Integrating Microsoft AD CS server with MDM
Microsoft Active Directory Certificate Services (AD CS) provides digital certificates that can be used to encrypt, digitally sign and authenticate users and devices on a network. By integrating Microsoft AD CS with Mobile Device Manager Plus, IT admins can leverage AD and Groups Policy for certificate registration and assignments. It allows organizations to dynamically create user-specific certificates, distribute certificates at large scale and automatically renew the certificates on devices, thereby ensuring data security and compliance to organizational standards.
Pre-requisites
NDES must be installed in a Windows Server machine
- Open the Start Menu, select Run, type mmc, and click OK.
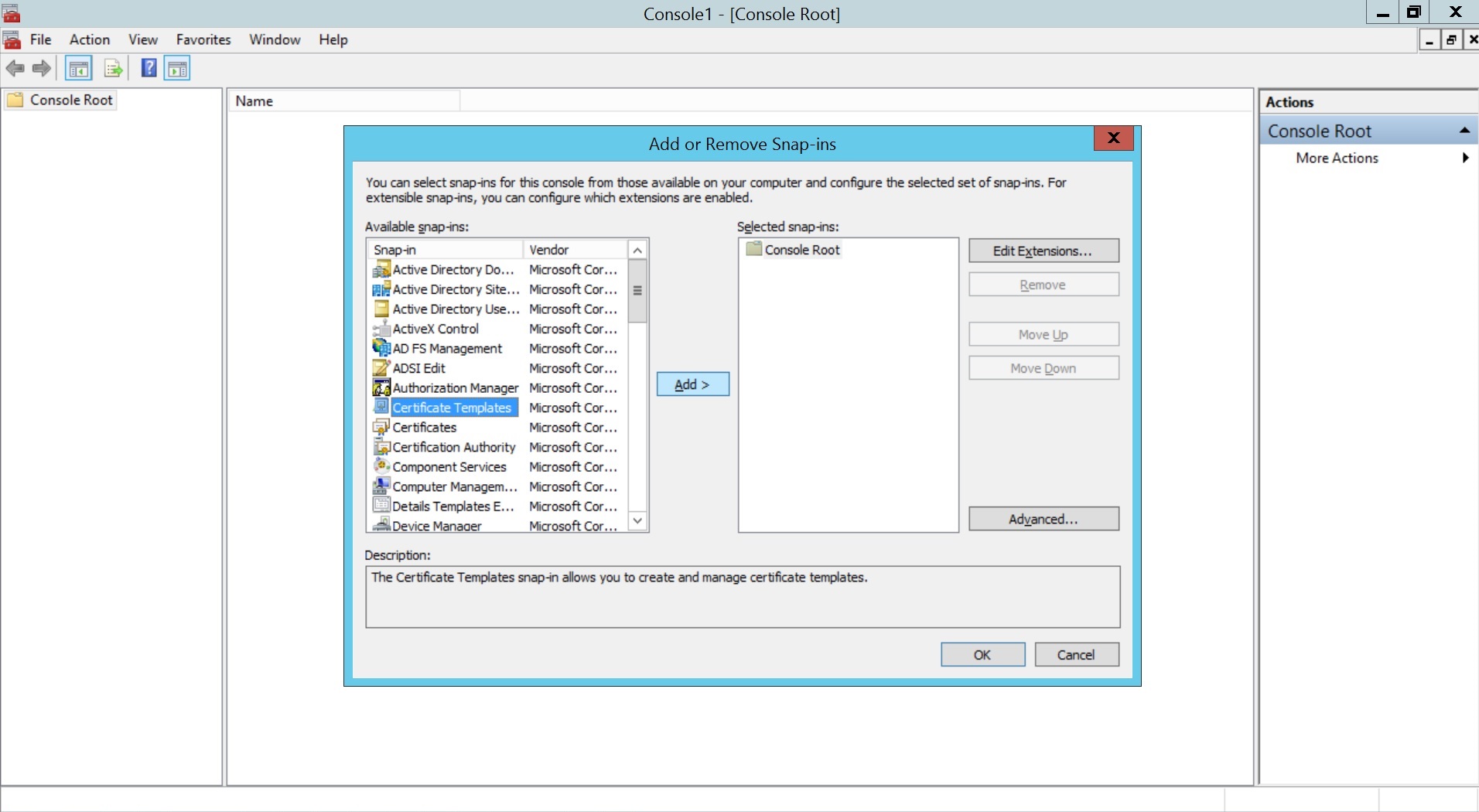
- Go to File > Add/Remove Snap-in, select Certificate Templates, click Add, and then click OK.
- Right click Certificate Template and select Manage.
- Right Click on the required template and select Duplicate Template.
