- Related Products
- Log360
- AD360
- ADManager Plus
- ADAudit Plus
- ADSelfService Plus
- Exchange Reporter Plus
 Click here to expand
Click here to expand
Correlation is the process of identifying a sequence of multiple events, across one or more devices, which are all related, and form a single large incident. The main reason correlation is so useful is because, in many cases, the individual events may not seem suspicious on their own, but when taken in relation to the other events, a larger picture emerges which points to a potential security incident.
For instance, the two events "employee logs on to Device A" and "employee logs on to Device B" seem perfectly normal.
However, "same employee logs on to two different devices (Device A and Device B) at almost the same time" may indicate a possible account sharing incident.
A correlation rule is a pattern or a template used to relate multiple logs and identify a security incident. The rule specifies a series of events that make up a larger incident, the time window between events, and specific conditions if any. The following illustrates the various parameters that can be specified in a correlation rule:
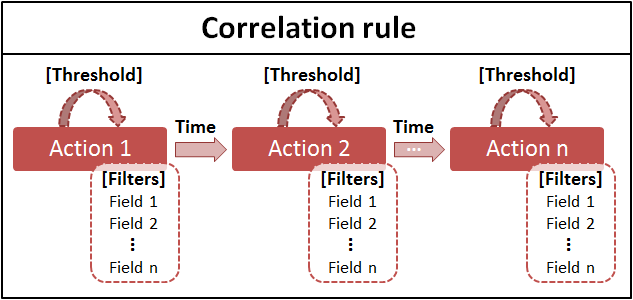
For more information on constructing a correlation rule using these parameters, see Constructing custom correlation rules.
A brute force attack occurs when an attacker tries to gain access to a device in your network, by trying several logon credentials until one succeeds. It is characterized by several failed logons on a device, followed by a successful logon:
General pattern: Failed logon -> Failed logon -> Failed logon -> (...) -> Successful logon (all within a few minutes, to the same device)
Specific pattern: At least 10 failed logons to a single device within 2 minutes -> (within the next 1 minute) -> Successful logon to the same device
The rule can thus be configured as below:
Action 1: Failed logon - an employee fails to log on to a network device.
Time window between Action 1 & Action 2: 1 minute
Action 2: Successful logon - an employee logs on to a network device.
To know more about correlation, check out the following pages:
A series of application crashes on a device over a short time-frame may point to a faulty device. Further, this check should not be applied to a specific device named "Device-1234" as it is used for application crash testing purposes and may generate too many false positives.
General action flow: Application crash -> Application crash -> (...) -> Application crash (all within few hours on a single device, not applicable to Device-1234)
Specific action flow: At least 5 application crashes on a single device within 180 minutes (except for Device-1234)
The rule can thus be configured as below:
Action 1: Application crash - an application crashes on a Windows device.
A ransomware attack typically progresses with a newly started process modifying several files on a network devices (in order to encrypt them). It can be identified with a process being started, shortly followed by multiple file modifications.
General action flow: Process started -> File modified -> File modified -> (...) -> File modified (all within a few minutes, on the same device)
Specific action flow: Process started -> (within the next 5 minutes) -> At least 15 file modifications on the same device, by the same process
The rule can thus be configured as below:
Action 1: Windows Process started - a process is started on Windows.
Time window between Action 1 & Action 2: 5 minutes
Action 2: File modified - a file is modified on a Windows device.
Copyright © 2020, ZOHO Corp. All Rights Reserved.