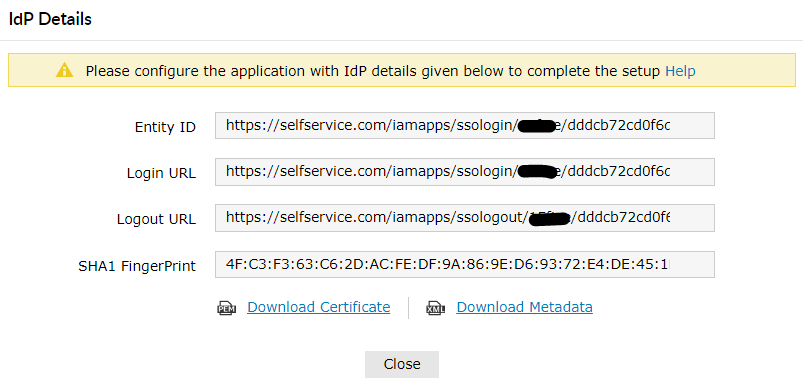
These steps will guide you through setting up the single sign-on functionality between ADSelfService Plus and ServiceNow.
Navigate to Manage → Instance.
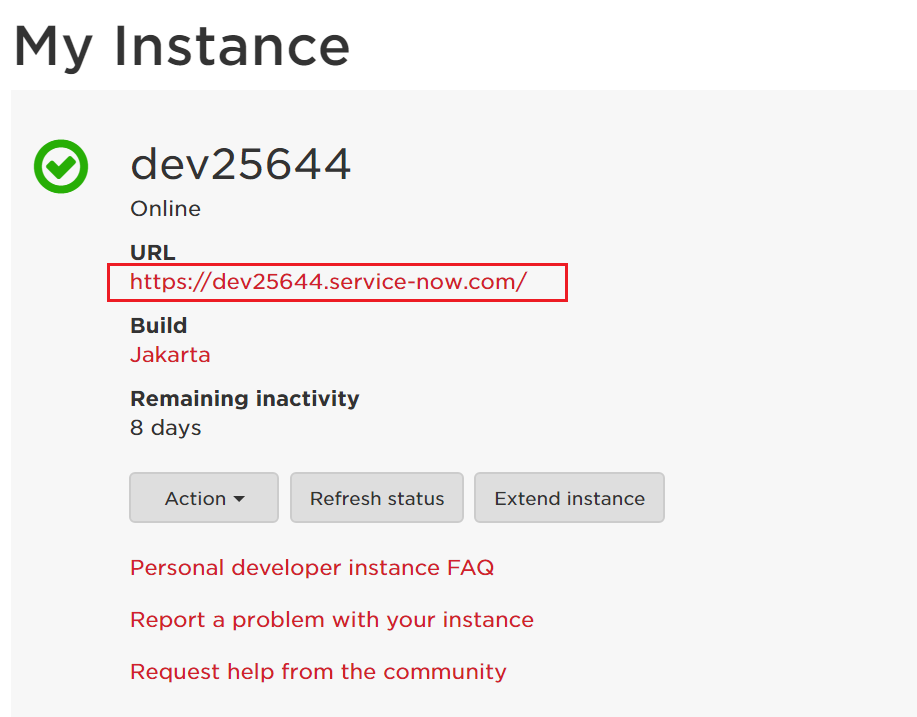
In the My Instance page, click on the instance URL. Also, note down this value. We will need it while configuring ServiceNow with ADSelfService Plus.