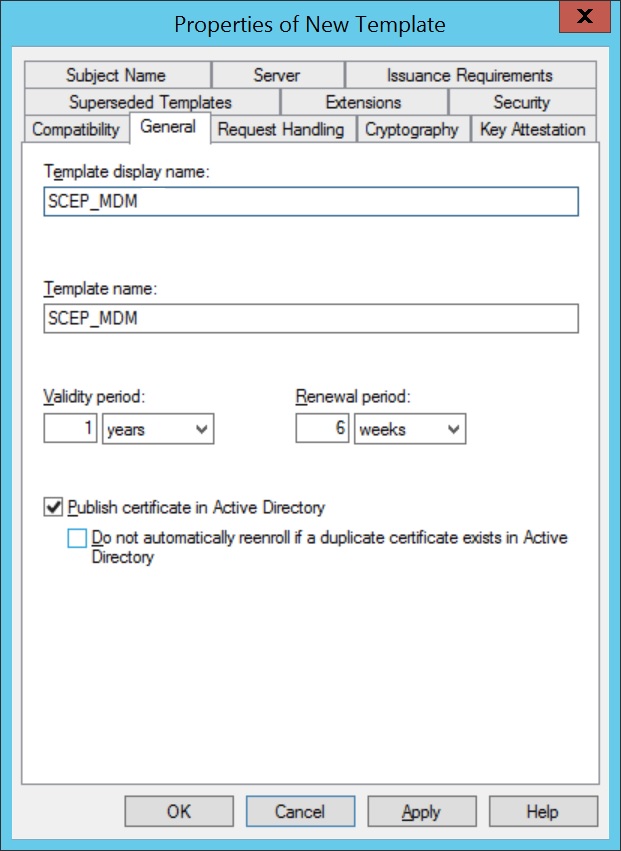
- Specify a Template display name and save it by clicking OK to save the new template
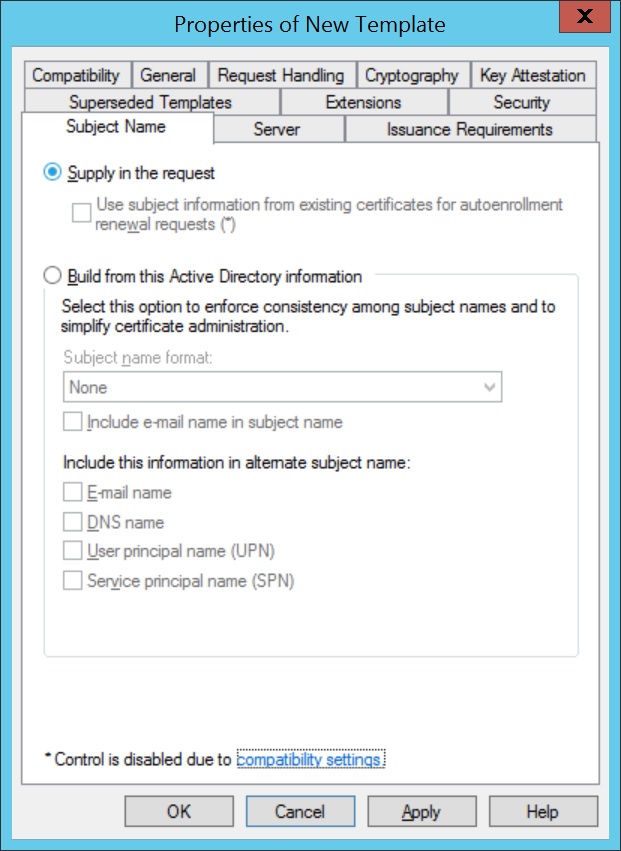
- Navigate to Extensions > Application Policies, click Edit, and add Client Authentication to the list of policies.
- Select Cryptography and configure the Minimum Key Size. A key size of 2048 bits is recommended for enhanced security. This value must match the configuration used when setting up SCEP in MDM.
- Create a dedicated Active Directory (AD) user account for the NDES service. This NDES Service account will be used by ADCS to proxy certificate requests from MDM-enrolled devices.
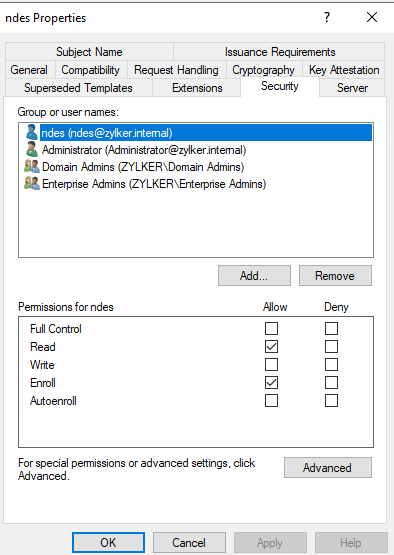
- Go to the Security tab of the certificate template > Add the NDES service account > Grant Read and Enroll permissions.
