- Unified security environment
- Breaking down the walls: Unified security
- Combining endpoint security
- Integration process
- Why choose Log360
Unified security environment for effective threat detection and remediation
Imagine a security analyst investigating a cyberattack. They have access to a vast amount of data—firewall logs, endpoint security alerts, network traffic data—but it is scattered across different tools. This fragmented landscape, known as security silos, can create a complex environment as each tool operates independently with its own data format.
For security teams, this can lead to limited visibility and a lack of context while handling anomalies from different tools. It also means a slower investigation process and longer response times due to siloed data.
Breaking down the walls: Unified security
To foster a unified security environment, ManageEngine's SIEM solution, Log360, integrates with ManageEngine's endpoint detection and response (EDR) solution, Endpoint Central.
By pulling security data points from Endpoint Central and applying them in the advanced threat detection module in Log360, you can quickly and effectively investigate and respond to security incidents. This can help:
- Unify your security posture: Get a complete picture of your security health by combining endpoint data from Endpoint Central with network activity in Log360. This eliminates blind spots and helps you identify real threats hiding among the noise.
- Fast-track threat investigations: The Incident Workbench in Log360 automatically assembles a timeline of suspicious events, streamlining your investigation process.
- Improved MTTR and MDR: Log360 uses advanced analytics to detect high-fidelity threats with pinpoint accuracy. When a threat is identified, Log360 triggers automated responses in Endpoint Central to patch vulnerabilities, automatically stopping threats in their tracks. This translates to significantly faster mean time to respond (MTTR) and improved managed detection and response (MDR) capabilities.
Combining endpoint security with advanced attack detection capabilities
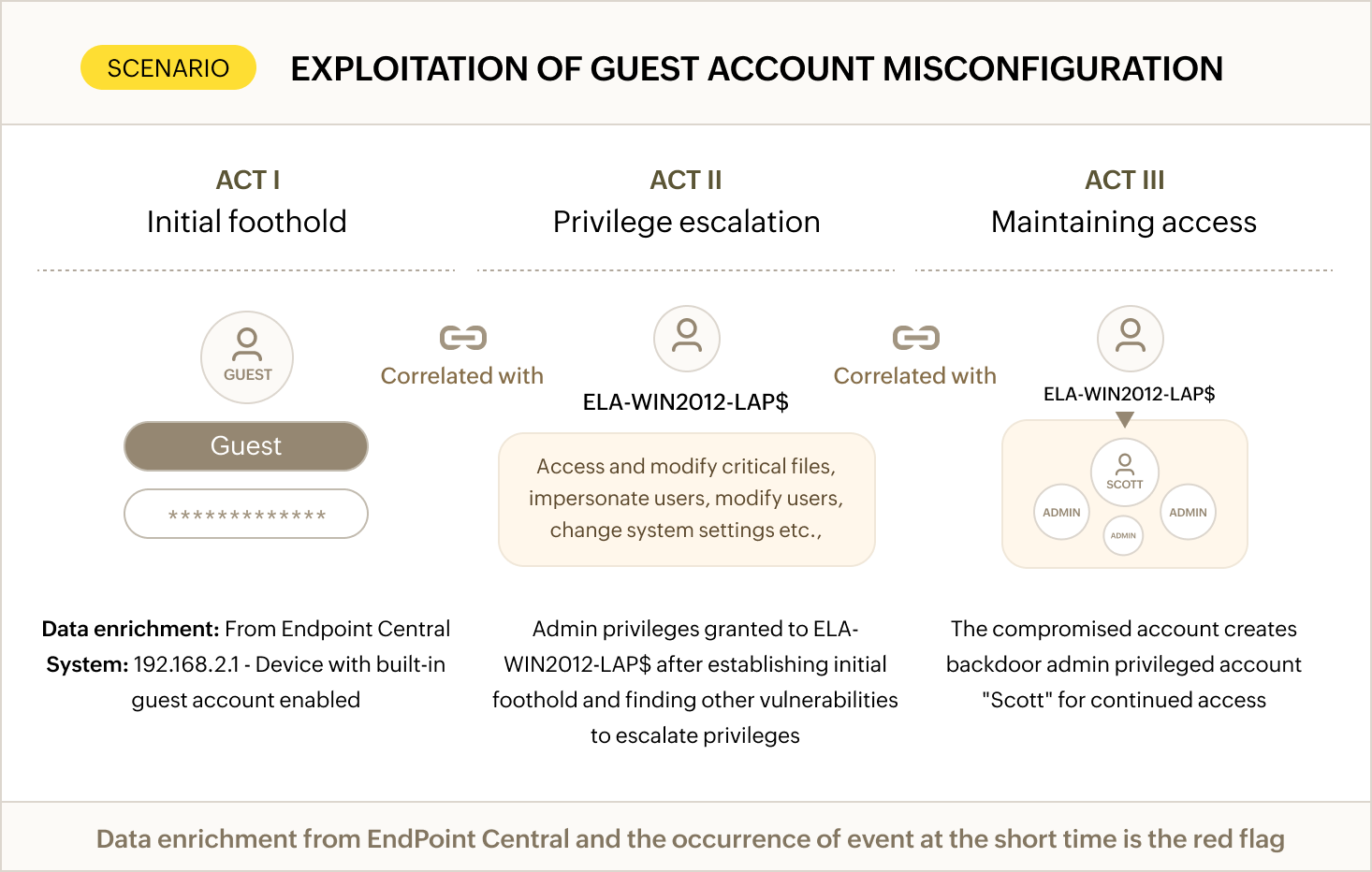
Privilege escalation and lateral movement detection
Log360 automatically detects misconfigured user accounts that could be exploited by attackers. This out-of-the-box rule helps prevent privilege escalation attempts, a common tactic used to gain access to critical systems.
Through having complete visibility into the health and behavior of your devices from Endpoint Central, you can spot compromised machines that attackers might use as footholds to move laterally across your network and launch further attacks.
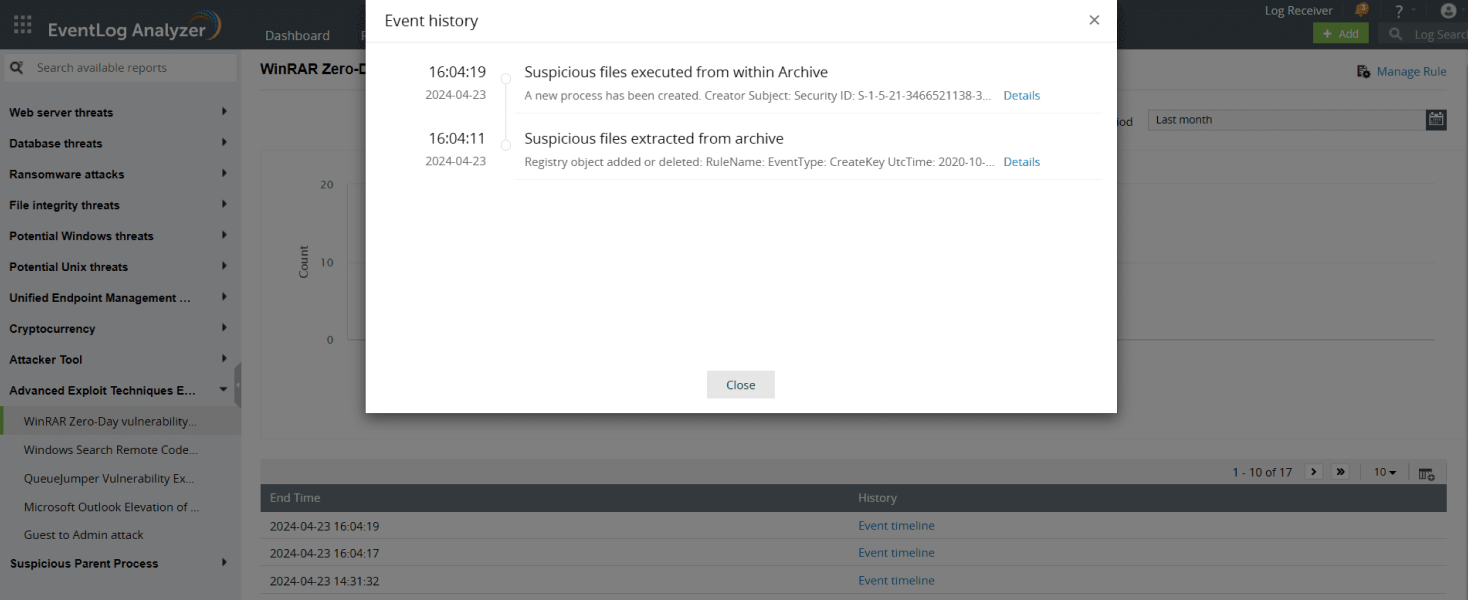
Zero-day exploitation detection
Advanced anomaly detection capabilities go beyond known vulnerabilities to uncover even the latest zero-day exploits. This proactive approach ensures you are protected from the newest threats, including recent exploits like the WinRAR zero-day, Windows Search remote code execution, and QueueJumper and Microsoft Outlook vulnerabilities. Log360 provides in-depth analysis of these exploits, empowering you to understand how they work and effectively safeguard your network against them.
