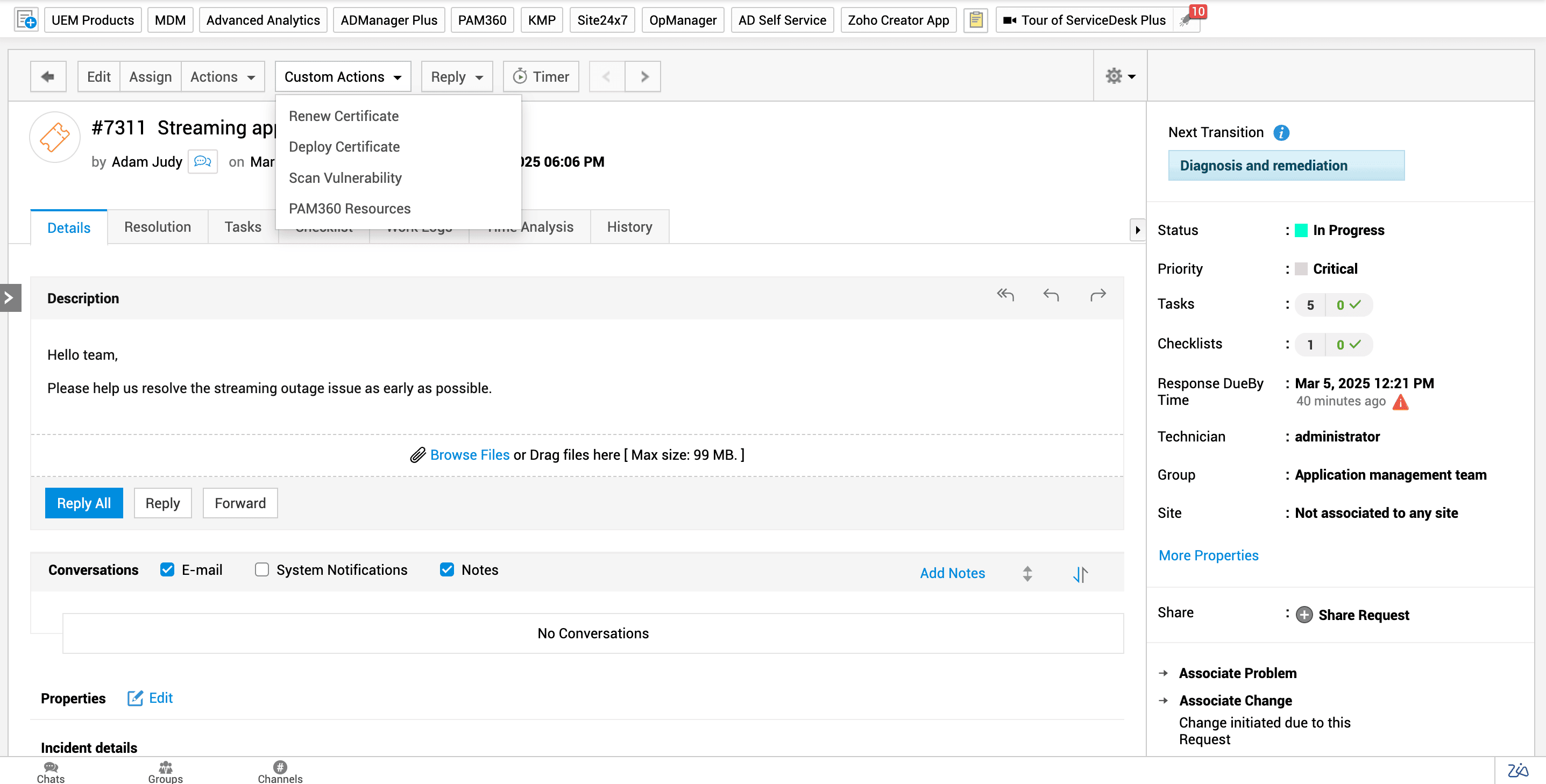
in ServiceDesk Plus (on-premises).