Important Note: Avoid granting Enroll permissions to broad or widely scoped groups, such as Domain Users. This can lead to unintended enrollments, unauthorized certificate requests and potential impersonation risks. - Click on Subject Name and select Supply in the request, for subject names to be specified in the certificate request.
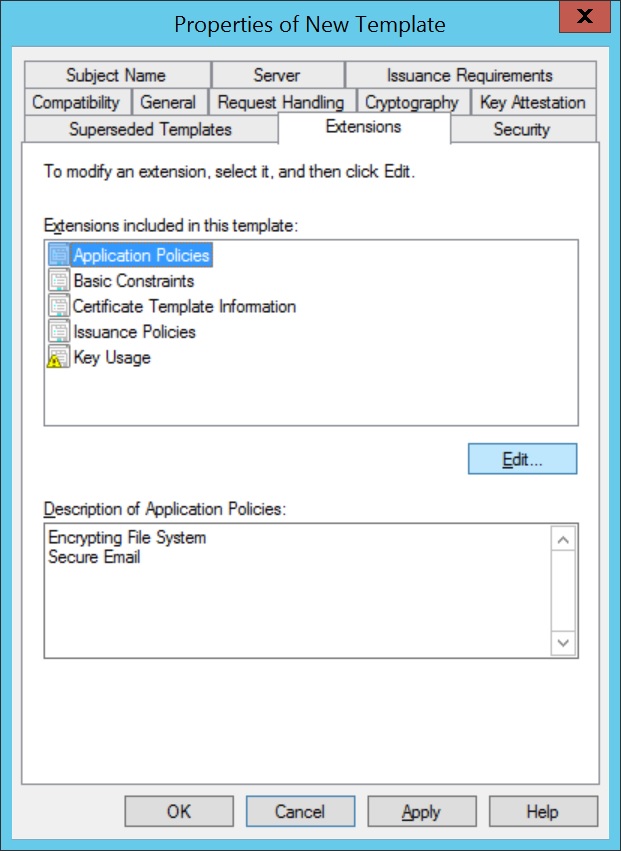
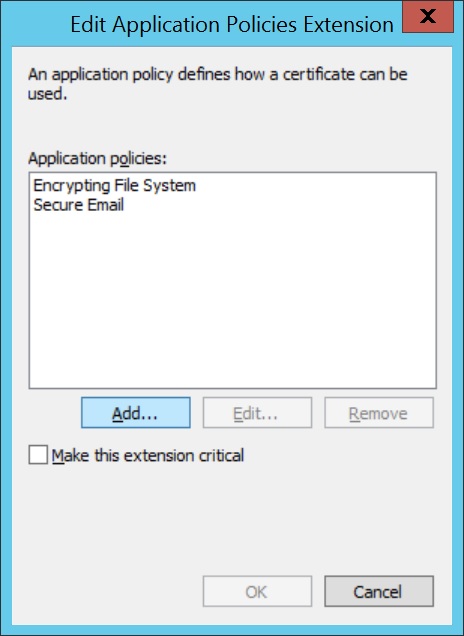
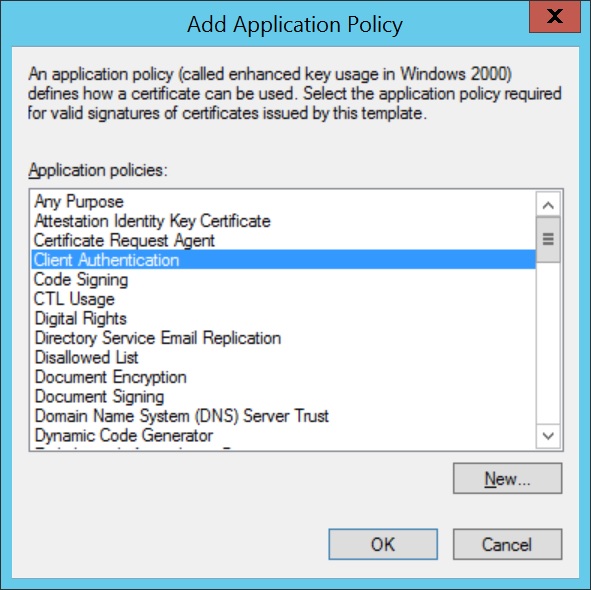
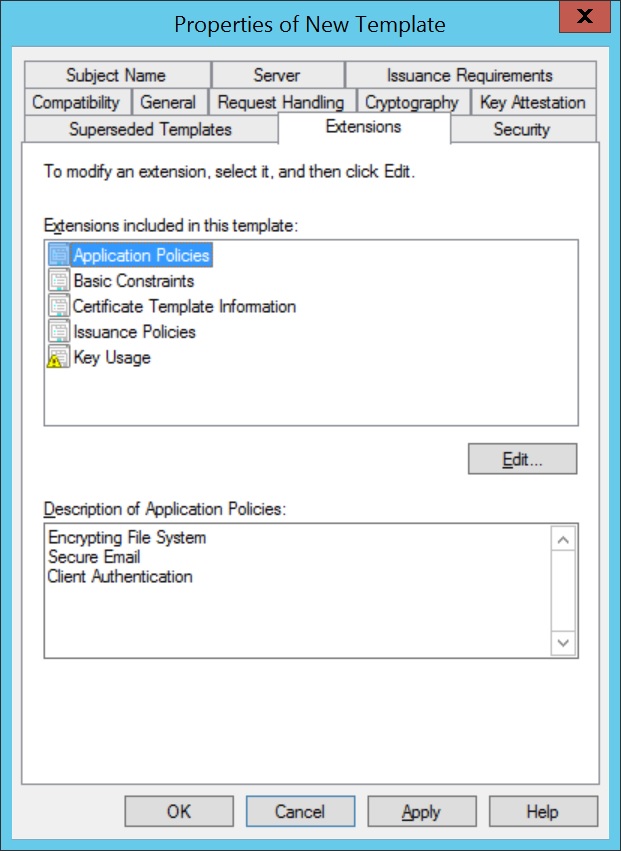
Note: Add or remove only the required Application Policies values.
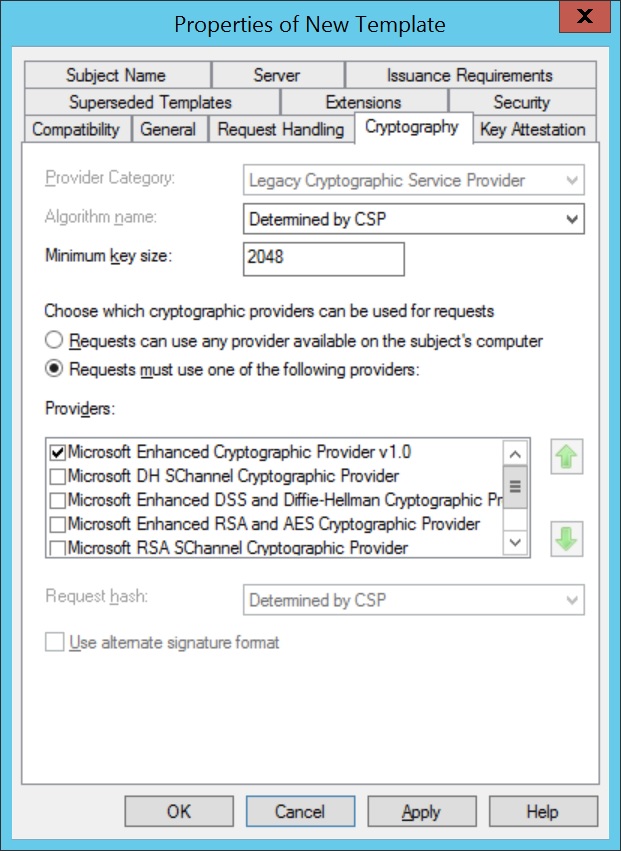
Make sure to take a look at your existing certificate templates and review if the permissions are setup properly by following the recommended steps in our how-to document . Read more on technical controls for securing PKI on the Windows official documentation.