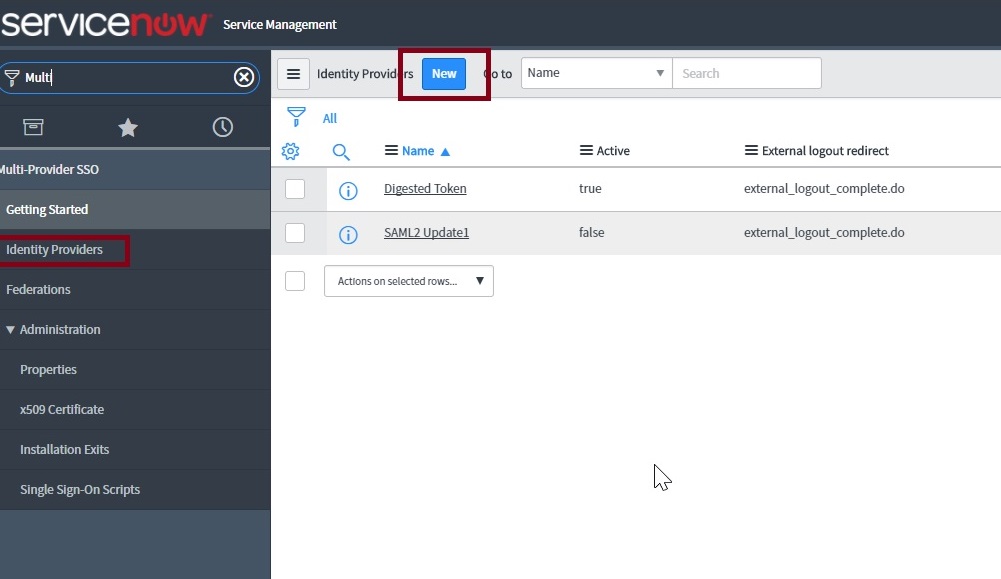
In the What kind of SSO are you trying to create? section, select SAML
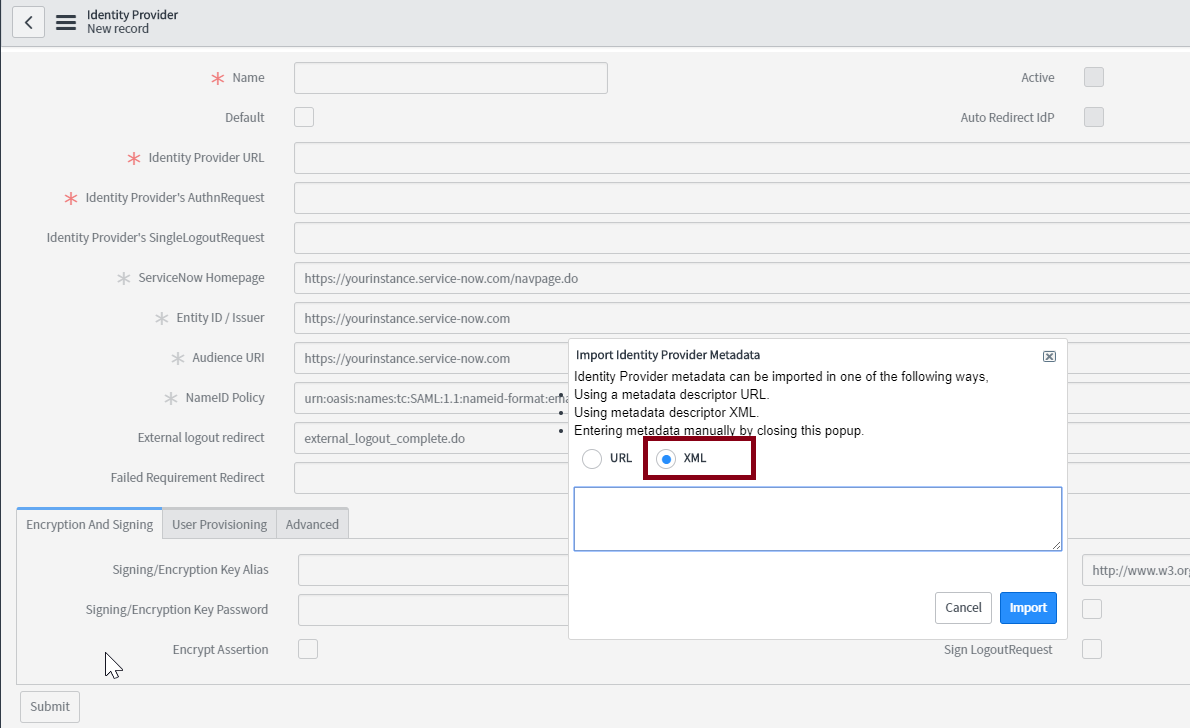
In the Import Identity Provider Metadata pop up that appears, select XML and paste the XML file content you had copied in Step 4 of Prerequisite.
