Configuring SAML Single Sign-On (SSO) for Entra ID Users
You can set up SAML single sign-on (SSO) in Password Manager Pro for Entra ID users. This document also details steps to enable multi-factor authentication (MFA) in the Microsoft Azure portal.
Note: Password Manager Pro allows users to configure SAML SSO for the secondary server as a service provider, which allows users to log in to Password Manager Pro using the secondary server when the primary server is down.
At the end of this document, you will have learned the following configuration concerning SAML SSO configuration for Azure AD users and setting up MFA for the first login users.
- Prerequisite
- Steps to Configure SAML SSO for Entra ID Users
- Steps to Enable MFA and Set up First Login for Entra ID Users
- Troubleshooting Tips
1. Prerequisite
Before setting up SAML SSO, follow the steps provided here to import Entra ID users into Password Manager Pro.
2. Steps to Configure SAML SSO for Entra ID Users
Detailed below are the steps to configure SAML SSO in Password Manager Pro for Entra ID users in the Microsoft Azure portal.
2.i Adding Password Manager Pro as an Enterprise Application in the Azure Portal
- Log in to the Microsoft Azure portal.
- Click Entra ID below Azure services.
- In the window that opens, select Enterprise Applications under the Manage tab.
- Now, click New Application available at the top of the Enterprise applications page.
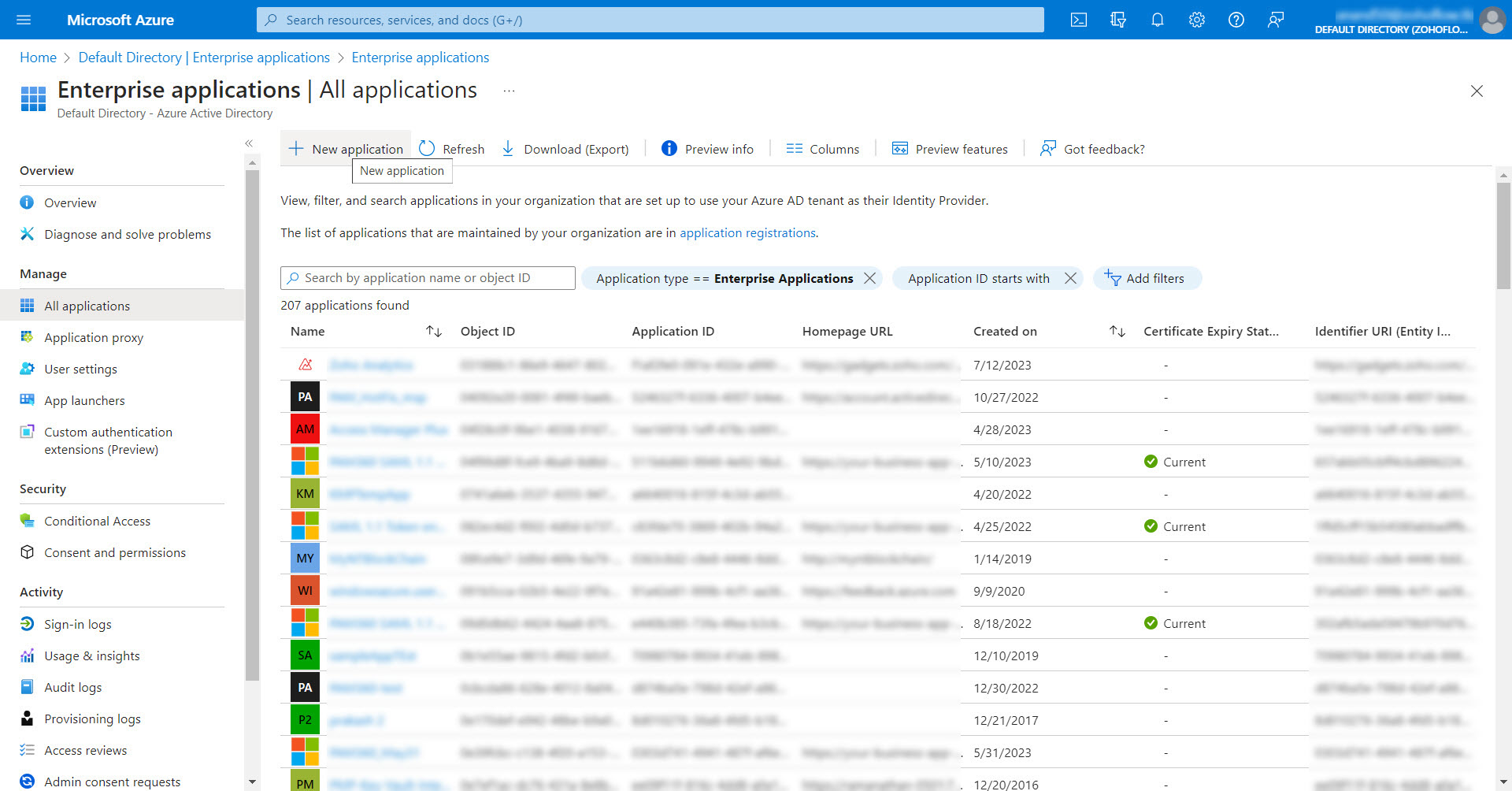
- You will be taken to the All Applications page, from which you can choose and add your desired applications. In the search bar, type 'SAML ' and press Enter.

- From the search results, click on SAML 1.1 Token enabled LOB App. The application will open in a minimized window on the right pane.
- Edit the application name as the desired name and click Create.
Note: It is recommended to avoid the usage of special characters, spaces, or punctuation in the application name.

- Now, the application will be added as the Enterprise Application successfully.
2.ii Assigning Azure Users to the Enterprise Application
- Under the Manage section on the left pane, select Users and groups and click Add user/group at the top pane.
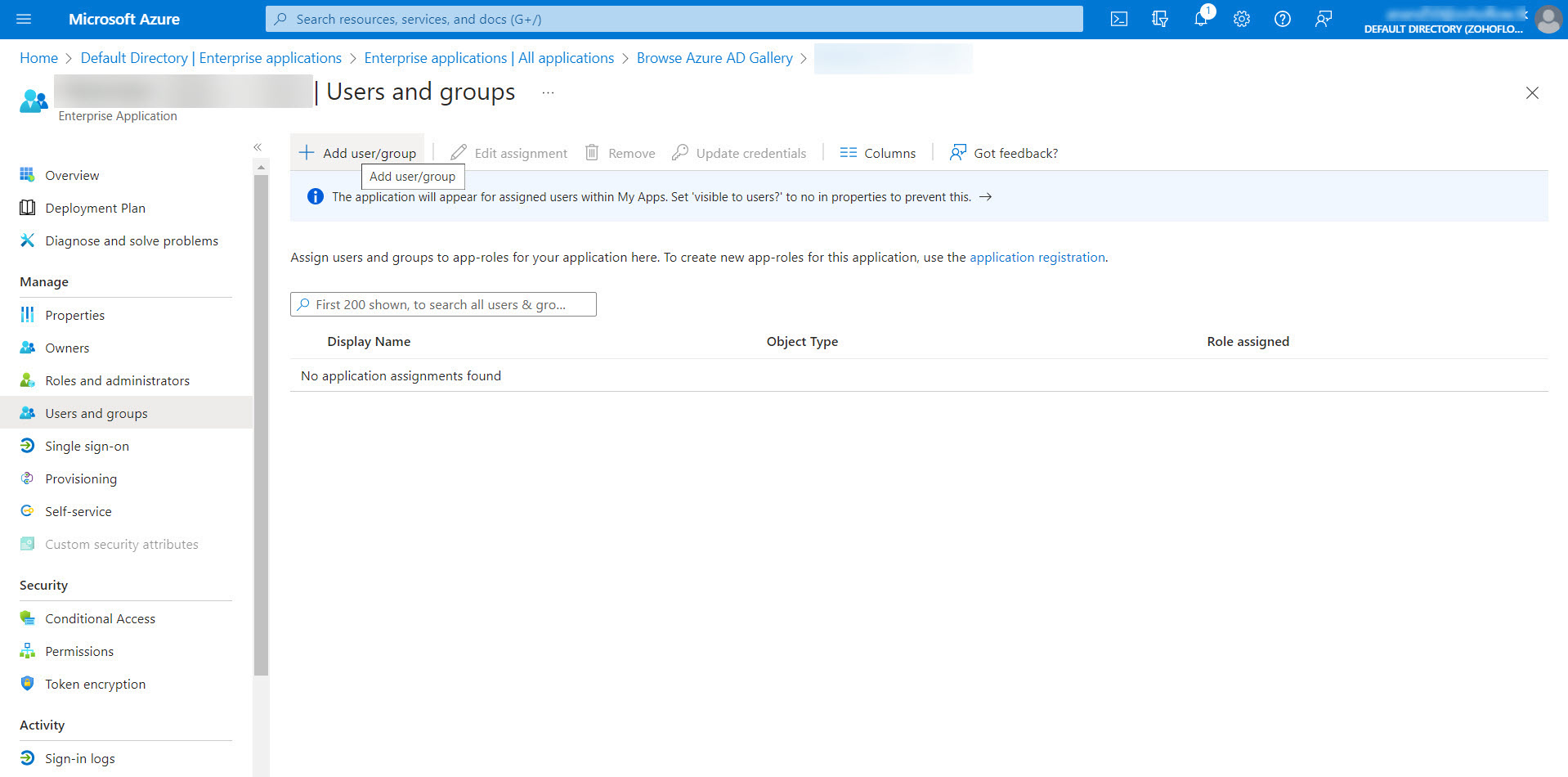
- In the Add Assignment page that opens, click on None Selected to open up a list of users. Select the required users and then click the Select button.