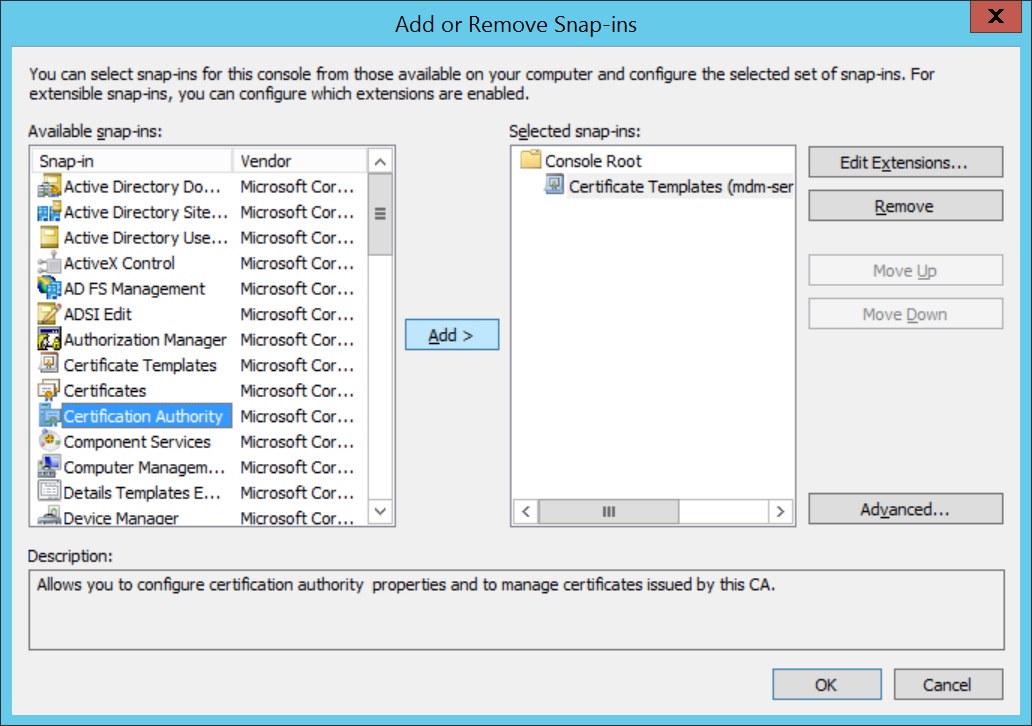
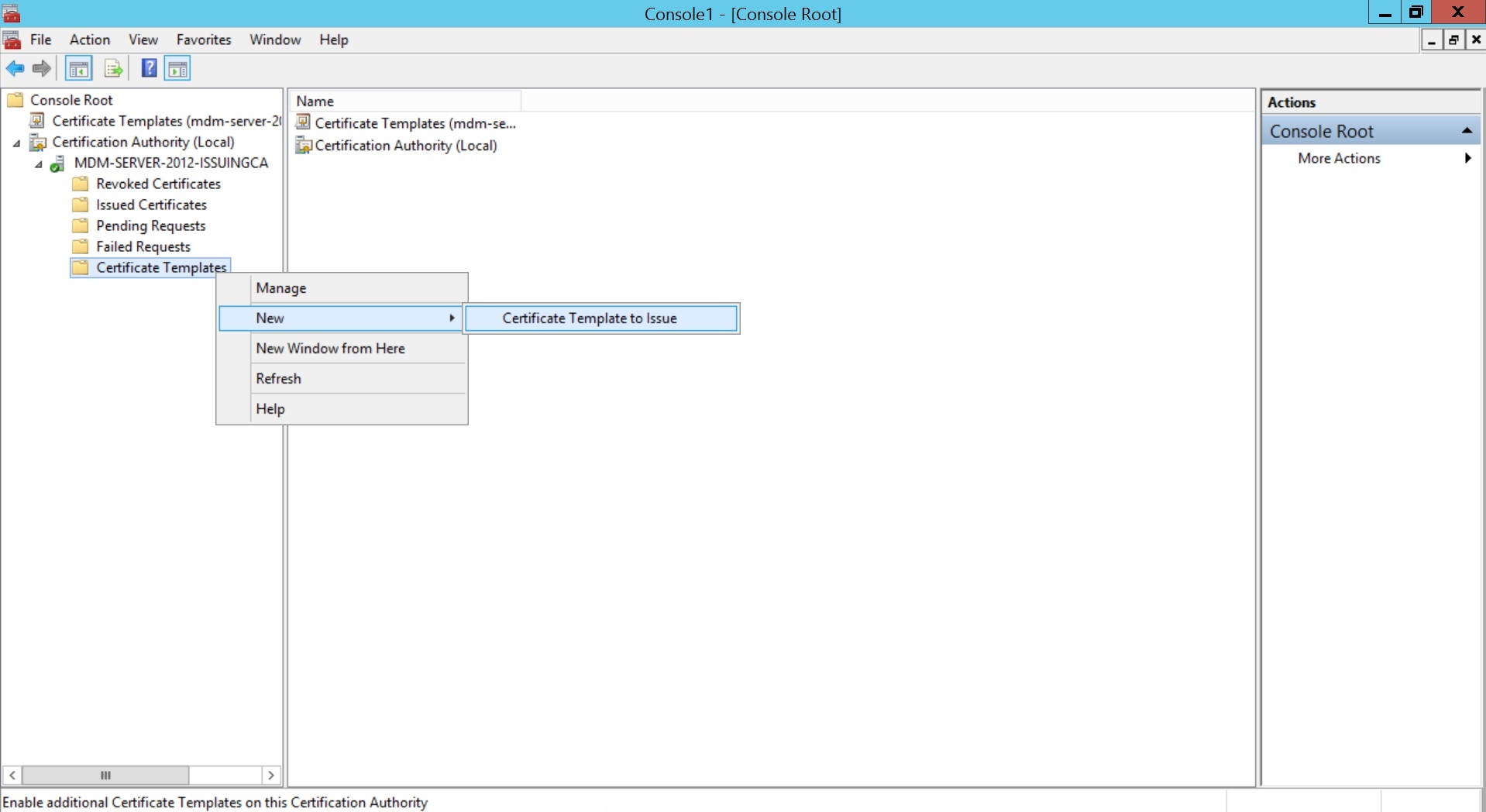
- Add Certificate Authority as a snap-in in the Microsoft Management Console(MMC).
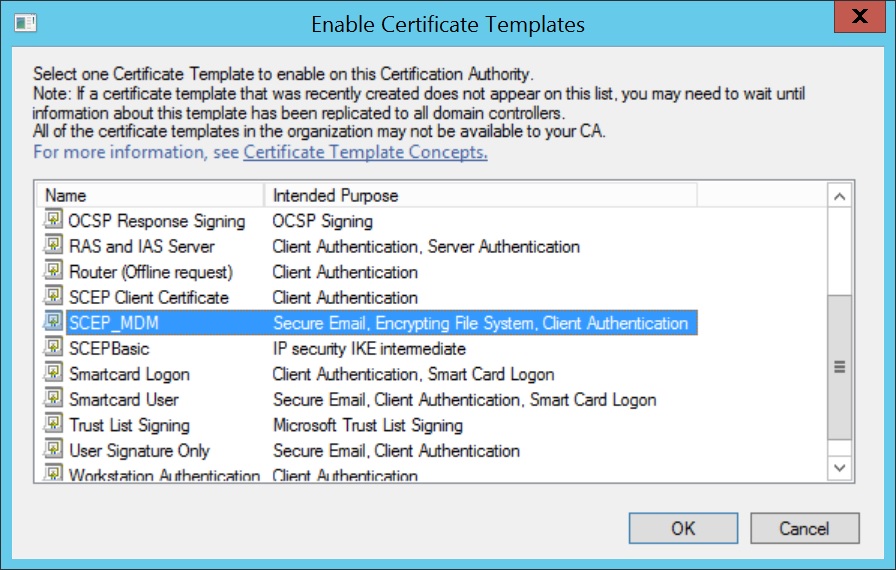
- Expand Certification Authority and right-click on Certificate Templates. Click New and select Certificate Template to Issue.
