Rogue detection made easy with OpUtils
As networks grow in complexity, gaining full visibility to identify unauthorized devices becomes essential. OpUtils addresses this challenge with its advanced network discovery capabilities, periodically scanning the network to identify all connected devices. IT administrators can then group these devices based on their authorization levels, manage switch ports effectively, and instantly block any rogue devices. In a nutshell, OpUtils enhances network security by simplifying rogue device detection.
Feature highlights: OpUtils' rogue detection software
Automated scanning
OpUtils automatically schedules the regular scans of your network. This solution proactively monitors the network for unauthorized devices, allowing prompt action.
Real-time detection
IT admins receive immediate notifications when unauthorized devices connect to the network. This ensures no rogue device is unnoticed.
Remote blocking
IT admins can swiftly disconnect unauthorized devices from the network by remotely blocking switch ports. This proactive approach stops rogue devices in their tracks, ensuring the integrity and security of your network.
Authentication
OpUtils enhances network security by enabling IT admins to inspect device details and classify them based on their authenticity.
Integration capabilities
OpUtils' Rogue Detection is tightly integrated with Switch Port Mapper, IP Address Manager, and Active Directory, providing detailed visibility and control over network activities, enabling efficient identification and management of unauthorized devices.
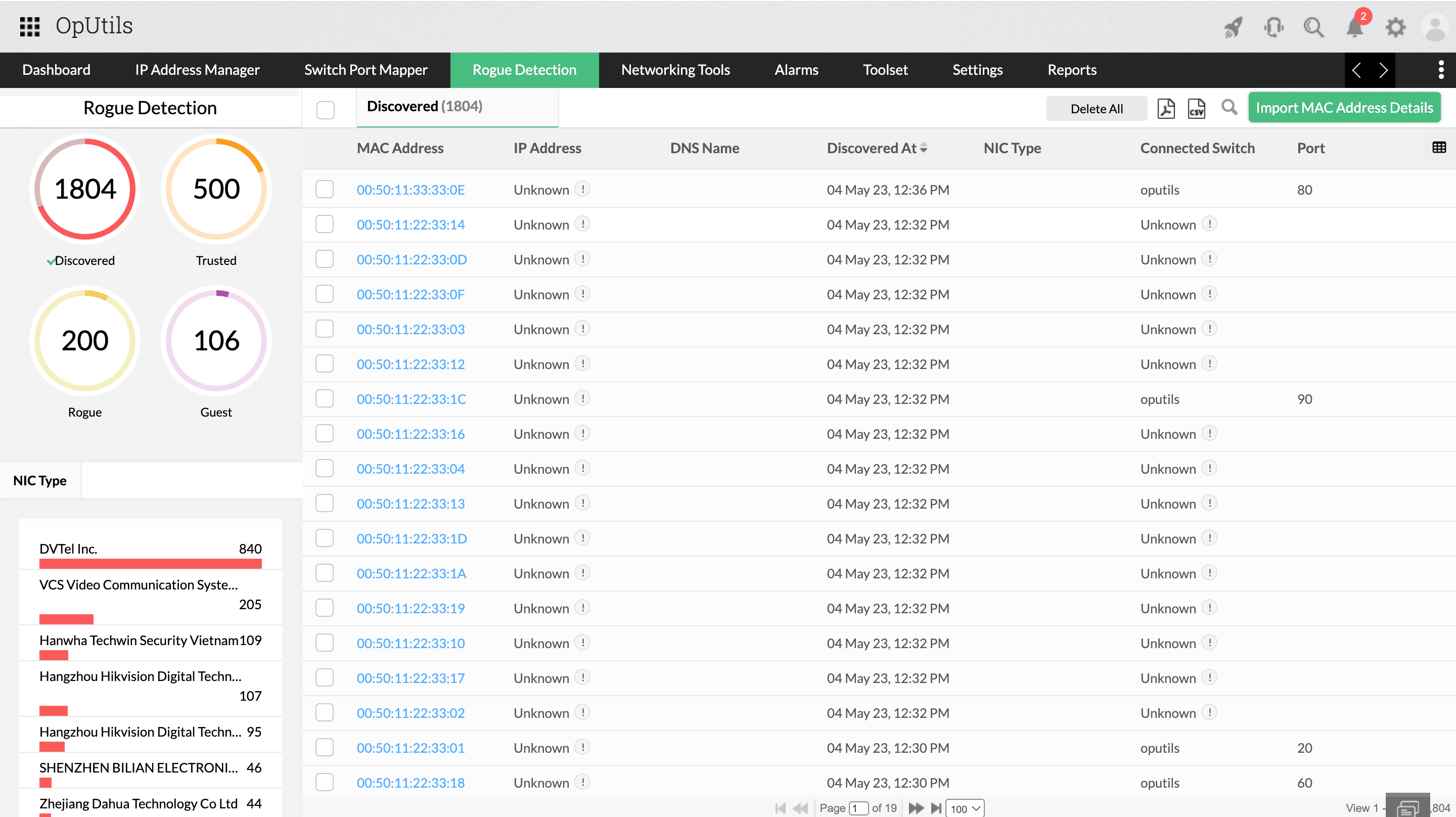
How OpUtils simplifies rogue device detection
Seamless discovery
OpUtils' rogue device detection module seamlessly fetches the MAC addresses of devices discovered from routers, port scanning, IP scanning, and DHCP server imports. These addresses are then compared with Active Directory for automatic classification. Additionally, you can manually import MAC addresses for devices outside of Active Directory, ensuring comprehensive network coverage. New devices are added automatically during subsequent scans, ensuring no device is left out without being discovered into the tool.
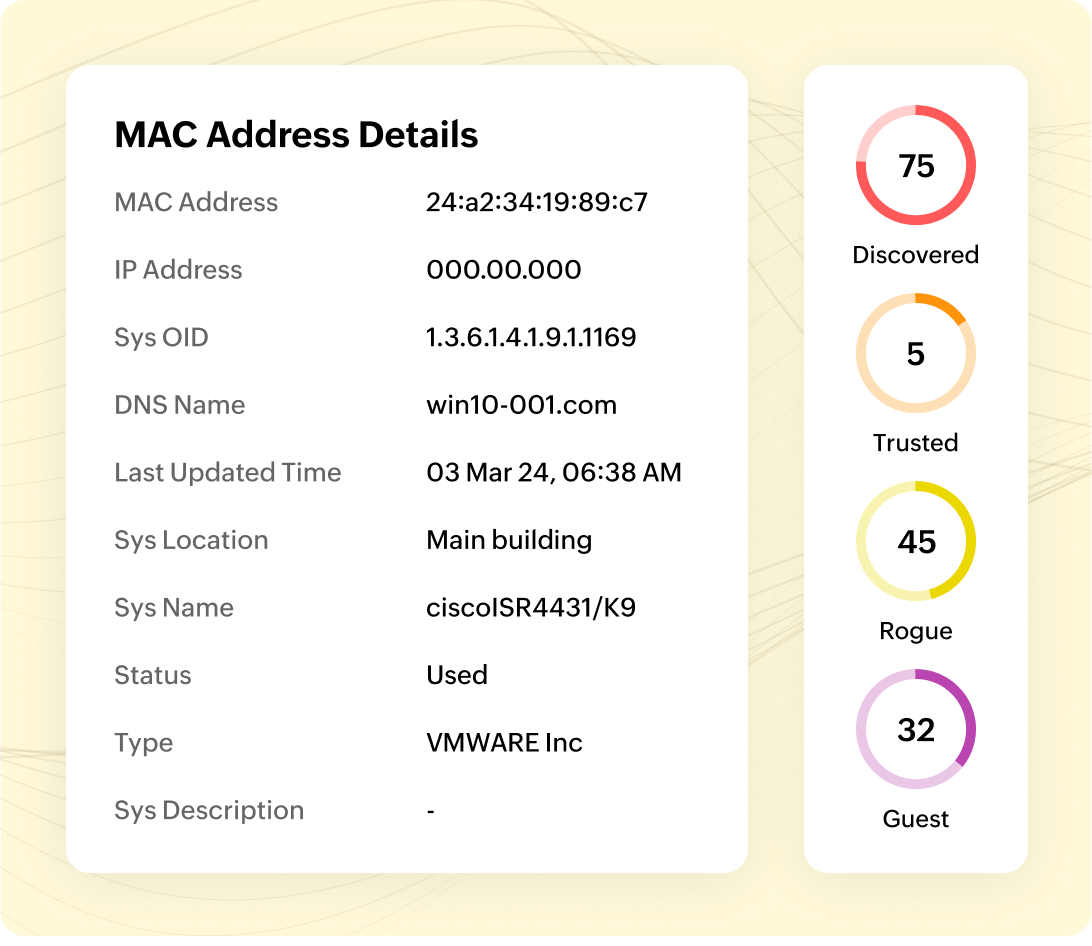
Authenticity profiling
OpUtils enables IT admins to inspect devices by clicking on the discovered devices, displaying details such as MAC address, DNS name, IP address, and connected port information. Utilizing the Switch Port Mapper tool, OpUtils maps all switches and provides connected port details. This helps IT admins understand through which devices rogue data might have passed, enabling them to take precautions with these devices as well. With this comprehensive information, IT admins can verify and classify devices based on their authenticity, enhancing network control and security.