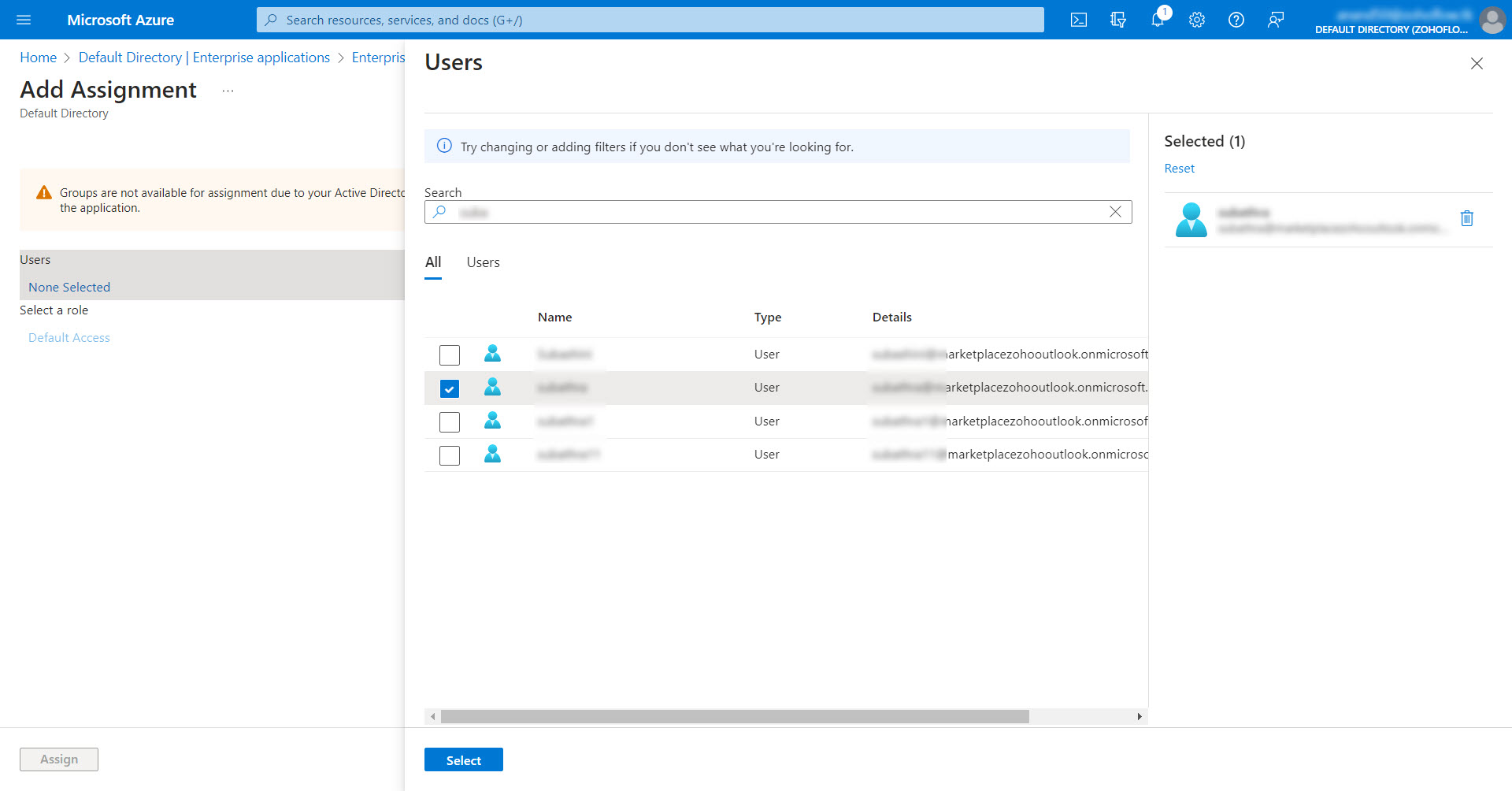
- After the required users have been selected, click Assign to assign them to the enterprise application.
2. iii Configuring SAML SSO with Password Manager Pro
- Under the Manage section on the left pane, click on Single sign-on. In the Select a single sign-on method section, select SAML.
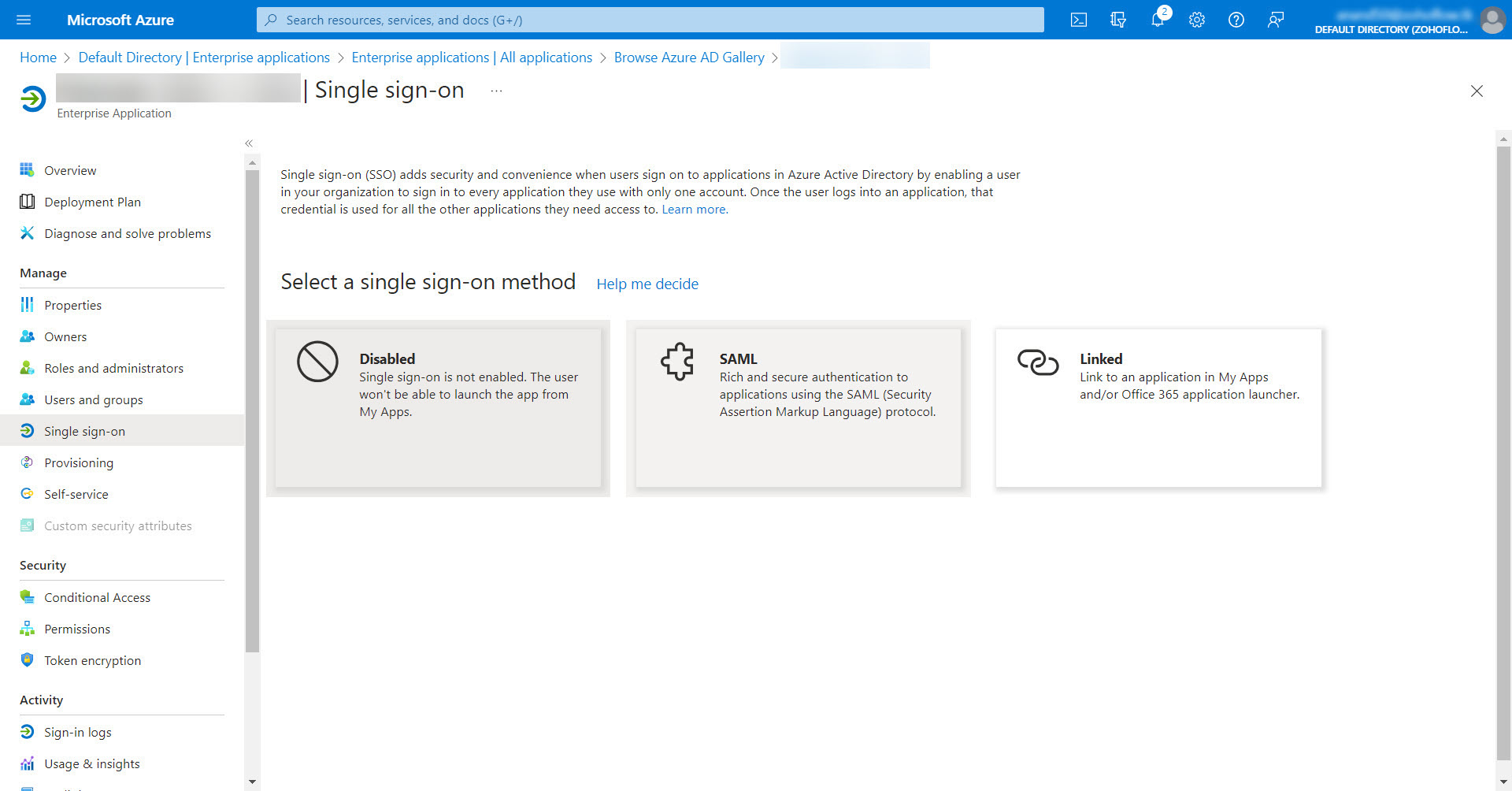
- To set up a single sign-on with SAML, you need to provide basic SAML configuration details, such as Identifier, Reply URL, and Sign on URL.
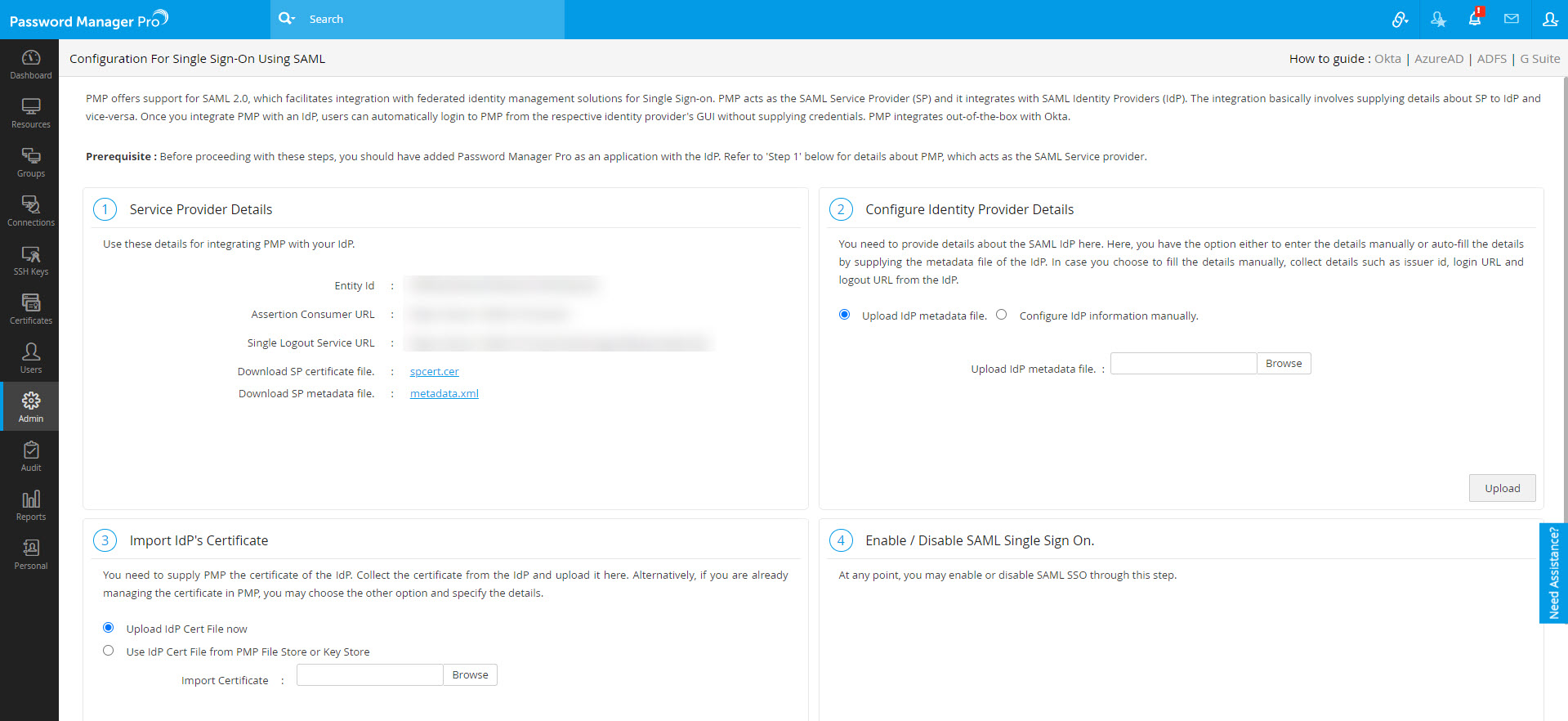
- You can get all the required entities from the Password Manager Pro interface. To do so,
- Log in to Password Manager Pro and navigate to Admin >> Authentication >> SAML Single Sign On.
