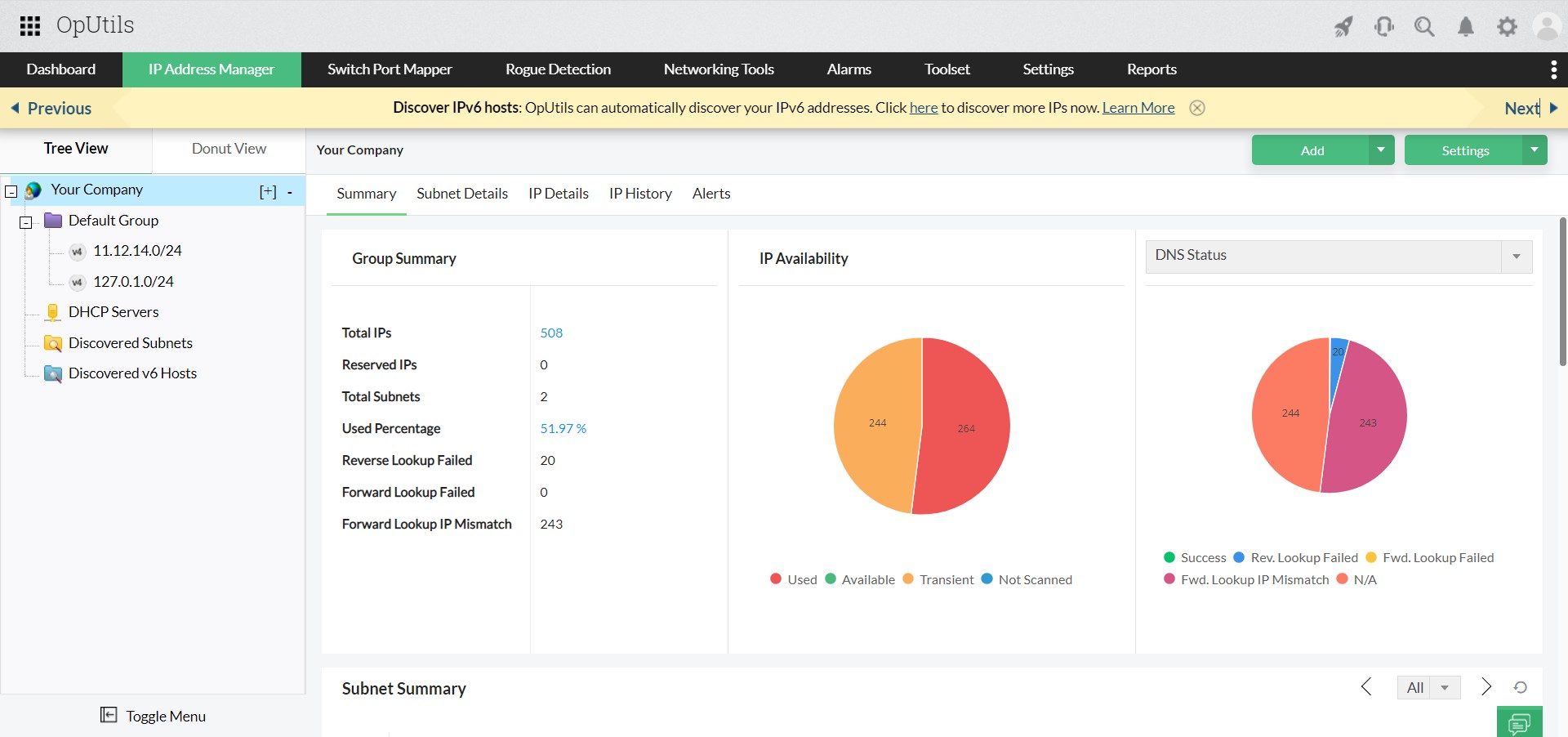
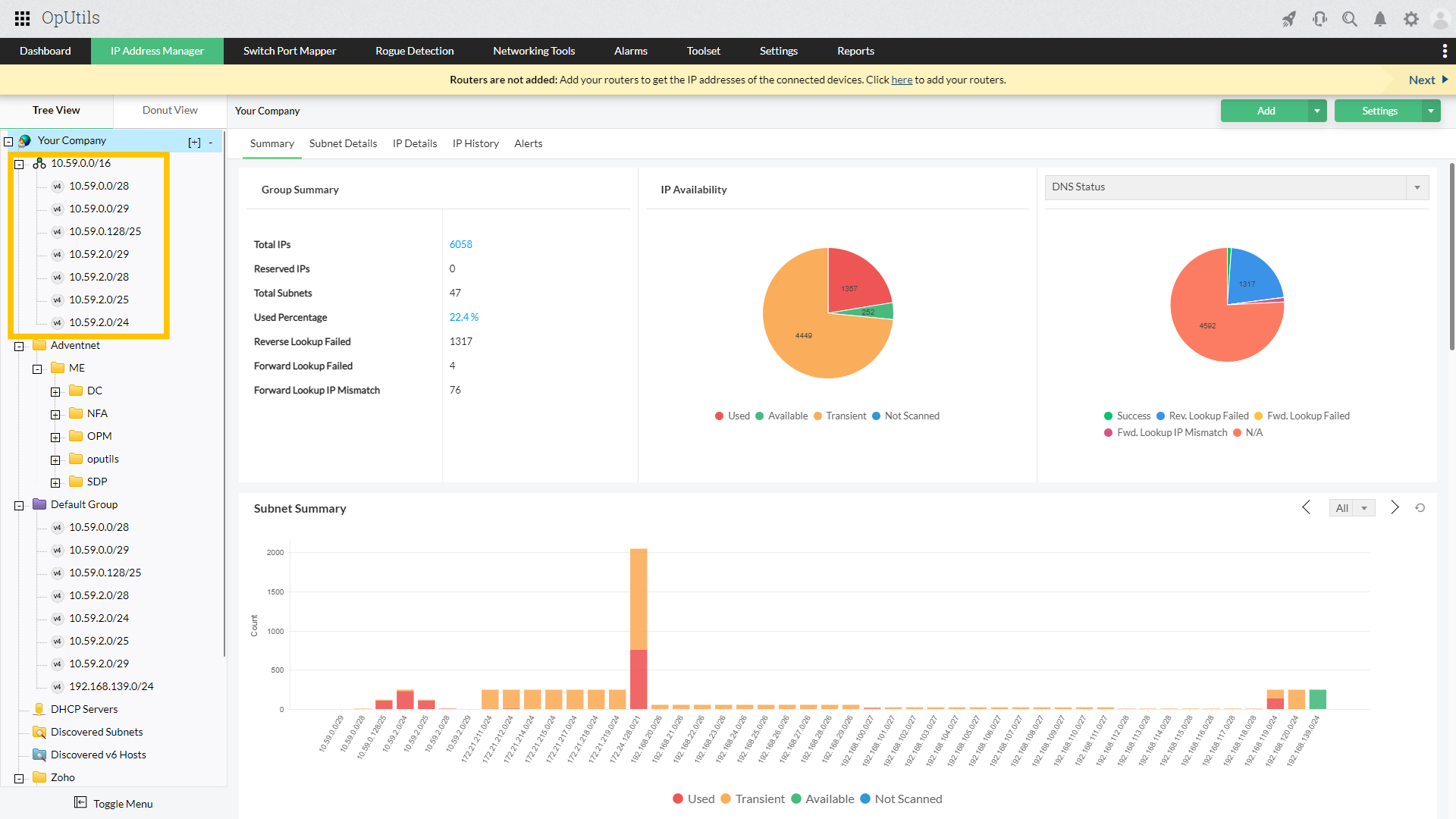
Managing IP addresses has shifted from being a mere routine task to a core function of IT operations. What once involved tracking a limited pool of addresses in static environments has transformed into overseeing thousands of dynamic, short-lived IPs across cloud-native, containerized, or hybrid environments.
This shift demands a structured approach to IP address management, helping the IT teams maintain in-depth visibility, prevent IP conflicts, and support a scalable environment without affecting the network's performance or security.