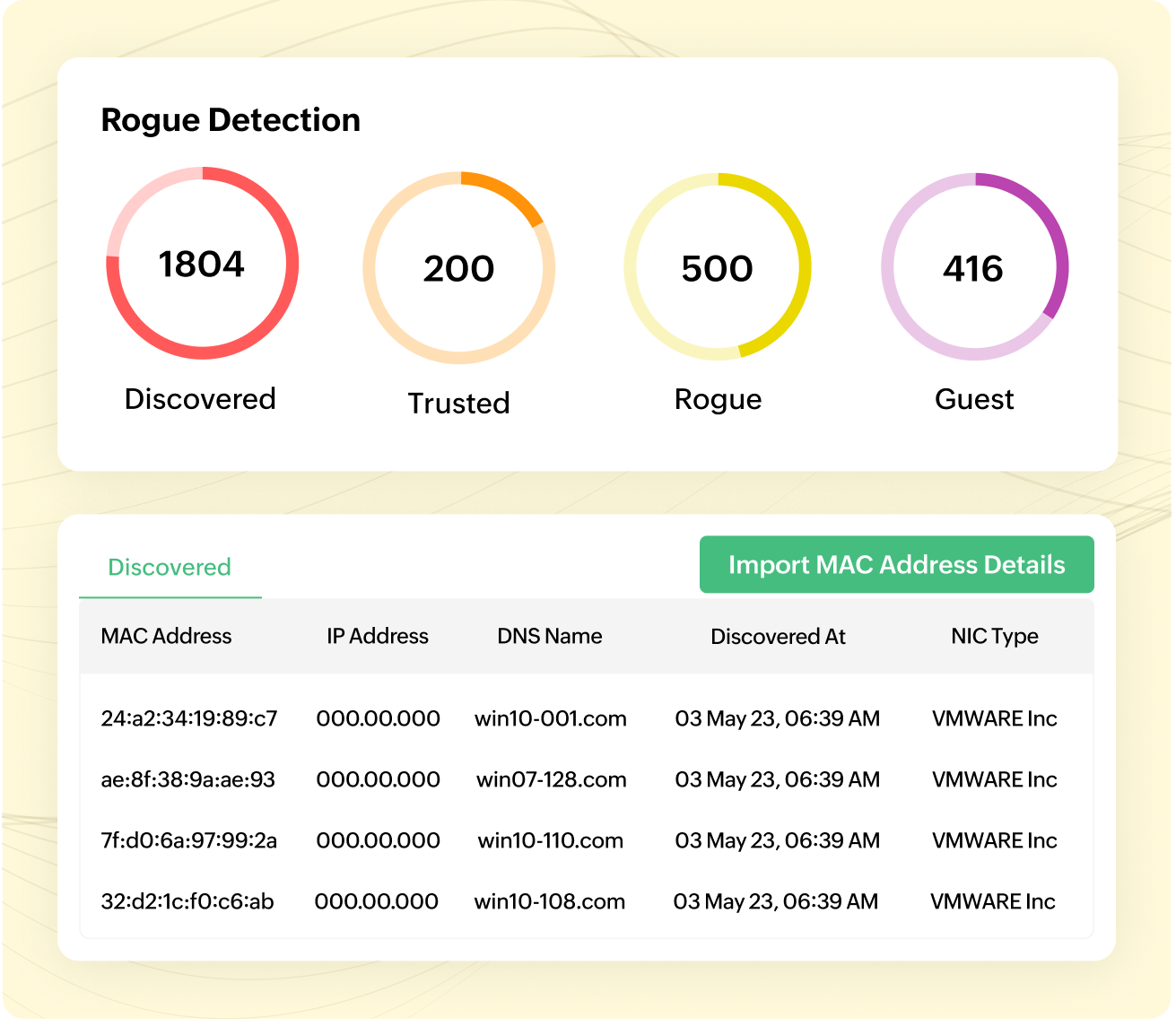
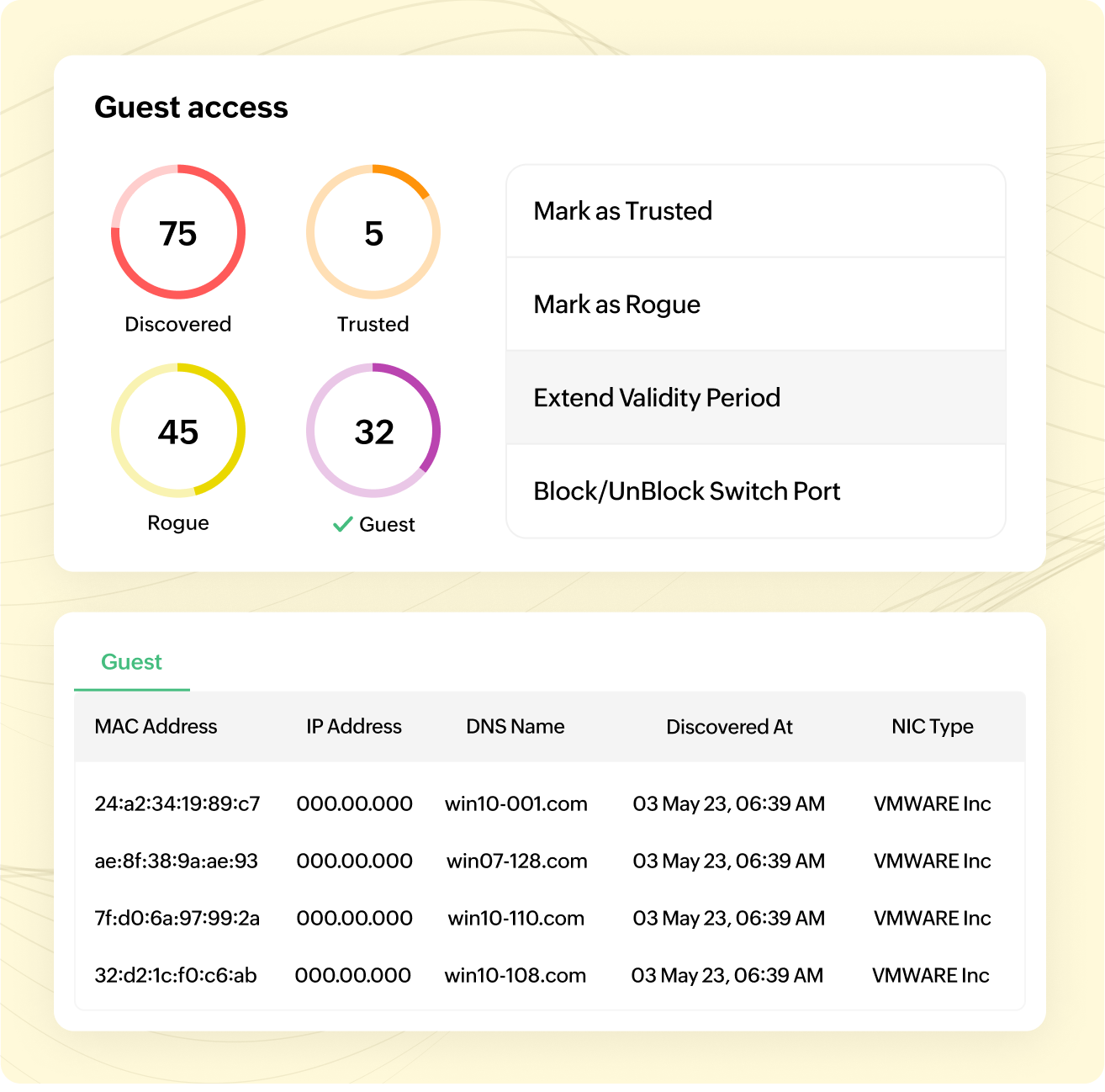
Guest access
There could be scenarios in your network where you need to grant access to certain devices for a limited period. If these devices are marked as trusted and not unmarked after the required period, it can lead to serious security consequences. To resolve this, OpUtils provides an option called "mark as guest." IT admins can use this resource to mark the devices as "guest" and set a validity period with an expiry. The IT admins can also choose to extend the validity period of the guest users.
