Event logs are used to monitor the windows servers in your network. The logs help you monitor the program, security, and system events occurring in Windows devices. For example, you can identify performance issues like a process failure or security events like unauthorized login requests.
In Windows machine, there is a default event viewer that helps you to view the events in that machine. But, manually checking the events through this method is not feasible if you want to monitor an enterprise network. OpManager supports event log monitoring and helps you easily identify critical events with the help of alerts.
Prerequisite: OpManager uses WMI to fetch the details of these logs from a window device.
So please ensure to provide the user login credentials with administrative privileges to access the end device. (If you are a non-admin user (visit this KB article to know more)To monitor Windows events, you need to associate the event log monitors with the device.
Once you have ensured you have the necessary permissions, follow the steps given below:
To create an event log monitor, follow the steps given below:
Go to Settings > Monitoring > Event Log Rules
In this page, you can see the default rules supported by OpManager. They are categorized into Applications, Security, System, DNS Server, File Replication Service, and Directory Service.
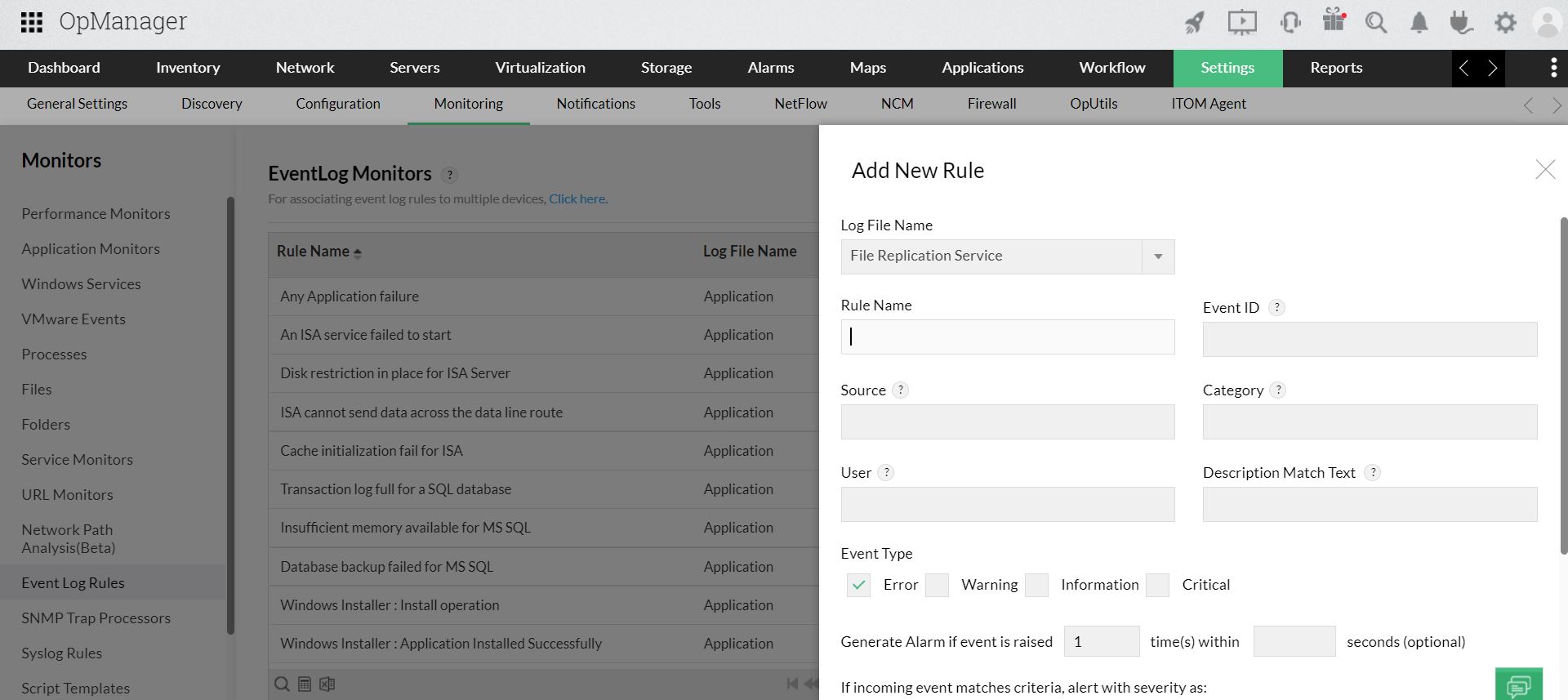
To add a new rule click on Add.
Note: Entries to all the fields except Rule Name are optional. The details you input in the fields are required to filter the event. For example, when you mention the source and event ID, all events with the given ID from the mentioned source will be monitored. In an other instance, if you mention only the category such as error, all events with error category will be monitored.
Select the Log File Name.
Type a unique Rule Name.
Enter the Event ID to be monitored. This is the unique identifier for the event logs.
Enter the event Source. This is the source that logs the event, it can be an application or a sub component of an application. For example: DesktopCentral, Microsoft Windows security
Enter the event Category. Each event source defines its own categories such as data write error, date read error and so on and will fall under one of these categories.
Type the User name to filter the event log based on the user who has logged on when the event occurred.
Choose the Event Types to filter the event logs based on its type. This will typically be one among Error, Warning, Information, Security audit success and Security audit failure.

Description Match Text : Enter the string to be compared with the log message. This will filter the events that contains this string in the log message.