- Under Service Provider Details, you will find all the required URLs.
Note:
By default, the Assertion Consumer URL is the hostname of the server. To update this, follow the below steps:
1. Navigate to Admin >> Settings >> Mail Server Settings.
2. Under Access URL, update to the required URL and click Save.Now, the Assertion Consumer URL under Service Provider Details will be updated.
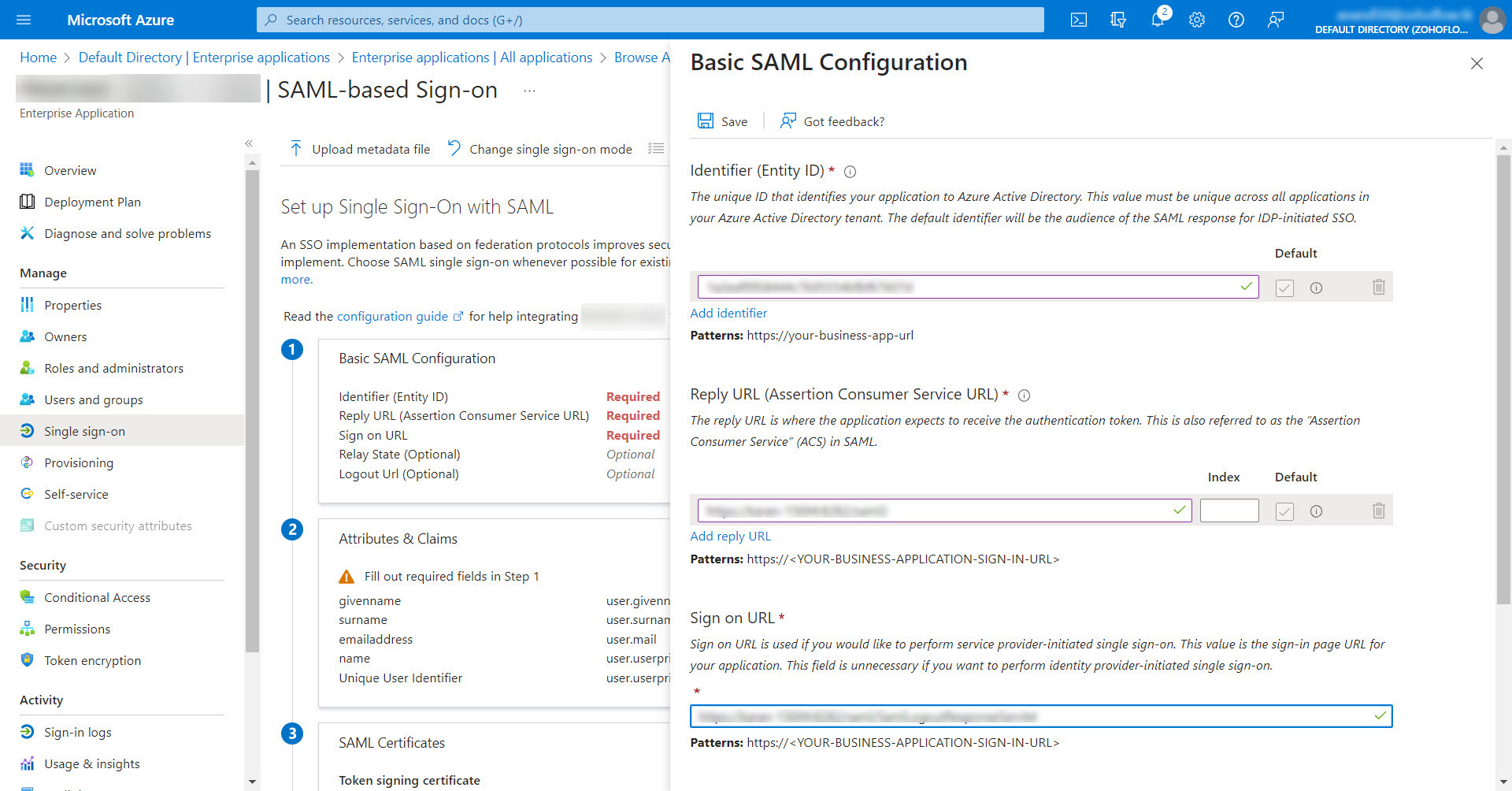
- Now, go back to the Microsoft Azure portal and click the edit icon to edit the Basic SAML Configuration details:
- For Non-MSP, enter the Entity Id (copied from Password Manager Pro) under Identifier. Enter your Password Manager Pro web interface URL under the Sign on URL (e.g., https://<Host-Name-of-PMP-Server OR IP address>:<Port>) and provide the Assertion Consumer Service URL under Reply URL.
- For MSP Client Organizations, enter the Entity Id (copied from Password Manager Pro) under Identifier. Enter the Assertion Consumer URL under the Reply URL and enter the Org URL (eg. https://<Host-Name-of-PMP-Server OR IP address>:<Port>/<Org_name>) under Sign on URL.
- Now, click Save.
- To configure SAML Single Logout,
- Mention Single Logout Service URL (copied from Password Manager Pro) in the field next to Logout URL.
- Navigate to <Password_Manager_Pro_Installation_Directory\conf\system_properties.conf> and append the following system property under the existing properties.
- saml.logout.redirect.slo=true
Note: SAML Single Logout is applicable from Password Manager Pro build 12100 and above only.
- Now the SAML configuration details taken from Password Manager Pro will be saved in the Azure portal.
- In the SAML Certificates section of the SAML configuration settings window, download the XML file named Federation Metadata XML or copy the Login URL, Entra ID Identifier, and the Logout URL values and download the file named Certificate (Base64).
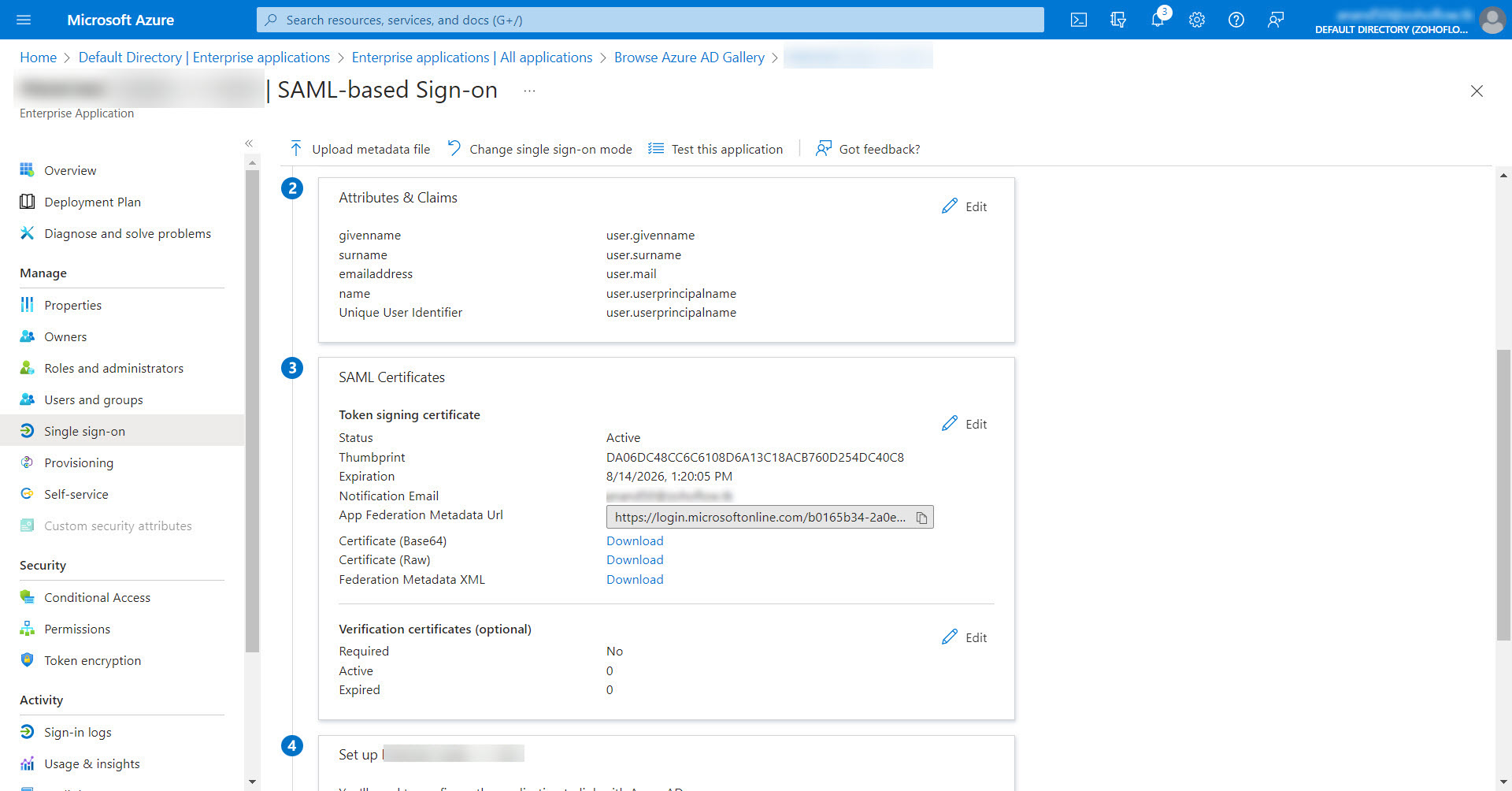
- Return to the Password Manager Pro interface and navigate to Admin >> Authentication >> SAML Single Sign-On.
