Configuring Okta as the Identity Provider
-
Log in to your Okta domain.
-
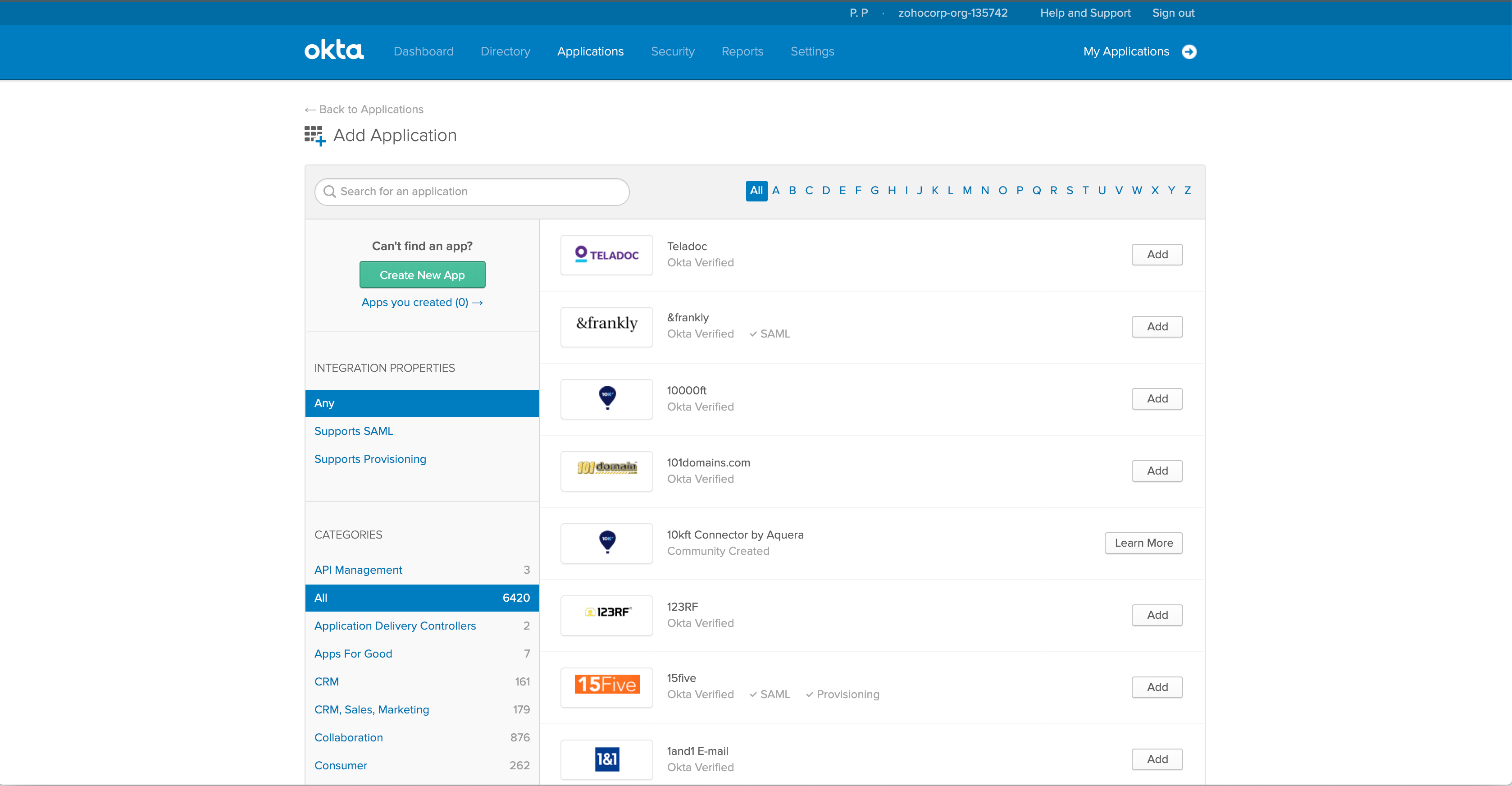
Go to the Applications >> Add Application.
