
- Schedule demo
- Get quote
-
Download
Log File Reader Tool for Windows, Linux, and Cloud Environments
Analyze your log data with intuitive dashboards and
pre-built reports
*Fully functional 30-day free trial. No credit card required.
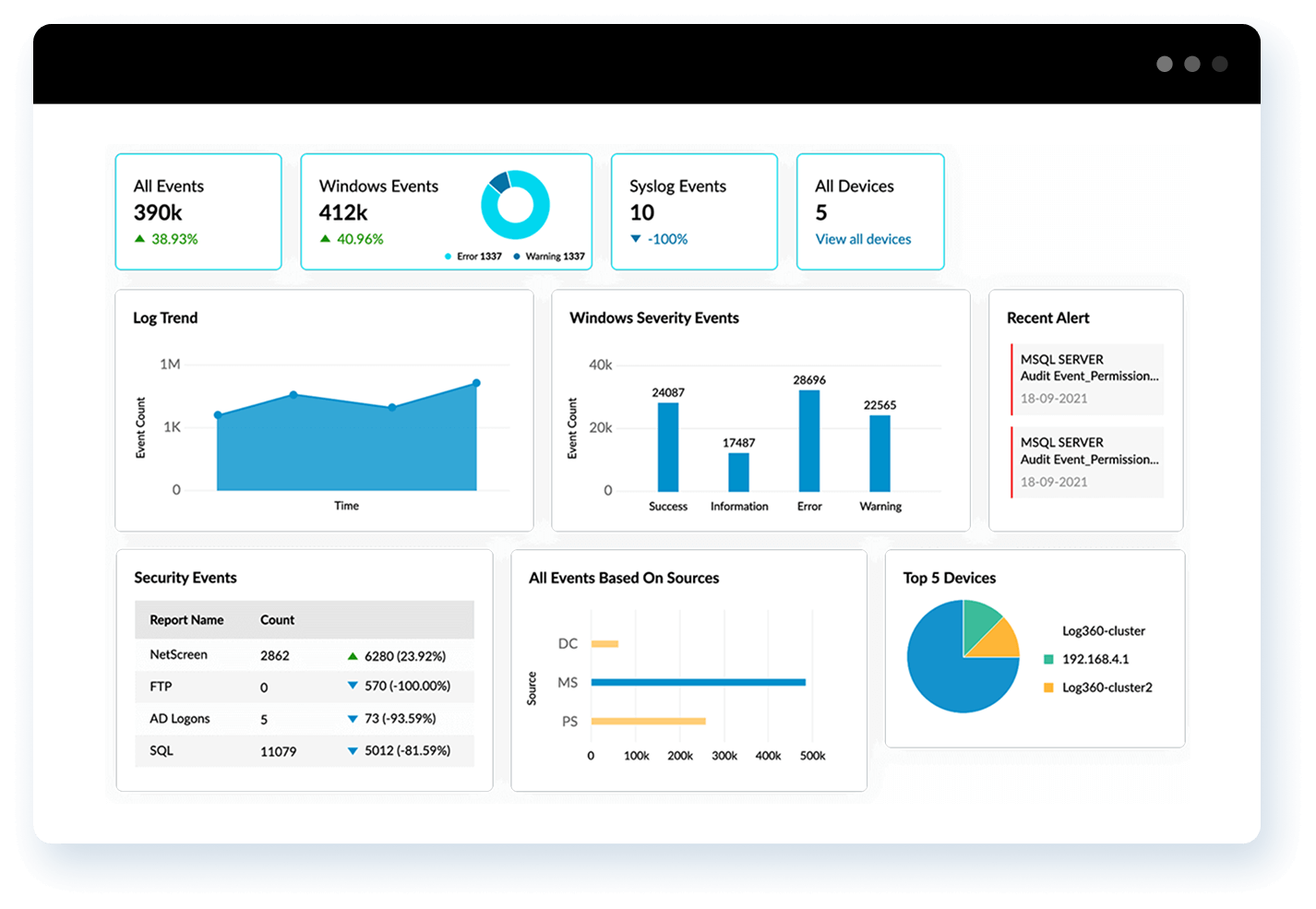

Analyze your log data with intuitive dashboards and
pre-built reports
*Fully functional 30-day free trial. No credit card required.

