Zero-day vulnerability Mitigation
Though deploying patches and putting an end to vulnerabilities once and for all sounds ideal, there are cases when patches aren't available to fix the flaw, such as with zero-day vulnerabilities and publicly disclosed vulnerabilities. Implementing a comprehensive zero-day vulnerability mitigation plan is the only way to harden your systems and software against zero-day vulnerabilities and publicly disclosed vulnerabilities.
Zero-day Vulnerability Mitigation: Complete Guide for Security Teams
Though zero-day exploits are difficult to prevent, you can defend against them by continually assessing your endpoint security posture and hardening your defenses. Let's take a look at how Vulnerability Manager Plus helps you execute effective zero-day vulnerability mitigation strategies.
Leverage a dedicated view for zero-day vulnerability mitigation
ManageEngine's security researchers constantly probe the internet for any details regarding new threats. As soon as details on zero-day and publicly disclosed vulnerabilities come to light, the information is verified and added to the central vulnerability database, and the data is synchronized with the Vulnerability Manager Plus server.
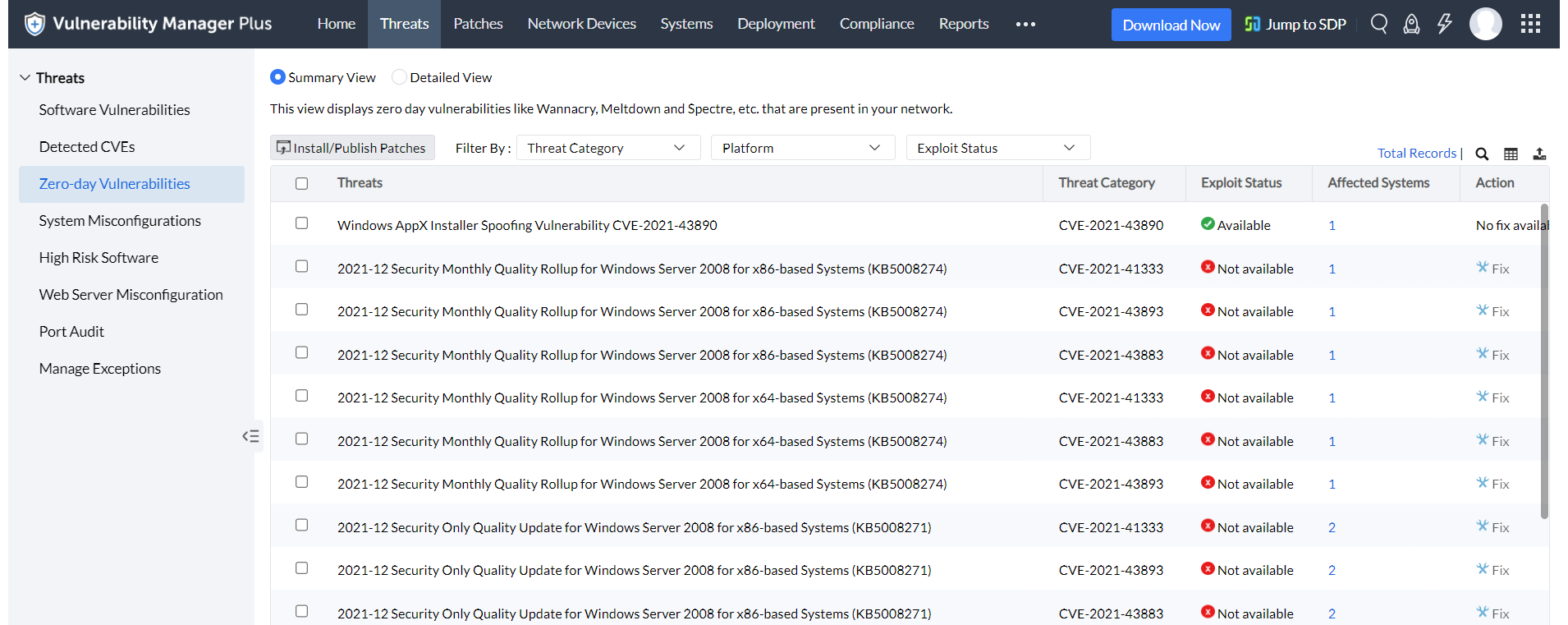
Subscribe to the Vulnerability Manager Plus pitstop to receive email notifications on the latest zero-day attacks and related news
Deploy mitigation scripts
Once zero-day exploits start circulating and vendors become aware, they're quick to publish a workaround to mitigate the issue while they develop a patch. Now, you can apply these workarounds to all affected machines instantly with Vulnerability Manager Plus prebuilt mitigation scripts that harden systems, alter registry values, close vulnerable ports, disable legacy protocols, etc., thereby minimizing the likelihood of a zero-day vulnerability being exploited in your network.
Stay up-to-date with the latest patches
A decade ago, a single zero-day vulnerability would have been powerful enough to topple your business. With increased security in modern-day operating systems, it takes at least two to tango, or sometimes even dozens of other known vulnerabilities, to successfully launch a zero-day attack.
Although keeping all the known vulnerabilities patched can't guarantee complete safety against zero-day exploits, it does make it more difficult for hackers to succeed if the intended target requires additional vulnerabilities to be exploited. The automated patch deployment feature in Vulnerability Manager Plus keeps all your OSs and applications up to date with the latest patches, thwarting hackers even if they manage to exploit a zero-day vulnerability.
