Custom Truststore
AssetExplorer adopts custom truststore to support untrusted SSL certificates and self-signed certificates.
Earlier, whenever AssetExplorer remote server tries to connect with ServiceDesk Plus/AssetExplorer central server, the authenticity of the server will be validated using the certificate stored in the default truststore (cacerts) and if the certificate is not authorized, the connection will not be established. Now with custom truststore, if the certificate is not authorized, the administrator can proceed to trust the certificate and establish connection.
How Does Custom Truststore Work
While connecting AssetExplorer remote server with ServiceDesk Plus/AssetExplorer central server, the application triggers a warning as shown in the below screenshot if the certificate is not authorized.
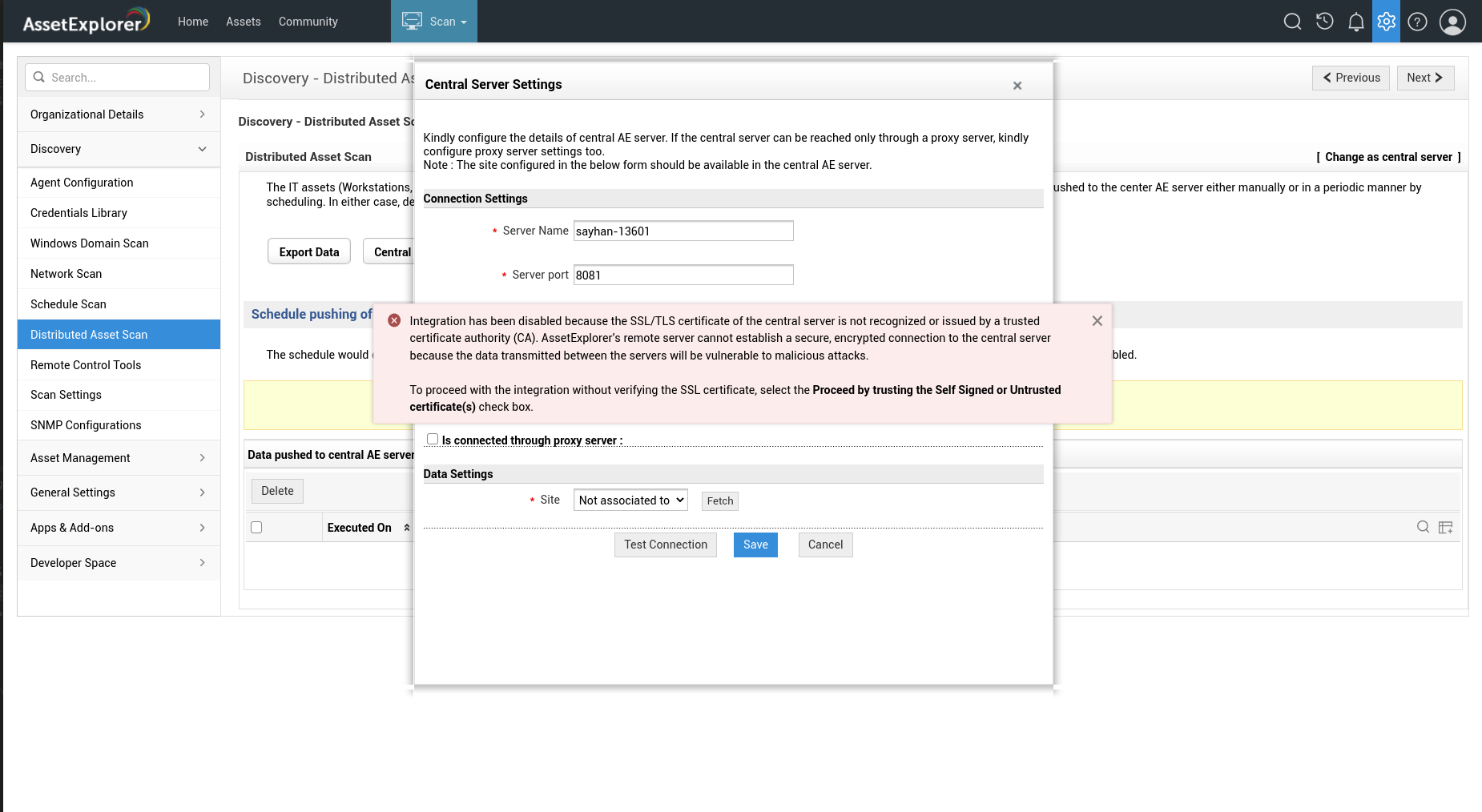
-
The administrator can proceed to trust the certificate. Then, AssetExplorer remote server will create a custom truststore and store the security certificate provided by the central server.
-
After storing the certificate in the custom truststore, the authenticity of the central server is verified and connection is established.
connection failure.