Alert triaging and faster threat resolution
Log360 prioritizes security alerts based on threat context and endpoint data, helping security teams focus on the most critical issues first while automating incident response workflows. This reduces alert fatigue by filtering out false positives and streamlines the process by automatically isolating endpoints, patching vulnerabilities, or containing threats upon detection.
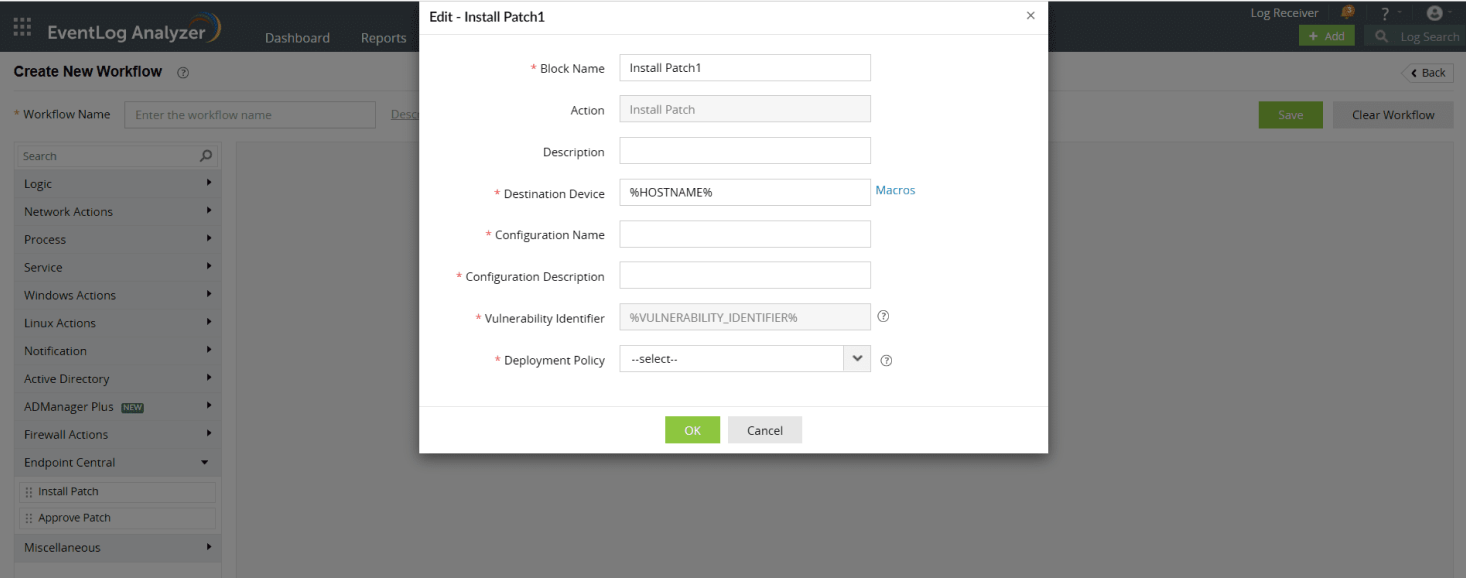
Integration process
You can integrate Endpoint Central in Log360 in a few easy steps.
- To integrate Log360 in Endpoint Central, please follow these steps.
- To utilize the threat detection and alert functions, you should enable Data Enrichment. To know how to configure this in Log360, see our help document.
Why choose Log360 for a unified security experience?
-
Improved security visibility
Gain a holistic view of your IT infrastructure, including user activity, endpoint health, and network traffic.
-
Reduced security complexity
Consolidate security data from disparate sources into a single pane of glass for simplified threat detection andinvestigation.
-
Vulnerability exploitation detection
Get alerted on the latest vulnerability exploits, including zero-day vulnerabilities, in real time.
-
Expedited threat resolution
Approve and install patches on vulnerable endpoints as soon as they are detected from a single console.