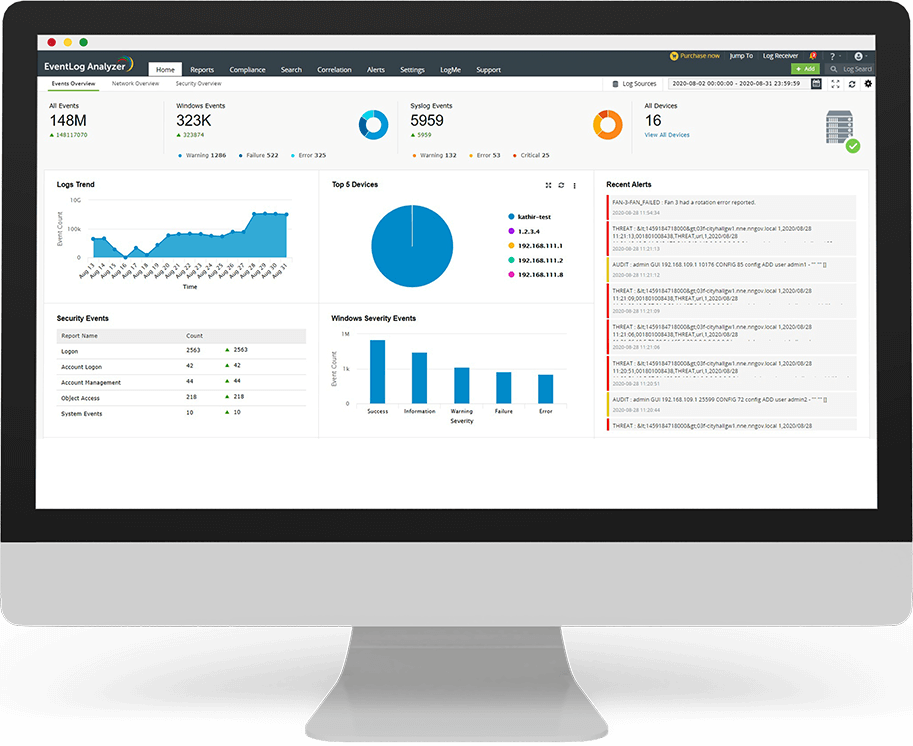
EventLog Analyzer jipprovdi maniġment tal-logs fl-istadji kollha, b’metodu ta’ ġbir tal-logs b’aġent u mingħajr aġent, analiżi ta’ logs personalizzati, analiżi ta’ log kompluta b’rapporti u twissijiet, magna tat-tiftix tal-logs b’saħħitha u għażliet flessibbli tal-arkivjar ta’ logs.
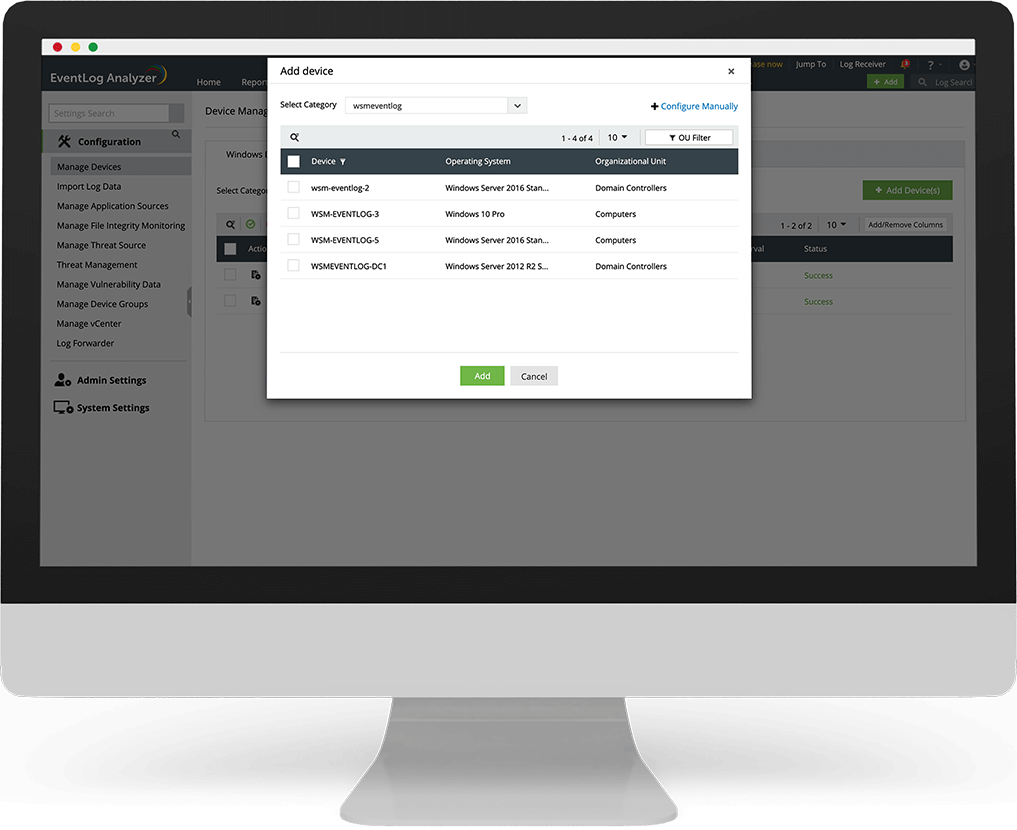
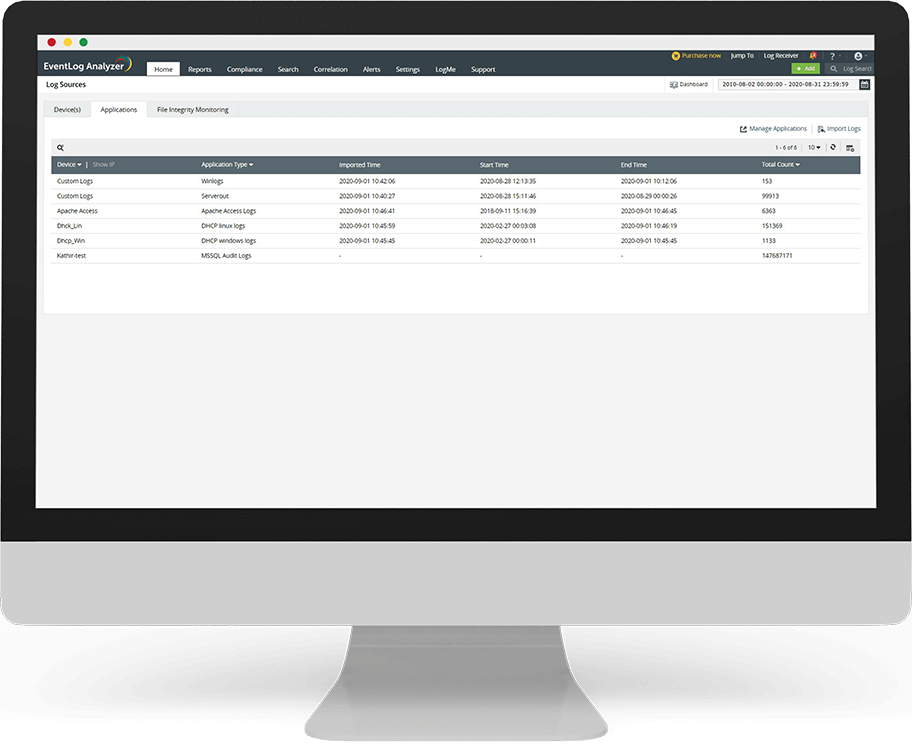
EventLog Analyzer jippermettilek tivverifika s-servers tal-applikazzjonijiet kritiċi kollha tiegħek. B’rapporti definiti minn qabel għall-applikazzjonijiet elenkati hawn, is-soluzzjoni tippermettilek timmonitorja applikazzjonijiet personalizzati. L-analizzatur tal-log personalizzat b’saħħtu tiegħu jippermettilek tanalizza u tivvalida faċilment formati ta’ logs personalizzati.