You can also use Regular Expressions (RegEx) to specify the match criteria for this field. For example, consider an Eventlog description that reads "Check whether any firewall is blocking". Below are some examples of how you can form RegEx patterns for this message:
| Condition | Logic used | RegEx pattern | Actual RegEx |
|---|---|---|---|
| Contains both "Check" and "any" | AND | (?=.*XXX)(?=.*YYY) | (?=.*Check)(?=.*any) |
| Contains either "blocking" or "firewall" | OR | (XXX)|(YYY) | (blocking)|(firewall) |
| Not contains "firewall" | NOT | ^(?!.*XXX).*$ | ^(?!.*firewall).*$ |
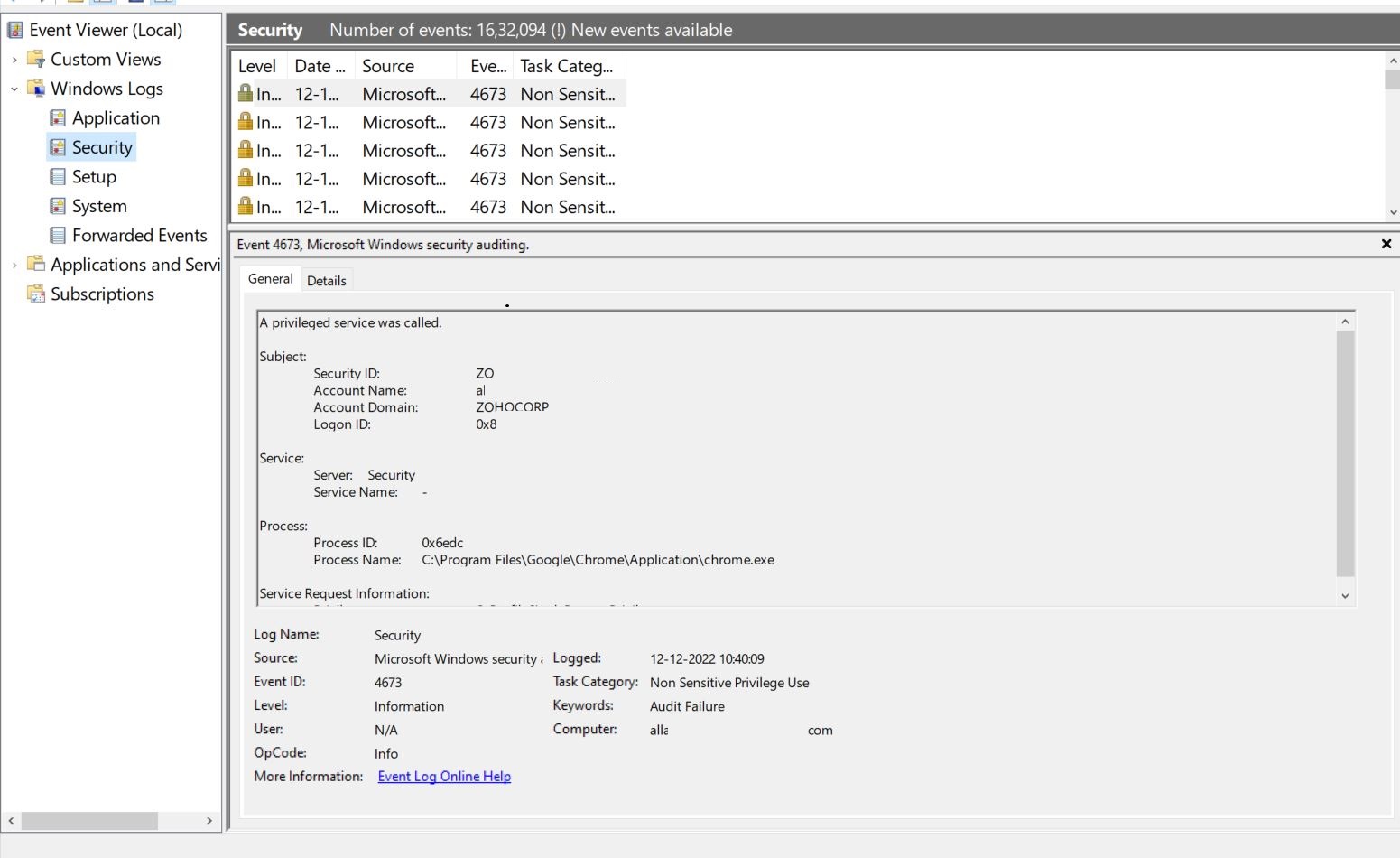
The above image shows an example of a security event. From the event viewer you can take the necessary details, specify them in OpManager and monitor the event.
You can monitor event logs under a custom category too. Some applications log the events in a new category other than the default System/Applications/Security category. You can now configure rules in OpManager to parse the events in such custom categories and trigger corresponding alerts in OpManager. Here are the steps:
Associating event log monitors to multiple devices is made simple in OpManager with the Quick Configuration Wizard option.
Applying event log rules to multiple devices is easier using the QCW, however, say if you discover new devices frequently for monitoring, then adding event log monitor to new devices would be a cumbersome task.
You can automate the process of event log rule association using the Discovery rule engine. Using this option you can create your own rule to associate event log rules to specific devices like Windows servers.
The event log rule will be applied to Windows servers whenever they are discovered in OpManager.
Thank you for your feedback!