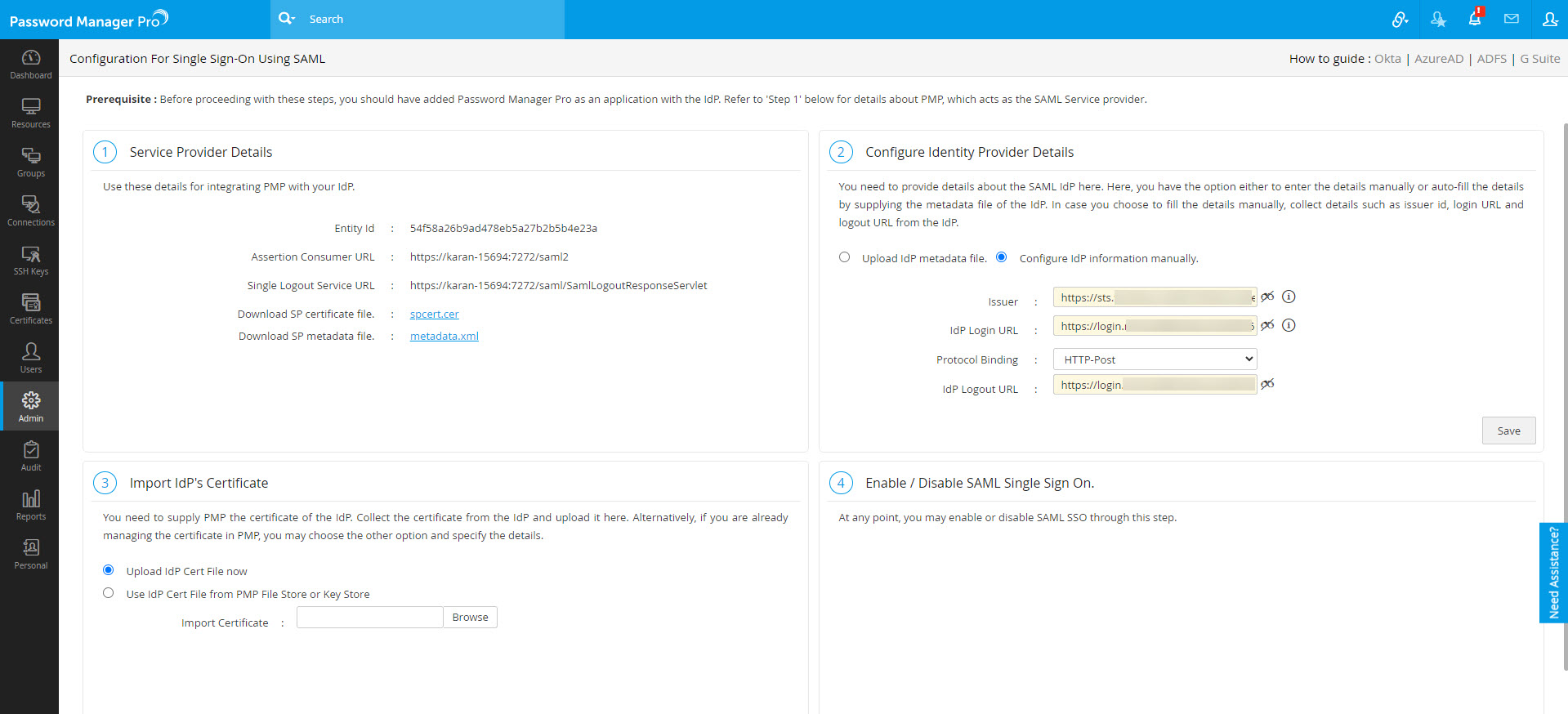
- Under Configure Identity Provider Details, you have to provide your Idp information via an XML file or manually.
- If you opt to update your Idp information via an XML file, select Upload IdP metadata file and click Browse to select the downloaded Federation Metadata XML file.
- If you opt to update your Idp information manually, enter the values copied from the SAML Certificates section - Issuer (Entra ID Identifier), Idp Login URL (Login URL), and Idp Logout URL (Logout URL).
- Now, click Upload to save the Azure SAML SSO settings in Password Manager Pro.

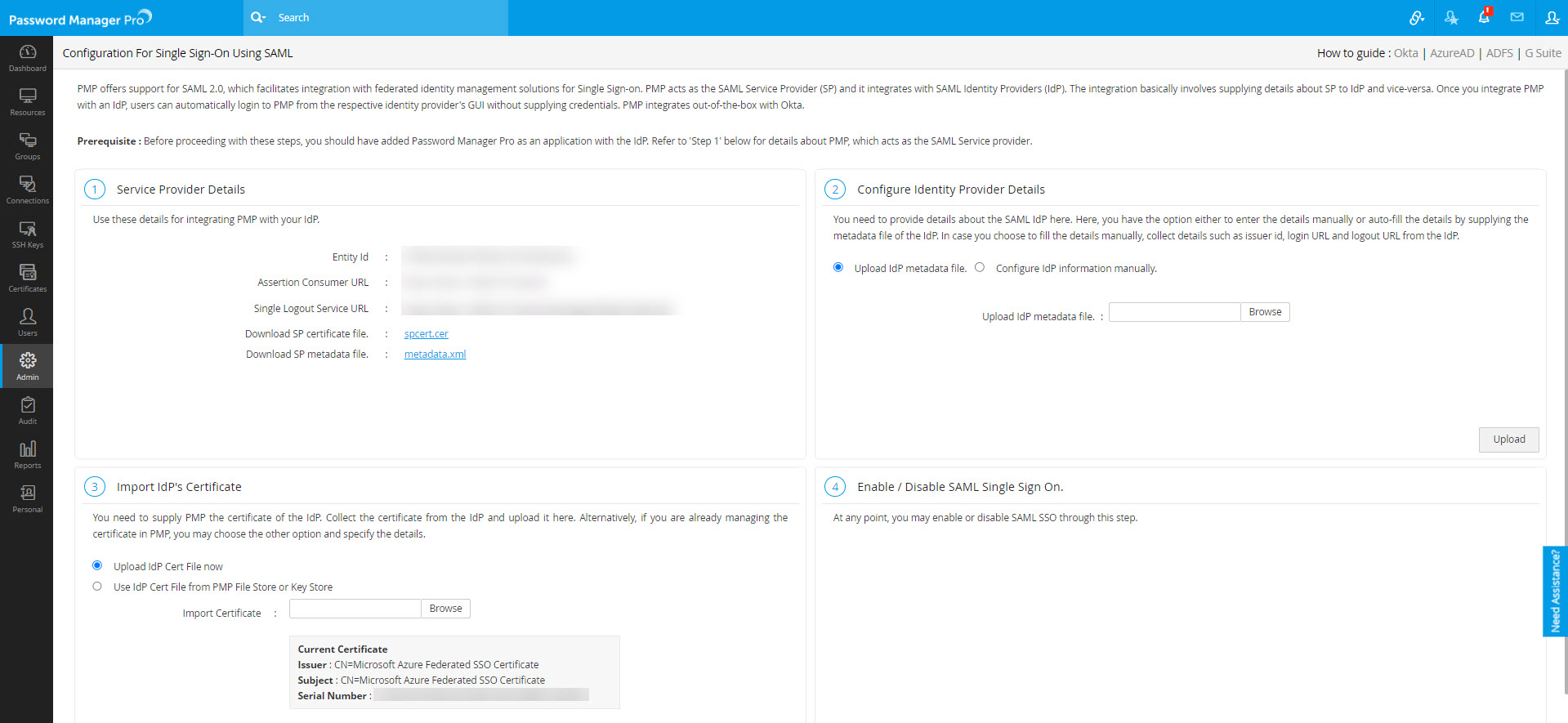
- If you have added your Idp information using the Federation Metadata XML, refresh the current page in Password Manager Pro. Now, under Import IdP's Certificate, you will see the Current Certificate details such as Issuer, Subject, and Serial Number.
- If you have added the Idp information manually, upload the downloaded Certificate (Base 64) file using the Browse option and click Save.
- For Azure SAML to function properly, go to the path: <Password_Manager_Pro_Installation_Directory\conf\system_properties.conf> and verify if the below-mentioned system properties are available in the conf file. If not, append them below the existing properties.
- Once the properties are added, restart the Password Manager Pro server for the changes to take effect.
- Finally, under Enable/Disable SAML Single Sign On, click Enable Now to activate the SAML SSO.