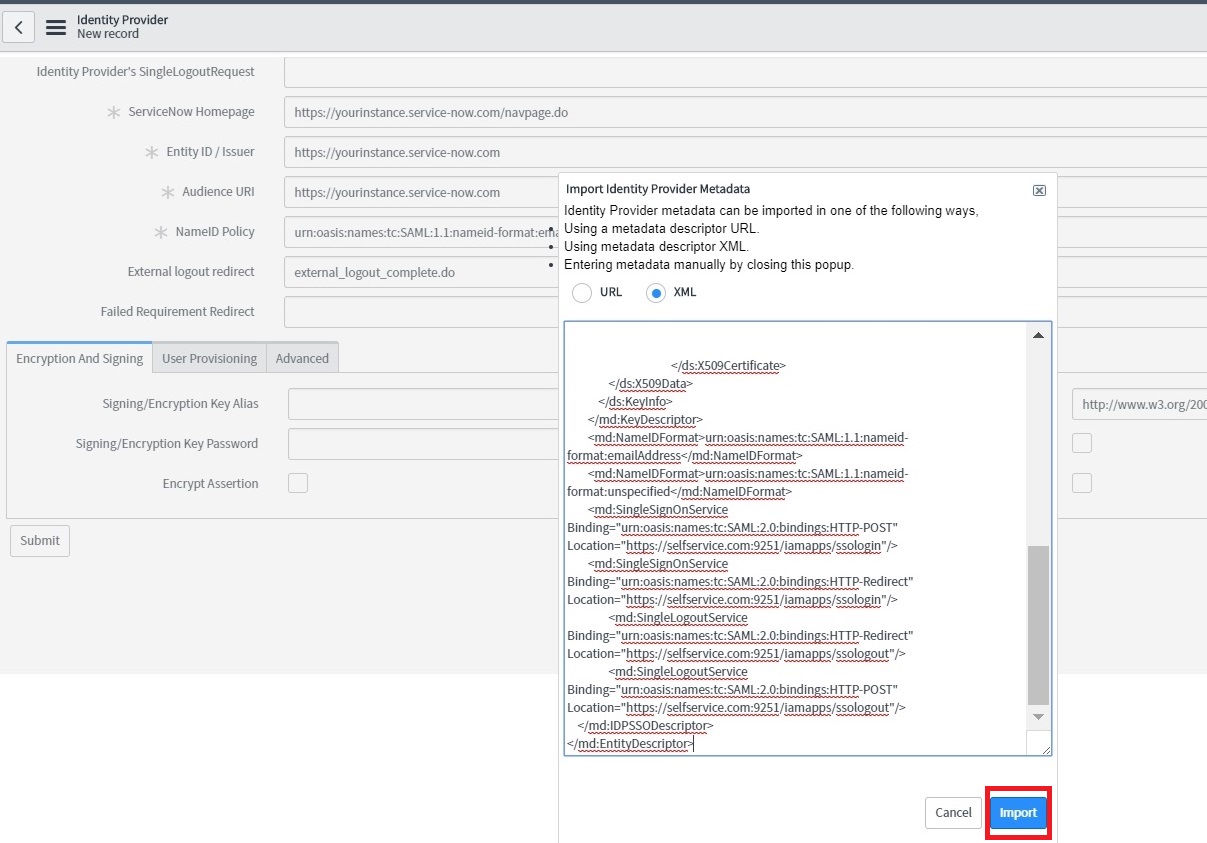
Click Import.
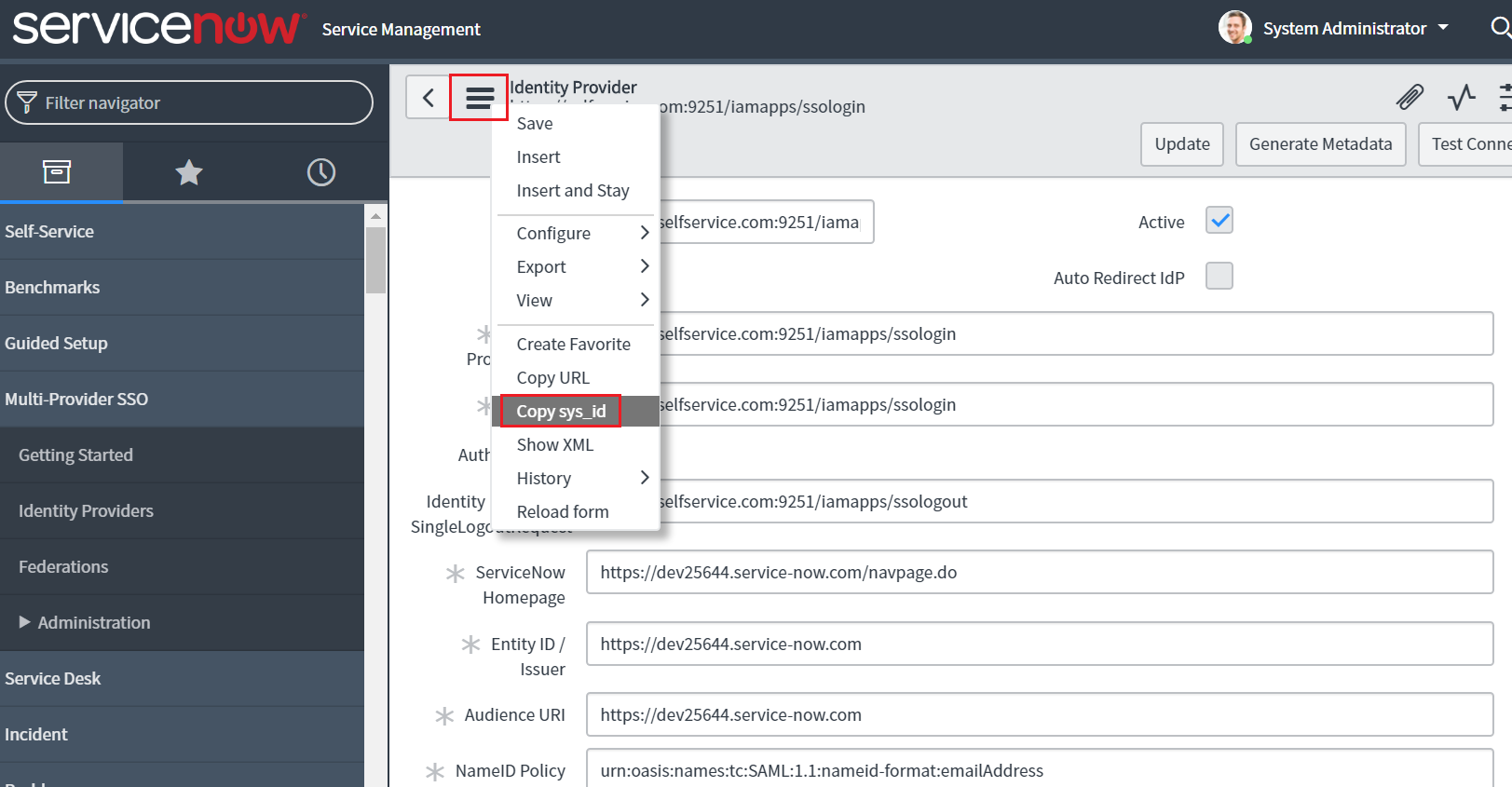
All the required fields will be auto-filled. Scroll down and click Advanced tab. Make sure in the User Field, the value “email” is entered.