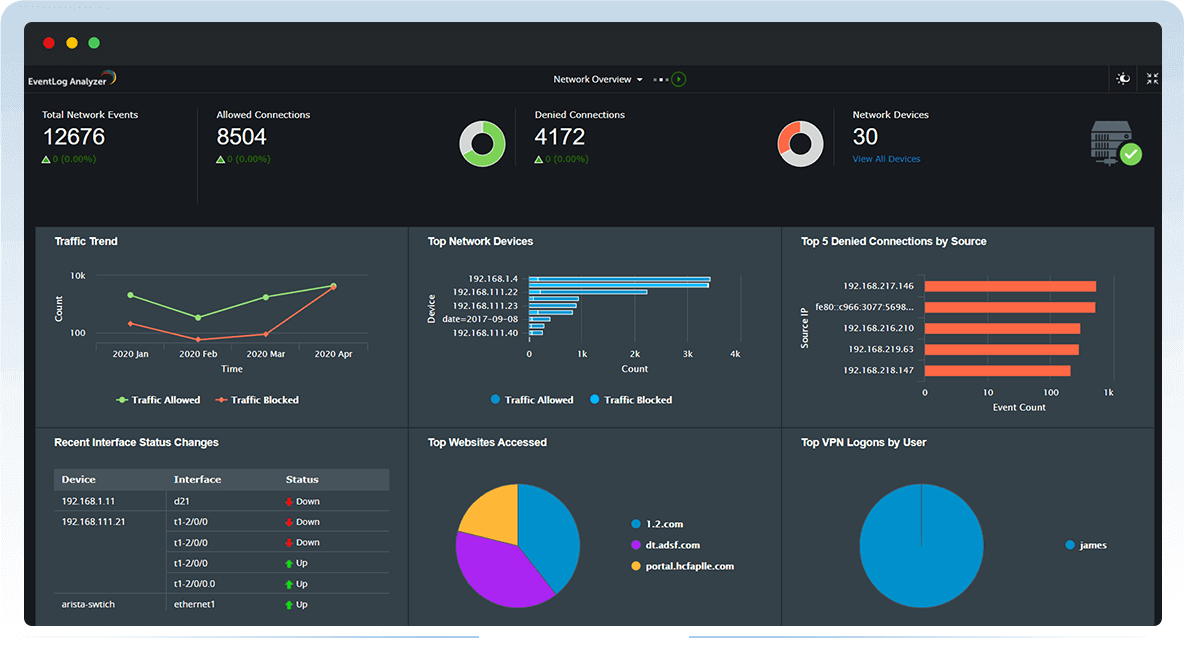


Gain actionable insights from your network logs with intuitive dashboards, predefined report templates, and alert profiles that are meticulously drafted to meet the security and auditing needs of organizations. This log analyzer software supports analysis of over 700+ log formats right out of the box.