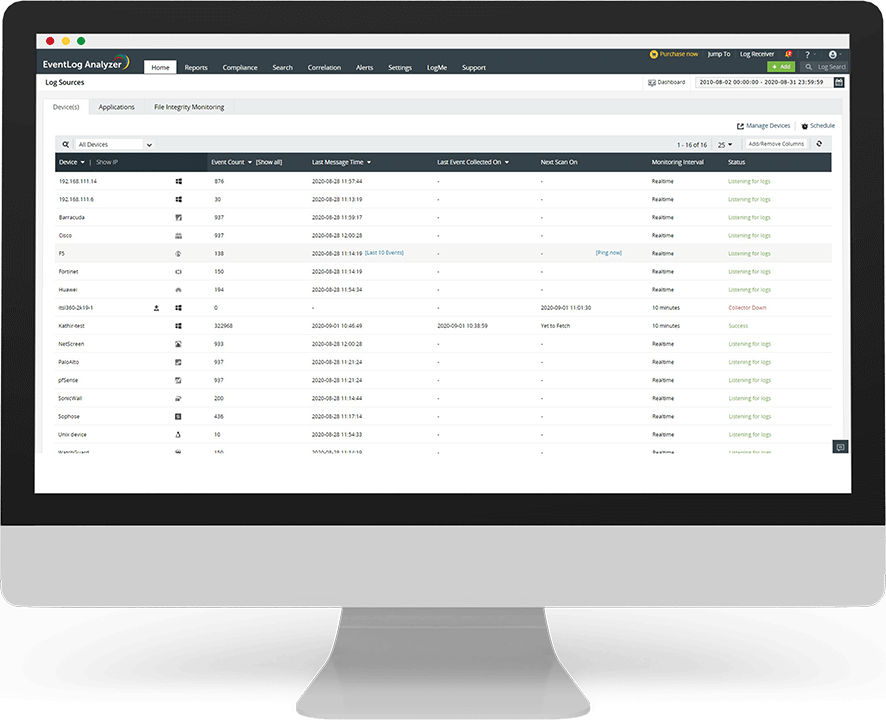
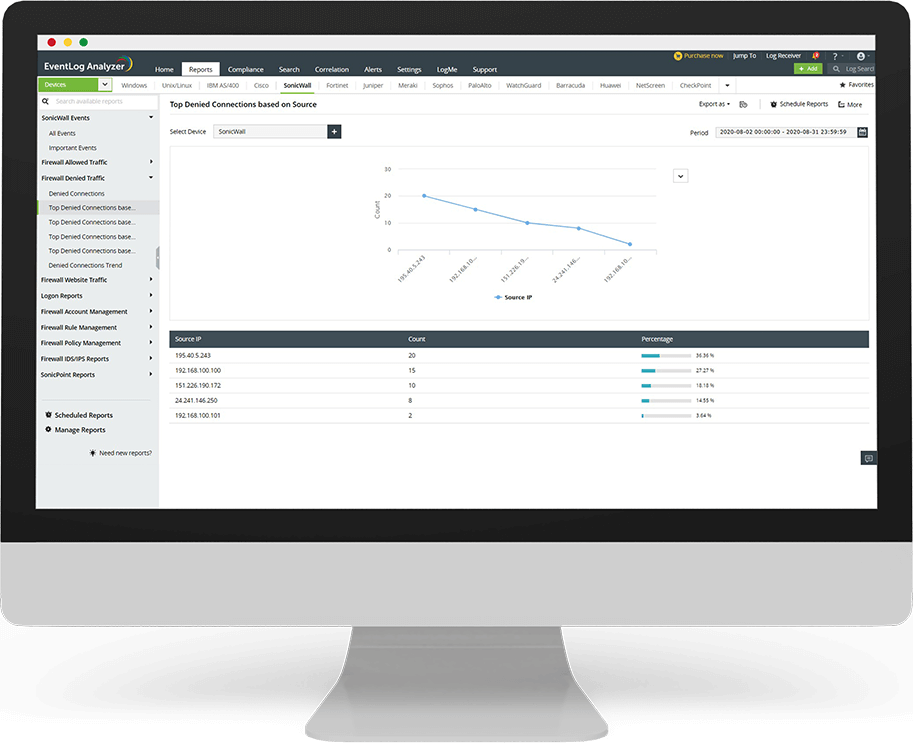
EventLog Analyzer jimmonitorja t-tagħmir importanti kollu tan-netwerk tiegħek bħall-fajerwols, routers u swiċċijiet tiegħek. Is-soluzzjoni tipprovdi rapporti definiti minn qabel għar-routers u s-swiċċijiet tiegħek ta’ Cisco, kif ukoll fajerwols minn Cisco, SonicWall, Palo Alto Networks, Juniper, Fortinet, NetScreen, Sophos, Check Point, WatchGuard, u Barracuda.