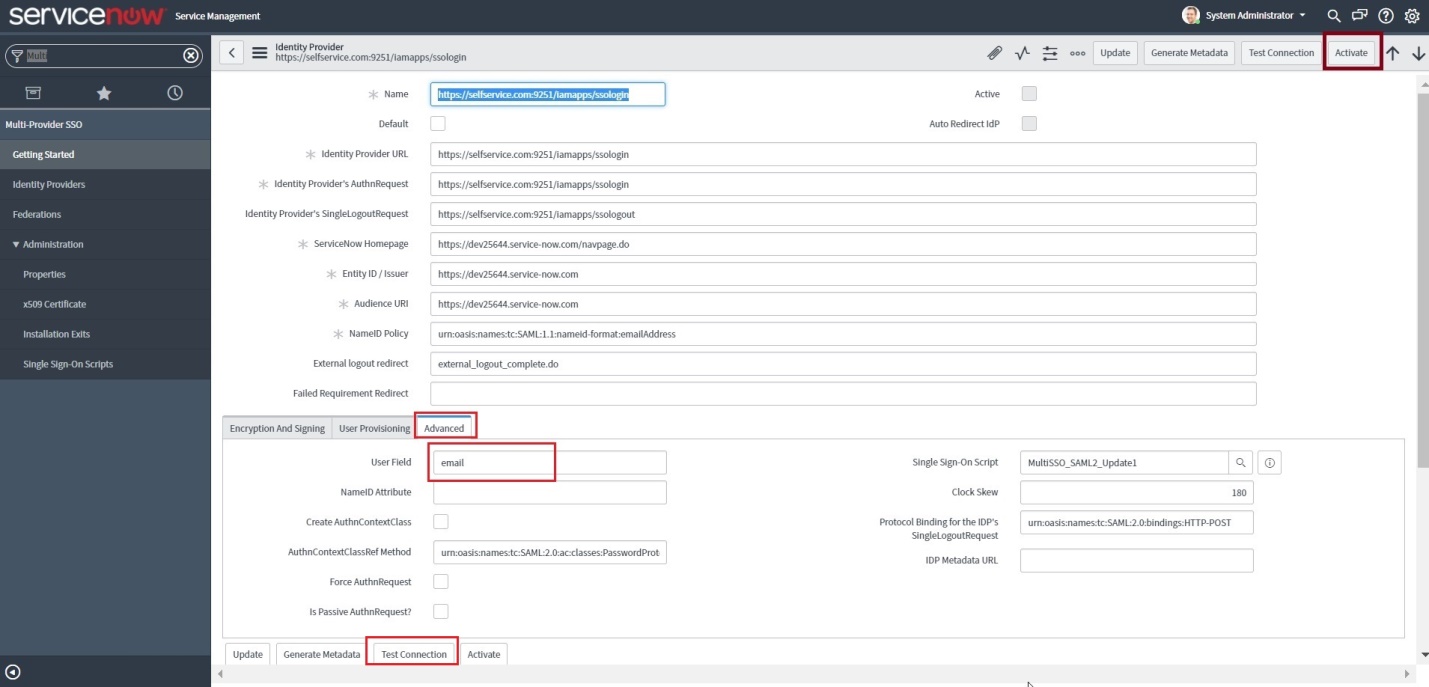
Now click on the Additional Actions icon at the topnear the identity provider and select Copy sys_id. Paste the value in a note and keep it safe.