Finally, the team examined the root cause with integrated problem management and took corrective actions to prevent such recurrences in the future. Thus, Zylker accelerated incident resolution while complying with organizational requirements.
Zylker's reliance on external contractors was crucial for scaling its operations, but erratic onboarding and offboarding experiences hindered its efforts. The HR team tracked contractor journeys in bulk using spreadsheets, distorting information collection. Without real-time sync with IT, information gaps lead to constant back-and-forths. Leveraging manual provisioning routines made it error-prone and inconsistent, increasing privilege creep.
With just a day's notice to offboard contractors, the IT team missed revoking their privileges, leaving them with read and modify access to server configurations.These standing privileges increased security threats. In short, siloed service and provisioning layers rendered subpar employee experiences and a compromised security posture.
To eliminate bottlenecks, Zylker needed to integrate its onboarding and offboarding processes tightly with access provisioning and deprovisioning.
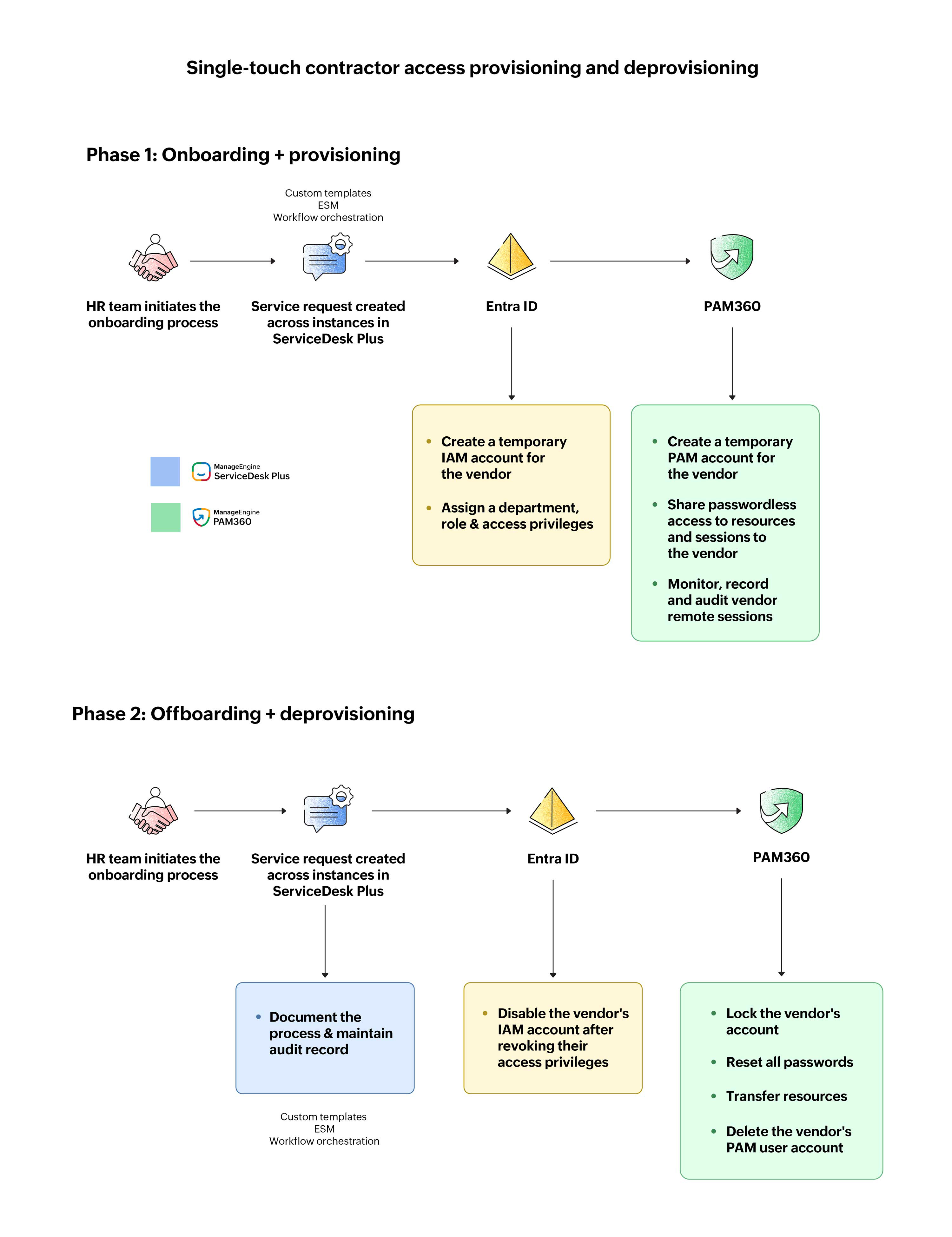
Crafting a secure contractor onboarding
With enterprise service management, it established department-specific instances while unifying service delivery across the organization. This removed silos and fostered seamless collaboration between enterprise teams. By automating bulk ticket creation from HR spreadsheets, Zylker ensured shared context across teams.