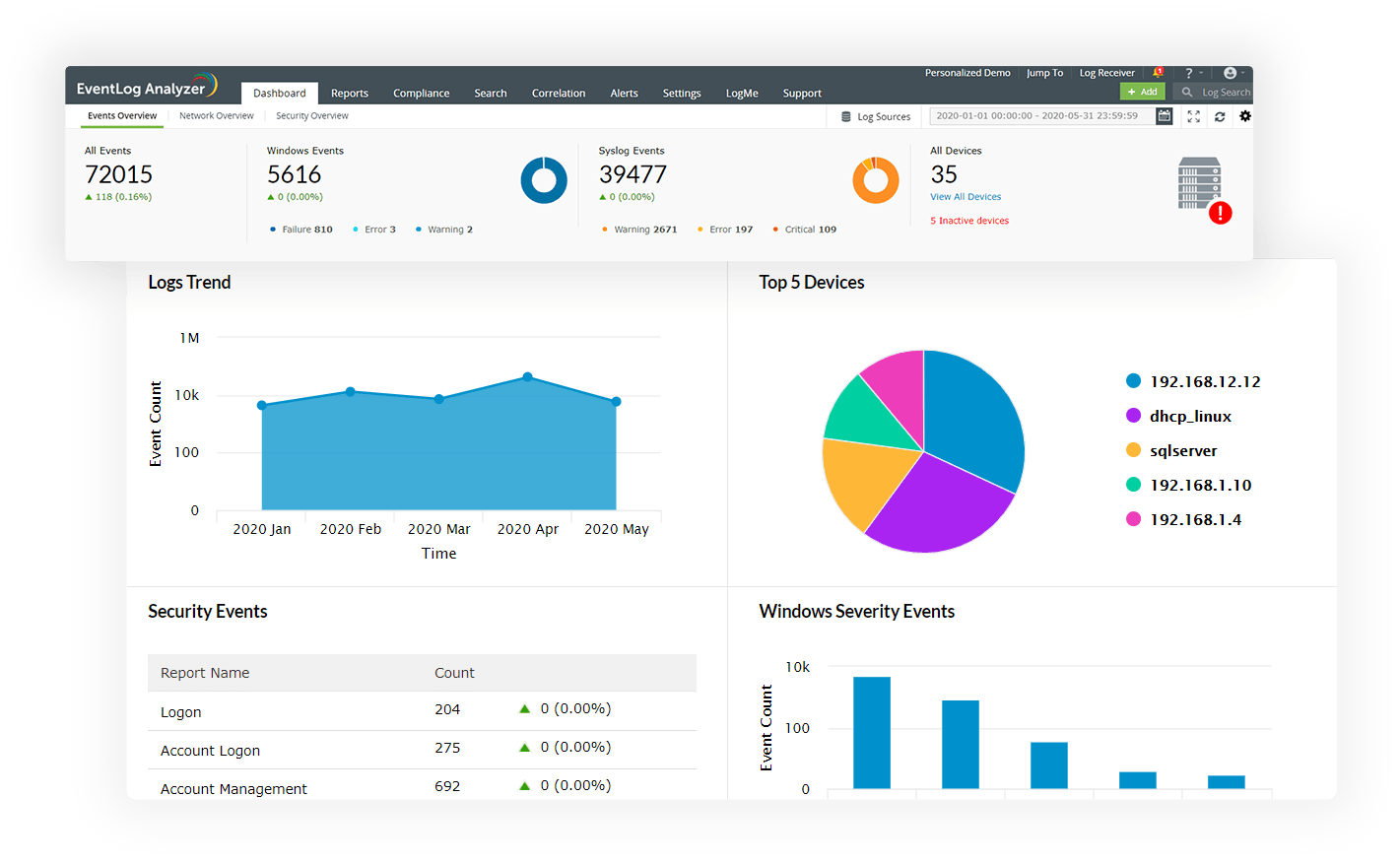
Centrally collect, monitor, analyze, correlate, search, and archive log data from devices across the network. This centralized log analytics tool helps you detect attack attempts and trace potential security threats faster. Ensure timely remediation of these threats using the automated incident response capabilities.