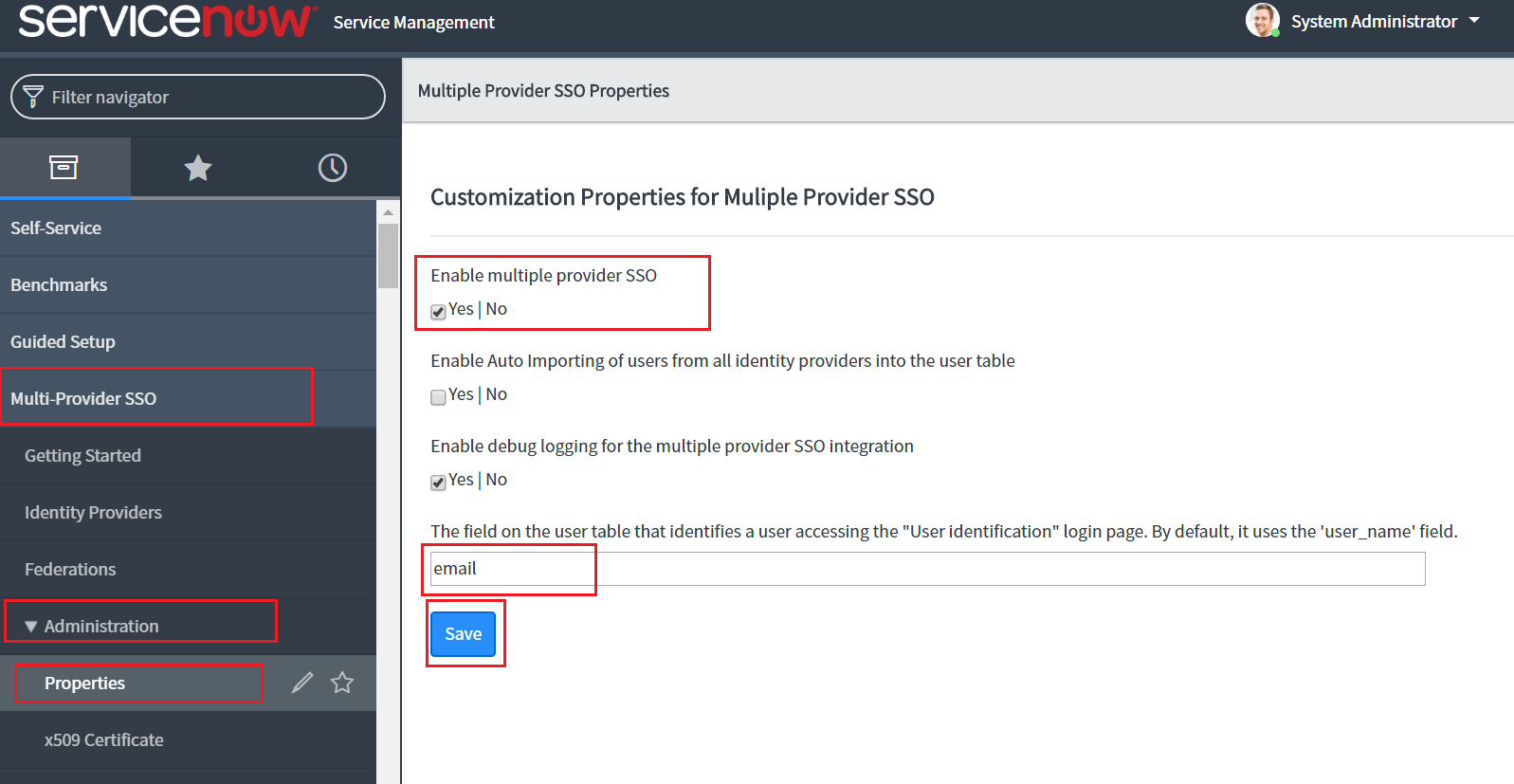
In the field for user identification, change ‘user_name’ to email as the value.