Meanwhile, it leveraged single-touch workflows in ServiceDesk Plus to orchestrate its onboarding tasks. With single-touch workflows, it could visualize the process as a series of states and automate various tasks across cloud and local systems. This included automatically creating Microsoft Entra ID accounts for contractors and ensuring synchronization of users across Microsoft Entra ID and PAM360. Once contractual user accounts were synchronized, PAM360 could automatically provision and deprovision asset access on a just-in-time basis as and when a ticket is created, enabling Zylker to automate mundane, repetitive tasks across its hybrid IT environment at scale, without any manual intervention.
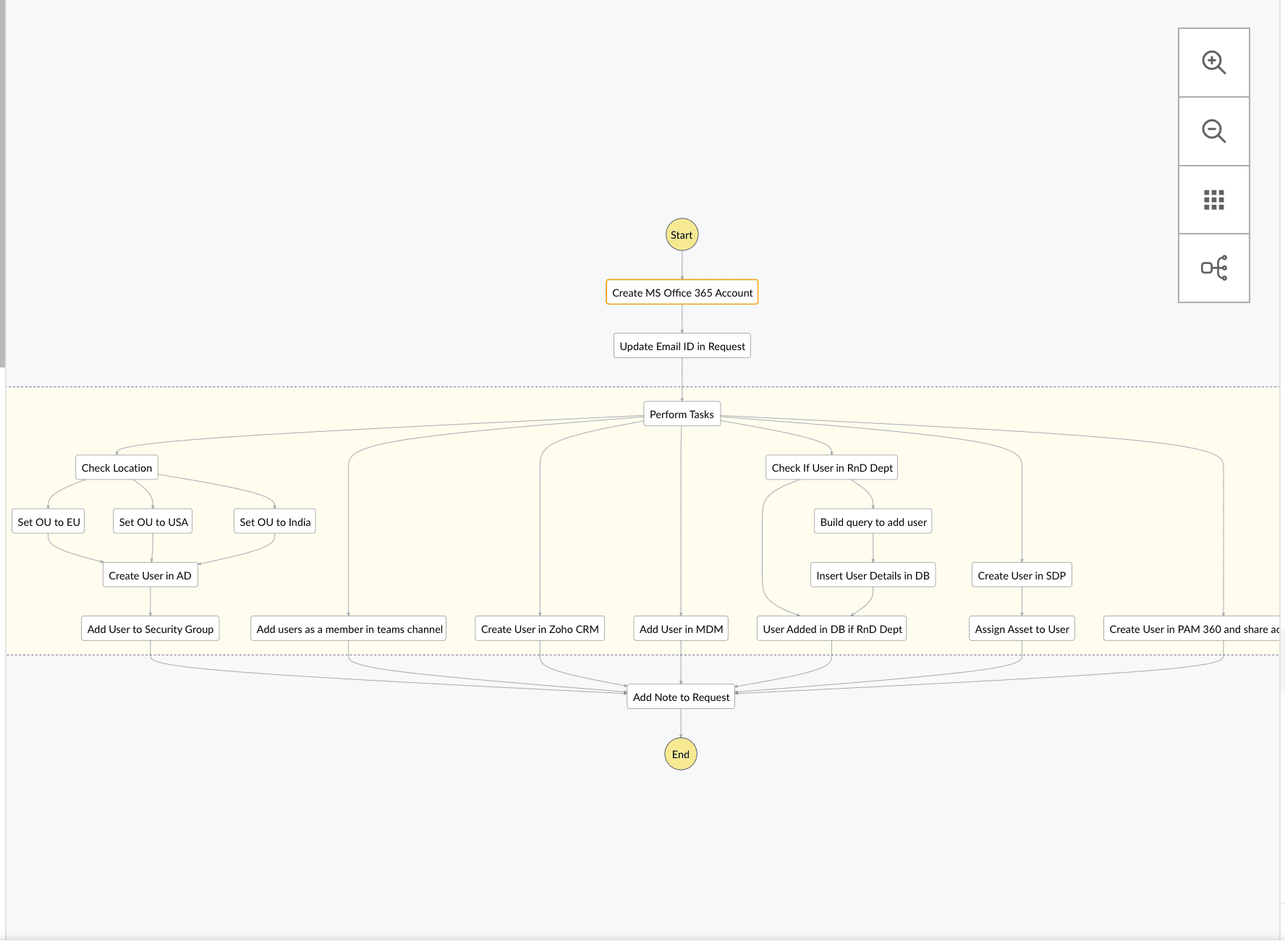
Now, let's say a contractor was responsible for optimizing the performance of Zylker's CDN infrastructure, complimenting its efforts towards seamless streaming experiences. Here's how Zylker securely provisioned access to the right server without compromising its security posture.
Once the contractor was assigned a ticket, they could directly request privileged access to the required server from within it. This streamlined approach allowed them to initiate passwordless, remote sessions securely. As soon as the ticket was closed, privileges were revoked automatically, ensuring need-based access with built-in checks and balances to prevent excessive privileges.
Automating secure contractor offboarding
During offboarding, contractor IAM accounts were automatically disabled in Microsoft Entra ID. Simultaneously, PAM360 locked their accounts, reset passwords, and transferred resources—eliminating standing privileges and reducing security risks.
By orchestrating provisioning routines along with contractor onboarding and offboarding, Zylker stayed compliant with regulatory and organizational policy and security requirements.
Zylker managed thousands of SSL certificates across its IT infrastructure to facilitate a secure streaming experience across its platform. But at the final leg of the sporting event, a hidden flaw turned into a ticking time bomb, disrupting streaming services.
Since Zylker managed its SSL certificates manually, tracking certificate expiry and vulnerabilities at scale became a challenge. So, when a critical certificate expiry went unnoticed, it suffered an unexpected service outage, irking fans again. Rushing to fix the issue, it faced another stumbling block−an outdated CMDB. Without complete visibility over the dependencies, it failed to examine the points of failure, delaying incident resolution and causing prolonged downtime.
