On this page
Ransomware is data-encrypting, malicious software that demands payment to release the data it has infected. An entire organization's or an individual user's crucial files are targeted and encrypted, denying the users access to their vital data. The encrypted files are still present on the victim’s system, but since they have been encrypted by ransomware, they cannot be accessed.
Once the data is encrypted, the malicious actor demands a ransom from their victim in exchange for the release of the infected data. The victim is also given instructions on how to pay to get a decryption key in return. Attackers usually demand payment in Bitcoin.
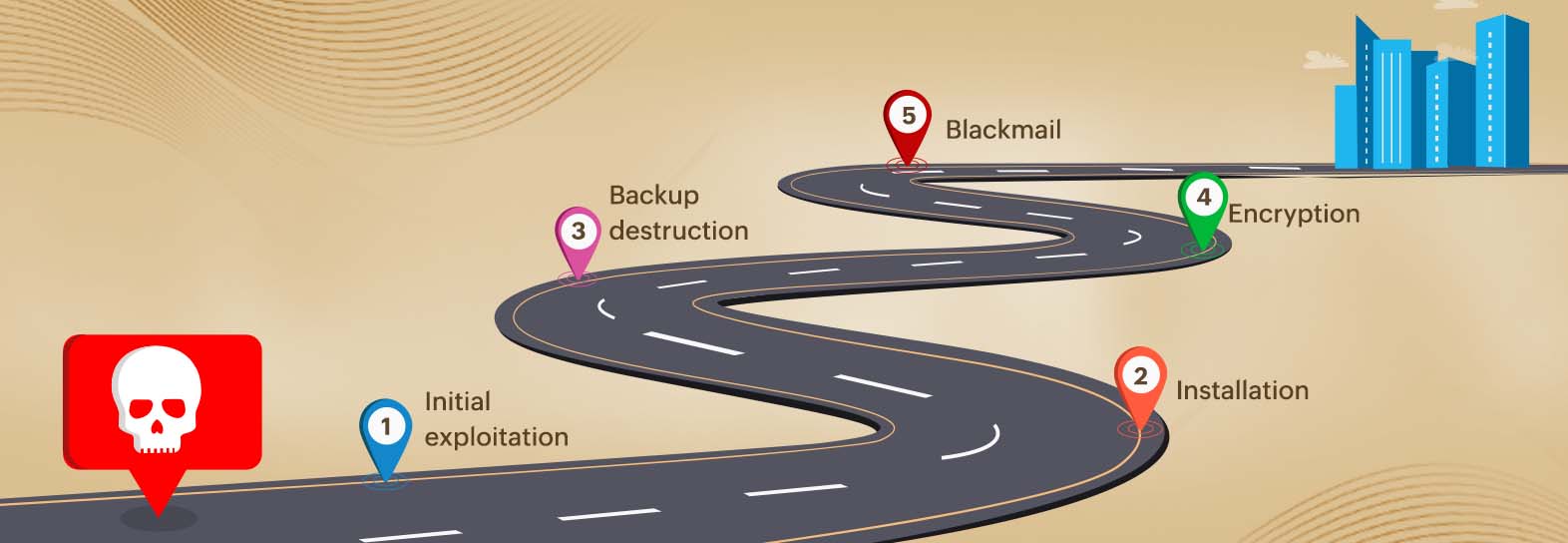
Here are the five main stages of a ransomware attack:
Stage 1: Initial exploitation
The first stage of a ransomware attack is initial exploitation, wherein an attacker sets up the ransomware to invade the victim’s system and, if targeting an organization, get a foothold in the company's network. There are many methods that attackers can utilize for this initial step, such as sending out phishing emails, brute-forcing into vulnerable servers, redirecting victims to malicious websites, or compromising a remote desktop connection.
Phishing is by far the most popular method among cybercriminals for carrying out this initial step.
Stage 2: Installation
Once the ransomware invades the victim's system, the second stage of installation takes place. Each time the victim's system boots up, the malicious code will be executed so as to gain persistence in the network. At this stage, the ransomware may also check and decide if the targeted victim's system is worth infecting or not and if it should proceed with the attack further. For example, if it detects that the targeted machine is a sandbox or a virtual machine, it may quietly exit.
Stage 3: Backup destruction
In the third stage of the attack, the ransomware checks for any backup files on the victim's system and destroys them. This creates a sense of fear in the victim and thereby increases the chance of the ransom being paid.
Stage 4: Encryption
At this fourth stage of the attack, the ransomware executes its malicious code and starts encrypting the victim's critical data. To achieve this, the installed ransomware establishes a connection with a command-and-control server, which holds the encryption key and gives instructions for the encryption. It might also give instructions on which specific file formats should be targeted for encryption.
Stage 5: Extortion or blackmail
In the final stage of attack, the attacker demands payment in return for the decryption key used to recover the infected files. A ransom message appears on the victim's screen, informing them that they have been targeted and compromised. This ransom message also contains instructions on how the payment has to be made. Generally, victims are given a specific time by which they should make this payment to get their important data back.
It is quite evident that a ransomware attack is not a one-step attack; rather, it is a chain of events that is capable of causing massive destruction, especially if carried out on a large scale.
The key to combating these attacks is to create awareness among organizations and security teams about how this type of attack operates. With an understanding of the ransomware life cycle, users and security teams can be more proactive in their prevention and recovery strategies. Organizations should also adopt a SIEM solution like ManageEngine Log360, which helps detect the tell-tale signs of ransomware through real-time event correlation, alerts, root cause analysis, and anomaly detection. These capabilities provide several avenues to combat ransomware attacks at every stage.
Try a free, 30-day trial of Log360 today to test the solution out for yourself.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement Zero Trust and the principles of least privilege with AD360.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect compromised credentials, reduce breach impact, and lower compliance risk exposure with Log360.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.