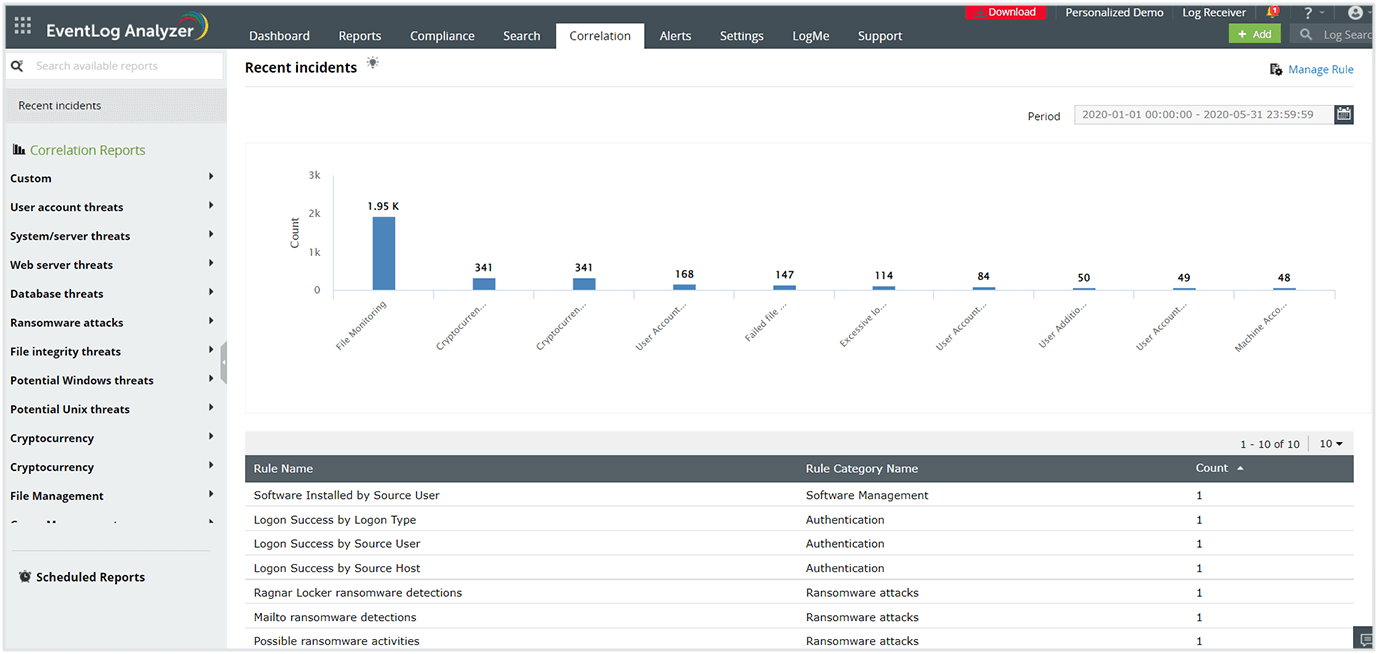
Meet compliance requirements for various regulatory mandates including PCI DSS, GDPR, FISMA, ISO 27001, and SOX with audit-ready report templates from EventLog Analyzer. Get notified in real time upon compliance requirement violations and build a custom compliance report to meet your internal security policy using the solution's integrated compliance management system.
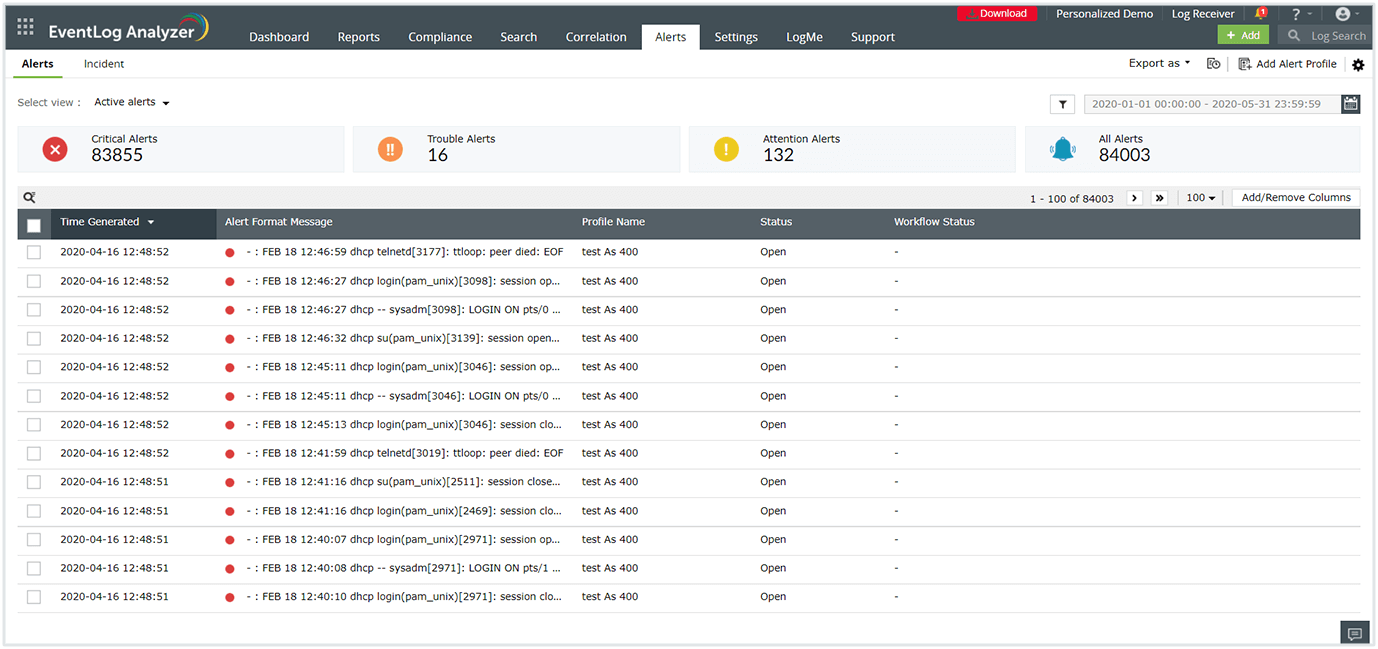
The log analysis software comes bundled with a global IP threat database and STIX/TAXII feed processor to detect any malicious inbound or outbound traffic. Analyze web server logs and firewall log data to identify traffic from and to blacklisted IP