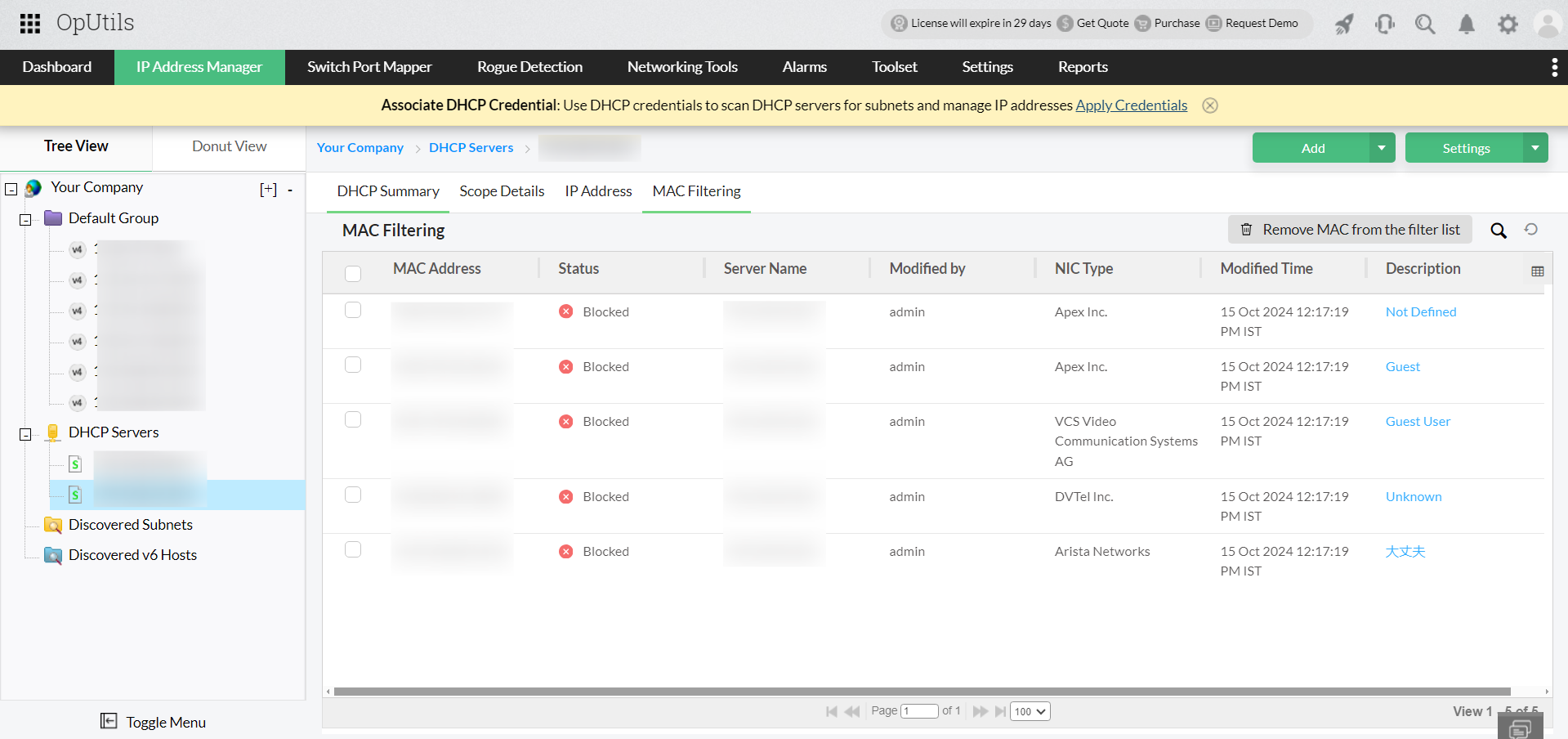
Relying on manual checks or waiting for user complaints is no longer practical. Modern IP conflict detection tools continuously scan for duplicate IP addresses, log historical incidents, and send instant alerts the moment a conflict occurs, helping teams minimize downtime and ensure seamless connectivity.
Hence, knowing the best practices for IP address management is the key to building a resilient network. Before diving into the best practices, let us understand the basics of IPAM.