A framework-layer that continuously validates identity hygiene across systems—human and machine—as distinct from IAM’s enforcement at point of login.
On this page
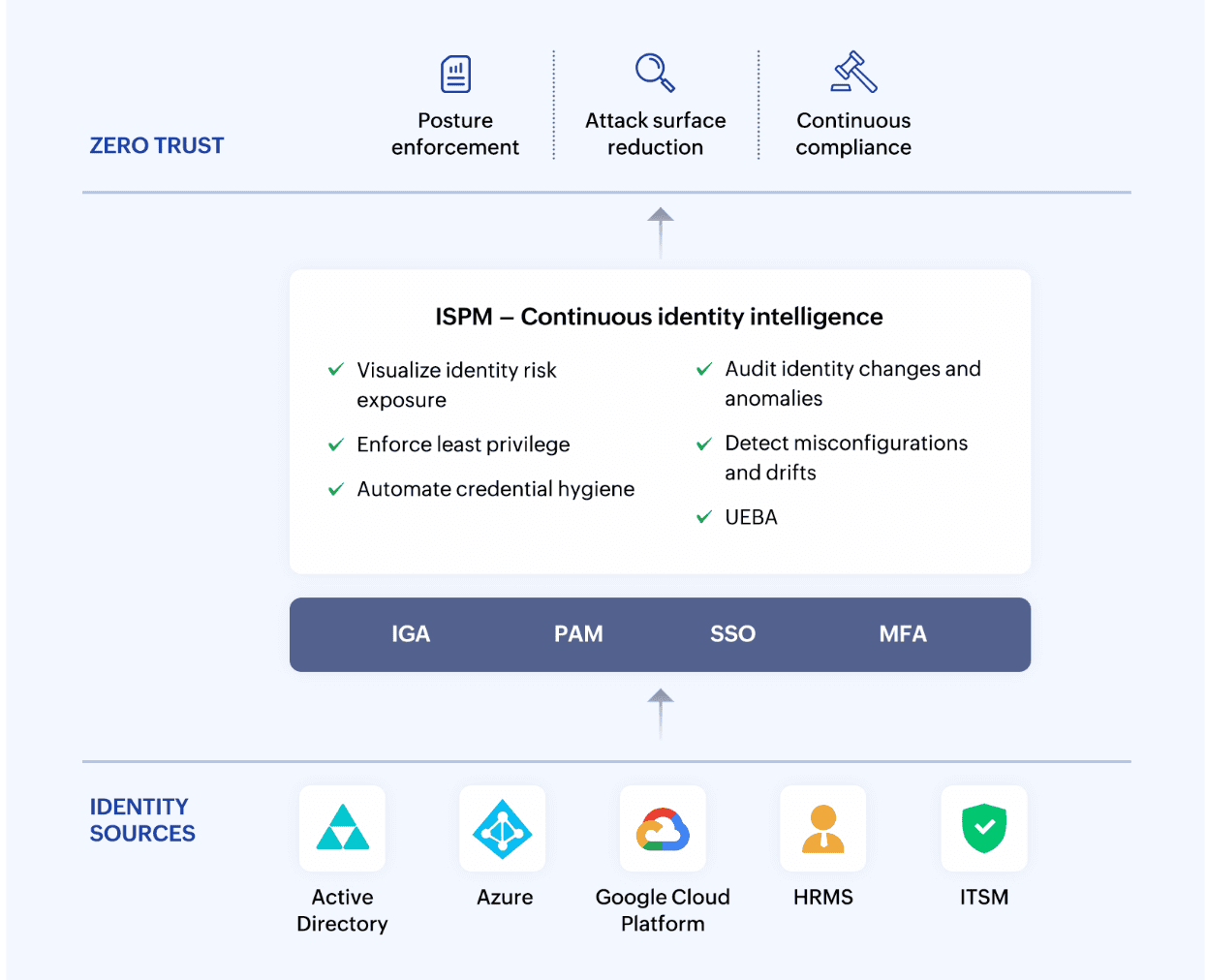
On paper, enterprise identity stacks look airtight. IGA governs who gets access, PAM locks down privileged accounts, SSO simplifies entry, and MFA verifies identity. Each tool does its job—but only within its own lane. None of them continuously check if the overall identity posture is drifting, if privileges have quietly accumulated, or if risky dependencies are hiding beneath the surface. That’s the gap: enterprises can deploy every acronym in the book and still miss how secure—or exposed—their identity layer truly is.