addresses and instantly block them with automated workflow profiles. Analyze Active Directory (AD) and domain name system (DNS) logs to instantly spot suspicious activities of insiders. Detect malicious activities such as privilege escalations, unauthorized access to sensitive data, first time access to critical resource, and more with effective AD and DNS log analysis.
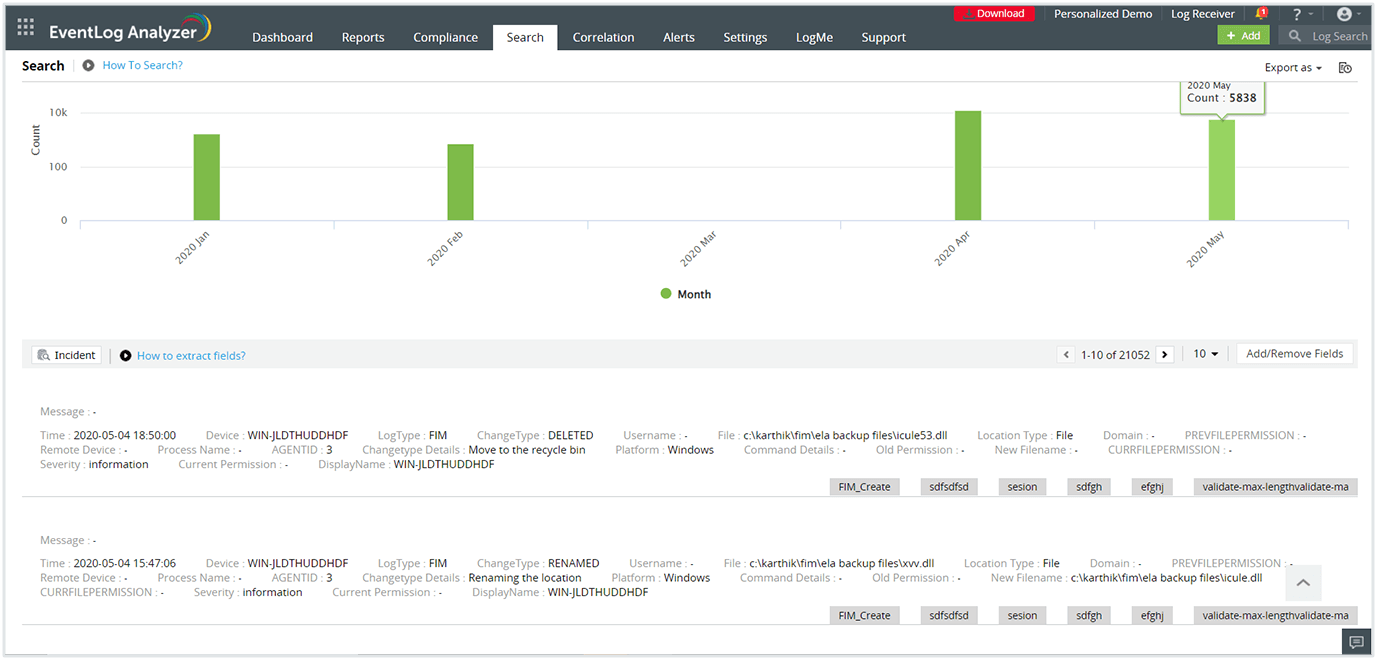
EventLog Analyzer, our log analyzer software, comes with a powerful log search feature for conducting root cause analysis. Search through raw and formatted logs and generate reports based on the results. Automate query building with an easy-to-use drag n drop interface. This log analysis