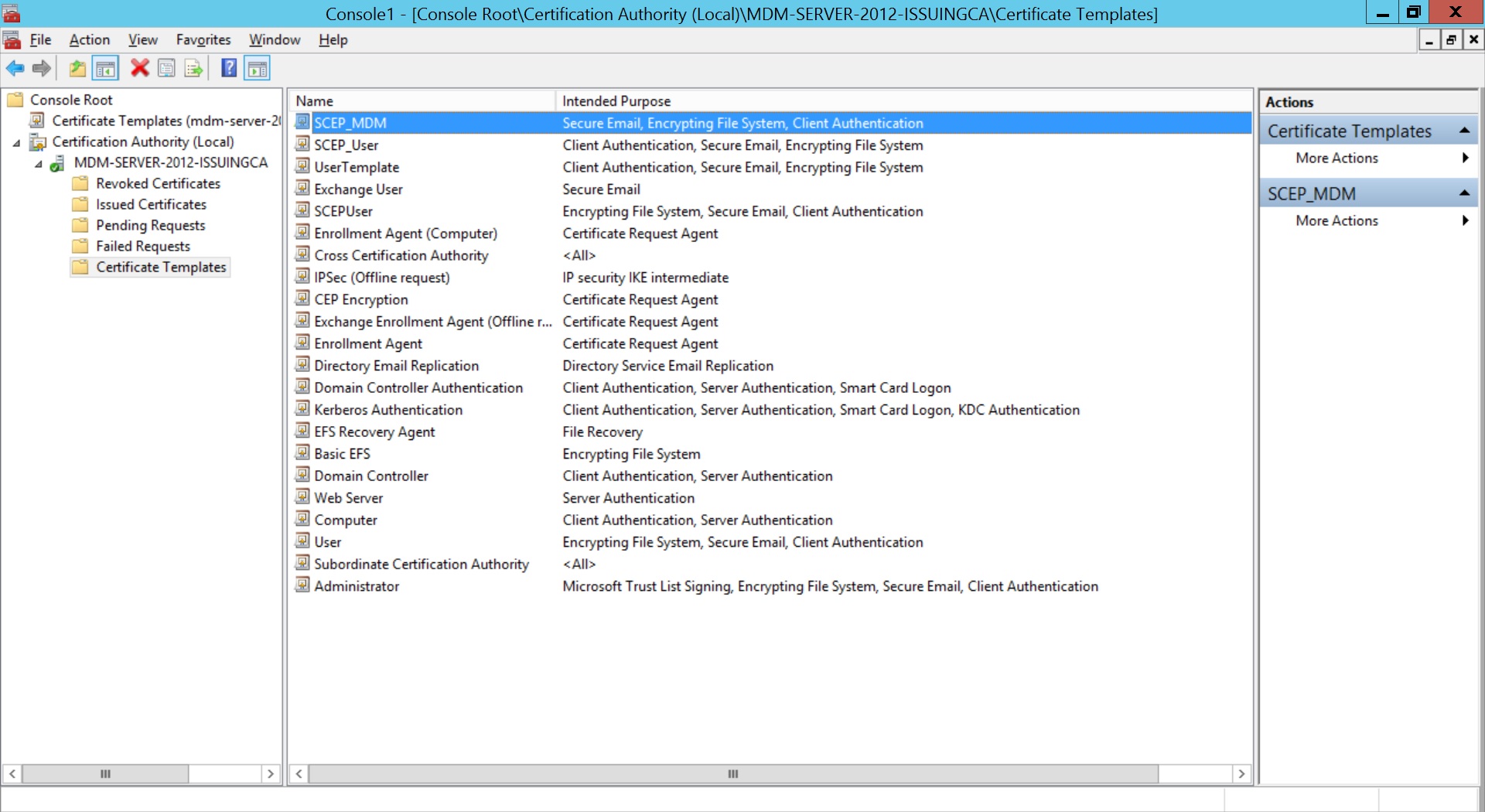
- Select the Certificate Template created before and click OK.