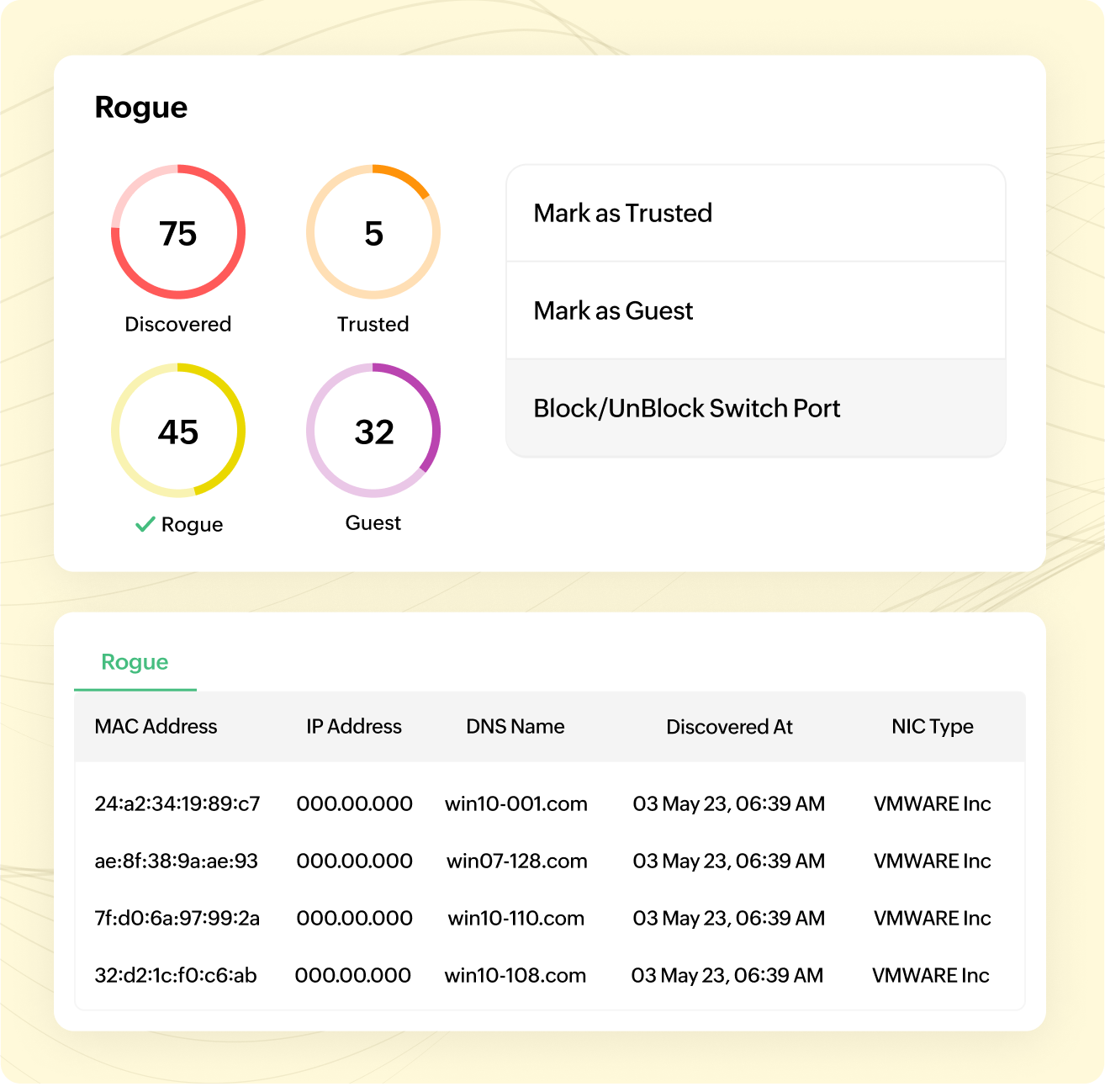
Blocking unauthorized devices
With OpUtils' Rogue Detection module integrated with Switch Port Mapper, IT admins receive instant notifications of unauthorized access. This integration provides detailed information about the switches and ports used by rogue devices, enabling swift action. IT admins can remotely block or unblock switch ports directly within OpUtils, ensuring prompt and effective network security management. Once the issue is resolved, IT admins can unblock the switch ports.