Get notified about zero-day patches
When patches are released for vulnerabilities that were previously labeled as zero-days, they're called zero-day patches. As soon as a zero-day patch becomes available, Vulnerability Manager Plus alerts you in the console's notification bar. You can then reapply the mitigation script to revert the relevant workaround and apply the patch to fix the vulnerability permanently.
Establish a secure foundation with security configuration management
Vulnerabilities are just entry points into the network. Once attackers are in, it's the existing misconfigurations that they'll manipulate to laterally move towards the intended target. Take, for instance, the infamous WannaCry ransomware; it could've been prevented from spreading across a network before Microsoft released a fix by simply disabling the SMBv1 protocol and setting a firewall rule to block port 445. By using Vulnerability Manager Plus' security configuration management feature to conduct a thorough, periodic configuration assessment of your operating system, internet browser, and security software, you can easily remediate any misconfigurations and bring them back into compliance.
Audit antivirus solutions for definition files
As long as your antivirus protection is up to date, you should be protected within a few hours or days of a new zero-day threat. It's recommended that you audit antivirus software in your network to ensure it's enabled and up to date with the latest definition files.
Keep track of the OS and application end-of-life
Forget zero-day attacks on the latest software; software that has already reached the end of life will stop receiving security updates from the vendor and will remain forever vulnerable to any discovered zero-day vulnerabilities. Therefore, it's essential to conduct a high-risk software audit to identify which applications and OSs are approaching or have already reached end of life. Once they reach the end of their life, it's recommended that you migrate to the latest version of obsolete software.
There's no silver bullet solution that renders your network impenetrable to zero-day vulnerabilities, but having Vulnerability Manager Plus in your network and implementing the security measures discussed above could very well improve your stance against zero-day exploits. If your current vulnerability management tool relies only on software vendors to patch zero-days and leaves your network wide open until then, it's high time you opt for a tool that offers an alternative solution.
Not a user yet? Get your free, 30-day trial and fortify your network against zero-day exploits.
FAQs About Zero-Day Vulnerabilities
What is a zero-day vulnerability?
A zero-day vulnerability, also known as a 0-day vulnerability, is an unintended security flaw in a software application or an operating system (OS) that is unknown to the party or vendor responsible for fixing it. They remain undisclosed and unpatched, leaving gaps for attackers to swoop in while the public remains unaware of the risk.
What is the difference between a zero-day vulnerability and a publicly disclosed vulnerability?
A zero-day vulnerability is a security flaw in a product/software that is unknown to the vendor. A publicly disclosed vulnerability is made known to the vendor, and its details are disclosed in an open forum.
How does a zero-day attack happen?
While organizations focus on defending themselves against known threats, attackers slip past their radar by exploiting zero-day vulnerabilities. Zero-day attacks occur out of the blue because they target vulnerabilities that are not yet acknowledged, published, or patched by a vendor. Ever wondered why it's called a zero-day attack? The very term "zero-day" implies that the software developer or vendor has zero days to patch the flaw, since they're often unaware the vulnerability exists before attackers begin exploiting it.
How does an attacker find a 0-day vulnerability?
Security researchers and hackers alike incessantly probe operating systems and applications in search of weaknesses. They may use an array of automated testing tools to try to crash an application or to see if the program responds in ways the programmer never intended by feeding it multiple inputs, hoping to reveal a hole in the defenses. If they succeed, they're now aware of a 0-day vulnerability in the software. But unlike researchers who either report the flaw to the vendor or publish its details online to warn the public and force the vendor to release a fix, if cybercriminals find it, they use it to their own advantage.
Why are zero-day exploits dangerous?
Once the bug is discovered, the hacker will use reverse engineering tools to understand the cause of the crash. With this knowledge, they develop an exploit, which is a sequence of commands that manipulate the bug or vulnerability to their advantage. This is called a zero-day exploit. The zero-day exploit exploits the vulnerability to break into the system and deliver a payload, which could be malicious malware with instructions to disrupt system functions, steal sensitive data, perform unauthorized actions, or establish a connection to the remote hacker's systems.
Due to their high demand, zero-day exploits are often sold on the black market at very high prices to espionage groups and other malicious actors.
What are some real-life examples of zero-day vulnerabilities?
- The Stuxnet worm, the most notorious zero-day exploit, leveraged four different zero-day security vulnerabilities to launch an attack on Iranian nuclear plants. It is a self-replicating computer worm that altered the speed and sabotaged the centrifuges in the plants, shutting them down.
- The Spring4Shell zero-day vulnerability, detected in the Spring Core Java framework, can allow attackers to remotely inject malicious code into computers that can affect real-world Java applications.
Zero-day vulnerability vs. Zero-day attack vs. Zero-day exploit
Security vulnerabilities disclosed without a patch to mitigate them are referred to as zero-day vulnerabilities. When these zero-day vulnerabilities are exploited by cybercriminals, they are called zero-day exploits. Once vulnerabilities are exploited, they can escalate into targeted cyberattacks in which cybercriminals steal or extort data and money from your enterprise. This type of cyberattack is known as a zero-day attack. Therefore, zero-day vulnerabilities can be exploited to launch zero-day attacks.