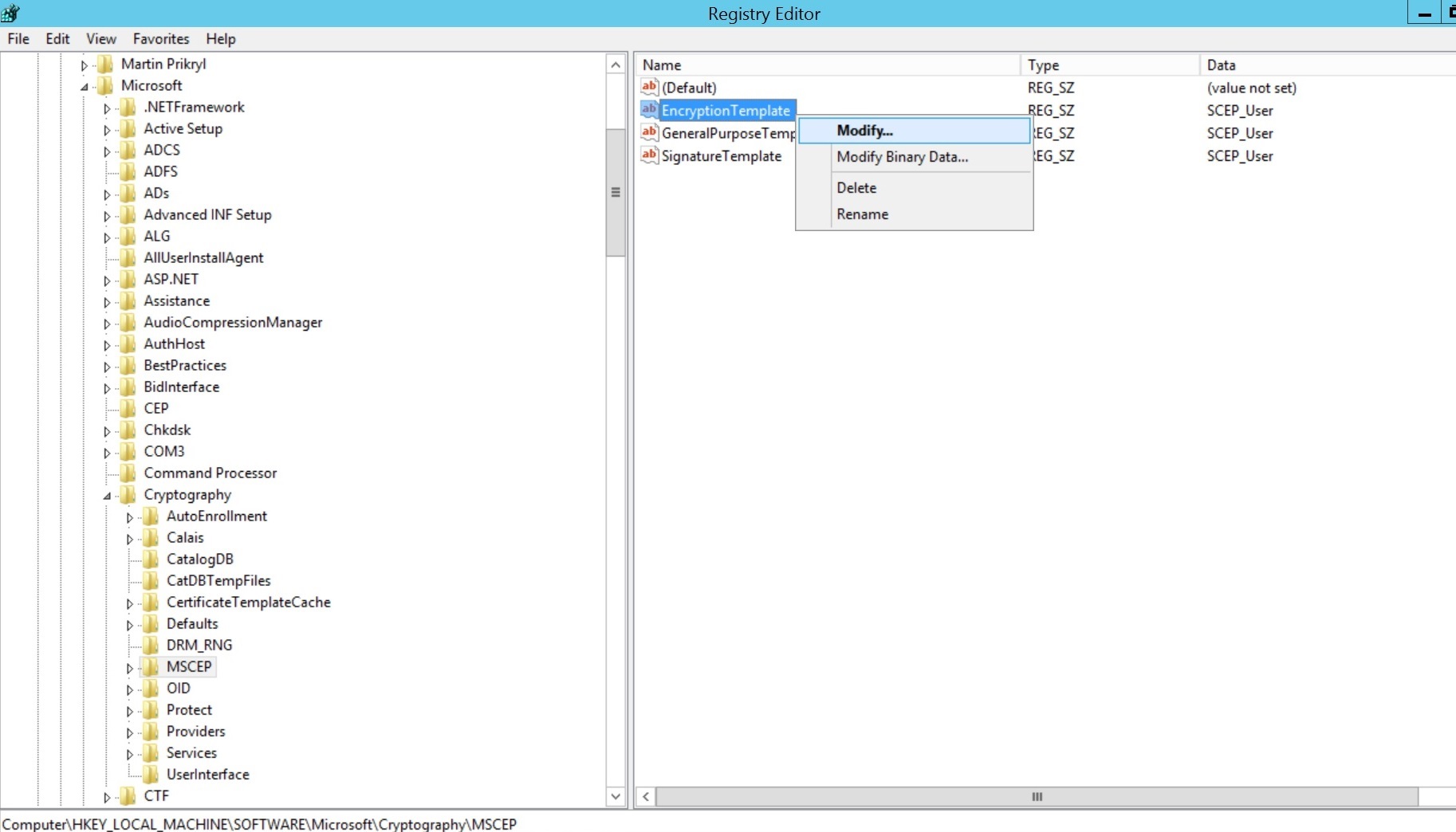
- Click on Start Menu, select Run, type regedit and click OK.
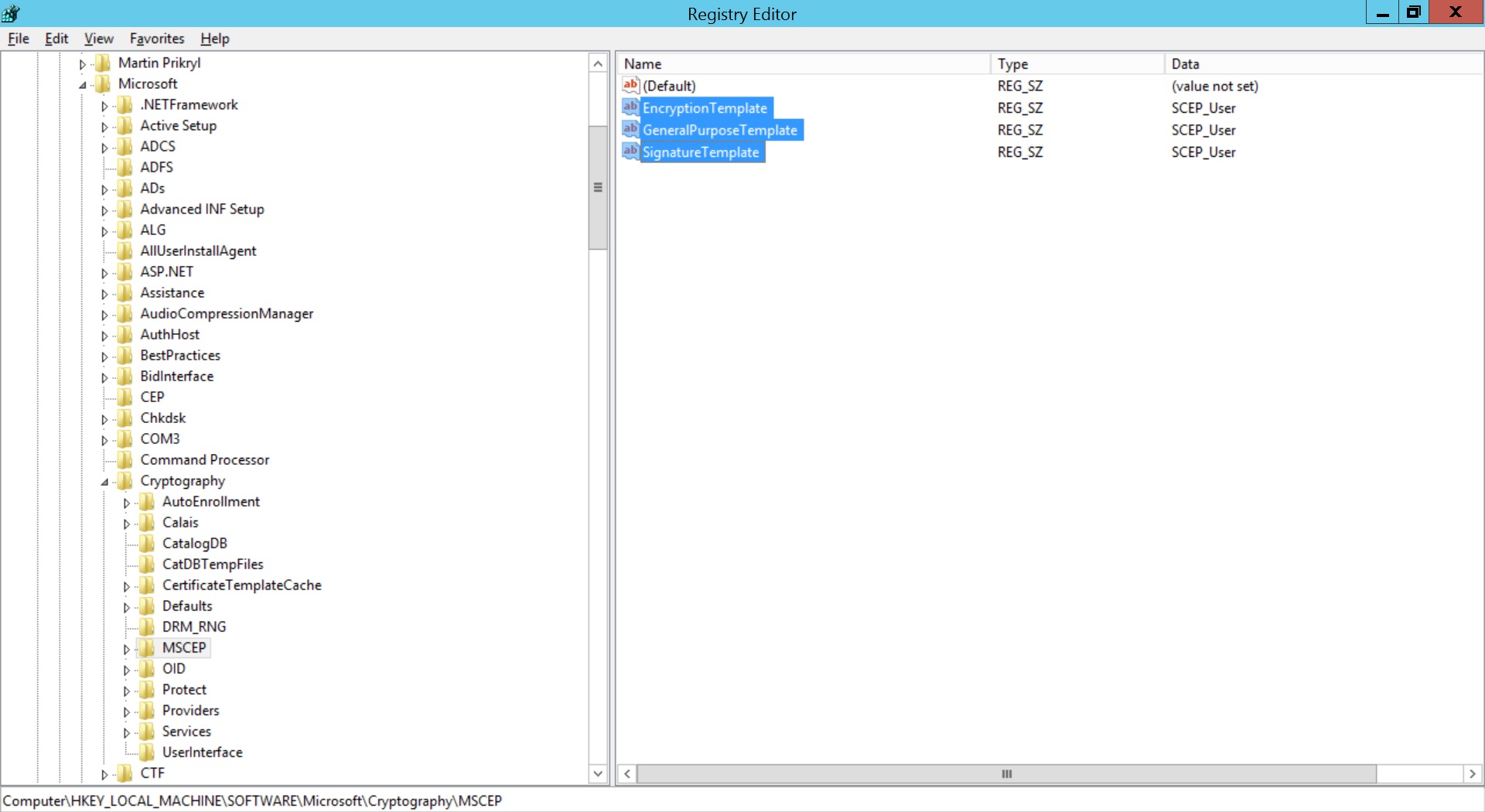
- Expand HKEY_LOCAL_MACHINE -> SOFTWARE -> Microsoft -> Cryptography -> MSCEP.
- Right-click on Encryption Template and click Modify.