This is where Identity Security Posture Management (ISPM) comes in. ISPM doesn’t replace IGA, PAM, or MFA; it connects them. By continuously mapping identities, entitlements, and trust relationships across hybrid environments, ISPM provides a real-time view of the organization’s identity risk posture—and the ability to fix issues before attackers exploit them.
1. Policies are not protection: The illusion that puts your identity security at risk
Today's enterprises have sprawling identity architectures: identity providers for employees, partners, and customers; PAM systems for critical infrastructure; CIEM overlays for cloud roles; and directories that bind legacy and modern systems together. These tools—once configured—are expected to represent a secure, well-managed identity environment. While this belief is widespread, it's dangerously misplaced.
Identity today is not just a route to access—it is the attack surface. Threat actors no longer need to exploit code vulnerabilities when they can simply exploit credential misuse, excessive entitlements, and overlooked service identities. According to IBM’s Cost of a Data Breach Report 2024, compromised credentials remain the leading cause of data breaches, with each incident costing enterprises over $4.88 million on average. Verizon's 2024 Data Breach Investigations Report notes that over 60% involve credential abuse or misuse of access controls.
While identity providers, PAM, CIEM, IGA, and directories are essential, they focus primarily on enforcing access policies—determining who can access what.
They don’t continuously validate whether that access remains appropriate over time. This is the critical gap identity security posture management (ISPM) is designed to fill. It's a control layer that monitors, verifies, and challenges whether access is still justified—based not just on policy, but on behavior, context, and evolving risk.
2. The missing layer in your identity stack is posture management
ISPM is not an access broker, policy engine, or identity provider. It does not replace IAM, PAM, or CIEM tools. Instead, it forms a continuous observability and decision-making layer that inspects and challenges the real-time state of identity across systems—not based on policy configuration, but based on behavioral evidence, context, and security posture.
While traditional identity tools answer the question:
Can this identity access this resource based on policy?
ISPM answers the more critical question:
Should this access still exist, based on behavior, context, usage, and risk?
To do this, ISPM continuously collects and correlates telemetry across IAM systems, access logs, entitlement graphs, privilege assignments, API usage, and directory states. It uses this to identify posture anomalies that most IAM systems cannot surface:
- Excessive access privileges that exceed functional roles or are retained post-transfer.
- Dormant accounts—human and service—whose inactivity makes them ideal entry points for adversaries.
- Unmonitored service tokens that are still valid but unlinked to any current business function.
- Entitlement creep, especially across federated environments or multi-cloud CIEM layers.
- Configuration drift, or discrepancies between policy definitions and what’s actually in place.
- Inconsistencies across identity silos, such as mismatched entitlements between HRIS, Active Directory (AD), Microsoft Entra ID, and Okta.
Unlike policy engines, ISPM works retrospectively. It audits what IAM systems have provisioned and what is currently in effect, revealing where actual access deviates from policy intent. ISPM elevates access decisions from static policy enforcement to dynamic, risk aware governance that empowers teams to act with context. Crucially, ISPM is system-agnostic. It operates across vendors and architectures, integrating signals from PAM, CIEM, IGA, and third-party sources without introducing friction or dependence.
The strategic implications of ISPM are significant:
- Reduces attack surface by identifying and recommending the removal of unnecessary access.
- Improves compliance with real-time evidence of least privilege, rather than static policy attestations.
- Enables Zero Trust enforcement based on posture, not static trust assignments.
- Breaks identity silos by correlating entitlements, activity, and user behavior across platforms.
- Flags risk proactively before a breach scenario can materialize.
Gartner® and other leading analyst firms have identified misconfigurations—particularly in IAM and cloud security—as the single most consistent cause of breaches in hybrid environments. By 2026, "70% of organizations will prioritize identity-first security strategies to combat cloud-based threats." Additionally, the volume of machine identities is growing at 3–4x the rate of human identities, adding to complexity and fatigue-induced oversight.
IAM tools were designed to provision and enforce. ISPM was designed to verify and prioritize. Without ISPM, enterprises are effectively blind to the real-time validity of their identity landscape, leaving critical blind spots in their identity defense strategy.