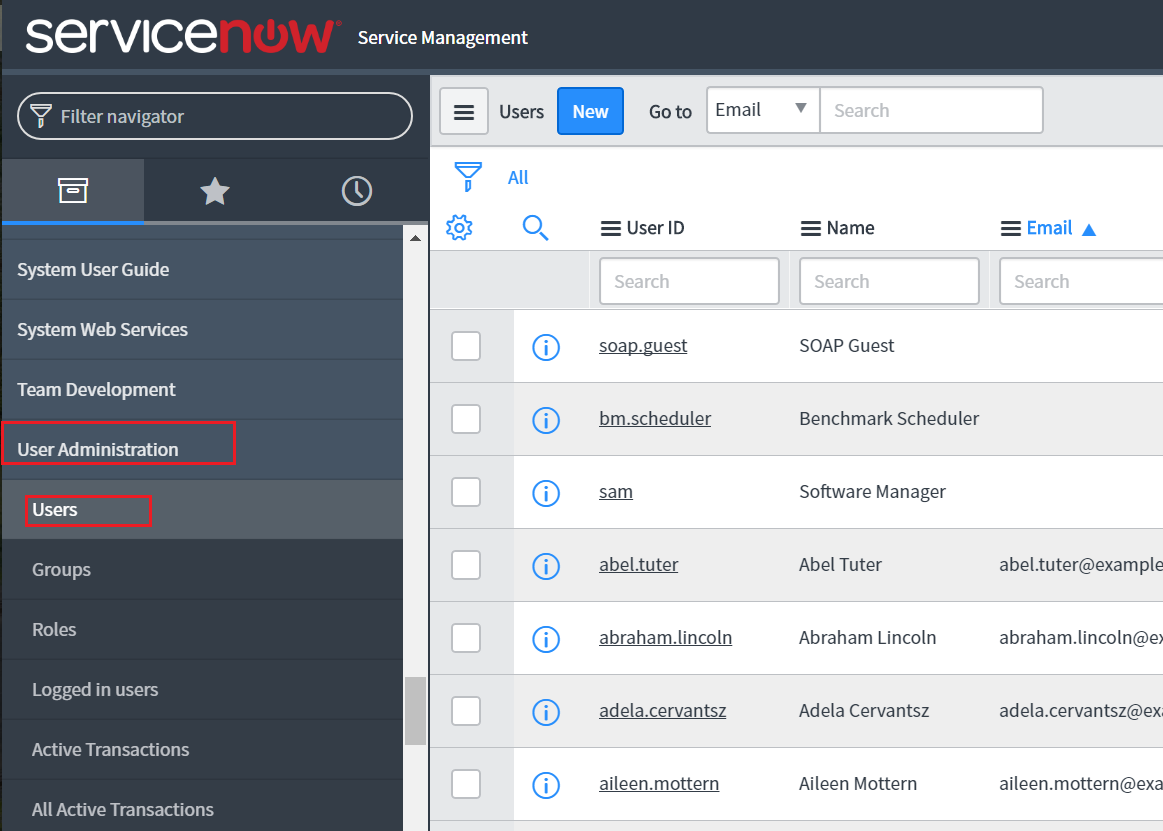
In the left pane, navigate to User Administration → Users.