- Specify the name of the created Certificate Template for Value date. Repeat the same for GeneralPurposeTemplate and SignatureTemplate. Restart the server machine once for the changes to take place
To change the default certificate template used by Microsoft NDES, windows registry values are to be changed.
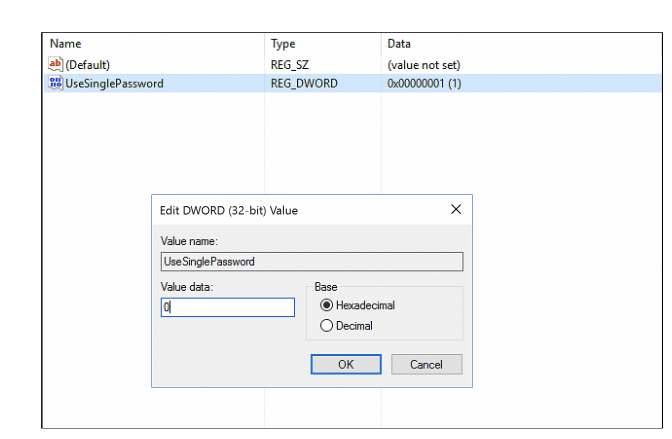
- Open regedit and expand HKEY_LOCAL_MACHINE -> SOFTWARE -> Microsoft -> Cryptography -> MSCEP -> UseSinglePassword.
- Right-click UseSinglePassword and change the value of data as 1.
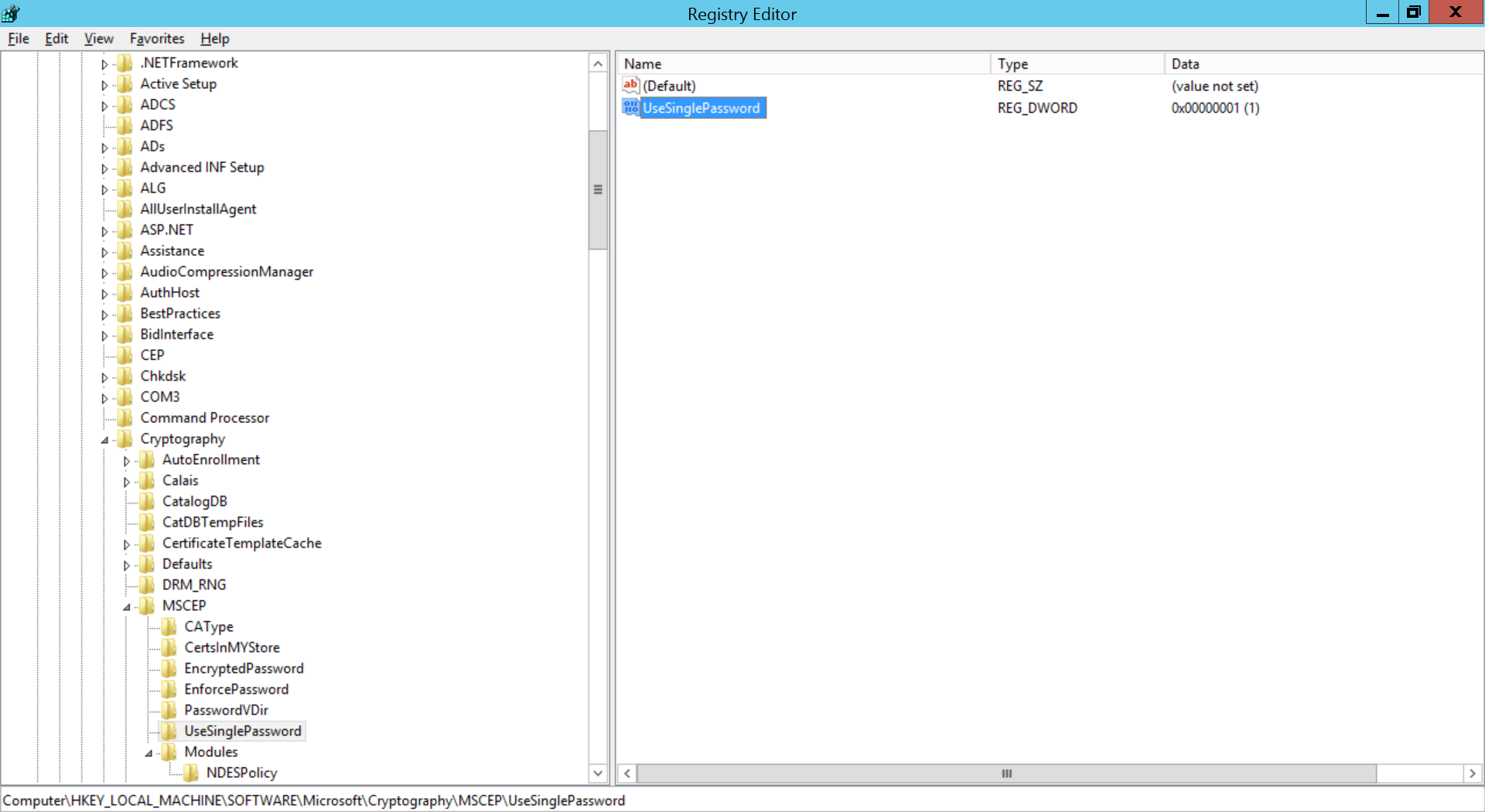
If you're using Challenge password(recommended), then registry values must be modified to prevent expiry of Challenge password.
After configuration is complete, restart the NDES Server.
Steps to increase the password cache limit
- Open the Registry Editor in NDES machine and navigate to HKEY_LOCAL_MACHINE - > SOFTWARE -> Microsoft -> Cryptography -> MSCEP -> UseSinglePassword
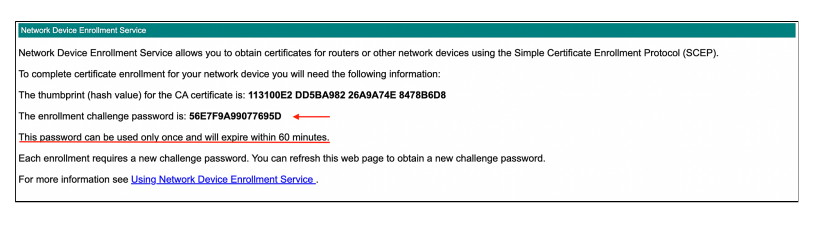
- Set the value for UseSinglePassword to 0. By configuring this, every time we hit the NDES admin URL, it will generate a unique challenge password Admin URL: https://
/certsrv/mscep_admin/mscep.dll - Restart the IIS server.
