- Related Products
- Log360
- AD360
- ADManager Plus
- ADAudit Plus
- ADSelfService Plus
- Exchange Reporter Plus
 Click here to expand
Click here to expand
EventLog Analyzer's user interface tabs help you navigate to different sections of the product. The tabs include:
The Dashboard tab contains multiple dashboards that give you insights into important network activities. The below dashboards are present by default when you click on the Dashboard tab:
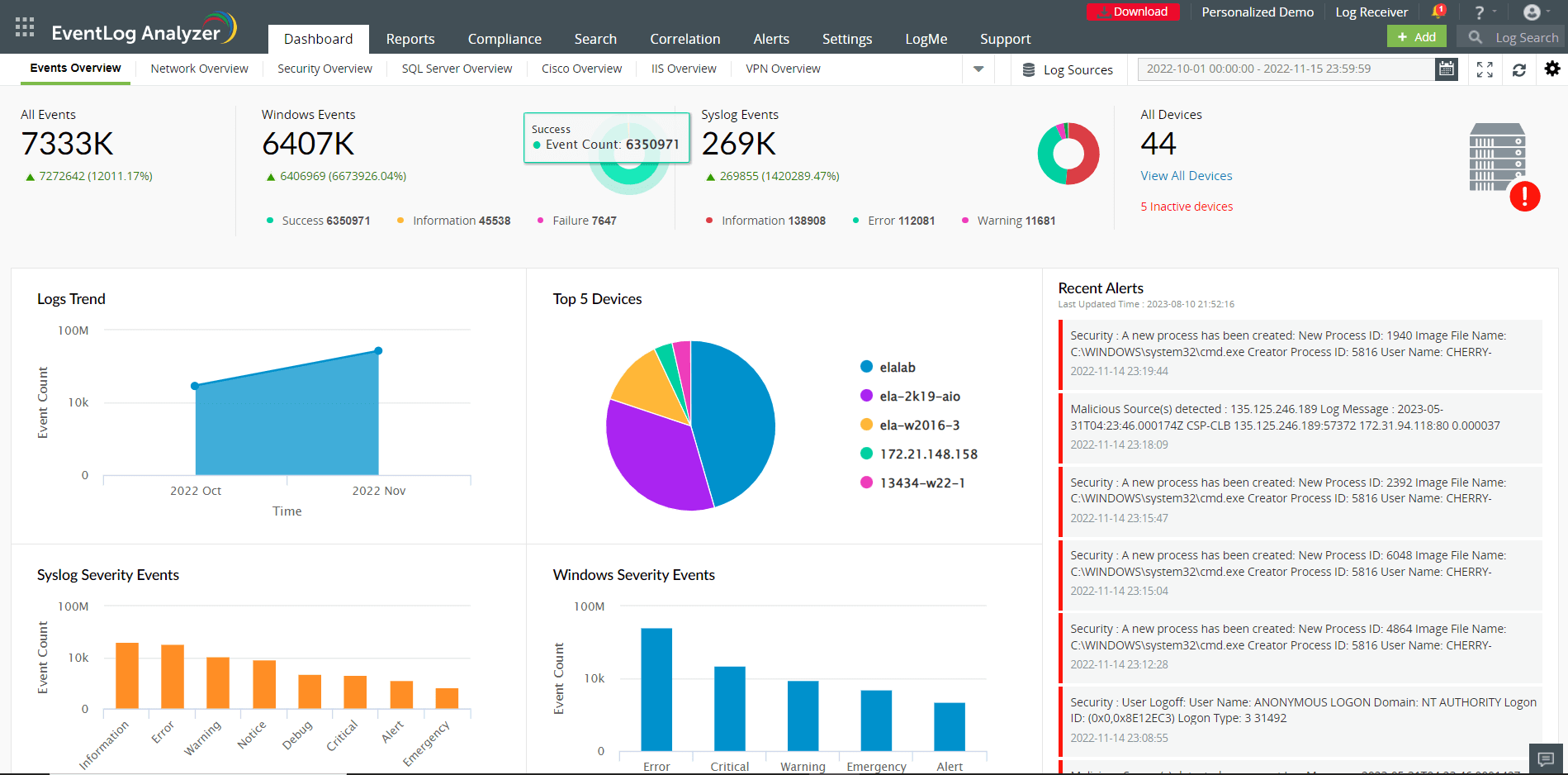
This tab presents a high-level overview of security events by generating graphical reports such as Logs Trend, Syslog Severity Events, Windows Severity Events, and Recent Alerts. These reports are generated for events that occur in a specific time frame (which can be customized). Hovering your mouse pointer over the charts or graphs will give you information about the Event Count of a particular device, its IP address, and the Severity of the event (Information, Notice, Debug, Warning, Alert, Error, Critical, and Emergency).