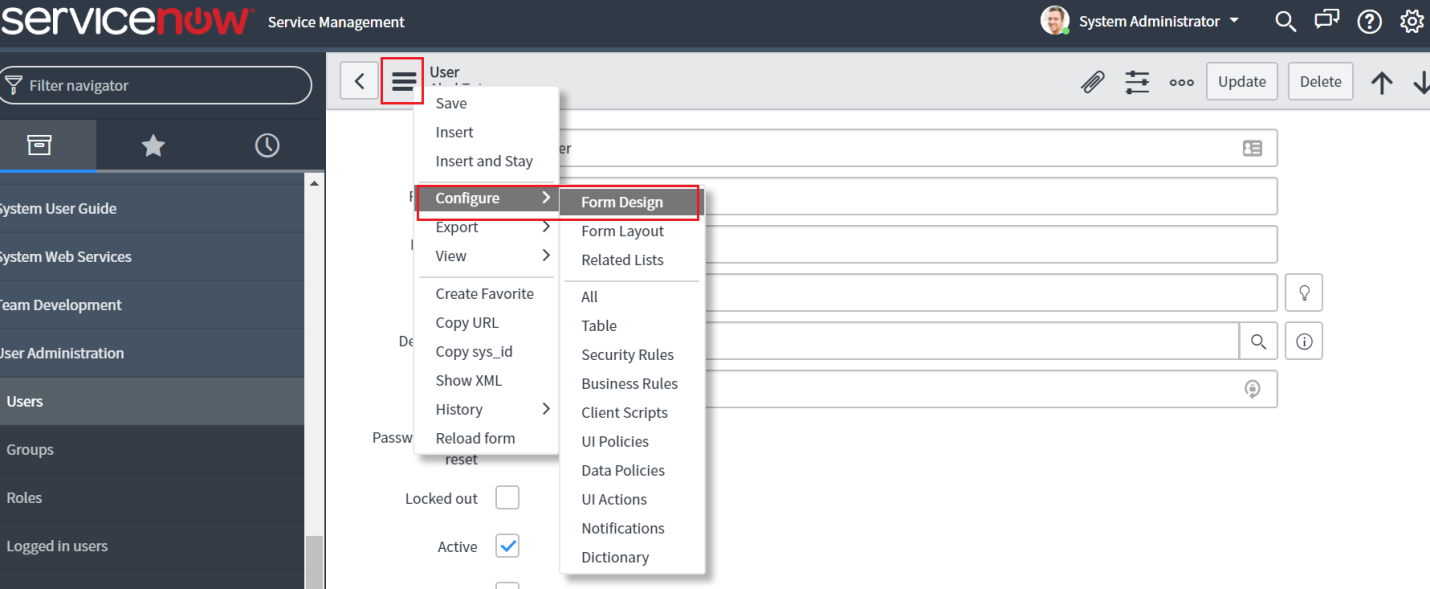
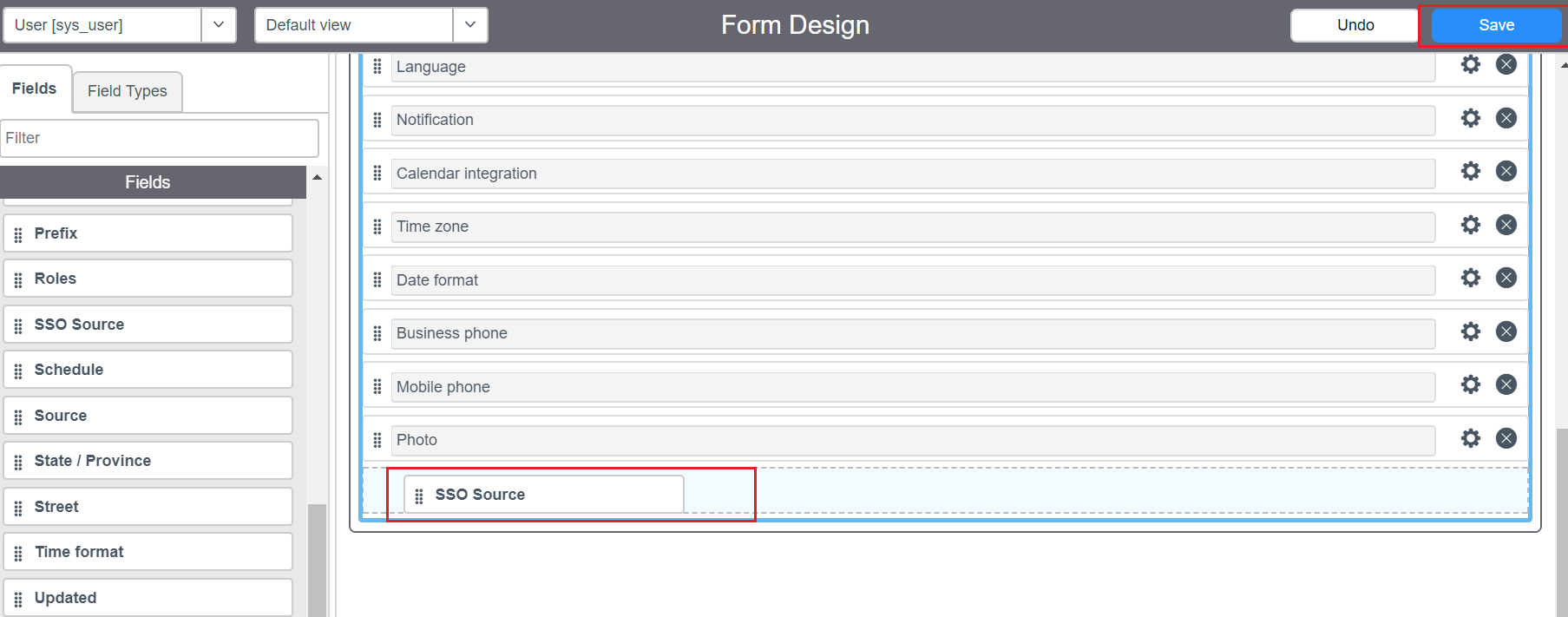
Now click the Additional Actions icon and select Configure → Form Design.