3. IAM and PAM operate in isolation—and adversaries thrive in the silence
Each modular system operates in a vacuum. Their outputs do not intersect. Their assumptions go unchallenged. And their telemetry is never correlated unless it's done manually.
This systemic disconnect is not just inefficient—it introduces systemic risk. In practice, identity silos allow access to persist undetected, even when users or accounts should have been revoked, downgraded, or fully decommissioned.
Real-world examples illustrate how this plays out:
- A user account is disabled in Okta, but the same user retains persistent access to AWS via a legacy SAML-based SSO integration. The access token was issued prior to deactivation and never revoked because CIEM has no awareness of the change in Okta.
- In AD, nested group memberships grant domain-wide privileges through indirect inheritance. IAM policies reflect only top-level assignments, and provisioning logic misses the transitive access introduced via group nesting.
- A privileged session is logged and terminated by PAM, but the associated service token remains valid and active within a cloud CIEM-managed workload—unmonitored and unexpired.
These examples are not outliers—they are structural weaknesses. The core issue is that IAM and PAM systems do not reconcile identity state or access posture with each other. No single system has authoritative insight into the complete life cycle or context of access. As a result, misalignments persist silently, and lateral movement is no longer a brute-force exercise but a matter of slipping between tools that don’t communicate.
ISPM sits above these silos, continuously ingesting state, privilege assignments, session telemetry, and policy definitions from all identity systems. It identifies contradictions, unresolved access, and configuration drift—surfaces them for prioritization—and enables remediation through structured workflows or integrations.
ISPM replaces fragmented, human-driven reconciliation with continuous, cross-system posture validation—something most security teams lack both tooling and bandwidth to perform at scale.
4. What risks does ISPM explicitly target?
ISPM goes beyond abstract notions of so-called identity hygiene and directly addresses critical and often exploited risks across identity ecosystems. Chief among these is the challenge of excessive permissions—entitlements that extend beyond what users or systems require, which are usually a result of outdated roles, accumulated privileges, or unrestricted group memberships. These over-entitlements become easy access points during breaches.
Another insidious risk is the persistence of dormant and orphaned identities—user or machine accounts that remain active in some systems long after they’ve been deactivated elsewhere. These arise from fragmented provisioning and the absence of coordinated revocation logic across identity platforms. ISPM surfaces these accounts by correlating status across sources and flagging residual access. Unmonitored service accounts and hardcoded tokens form yet another class of risk, often overlooked due to their non-human nature. When left unrotated and unaudited, these credentials become persistent attack vectors that evade detection. Similarly, configuration drift—where intended IAM baselines diverge from real-world permissions—undermines security and compliance. This drift often occurs silently as systems evolve independently.
Lastly, ISPM exposes policy misalignment across cloud and on-premises environments. An identity might be correctly configured in Microsoft Entra ID, yet retain excessive rights in on-premises AD due to overlooked group inheritance. Or a CIEM-enforced cloud role might be contradicted by over-permissive SSO configurations. ISPM resolves these discrepancies by surfacing inconsistencies across identity control planes.
5. Understanding the root causes of identity posture weaknesses
Weak identity posture is rarely caused by a single oversight. Instead, it stems from structural and systemic inefficiencies. In many organizations, access management is siloed across departments and technologies, preventing holistic visibility. Role assignments are made in isolation, and access requests are approved without visibility into cumulative entitlements. This fragmentation is further amplified during rapid business changes—such as mergers or departmental growth—where access hygiene lags behind organizational scaling.
The absence of timely entitlement reviews is another factor. Traditional audit cycles are too infrequent to detect fast-moving changes. Drift goes unnoticed, privileges persist after role transitions, and temporary access becomes permanent. Additionally, many provisioning workflows err on the side of convenience, granting broad privileges “just in case” rather than following least-privilege principles.
ISPM addresses these root causes not by layering on complexity, but by integrating identity telemetry across platforms, continuously validating privilege alignment, and triggering guided remediation. It moves organizations from periodic compliance to continuous assurance.
6. How ISPM detects posture risks and drift
Effective posture management begins with comprehensive detection. ISPM platforms deploy multi-layered mechanisms to surface identity risk. At the foundation are inventory scans, which enumerate all human, machine, and service identities across platforms such as AD, Azure, Okta, and cloud infrastructures. These inventories establish the ground truth of who—and what—has access.