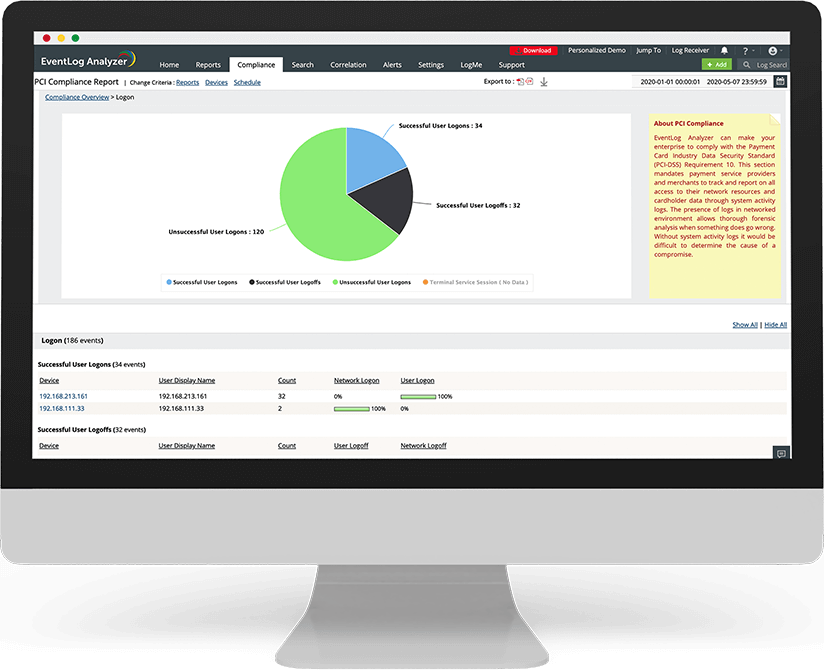
EventLog Analyzer enables you to comply with ease with a variety of regulatory policies, namely PCI DSS, ISO 27001, GLBA, SOX, FISMA, HIPAA, and the newly created GDPR policy. The solution further allows for future needs by enabling you to create custom compliance reports for new compliance policies.
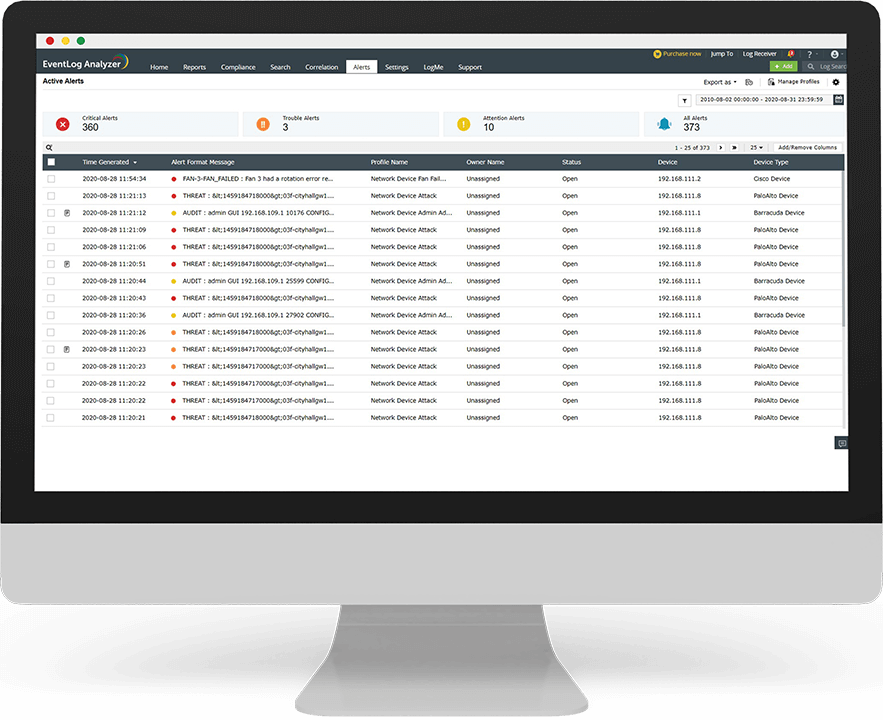
With comprehensive log management combined with extensive security features, EventLog Analyzer is a perfect SIEM platform for your network. Security features such as log forensics, threat intelligence, external threat mitigation with auditing of vulnerability scanners and threat applications, make the solution an ideal choice to secure your network and safeguard it against unwanted breach attempts and critical data theft.
EventLog Analyzer's reporting console is highly intuitive, with hundreds of predefined reports to meet all your auditing needs, which can be customized, scheduled, and distributed as you require. The reports comprehensively cover the network, including Windows, Unix/Linux, IBM AS/400, cloud platforms, vulnerability management systems, and your critical files and folders.