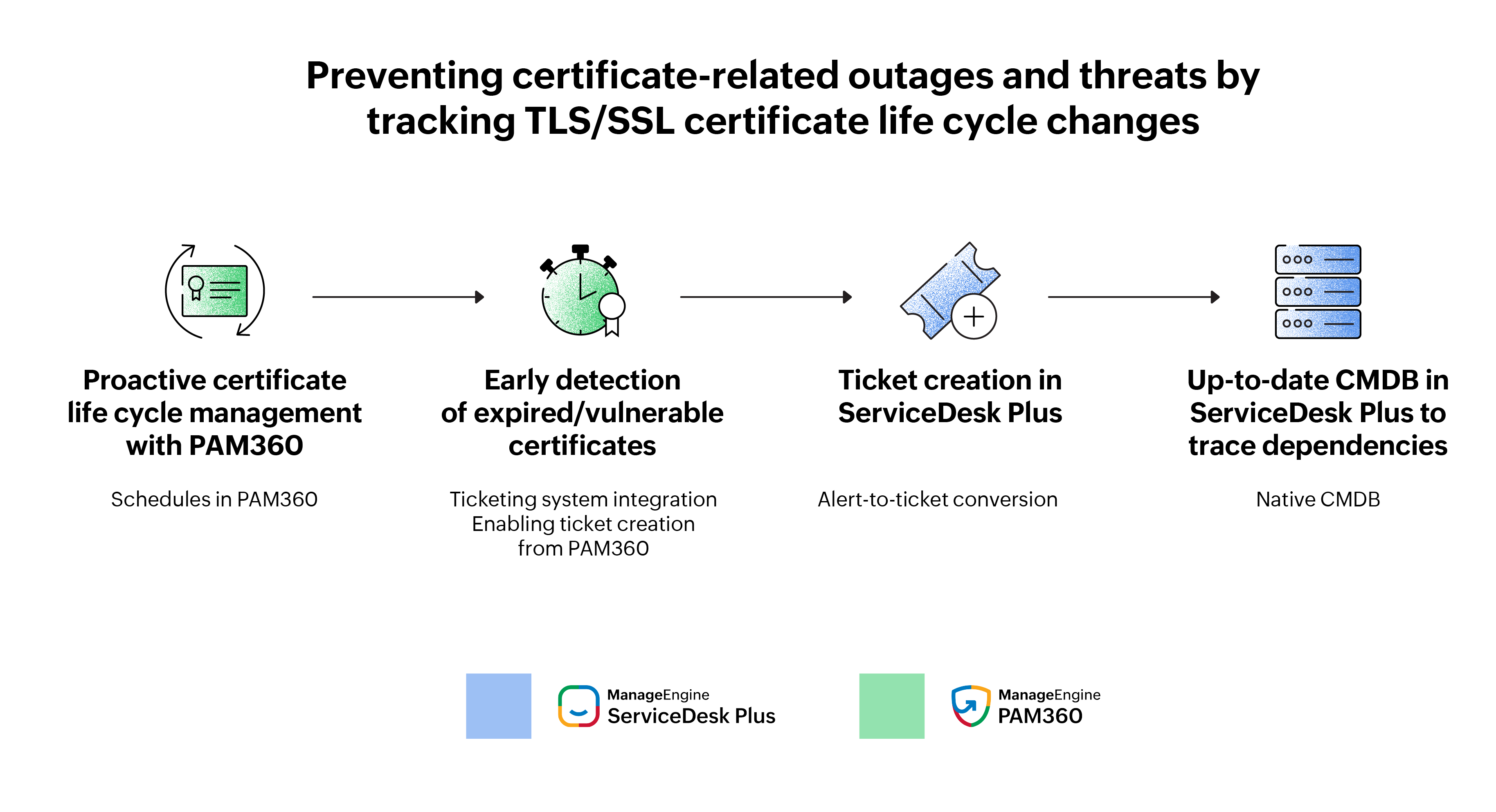
With the Key Manager Plus integration, it employed notification policies and scheduled expiry and vulnerability reports periodically, ensuring proactive certificate management. Scouring through Zylker's IT environment, Key Manager Plus detected expiring or vulnerable SSL certificates in advance, triggering alerts. These alerts were then automatically converted to tickets in ServiceDeskPlus, helping Zylker's IT teams stay on top of certificate expiry and vulnerabilities. Moreover, the team could kick-start contextual actions, from certificate deployment to renewal to scanning, from the ticket itself without hopping to multiple tabs.