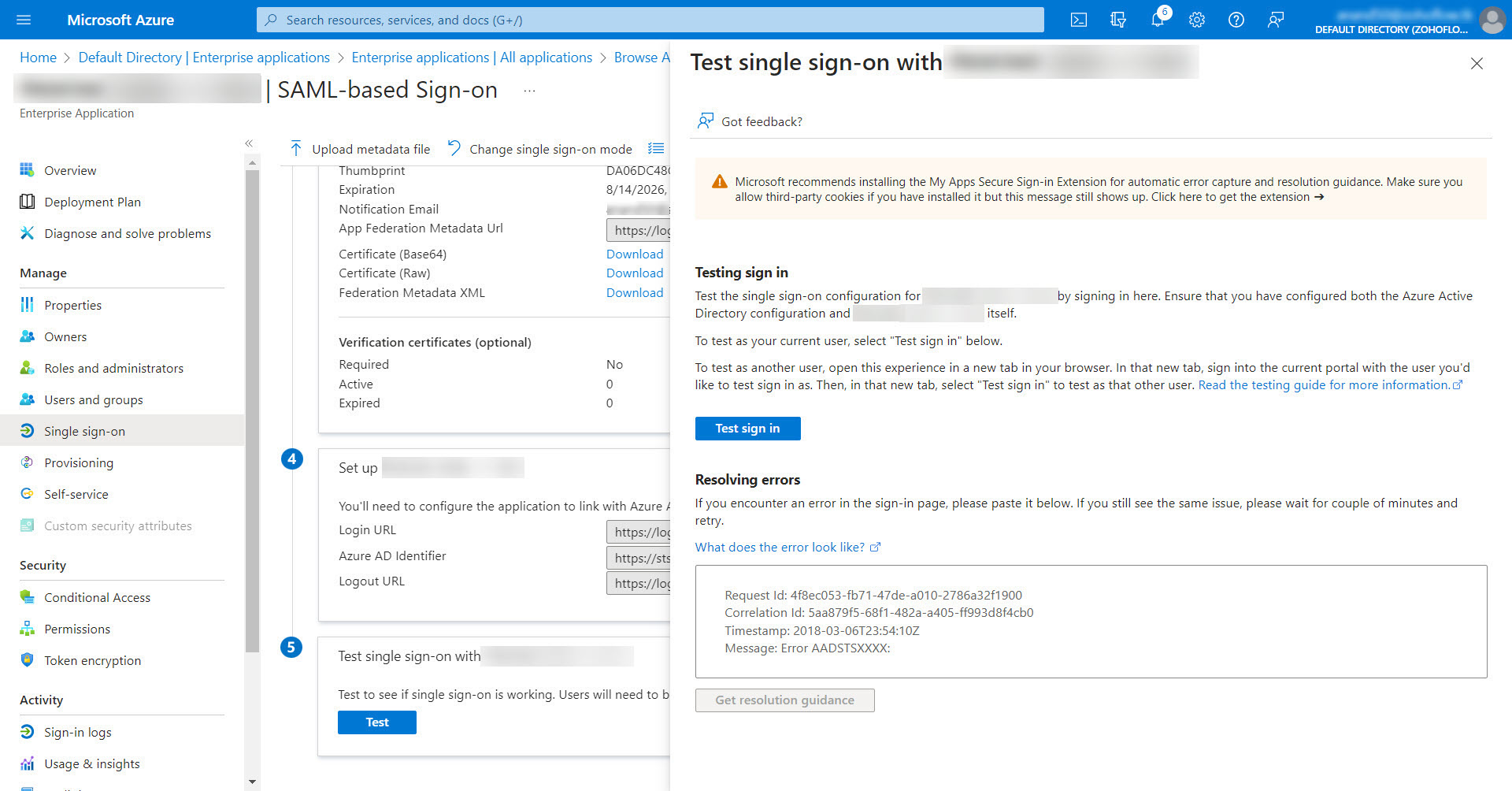
- To validate if the single sign-on works, go to the Azure portal, and in the Single sign on section under Manage, click Test.
saml.redirect.idpprotocolbindingpost=true
saml.authcontext.comparison.exact=true
saml.AuthreqForceAuthn=false
saml.nameidFormat=unspecified
saml.idp.version=1.1
saml.authnContextClassRef=Password
3. Steps to Enable MFA and Set up First Login for Entra ID Users
Below are detailed steps to activate MFA for Entra ID users in the Microsoft portal and to set up their first login.
3.i Enabling MFA for Entra ID Users
- Log in to the Microsoft Azure portal.
- Select Entra ID under Azure services.

- Under the Manage section from the left pane, select Users.
- Here, click the Per-user MFA option at the top pane. Now you will see the list of users populating in a new browser window.
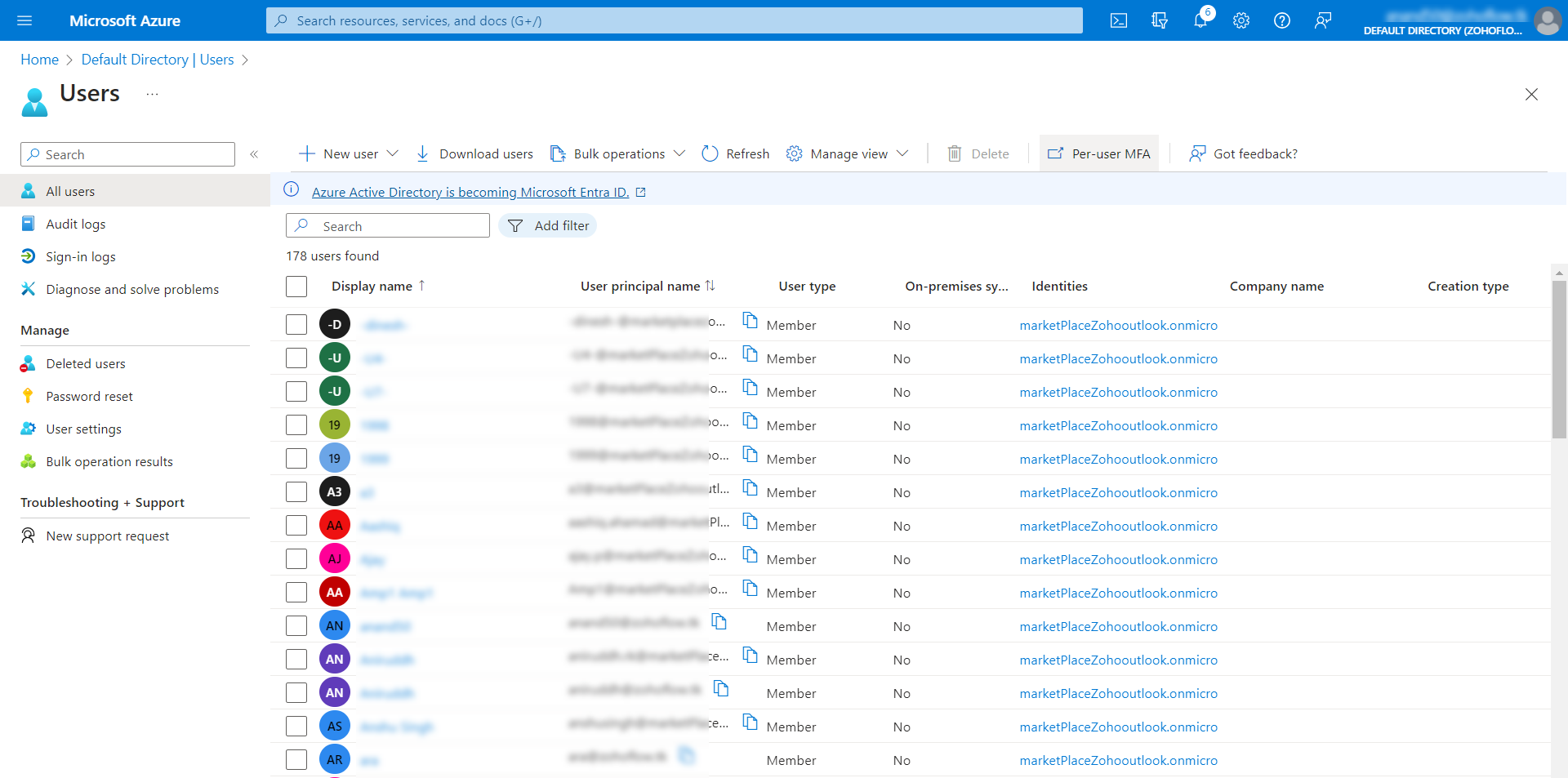
- Select the user(s) for whom you want to enable MFA and click the Enable option on the right pane.
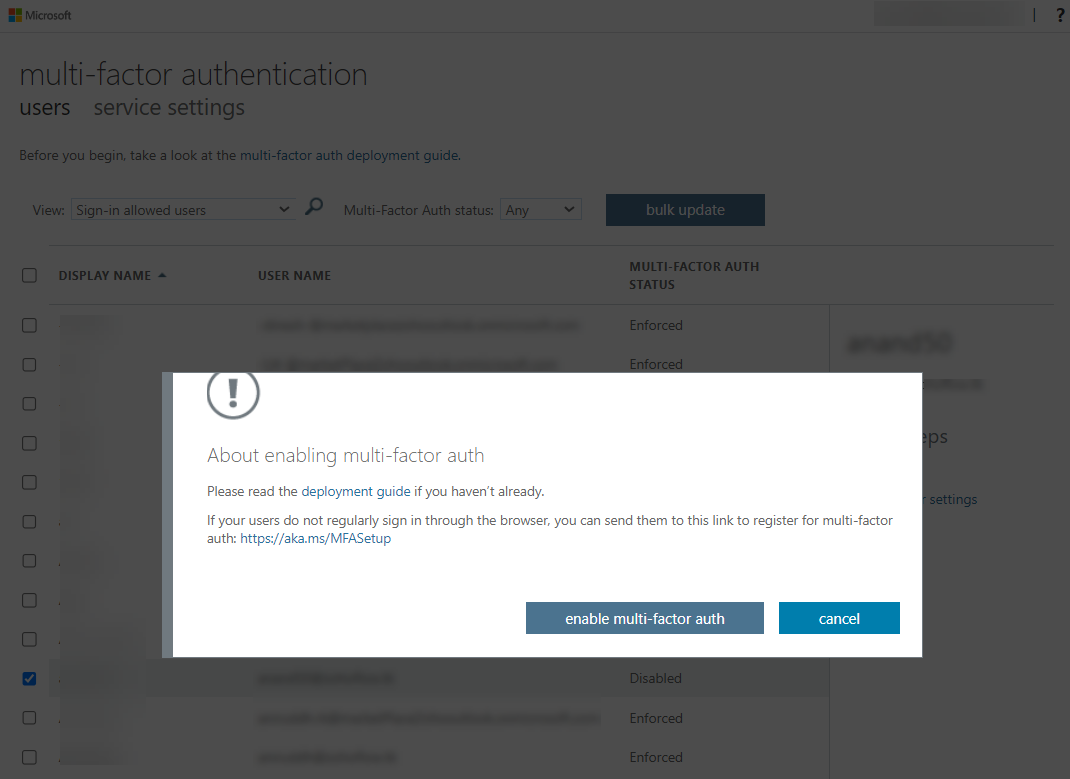
- In the pop-up that opens, click the enable multi-factor auth button to complete the setup.
3.ii Assigning Azure Users to the Enterprise Application
- Click on Entra ID and select Enterprise applications under the Manage tab.
- Search for your enterprise SAML application and then select it.
- Select Users and groups from the left pane and click the Add user/group option at the top pane.