This tab gives you information about network traffic in your environment. It provides details on the traffic trend, allowed and denied network connections, and more to help you track events of interest.
The security overview dashboard consolidates events from network devices such as IDS/IPS, endpoint security solutions, vulnerability scanners, and other threat detection solutions. This dashboard contains reports that help security teams keep tabs on crucial security events such as vulnerabilities and threats. It also has an interactive widget on IDS/IPS attacks, which helps you identify the type of attack, number of attack attempts, and the time when the attack happened.
The dashboard also contains the Alerts Count Overview widget that displays the number of alerts triggered in a given time frame.
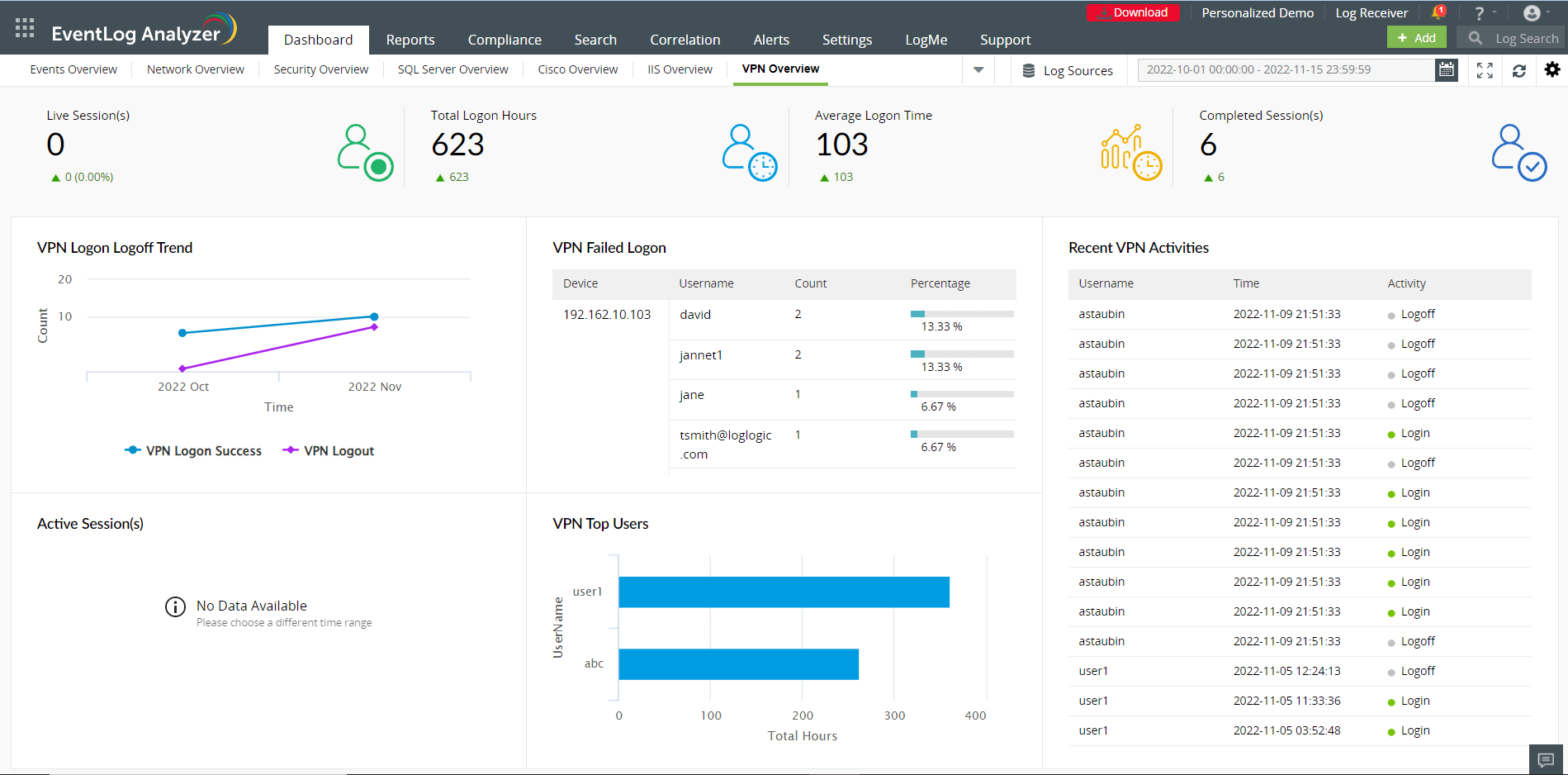
You can customize the Dashboard tab to include the VPN Overview tab by navigating to Settings → Add Tab → VPN Overview. EventLog Analyzer monitors VPN session activities and generates reports to help you visualize events of interest. The VPN Overview dashboard will give you insights on VPN user and session activities by displaying widgets such as Live Sessions Count, Total