Application Credential Injection in PAM360 Remote Connect
PAM360 supports automatic password injection for third-party thick-client applications via the Application Credential Injection feature in the PAM360 Remote Connect desktop client. The Application Credential Injection significantly improves both security and usability by eliminating the need for users to enter manually or manage complex passwords when connecting to target database servers.
With this feature, users can seamlessly launch supported applications, including DBeaver, MySQL Workbench, and the SAP GUI (saplogon.exe), to connect to database servers (MS SQL Server, MySQL, Oracle, and PostgreSQL) or SAP ERP systems without manually entering passwords or connection details. Credentials are securely fetched from PAM360 at runtime, ensuring they are never exposed to the user. This functionality is available when the target database servers or SAP systems are added as resources in PAM360 and shared with the appropriate end users.
1. Prerequisites
1.1 DBeaver and MySQL Workbench
To successfully establish session to target database servers using the Application Credential Injection feature, ensure the following requirements are met:
- The PAM360 Remote Connect application installed machine should have seamless connectivity to both the PAM360 server and the target database servers.
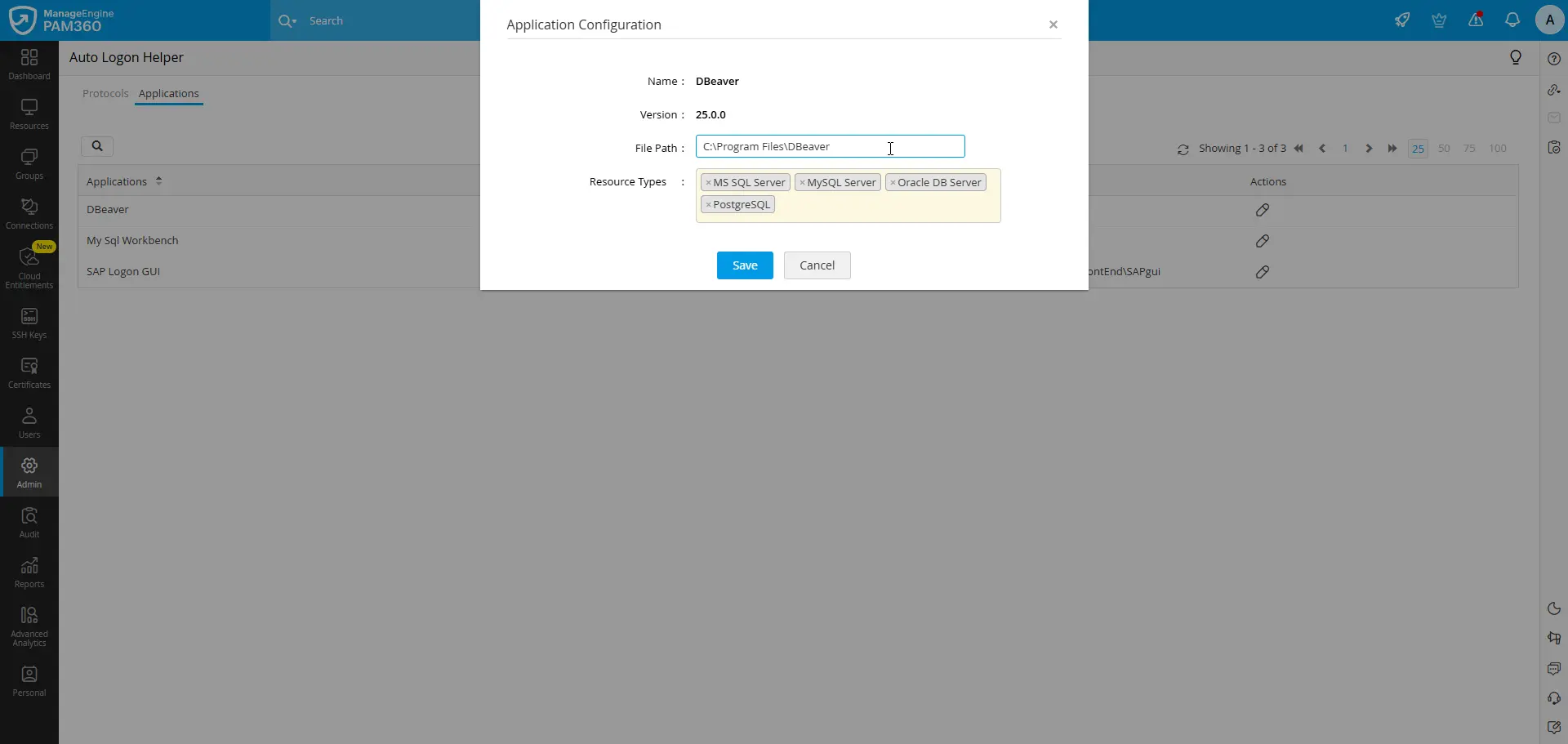
- The third-party thick-client applications, such as DBeaver (version 25.0.0 & above) and MySQL Workbench (version 8.0.40 & above), should be installed on the machines where the PAM360 Remote Connect client is running and accessible at the same directory (specified on the Applications page in PAM360) across all the installed machines as this path is used to launch and autofill passwords for remote connections. Refer to this section for details about configuring the file path for the application as needed.