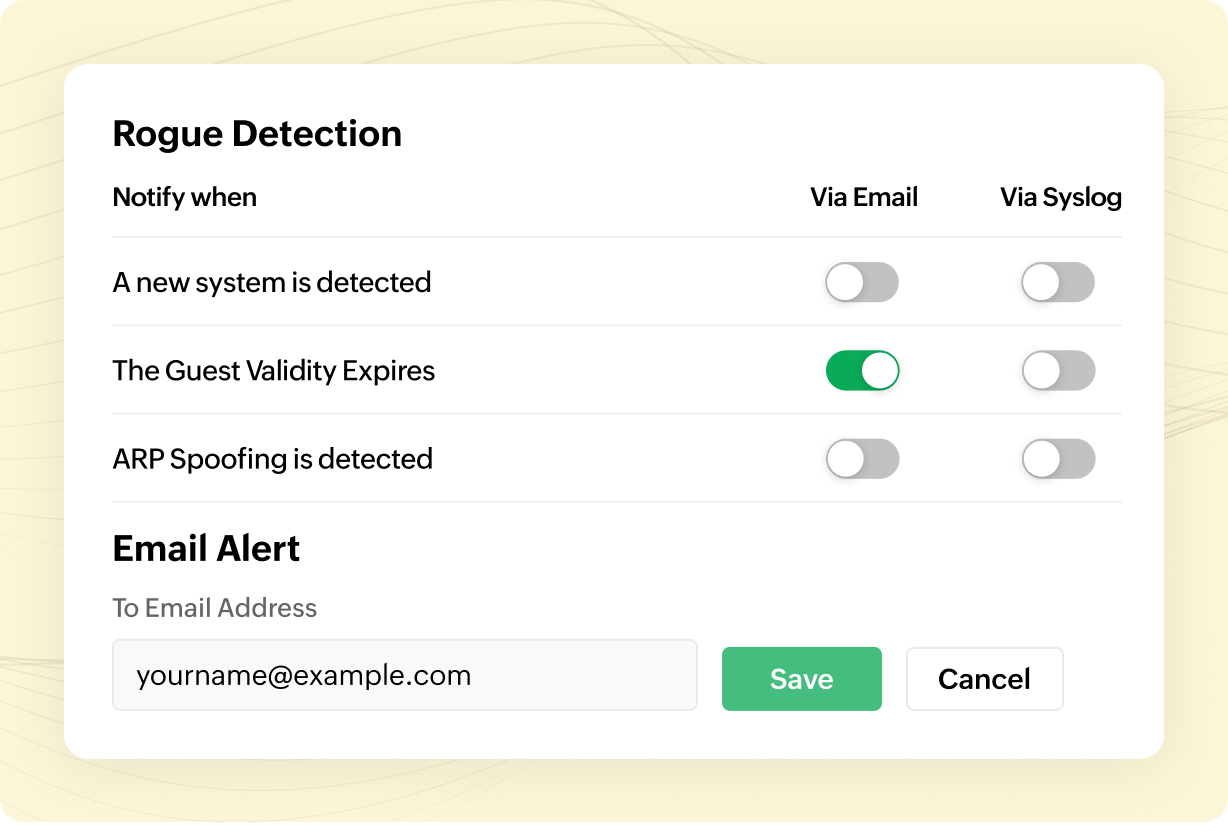
Real-time alert notification
OpUtils instantly notifies IT admins upon detecting new devices, guest device validity expiration, and ARP spoofing incidents in real-time, ensuring comprehensive network security monitoring. Additionally, the notifications can be received through emails, syslogs, and through the console. This ensures comprehensive security management in the network.