solution comes with different search options such as boolean, range, group, and more to narrow down the search to the exact log entry within minutes. The powerful log search analytics can process up to 25,000 logs per second. This log analyzer software is capable of locating a malicious log entry and setting up remediation from within the log search console.
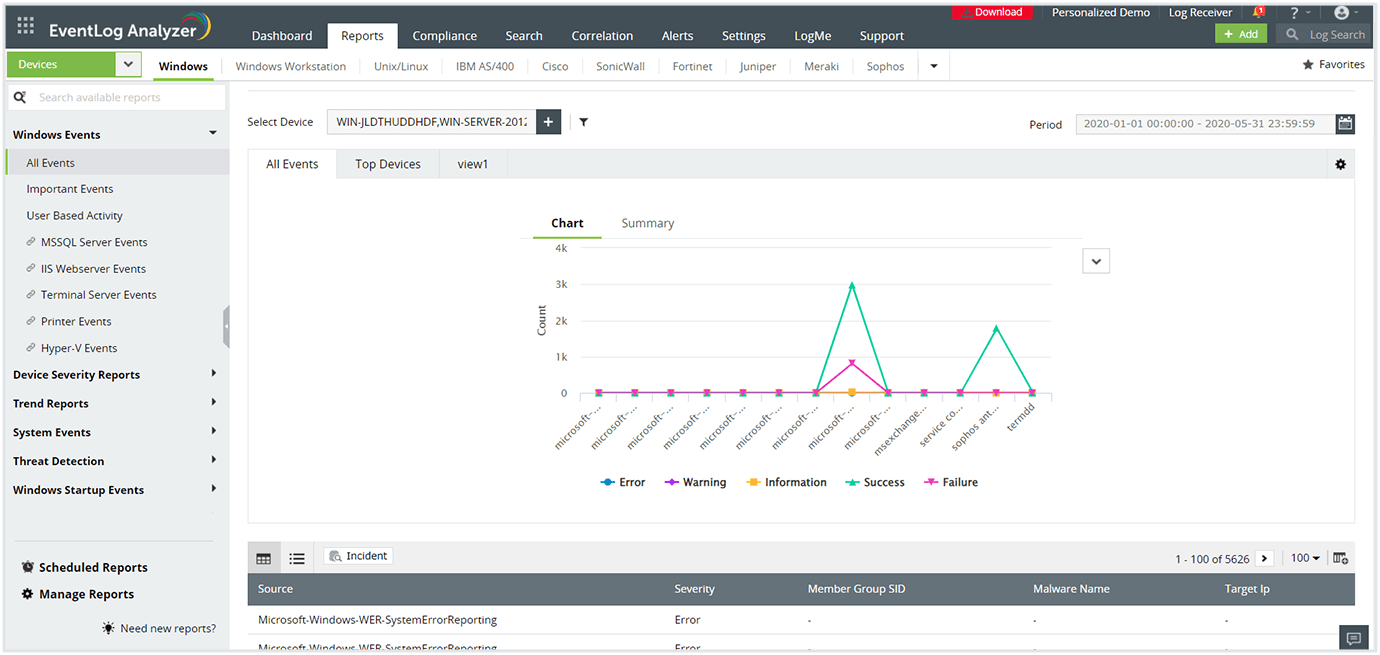
Gain actionable insights from your network logs with intuitive dashboards, predefined report templates, and alert profiles that are meticulously drafted to meet the security and auditing needs of organizations. This log analyzer software supports analysis of over 700+ log formats right out of the box.