Privilege audits provide the next layer, analyzing roles, group memberships, direct permissions, and policy links. By mapping effective access rather than just assigned roles, ISPM uncovers privilege escalation pathways. These audits are reinforced by policy-baseline comparisons that assess current configurations against intended templates or role definitions.
Where ISPM distinguishes itself from traditional identity governance frameworks is in its behavioral dimension. User and entity behavior analytics (UEBA) monitor access patterns, login geographies, time-based anomalies, and lateral movement to detect suspicious activity that might not trigger static policy violations. Complementing this is the tracking of non-human identities—especially service account token issuance, usage, and expiration—providing visibility into one of the most opaque identity categories.
Together, these detection capabilities equip security teams with a comprehensive picture of identity risk—enabling timely, informed decisions.
7. Preventing identity-based posture threats
Spotting threats isn’t enough if you can’t respond to them. ISPM frameworks are built to operationalize risk insights into a preemptive defense. Prevention begins with enforcing least privilege—achieved through dynamic role-based and attribute-based access control frameworks that grant access only to the extent required and for the time needed.
Life cycle automation plays a crucial role. Synchronizing identity status with HRIS and ITSM systems ensures that terminations, role changes, and leave-of-absence events are reflected in real-time access revocations. This is bolstered by embedding posture checks into CI/CD pipelines, allowing identity risk to be assessed even before new systems or roles go live.
ISPM also introduces ongoing monitoring for high-risk accounts—particularly privileged or shared users—ensuring that stale or misused access is flagged early. Routine access certifications are automated and adapted to contextual risk, with quarterly or event-driven reviews prompted by drift or behavioral anomalies.
Finally, ISPM mandates enforceable policies around credential rotation, token expiration, and secure retirement of identities. When supported by policy-driven automation, these controls dramatically reduce the window of exposure for identity-based threats.
8. Tools and technologies supporting ISPM
ISPM is not a standalone product—it's an architectural approach that relies on a constellation of interconnected tools working in harmony. Foundational among them are:
- Identity governance and administration (IGA) systems, which provide essential visibility into users, roles, access histories, and workflow enforcement. These platforms support access certification campaigns, entitlement reviews, and approval routing, making them indispensable for ensuring posture accuracy.
- Privileged access systems contribute by enforcing fine-grained controls on high-risk accounts and sessions. They bring necessary oversight to activities that operate with elevated privileges, such as administrative actions or emergency access scenarios. When integrated into an ISPM framework, they contribute essential context for posture risk scoring and remediation workflows.
- Cloud entitlement tools bring visibility into dynamic cloud identities and permission boundaries. Their ability to detect overly permissive roles or cross-tenant access issues enriches posture awareness across multi-cloud environments. Yet on their own, they require orchestration to reconcile findings with on-premises and federated identity systems.
- Threat detection engines help map attack paths across identity surfaces, correlating events like lateral movement, credential abuse, or privilege escalation. These engines work in tandem with UEBA and SIEM platforms, which process identity-centric behavioral telemetry and surface anomalies indicative of posture violations or compromised accounts.
- Finally, authoritative identity sources such as HRIS and ITSM systems provide real-time updates on joiners, movers, and leavers. Their integration ensures posture fidelity across the employee life cycle and enables near-instant revocation or reassignment of privileges based on employment status.
The goal is not to consolidate tools, but to achieve strategic coordination—where identity posture data moves seamlessly across this ecosystem, supporting continuous, automated, and accountable enforcement of secure access across the enterprise.
9. CISO best practices for ISPM success
Here are recommended strategic practices for CISOs:
- Define ISPM metrics:
- Number of dormant identities
- Count of over‑privileged roles
- Shadow entitlements
- Unmanaged service tokens
- Embed ISPM in Zero Trust architecture: Don’t just enforce access at login—continually validate that trust isn't stale.
- Standardize identity hygiene across hybrid-cloud and multi-cloud: Local and cloud directories must reflect each other's identity states.
- Automate detection and remediation: Link posture alerts to playbooks—disable, attest, or flag when risk thresholds are crossed.
- Enable cross-functional ownership: Position ISPM under CISO, with IAM, GRC, cloud, and compliance teams partnering in operations.
