Steps to modify REST API permissions
Though we suggest providing all the recommended permissions, organizational requirements may not allow this. In this section, you will learn how to modify the REST API permissions for an already configured tenant. If you are looking for a way to configure a tenant with only the permissions you require, please configure it manually.
Prerequisite: The tenant has been successfully configured in M365 Security Plus and REST API is enabled for it.
- Log in to the Microsoft Entra ID admin center using the credentials of a Global Administrator or any other user account with the permission to create Entra applications.
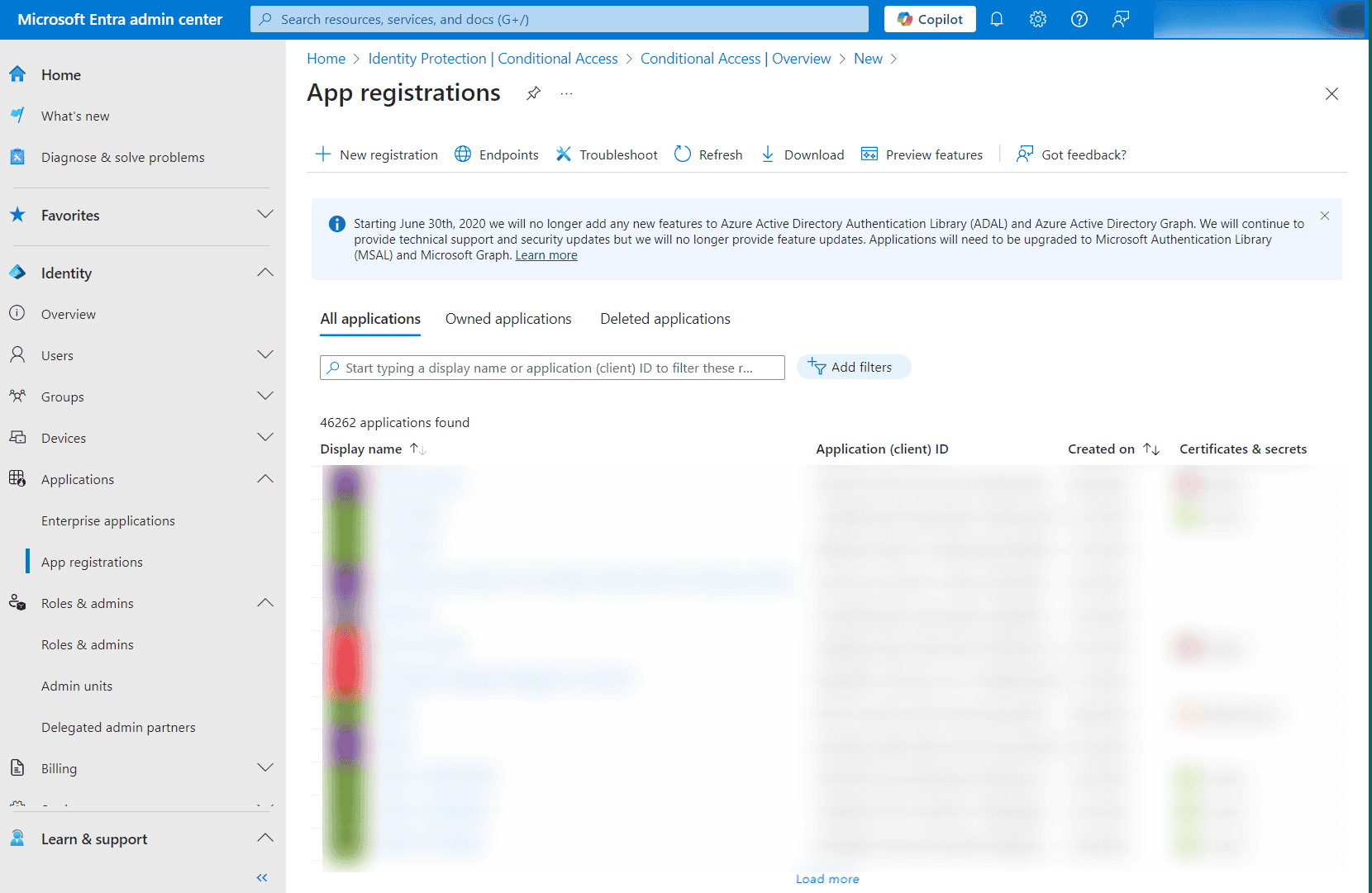
- Navigate to Identity > Applications > App registration.