Drag and drop the SSO source field from the left pane into the user’s form and click Save.
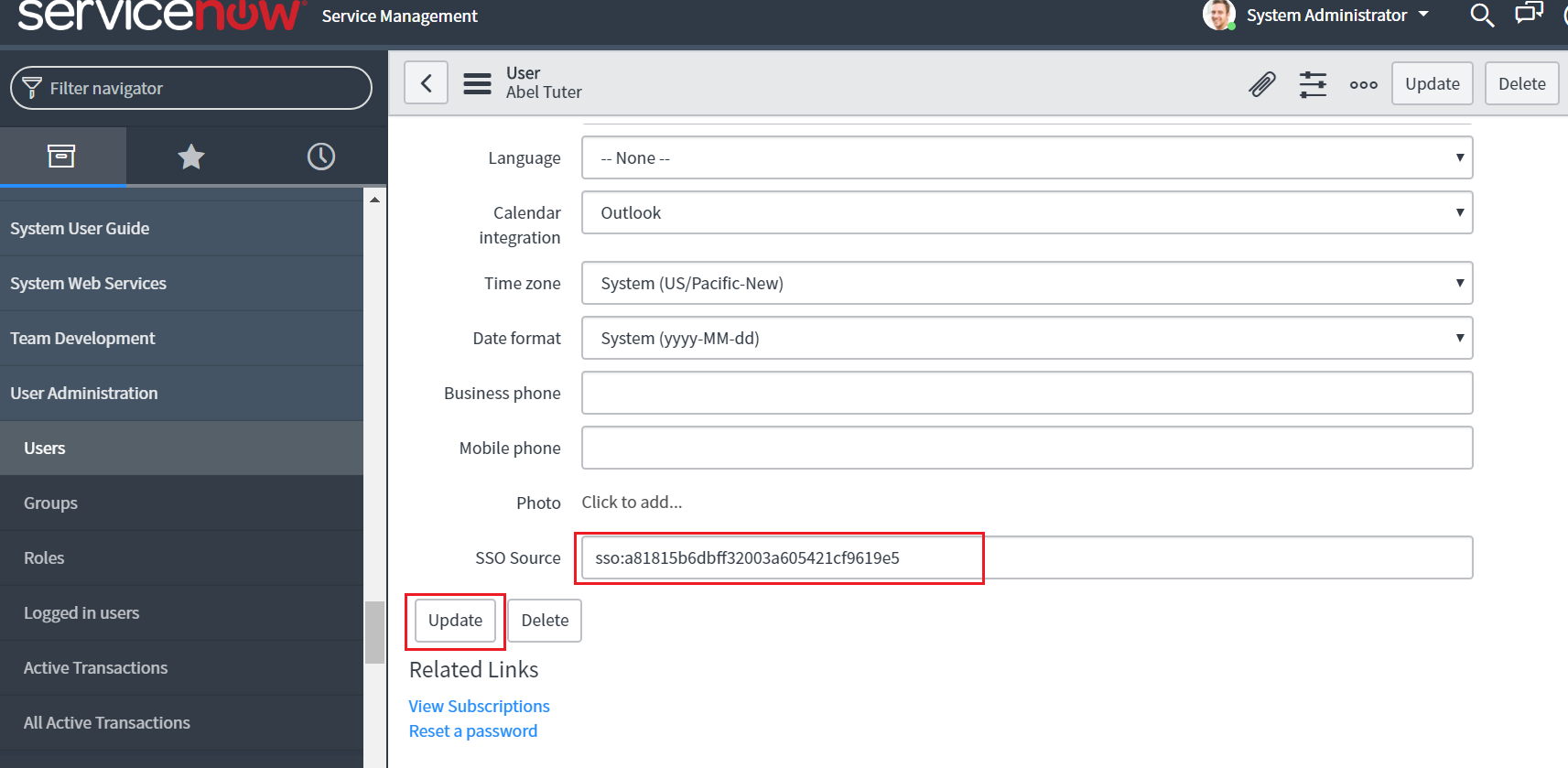
In the SSO source field, paste the sys_id you had copied in Step 11. Append “sso:” before the sys_id value.
Note: Use Unspecified as the default option if you are unsure about the format of the login attribute value used by the application
Your users should now be able to sign in to ServiceNow through ADSelfService Plus.
Your request has been submitted to the ADSelfService Plus technical support team. Our technical support people will assist you at the earliest.
Copyright © 2025, ZOHO Corp. All Rights Reserved.