- Ensure that the third-party thick-client applications are set to use English as the interface language.
- To ensure Application Credential Injection works during remote connections to target database servers, the PAM360 server should have a valid web server certificate.
- The target database servers should be added as resources in PAM360. While adding the resources, ensure the following factors:
- Details such as Username, Password, Hostname, and Port should be configured correctly.
- The Default Database field must exactly match the actual name of the target database. For Oracle database servers, the value configured as the Default Database in PAM360 should be the service name of the database, not the SID.
- Remote Login Credential should be configured for each database server in PAM360. This is essential to allow PAM360 Remote Connect to retrieve the port details for the database server from PAM360 for the autofill support during the remote connection to the database servers through thick-client applications.
- Currently, only non-SSL connections are supported when using PAM360 Remote Connect to launch thick-client applications like DBeaver for MS SQL database authentication. Ensure that the target MS SQL database does not enforce SSL or require client certificates, as these configurations are not currently supported.
- For now, the RSA public key retrieval property should be enabled to establish a connection to MySQL database servers (initial versions) using third-party thick-client applications for password autofill via PAM360 Remote Connect.
- When launching a connection to an Oracle database server using DBeaver via PAM360 Remote Connect, password autofill is currently supported only for user accounts with the role set to Normal. Therefore, ensure the role type is set to Normal before initiating the connection.
1.2 SAP GUI
To successfully establish session to the SAP GUI using the Application Credential Injection feature, ensure the following requirements are met:
- The PAM360 Remote Connect application installed machine should have seamless connectivity to the PAM360 servers.
- SAP GUI version 770 or later should be installed on the machine running the PAM360 Remote Connect client. The SAP executable should be accessible from the same directory path configured on the Applications page in PAM360. PAM360 uses this path to launch the SAP client on the user’s machine and automatically inject credentials during application sessions. For guidance on configuring the application file path, refer to the relevant section.
- Ensure that the SAP application is set to use English as the interface language.
- The SAP application should be added as resources in PAM360 with the relevant System ID, Client number, Username and Password.
2. Launching Remote Connection Using Application Credential Injection
After completing the required prerequisites, you can initiate remote connections to database servers and SAP systems using supported third-party thick-client applications directly from the PAM360 Remote Connect application. For instructions on using the Application Credential Injection with tools like DBeaver, MySQL Workbench, and the SAP GUI, refer to the corresponding help documentation.
