Audit, Reports & Miscellaneous
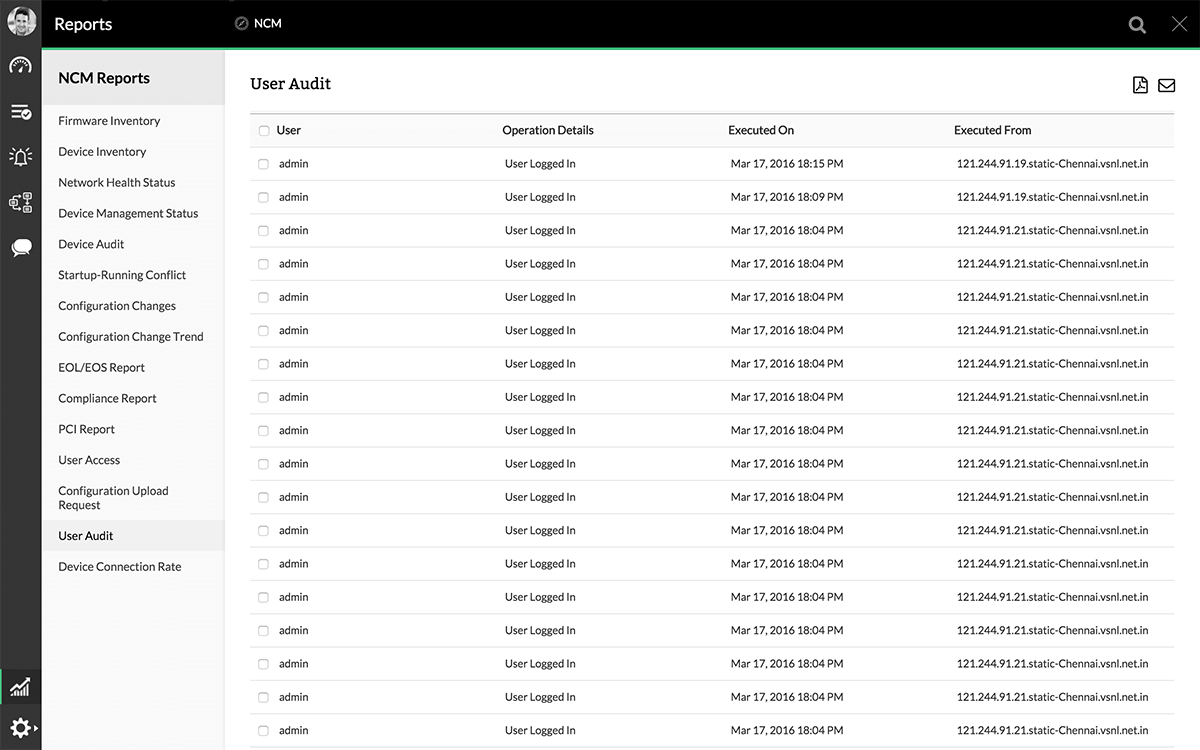
User Activity Tracking - 'who', 'what' and 'when' of configuration changes
Users perform various operations on device configuration such as backing up the configuration, uploading configuration to device, enabling real-time change detection etc., When something goes wrong due to faulty configuration change or when a security breach occurs, it is important to trace user actions to ensure accountability in the organization. To ensure this, it is essential to record the information on who invoked what operation, on what device, at what time and the result of the operation. This is done by the Audit module of Network Configuration Manager and this is termed as "Device Operation Audit".
Do you want to keep tabs on user activity? Learn how to track user activity in your network with Network Configuration Manager.
Besides, information about the various scheduled tasks executed by Network Configuration Manager along with details such as schedule name, result of execution etc., are listed by the Audit Module under "Schedule Audit".