- As shown in the above screenshot, when we navigate to the Admin URL, we will get a challenge password, and upon refreshing the page, we will get another challenge password.
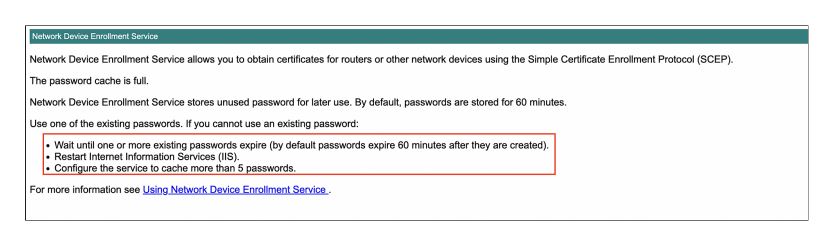
- A problem with this configuration is that NDES will only generate 5 passwords each hour.
- We can resolve this, by increasing the Password cache limit of the NDES. To do this, in the registry editor, navigate to HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\MSCEP
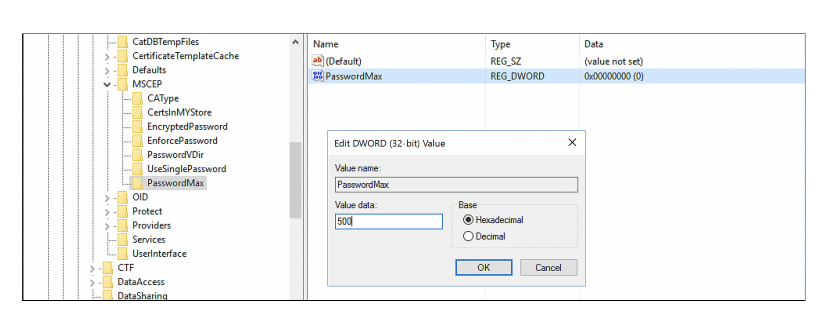
- Create a new key and provide the name as PasswordMax
- Right click on the PasswordMax key, and select New -> DWORD (32-bit) Value, provide the name as PasswordMax and provide a value according to your organization needs.
- Restart the IIS.
Configuring SCEP in MDM
- The value for Subject should be in LDAP DN format as explained here.
Follow the steps given below to configure SCEP in MDM
- On the console, navigate to Device Mgmt -> Certificates
- Click on the CA Servers tab and click on Add CA server
- Provide the following details:
| Profile Specification | Description |
|---|---|
| Server Type | Specify server type as Microsoft AD CS. |
| Certificate Authority Name | Specify the name of the Certificate Authority issuing certificates. |
| Server URL | The URL to be specified in the device to obtain certificate. Provide HTTP Server URL, if the SCEP server is within the organization network and not exposed to external networks. The certificate is requested through this URL. |
| Add CA Certificate | Upload the Certificate Authority's certificate |
Creating templates for the CA servers
For creating user-specific certificates, a template needs to be configured based on which all the certificates will be issued by the CA.
Follow the steps given below to configure the template on MDM:
- On the console, navigate to Device Mgmt -> Certificates.
- Click on Templates tab and click on Add Templates
- Select the server to which the template belongs
- Provide the following details:
| Profile Specification | Description |
|---|---|
| Certificate Template Name | Specify the certificate template name. |
| Subject | Specify the Subject DN that needs to be present in the certificate. You can use dynamic keys such as %username%, %email%, %firstname% to fetch the the corresponding details mapped to the device. For instance, you can specify C=US,O=Zylker,OU=Zylker,CN=%firstname%. |
| Subject Alternative Name Type | Specify one of the following values None, RFC 822 Name, DNS Name or Uniform Resource Identifier for the subject alternative name type |
| Subject Alternative Name Value (Can be configured only if Subject Alternative Name Type is configured) | Specify a value for subject alternative name value. The values to be entered can include DNS name, URI or email. For instance, you can use the dynamic key %email% for the subject alternative name value, email. |
| NT Principal Name | Specify the NT Principal Name used in the organization. |
| Maximum Number of Failed Attempts | Maximum number of failed validation attempts allowed to obtain the certificate from the CA. Once the maximum limit is exceeded, users will be temporarily restrcted from attempting to vaildate the user account. |
| Time interval between attempts | Time to wait before subsequent attempts to obtain the certificate |
| Challenge Type | A pre-shared secret key provided by the CA, which adds additional layer of security. If Static is chosen, the challenge password will be submitted to the SCEP server for authentication and all the devices will use the same password for authentication. If Dynamic is chosen, each device will use a unique challenge password for authentication. If None is chosen, no authentication is requested by the SCEP server and any device can receive the certificate by accessing the SCEP URL. |
| Enrollment Challenge Password (Can be configured only if Static challenge type is selected) | Provide the challenge password to be used for authentication. |
| Challenge URL (Configurable only if challenge type is set as Dynamic) | Specify the AD CS MSCEP admin endpoint URL. |
| Challenge Username (Configurable only if challenge type is set as Dynamic) | Specify the AD CS MSCEP admin username to be used. |
| Challenge Password (Configurable only if challenge type is set as Dynamic) | Specify the AD CS MSCEP admin password to be used. |
| Key Size | Specify whether the key is 1024 or 2048 bits |
| Use as Digital Signature | Enabling this option ensures the certificate can be used for Digital Signature |
| Use for Key Encipherment | Enabling this option ensures the certificate can be used for Key Encipherment |
| Certificate Auto Renewal | Enabling this option ensures the certificates are renewed automatically before it expires. |
| Certificate Automatic Renewal Before | Specify the number of days before which the the certificate must be auto-renewed. |
Creating a SCEP profile
To distribute certificates to managed devices, a SCEP profile need to associated with these devices. Follow the steps given below to create and associate the SCEP profile to devices
- Navigate to Device Mgmt -> Profiles and create either an Apple, Android or Windows profile.
- Select SCEP from the left pane.
- Select the created Certificate template.
- Click on Save and publish the profile.
It is recommended to distribute the profile to a device for testing before distributing it to your production environment. Once testing is complete, you can distribute the profile to your production environment using Groups.