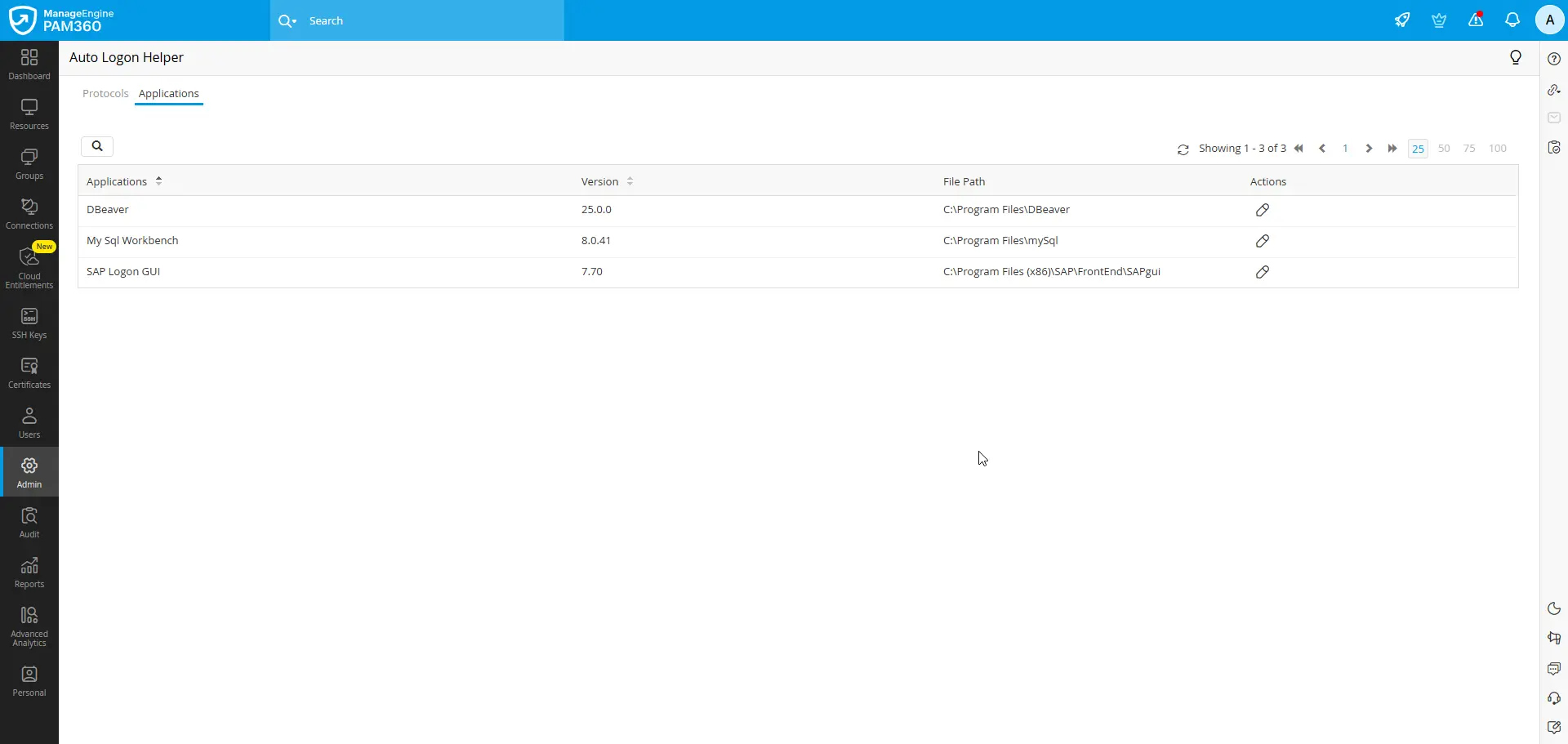
3. Modifying Application Details in PAM360
By default, PAM360 is pre-configured with the following settings for the third-party thick-client applications:
- The installation path is set to C:\Program Files\<application name> for Windows environments.
- By default, the following database resource types are selected as the supported resource types for DBeaver and MySQL Workbench application:
- MS SQL Server
- MySQL Server
- Oracle DB Server
- PostgreSQL
Caution
Application Credential Injection is supported only for MS SQL Server, MySQL Server, Oracle Database Server, and PostgreSQL database resource types. As of now, password autofill is not supported for any other custom resource types created using the default database resource types added under this configuration.
- By default, SAP resource type is selected as the supported resource types for SAP logon application.
To update the default configuration for any third-party thick-client application, go to Admin >> Privileged Session >> Auto Logon Helper >> Applications in the PAM360 web interface, open the Edit Application Details for the required application, and adjust the installation path or resource types as needed.