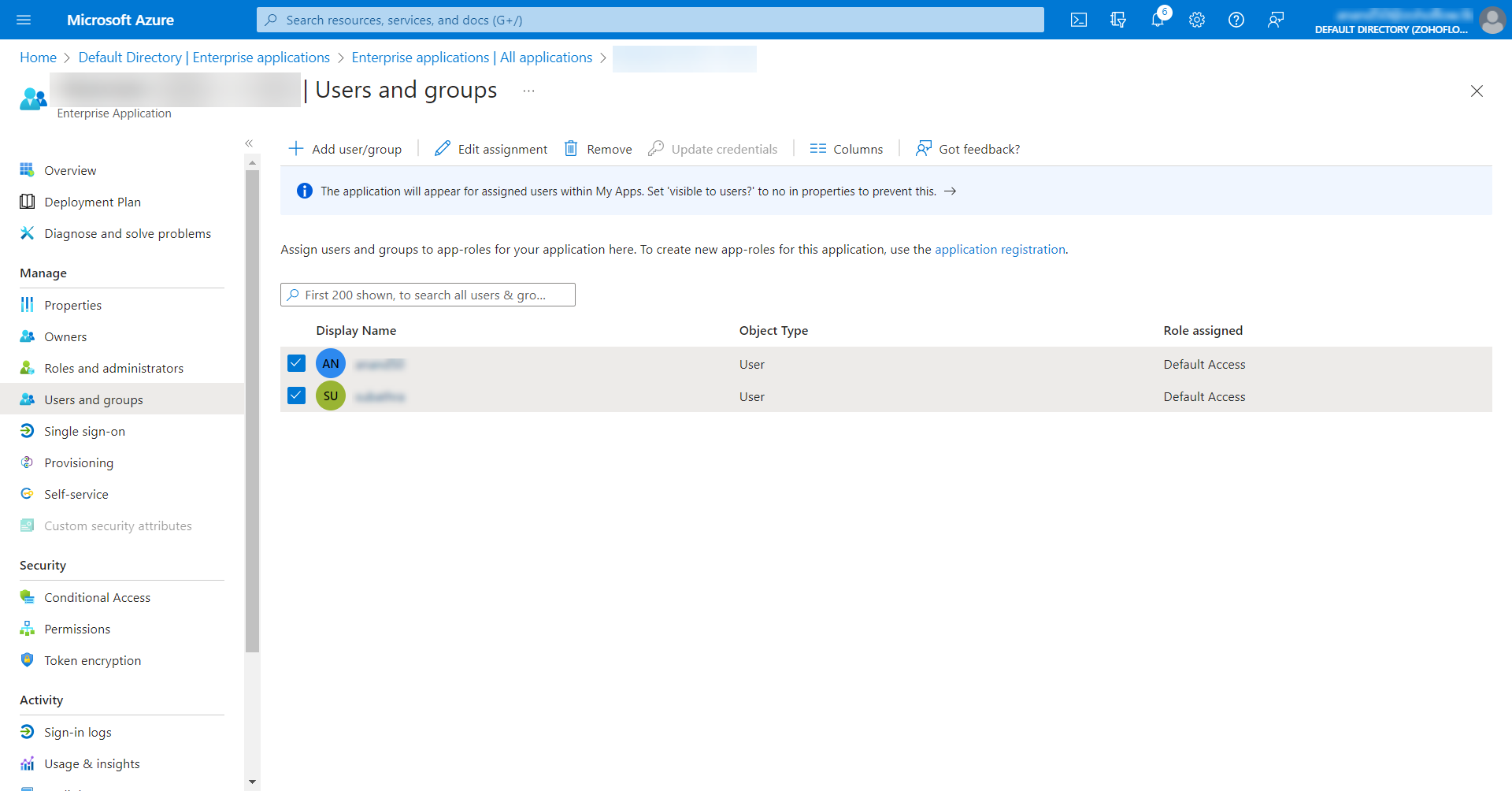
- In the Add Assignment window that opens, click on None Selected to open up a list of users. Select the required users and then click the Select button at the bottom.

- After the required users have been selected, click Assign at the bottom-left corner to assign them to the enterprise application.
3.iii. Setting Up First Login for the MFA-Enabled Azure Users
a. Prerequisite
You need to have the Microsoft Authenticator app installed on your phone for additional security verification.
b. Steps Required
Below steps are for users to set up their first login and multi-factor authentication using the Microsoft Authenticator app.
- Log in to the Microsoft Azure portal.
- Once you log in, you will be redirected to the Keep your account secure screen. Then, click Next until you see a QR code.
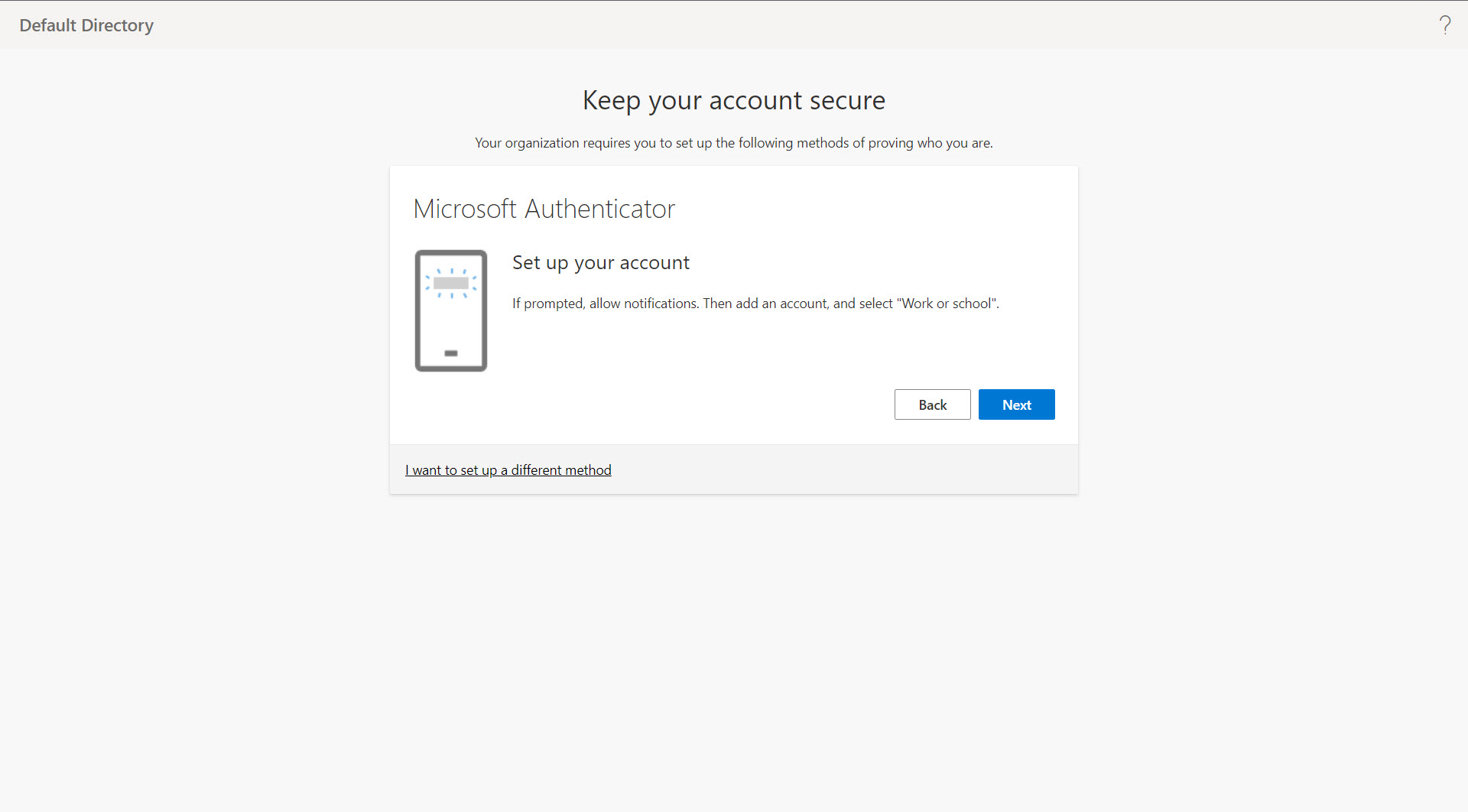
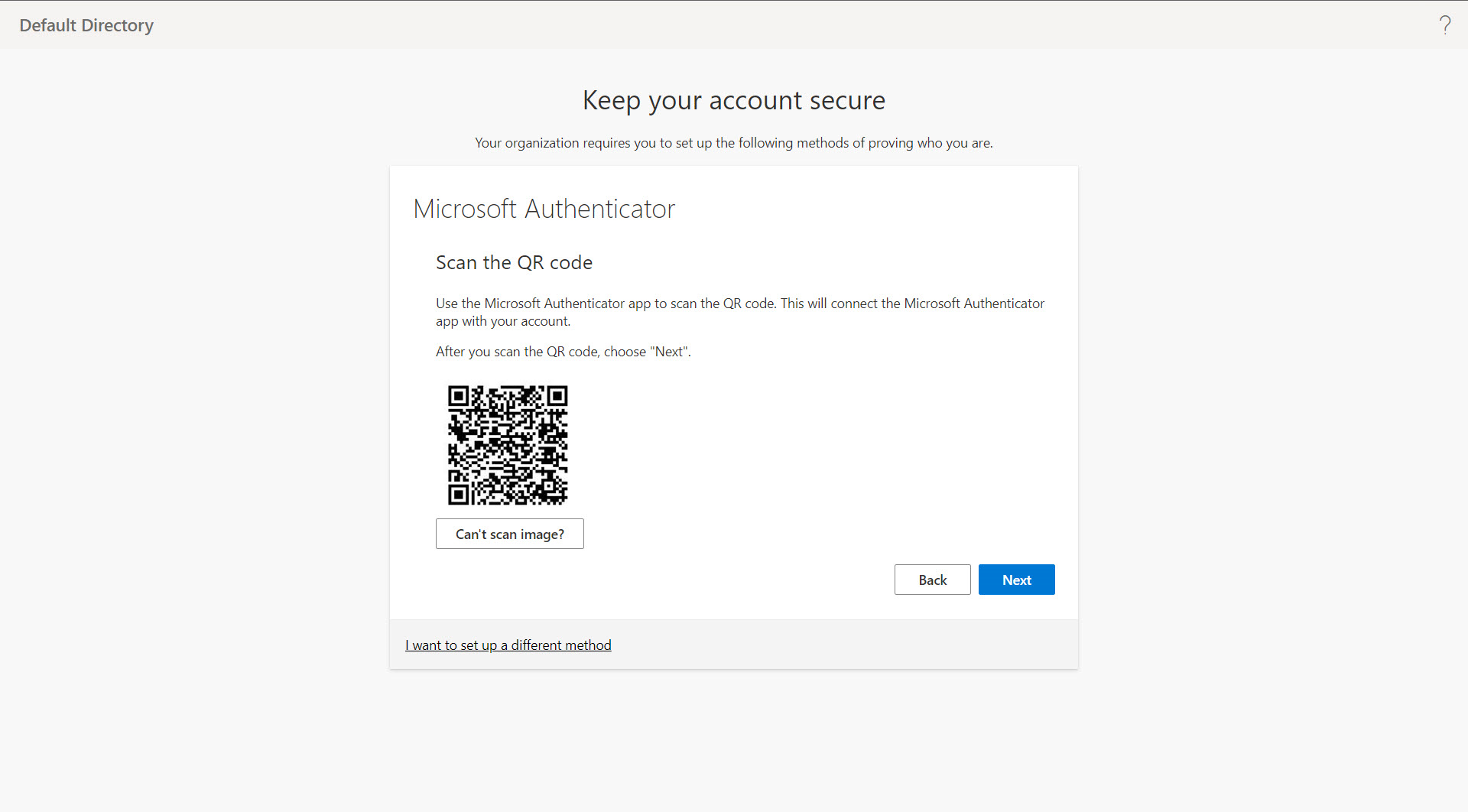
- Open up the Microsoft Authenticator app on your phone and scan the QR code shown; click Next.