- Train teams on hygiene and enforcement: Foster a least‑privilege mindset across engineering and admin teams.
- Review posture routinely: Baseline posture quarterly—or on every major merger, acquisition, or organizational change.
10. How is ISPM operationalized in practice
ISPM comes to life through a combination of identity intelligence, behavioral monitoring, contextual access decisions, and continuous auditability. It shifts posture management from a periodic review to a real-time operational discipline—embedded directly into the identity lifecycle.
Full-spectrum identity visibility:
Real-time visibility is established across identity stores, cloud directories, and infrastructure components. By maintaining a unified inventory of user and service accounts, and mapping entitlements across systems, it forms the foundation of identity posture—showing who has access, what they can do, and how that access evolves.
Behavioral analytics for posture drift:
Through baselining and anomaly detection, user behavior across endpoints, file systems, and directories is continuously monitored. Deviations such as unusual logon times, privilege misuse, or anomalous resource access offer early signals of identity compromise or misalignment, enabling timely intervention.
Attack surface insights:
Posture assessments surface identity-related attack paths, including dormant accounts, excessive permissions, stale entitlements, and unmonitored service accounts. These risks—often buried in hybrid and multi-domain environments—can be prioritized for cleanup or control reinforcement based on their exploitability.
Risk-based authentication decisions:
Context-aware authentication factors in device type, IP range, login time, and historical behavior. This enables dynamic access decisions—such as step-up authentication, access denial, or alerting—when posture appears risky or deviates from normal patterns.
Cross-platform auditing and change tracking:
Detailed logs are captured for logons, file access, privilege changes, account modifications, and GPO updates across domain controllers, member servers, and key systems. By correlating access activity with changes in configuration or entitlements, ISPM provides continuous posture validation and incident investigation depth.
Real-time response to identity threats:
Identity threat signals—such as lateral movement attempts, logon anomalies, or unauthorized privilege elevation—can trigger automated workflows. These may include revoking access, disabling accounts, escalating alerts, or applying conditional restrictions. This helps contain posture breaches as they unfold.
Lifecycle-centric posture alignment:
Access rights are aligned with business roles by integrating with directory data, provisioning systems, and HR sources. Joins, moves, and exits are reflected in near real-time, reducing lag in entitlement adjustments and minimizing the risk of orphaned or overprivileged accounts.
Policy enforcement through automation:
Policy logic is embedded into access approvals, role assignments, and entitlement checks. When violations occur—such as unauthorized group membership or role drift—automated actions can enforce correction, trigger re-certification, or alert stakeholders for review.
Audit-ready compliance reporting:
Structured, regulation-ready reports on identity posture show who has access, how it's used, and where deviations occurred. These reports support compliance frameworks like SOX, HIPAA, and GDPR, and provide clear evidence of posture enforcement over time.
Posture assurance for hybrid work:
As identity boundaries shift beyond the corporate network, posture enforcement extends to remote workers and endpoints. This ensures consistent application of access policies and monitoring—regardless of user location or connectivity.
ISPM doesn’t just exist as a concept—it operationalizes posture awareness into every phase of the identity lifecycle, enabling security and compliance teams to monitor, enforce, and respond in real time. In the face of hybrid IT, insider threats, and regulatory pressure, posture becomes a living control—and ISPM makes it actionable.
FAQ
IAM pipes rules in place, but ISPM checks whether those rules are still safe, relevant, and accurately reflected across tools—today, not months ago.
Yes. It uses APIs, logs, and connectors to automatically inventory identities, detect drift, assess risk, and trigger remediation—via SIEM, IGA, CIEM, and orchestration tools.
Organizationally, ISPM should reside in the office of the CISO—with distributed accountability across IAM, GRC, cloud security, compliance, and operations.
Continuously. At a minimum, baseline posture assessment should occur quarterly and after major system changes or workforce events.
ISPM focuses specifically on strengthening the security posture of identities by detecting privilege drifts, misconfigurations, and risky entitlements, while Zero Trust is a broader security framework that enforces continuous verification and least privilege for all users, devices, applications, and network interactions.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement the principles of least privilege with AD360. o learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect compromised credentials, reduce breach impact, and lower compliance risk exposure with Log360. To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