Centrally collect, monitor, analyze, correlate, search, and archive log data from devices across the network. This centralized log analytics tool helps you detect attack attempts and trace potential security threats faster. Ensure timely remediation of these threats using the automated incident response capabilities.

Meet compliance requirements for various regulatory mandates including PCI DSS, GDPR, FISMA, ISO 27001, and SOX with audit-ready report templates from EventLog Analyzer. Get notified in real time upon compliance requirement violations and build a custom compliance report to meet your internal security policy using the solution's integrated compliance management system.

The log analysis software comes bundled with a global IP threat database and STIX/TAXII feed processor to detect any malicious inbound or outbound traffic. Analyze web server logs and firewall log data to identify traffic from and to blacklisted IP addresses and instantly block them with automated workflow profiles. Analyze Active Directory (AD) and domain name system (DNS) logs to instantly spot suspicious activities of insiders. Detect malicious activities such as privilege escalations, unauthorized access to sensitive data, first time access to critical resource, and more with effective AD and DNS log analysis.

EventLog Analyzer, our log analyzer software, comes with a powerful log search feature for conducting root cause analysis. Search through raw and formatted logs and generate reports based on the results. Automate query building with an easy-to-use drag n drop interface. This log analysis solution comes with different search options such as boolean, range, group, and more to narrow down the search to the exact log entry within minutes. The powerful log search analytics can process up to 25,000 logs per second. This log analyzer software is capable of locating a malicious log entry and setting up remediation from within the log search console.

This log analyzer software can collect, store and analyze log data from across all devices in your network to provide in-depth visibility into your network activities.
Check out our user and entity behavior analytics (UEBA) add-on that can automate log analysis using machine learning algorithms to effectively track and stop insider and external threats.
Unlike other log analysis solutions available in the market, EventLog Analyzer comes bundled with out-of-the-box analysis support to over 700 log formats, including network devices such as firewalls, routers, IDS/IPS, and switches; web servers like IIS and Apache; file servers, workstations, and more.
Get better insights into your remote work environment by collecting and analyzing VPN logs. Gain visibility into access and activities of remote employees using the exclusive VPN security dashboard. EventLog Analyzer can also help with AWS and Azure log analytics.
Effectively conduct log forensics with a high-speed search engine that processes log data at 25,000 events per second. Narrow down to the exact log entry with automated basic and advanced log search query builder.
Centrally collect and analyze the logs of your web server application such as Internet Information Services and Apache. Read, parse, and analyze proxy server logs to detect suspicious network traffic and user behavior.
Gain insights about user activities happening on your Windows, Linux, and Unix servers. Visualize logins, file accesses, permission changes, and other critical activities using the security analytics dashboard to spot threats instantly.
Starts at $795Year
Try NowClick here for a detailed comparison between on-premise and cloud version.
We strive for excellence to provide your organization with the best security. Our commitment to innovate constantly and ensure customer satisfaction has earned us some awards and recognitions. Here are a few of the accolades from 2023-2024.
Niche Player in the 2024 Gartner Magic Quadrant for Security Information and Event Management
Contender in Extended Detection and Response (XDR) in the ISG Provider Lens Cybersecurity - Solutions and Services, 2023
Challenger in KuppingerCole's Leadership Compass: Data Leakage Prevention, 2023
Challenger and Outperformer in the GigaOm Radar for Autonomous SOC, 2023
Customer's Choice in the Peer Insights 'Voice of the Customer': Security Information and Event Management, 2023
Zoho Corporation Pvt. Ltd. All Rights Reserved.

Your download should begin automatically in 15 seconds. If not, click here to download manually.