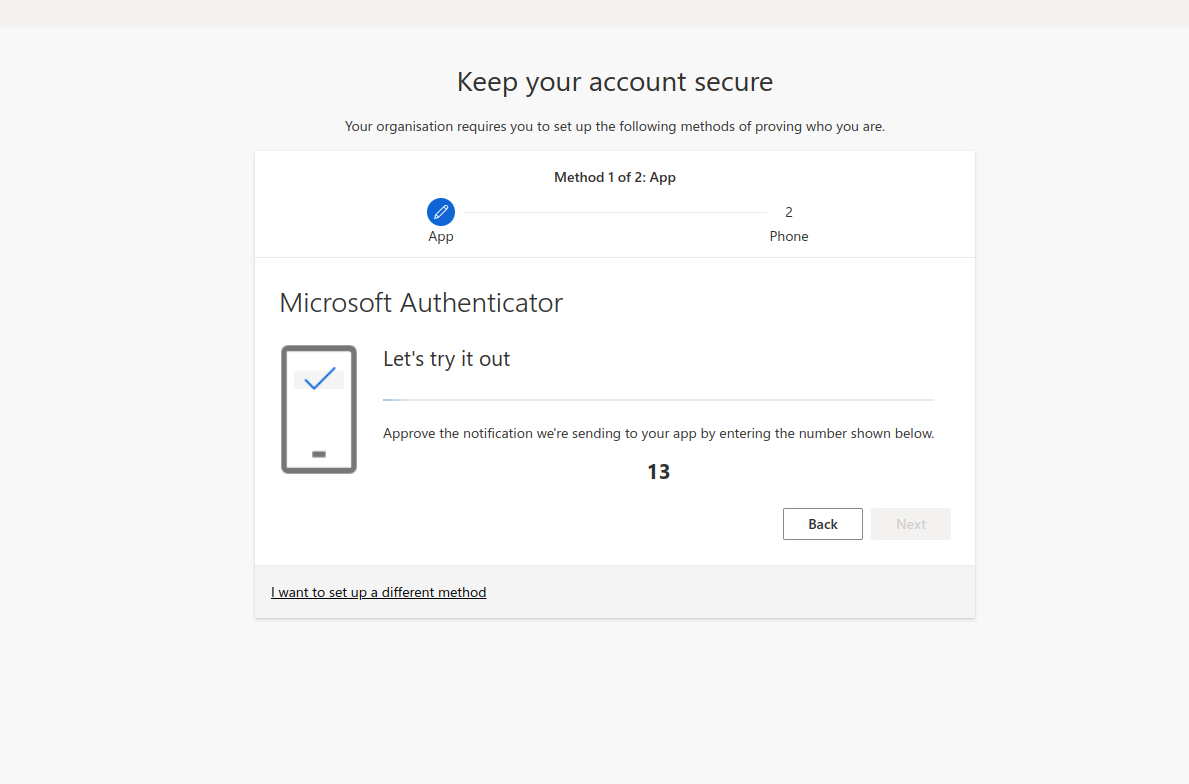
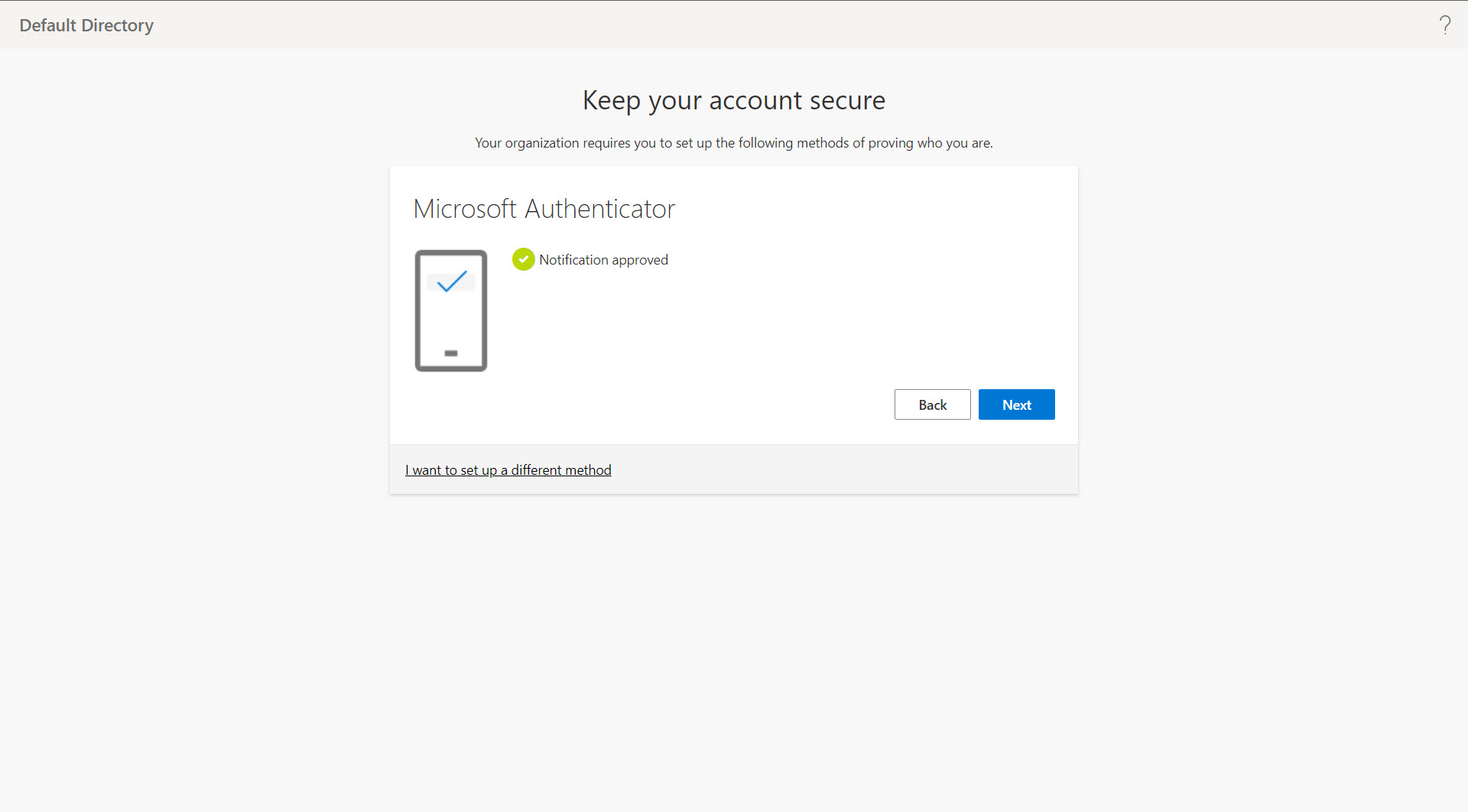
- Approve the notification that has been sent to the app by entering the number displayed on your computer screen. Once the notification is approved, click Next.
- Provide your phone number in the text field and choose either Text me a code or Call me. Click Next and complete the verification.