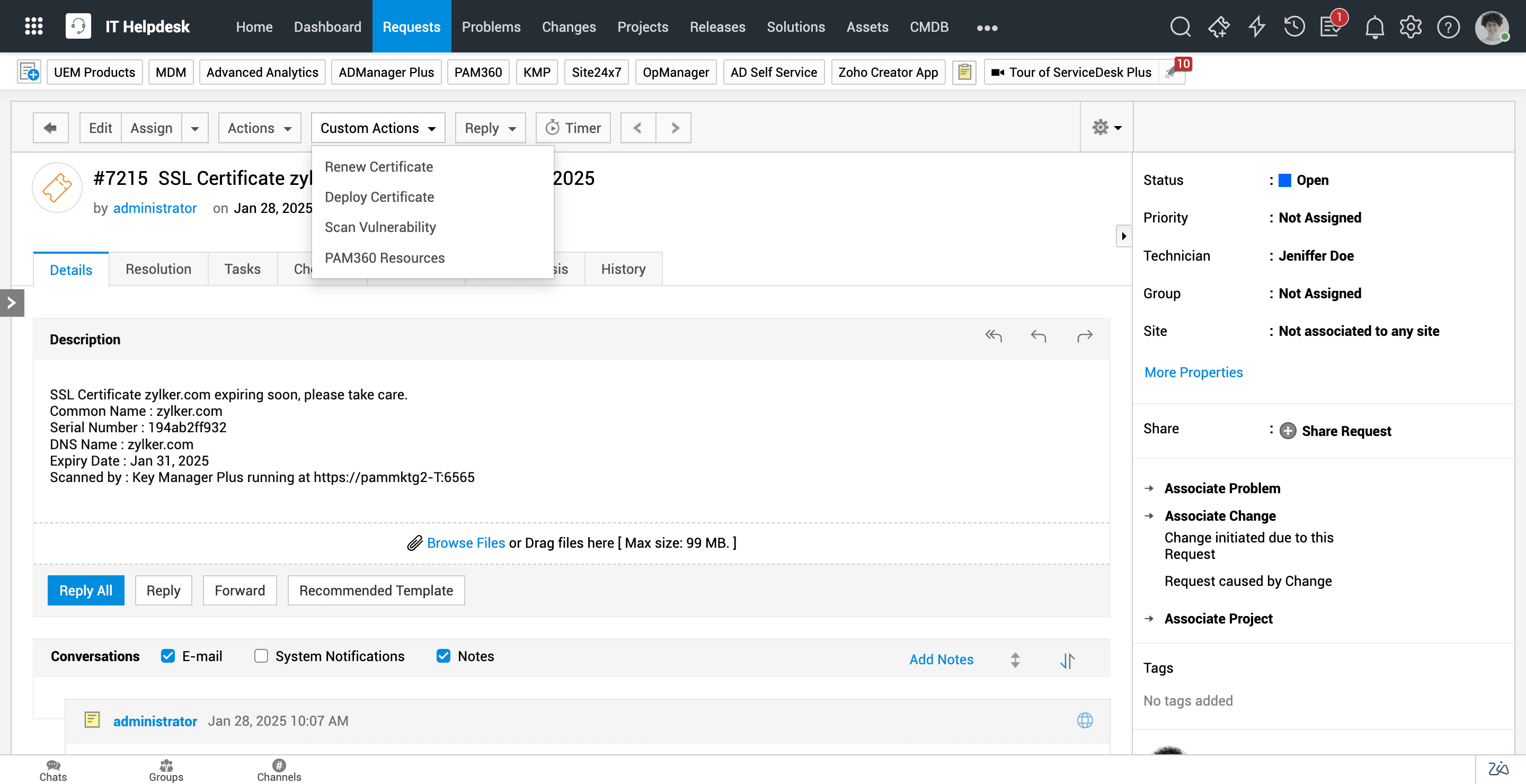
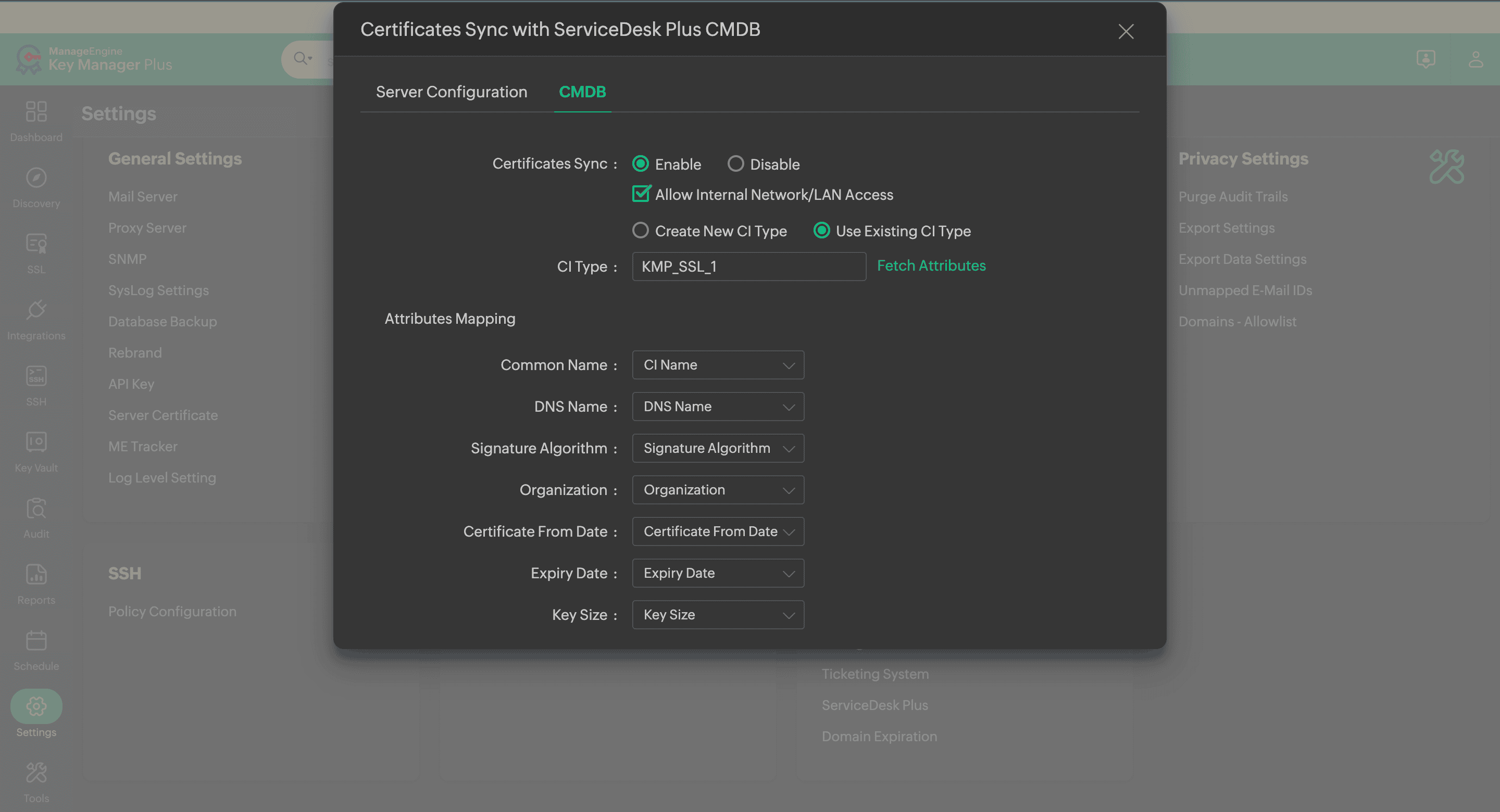
After renewal, certificate details from Key Manager Plus were synced with the CMDB in ServiceDesk Plus, creating an up-to-date view. Thus, Zylker grasped the nuances of its IT infrastructure and visually assessed dependencies to fast-track incident resolution.
Hidden security gaps in your organization's ITSM workflows can disrupt service experiences−unless you leverage the seamless integration of ServiceDesk Plus with PAM360.
With this integration, you can build layered access controls and prevent unauthorized access to crucial IT resources by validating tickets, minimizing privilege creep. You can further initiate remote sessions from the ticket in a passwordless manner, facilitating secure, context-aware, and accelerated resolution of incidents. By maintaining a record of privileged actions undertaken in PAM360, you can ensure an accurate audit trail, helping you stay compliant with regulatory and organizational requirements. Finally, you can stay on top of certificate expiries and vulnerabilities with automated ticket creation, helping you streamline certificate renewal and deployment from the ticket itself.
In short, this integration can empower your organization to unify IT security, enhance operational agility, and deliver uninterrupted service experiences.