Logon Hours, Average Login Time, Closed Sessions, and Top Users and Status. You can also customize the VPN dashboard by adding and reordering widgets by navigating to Settings → Add Widgets and Settings → Reorder Widgets respectively.
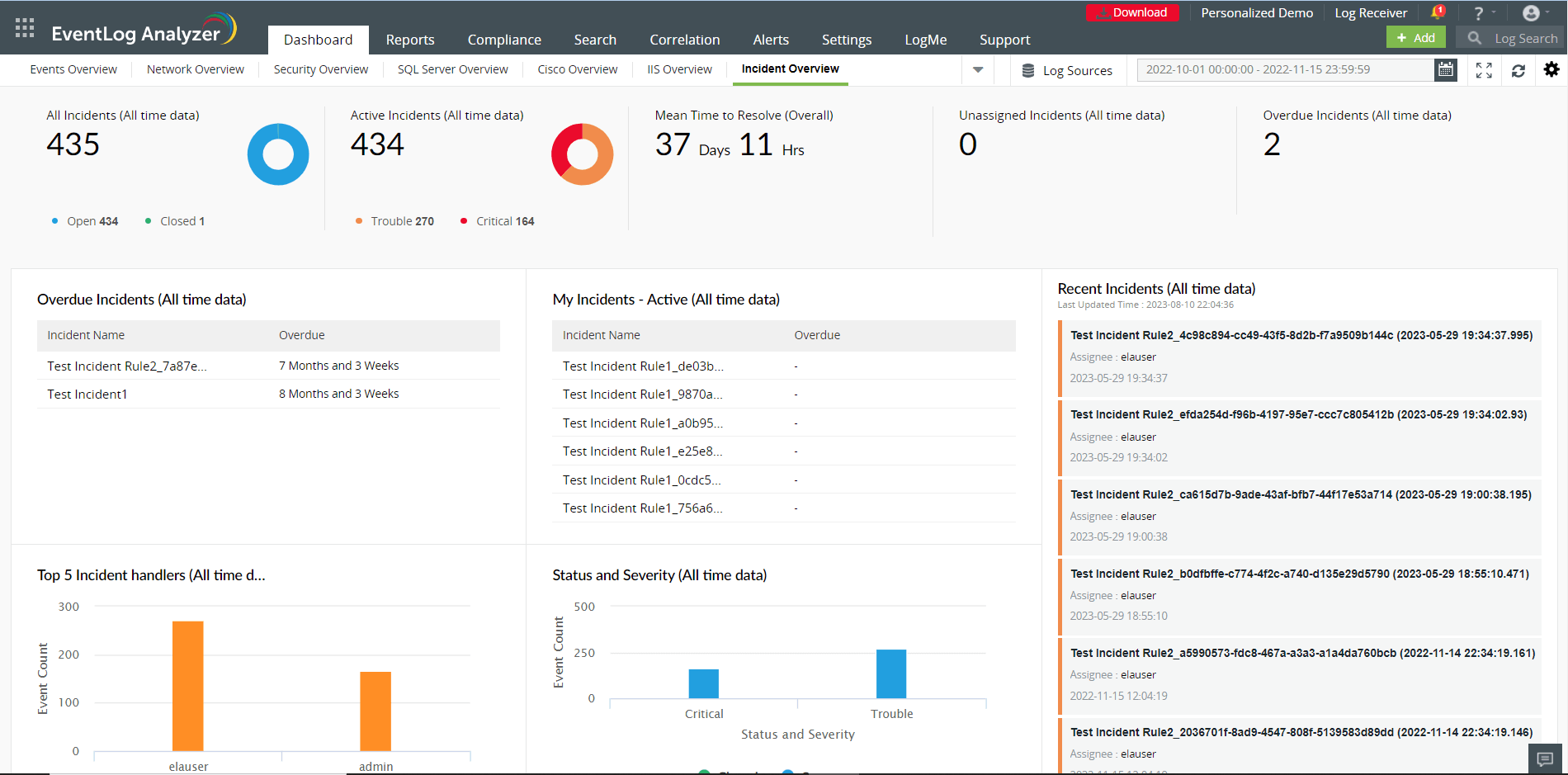
This tab helps you effortlessly manage the security incidents detected. The dashboard gives you the count of all, active, unassigned and overdue incidents. It also provides the mean time to resolve. The dashboard provides insights such as:
The Dashboard tab also contains the Log Sources, date and time selection, and settings icons.
When you click on the Log Sources tab, three tabs are displayed:
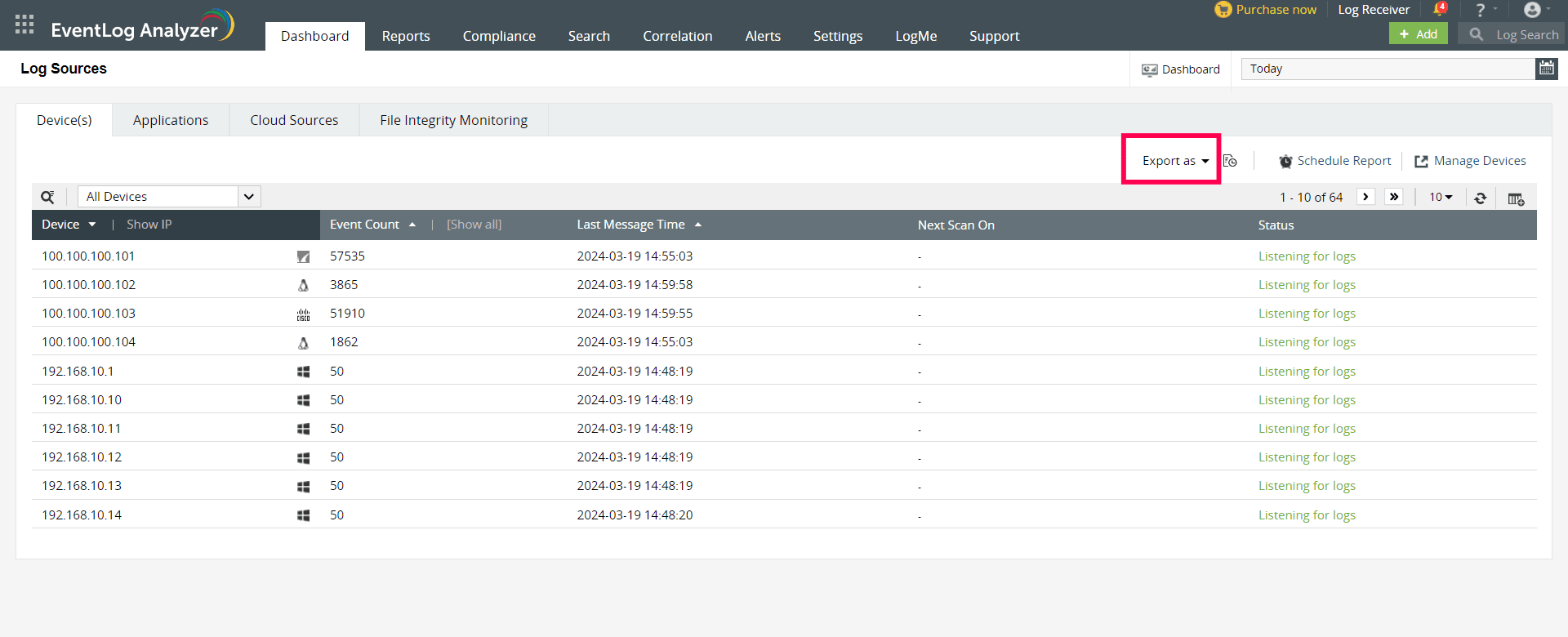
The Devices section displays the entire list of systems (Windows, Linux, IBM AS/400, HP-UX, etc.) and devices (routers, switches, etc.), from which EventLog Analyzer is collecting logs. The device list displayed is categorized based on the Device group selected from the drop-down list (default: All Groups). You can add a new device (+Device), or add and schedule new reports (+Schedule) from this section. You can search for a particular device based on its IP Address or Device Name, delete a device or set of devices, and disable/enable log collection from a particular device or set of devices.