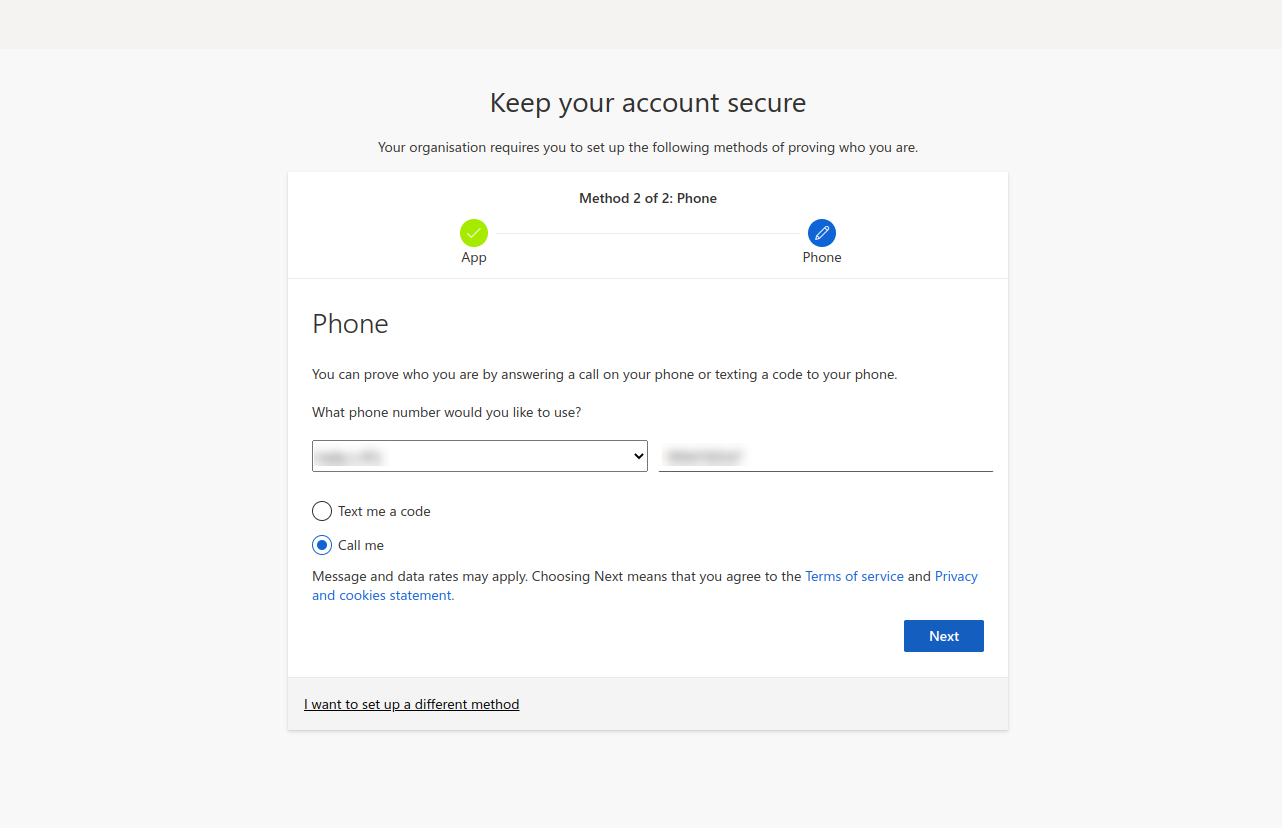
- You will get a "Success!" message. Click Done, and you will be asked to reset your password for security reasons.
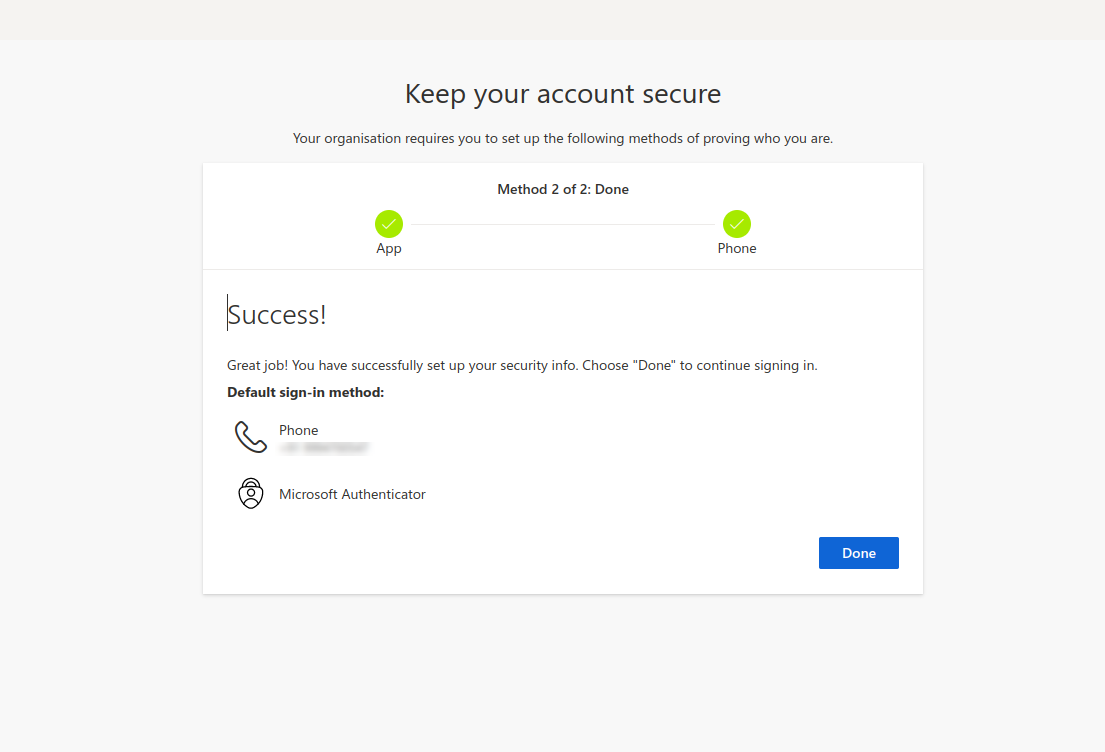
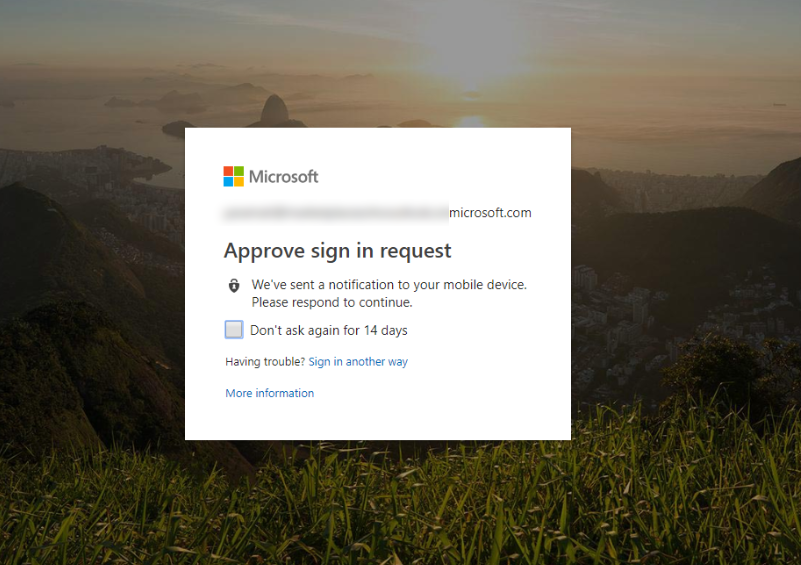
- The first login setup is complete. Now, when you try to log in to your Azure account for the first time, you will get a notification on your mobile device to verify the authenticity of your login attempt.
Note: To bypass SAML Single Sign-On and use local authentication to access Password Manager Pro, use the following skip URL:
https://hostname:port/PassTrixMain.cc?skipsamlsso=true
where,
"hostname" - the hostname on which the Password Manager Pro server is running.
"port" - the port number used for Password Manager Pro.
4. Troubleshooting Tips
The following are the few errors that can be encountered during Password Manager Pro login via Azure SAML SSO. All of those can be resolved by following the respective troubleshooting steps that follow:
1. Error: AADSTS75011
Issue: Password Manager Pro uses a Password for SAML authentication, but some browsers like Edge stores the previous session and use X509 certificates with Azure IDP, causing validation failure due to authRequest mismatch.
Solution:
To resolve this, remove AuthnRequest elements from Entra ID by:
- Navigating to <Password_Manager_Pro_installation_directory>\conf folder.
- Adding the system property saml.AuthnContextRequired=false to system_properties.conf file with administrator privilege.
- Restarting the Password Manager Pro server for changes to take effect.
2. Error: AADSTS750054
Issue: Incorrect configuration of SAML Single-Sign-On and SAML assertion consumer URL in the enterprise application.
Solution:
Update respective URLs with the valid input:
- Open the Password Manager Pro enterprise application in Microsoft Azure.
- Go to Single Sign On under Manage.
- Ensure correct URLs are set for the Sign On URL (Password Manager Pro web portal URL - https://hostname:port) and Reply URL (SAML assertion consumer URL - https://hostname:port/saml2).
3. Error: AADSTS7000218
Issue: SAML authentication failure due to the Password Manager Pro enterprise application being created as a confidential client, preventing username/password authentication.
Solution:
Configure enterprise app as PUBLIC client:
- Log into the Microsoft Azure portal, and open the Password Manager Pro enterprise application.
- Under Manage, click Authentication.
- Change from Web to Public client/Native.
- Select Default Client Type as YES.
- Ensure required API permissions are granted and consent is given under the Permissions section.
Note: If you have multiple redirect URLs, you need to make the necessary changes in all of them.
4. Error: AADSTS75005
Issue: Azure IdP doesn't support HTTPS REDIRECT binding protocol.
Solution:
Enable HTTP POST binding protocol:
- In the Password Manager Pro console, go to Admin >> Authentication >> SAML Single Sign-On.
- Choose Configure IdP information manually under the Configure Identity Provider Details section.
- Change the Protocol Binding to HTTP-POST, then save the changes.
5. Error: ADSTS50105
Issue: The user lacks access to PMP/Password Manager Pro app in Entra ID.
Solution:
Ensure the user is assigned to the Password Manager Pro enterprise application. The user must belong to an assigned group or be directly assigned to the Password Manager Pro enterprise application. Refer to the relevant help section for steps to assign users to the app.
By following these steps, you can effectively troubleshoot and resolve common login errors when using Password Manager Pro with Azure SAML SSO.
6. Error: [com.adventnet.passtrix.saml.SAMLResponseValidator]|[SEVERE]|[78]: SAML Signature could not be validated|
org.opensaml.xml.security.SecurityException: SAML Signature could not be validated
Issue: Could not able to validate the SAML signature
Solution:
Update the binding protocol in Password Manager Pro to HTTP-POST:
- In the Password Manager Pro console, go to Admin >> Authentication >> SAML Single Sign-On.
- Choose Configure IdP information manually under the Configure Identity Provider Details section.
- Change the Protocol Binding to HTTP-POST, then save the changes.
7. Error: [com.adventnet.passtrix.saml.SAMLServlet]|[SEVERE]|[56]: No user with name XXXXX@yyyyy.com configured|
org.opensaml.xml.security.SecurityException: No user with name XXXXX@yyyyy.com configured
Issue: SAML authentication fails due to a mismatch in user names. This occurs when the username stored in Password Manager Pro does not match the login name configured in Azure SAML.
Solution:
To address this, the solution involves creating a new claim ID in Azure that aligns with the login name format stored in the Password Manager Pro database. Refer to this help document to create a new claim and the complete the relevant configuration.