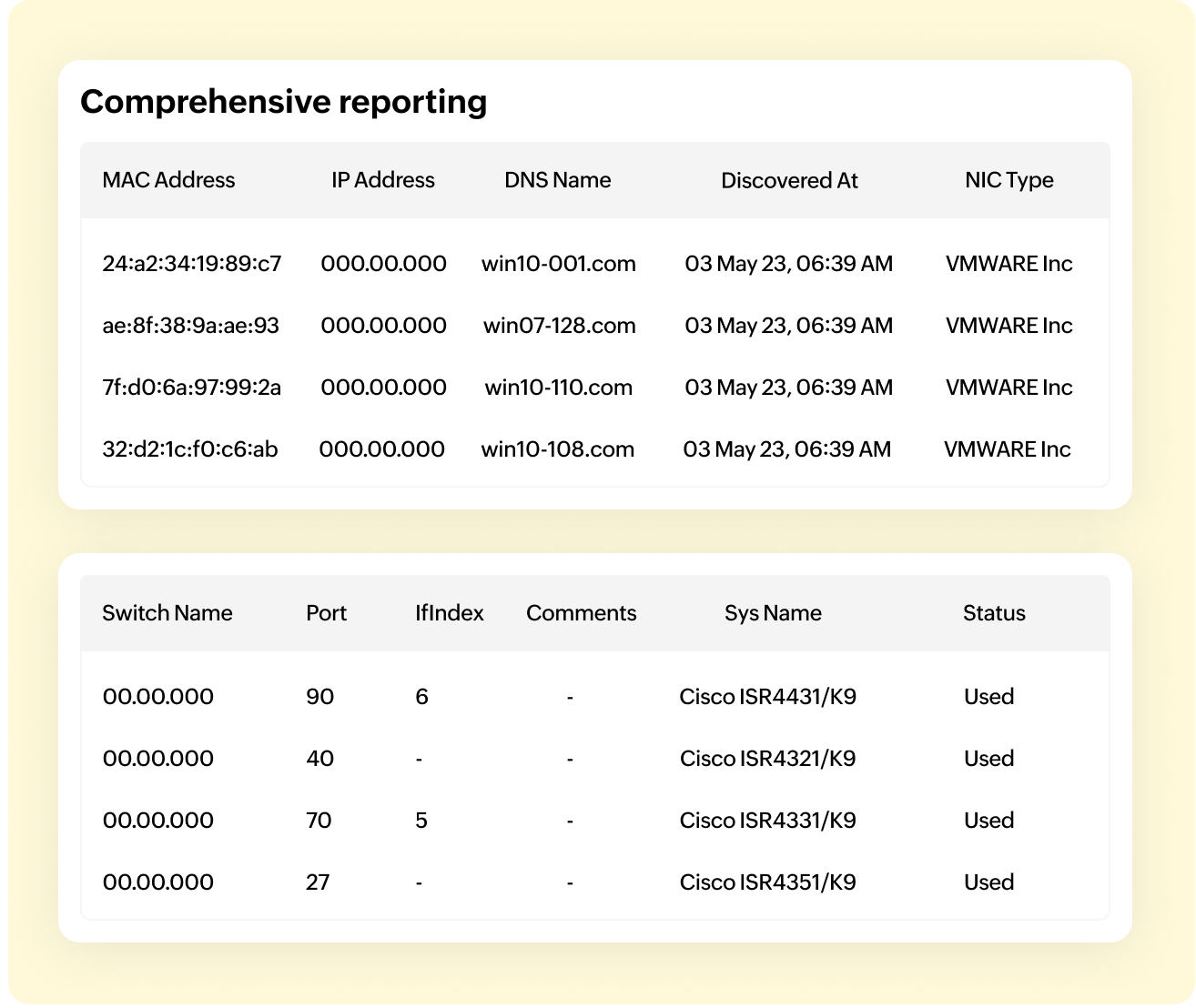
Comprehensive reporting
OpUtils' rogue device detection system lets you generate detailed reports that provide comprehensive insights into network security incidents and rogue device activities. These reports are essential for maintaining compliance with industry standards and regulations and play a vital role in audits. These in-depth insights help IT admins identify vulnerabilities and potential threats. Ultimately, these insights are crucial for enhancing and refining your overall security strategies.