The device list table displays details like device type, event summary (error, warning, failure, others), connection status of the device, time when the last log message was fetched, and device group to which the device belongs. Moving the mouse over any device brings up some options:
You can even customize the columns you would like to display in the device table by clicking the column selector icon or increase the number of devices that are displayed per page (from a minimum of 5 devices per page to a maximum of 200 devices per page). Using the drop down menu, you can list out only the Active devices or Enabled devices and have the option to exclude synced devices from Active Directory Audit Plus.
EventLog Analyzer lets you schedule report generation, export, and redistribution over email.
You can also export the reports in PDF or CSV format with the Export as option. These generated reports will include device details such as the display name, IP address, total count, last message time, next scan time, and device status.
The Applications section provides an overview pie-chart (which can be drilled down to raw log information) and lists the devices from which application logs for IIS W3C Web Servers, IIS W3C FTP Servers, MS SQL Servers, Oracle Live Audit, DHCP Windows/Linux Servers, Apache Web Servers or Print Servers, have been received or imported into EventLog Analyzer. The device list displayed is categorized based on Application Type selected from the drop-down list. Applications logs can be imported into EventLog Analyzer by selecting +Import from the Actions drop-down list.
The application device list displays details like device name, application type, total events, recent records, time imported, start time and end time. Click on the device name or the corresponding section in the pie chart to get the complete overview of the application event data, and generate corresponding reports. You can even customize the columns you would like to display in the application device table by clicking the column selector icon.
The File Integrity Monitoring dashboard gives information about changes made to files and folders of Windows, Linux, and Unix machines. It tabulates and reports on the files and folders created, deleted, modified, and renamed. It also displays changes made to file and folder permissions.