- Select All applications.
- Search for the application name from step 7 of the previous section and click it.
- Select API Permissions under Manage.
- Choose Microsoft Graph.
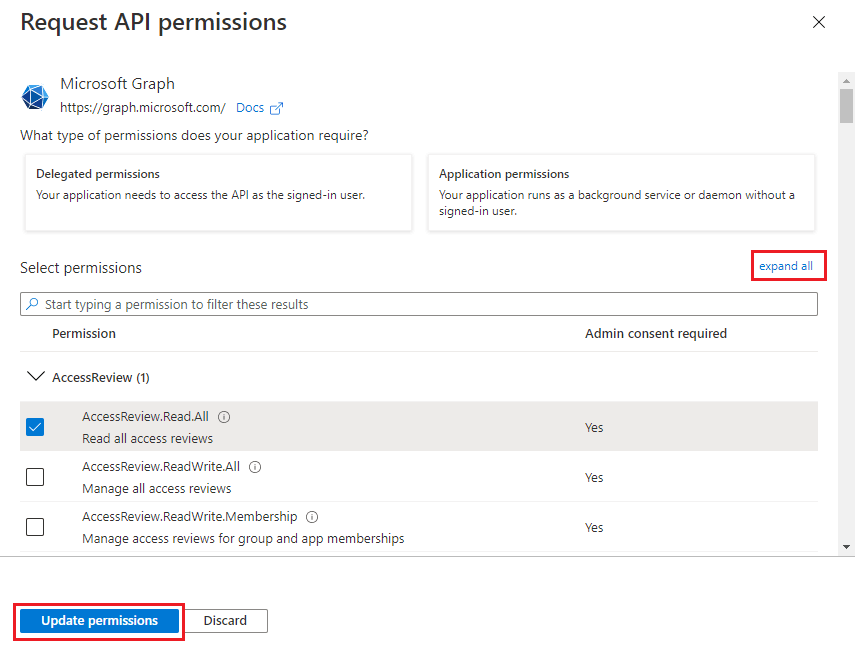
- Click expand all to view all the permissions already granted to this application.
- Add, remove, or modify permissions as per your requirements.
- Click Update permissions.
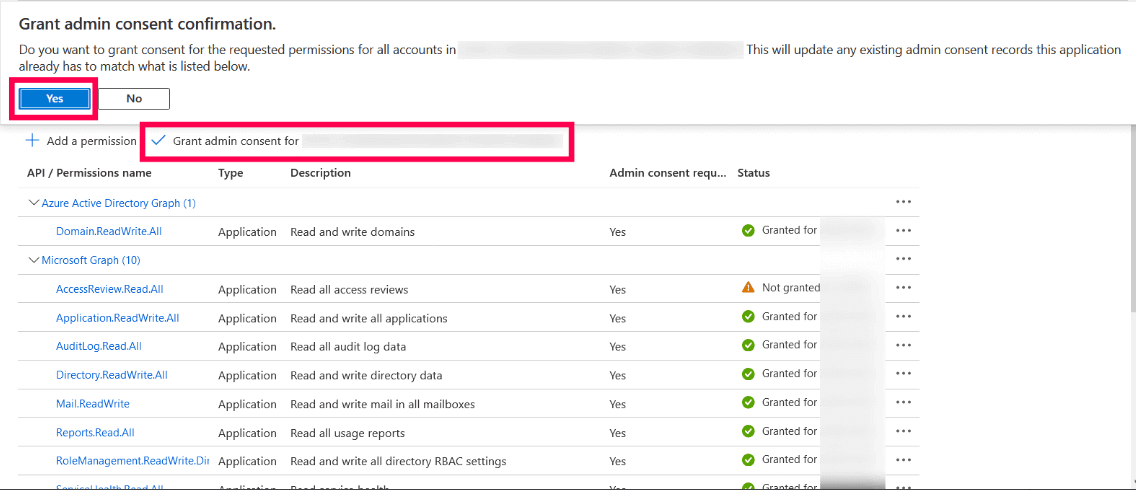
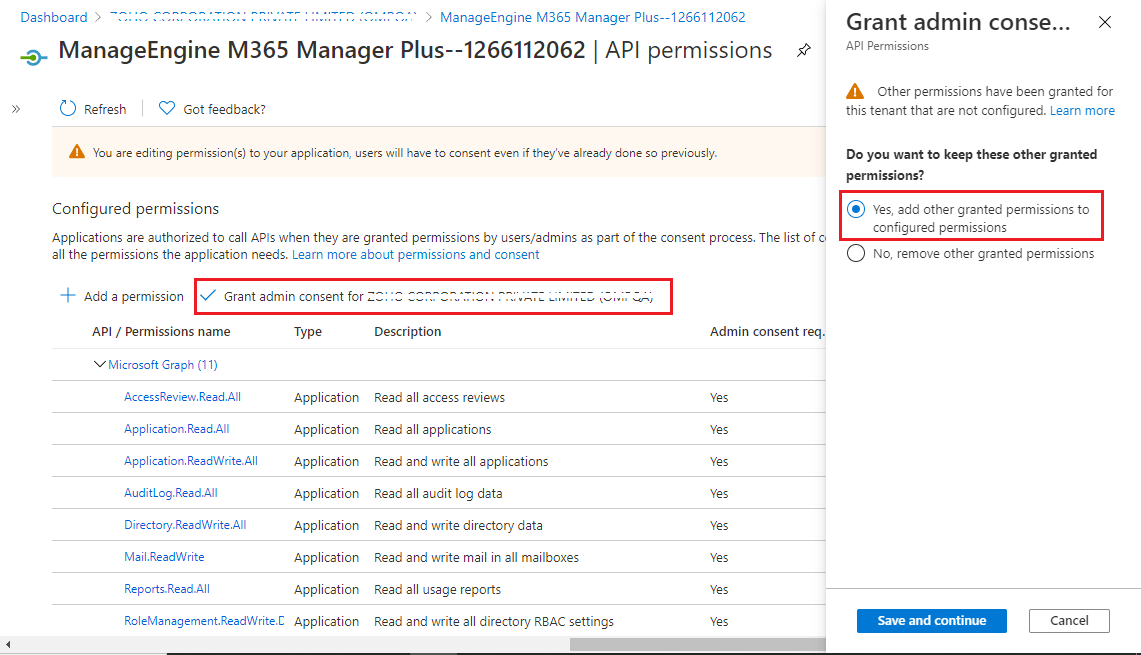
- Select the Grant admin consent for domain_name option found at the top of the permissions table.
- Choose Yes in the box that appears.
- You have now successfully modified the permissions required by the REST API application.
Steps to modify a Microsoft 365 tenant
- Click the Tenant Settings option found in the top-right corner.
- You will see the list of Microsoft 365 tenants configured in M365 Security Plus.
- Under the Actions column, click the corresponding to the tenant you need to modify
- Click the
 icon adjacent to Application Details to modify the corresponding values.
icon adjacent to Application Details to modify the corresponding values.
- Click Update once you have made the changes.
Don't see what you're looking for?
-
Visit our community
Post your questions in the forum.
-
Request additional resources
Send us your requirements.
-
Need implementation assistance?
Try onboarding