At the top of this dashboard, you can find the Manage File Integrity Monitoring tab which allows you to add, delete, and manage devices for File Integrity Monitoring. The FIM Alert tab allows you to configure alerts for anomalous file and folder modifications. The FIM Scheduled Reports tab helps you view and export scheduled reports.
You can generate and view all the audit reports for the required time frame using the date and time box provided.
The settings icon displays multiple options to customize all dashboards by adding, managing, and ordering the widgets and tabs that are displayed. You can also refresh the changes made to the time frame in the product using the Refresh Interval option.
This tab displays a dashboard that contains reports for all events taking place in your network. At the top left corner, you can find a drop-down menu that allows you to choose and view reports based on Devices, Applications, File Monitoring, Threats, Vulnerability, and Virtual Machines. You can also view Custom Reports, User Based Reports, and Top and Trend reports by clicking on the required option from this drop-down menu. The Export As drop-down menu enables you to export reports in either the CSV or PDF formats. You can schedule reports by clicking on the +Add option present in the Schedule Reports tab.
On the left pane, you can find multiple pre-defined reports that are automatically generated when log sources are added to EventLog Analyzer. You can also create custom reports by clicking on the Manage Reports tab present at the lower-left corner of the screen. The Scheduled Reports tab allows you to view existing scheduled reports and export them as and when needed.
The Compliance tab provides the set of canned reports as required by various compliance policies, namely, FISMA, PCI-DSS, SOX, HIPAA, GLBA, GPG, and ISO 27001:2013. The +Add option allows you to create and select the reports required for a new compliance policy of your choice. The Edit option allows you to customize the reports available under each compliance policy.
The Search tab provides two options to search the raw logs: Basic Search or Advanced Search. The search result is displayed in the lower half of the page and the final search result can be saved as a report (in PDF or CSV format) and can also be scheduled to be generated at predefined intervals and be automatically mailed to a set of configured users.
You can use Basic search if you are interested in manually constructing the search query. Here you can use phrase search, Boolean search, grouped search, and wild-card search to build your search query. You can use Advanced search to interactively build complex search queries easily with field value pairs and relational operators. New fields can be extracted from the search result and regular expression (regex) patterns can be constructed to easily identify, parse and index these fields in new logs received by EventLog Analyzer.
The Correlation engine analyzes logs collected from different parts of the network and generates alerts for suspicious patterns of events. The dashboard, by default, displays the report on Recent Incidents. You can create and modify correlation rules by clicking on the Manage Rules tab present in the dashboard.
This tab displays the number of Active Alerts in the dashboard along with their severities. You can view tabulated information about the alerts, their time of generation, the status, and their corresponding response workflow (if configured) in the dashboard.
This section allows you to configure EventLog Analyzer as per your requirements. It has three sub-sections as given below:
This section allows you to Manage Devices, Device Groups, Application Sources, Import Log Data, Threat Sources, File Integrity Monitoring, Vulnerability Data, FIM Templates, and vCenter. You can also configure threat management and log forwarding from this section.
This section allows you to perform various administrative activities by managing Alert Profiles, Archives, Technicians and Roles, DB Retention Settings, Log Collection Filters, Working Hour Settings, Product Settings, Log Collection Failure Alerts, Dashboard profiles, Privacy Settings, Logon Settings, Domain and Workgroups, Report Profiles, Resource Grouping, Custom Log Parsers, Tags, and Log360 Cloud platform.
This section can allow you to configure various settings including Notification Settings, System Diagnostics, Database Access, Re-branding, NT Service, Connection Settings, and Listener Ports.
This tab allows you to easily add log sources from Devices and Applications. It also has the provision to let you import logs from other sources. You can add Alert Profiles, Log Filters and create custom Reports from this tab.
Copyright © 2020, ZOHO Corp. All Rights Reserved.