-
Click Create New App.
-
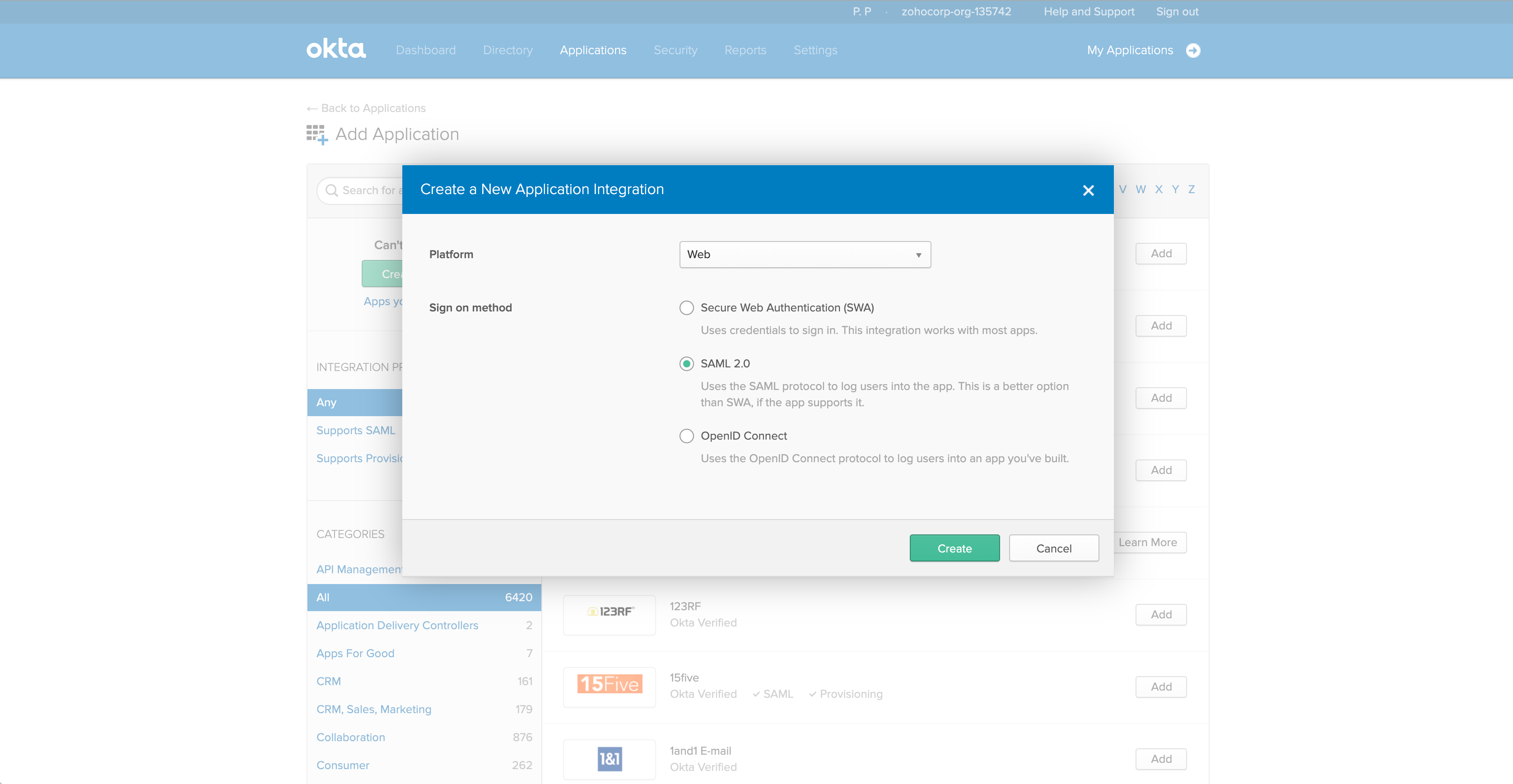
From the displayed dialog box, choose SAML 2.0 as the sign-on method.
-
Click Create.
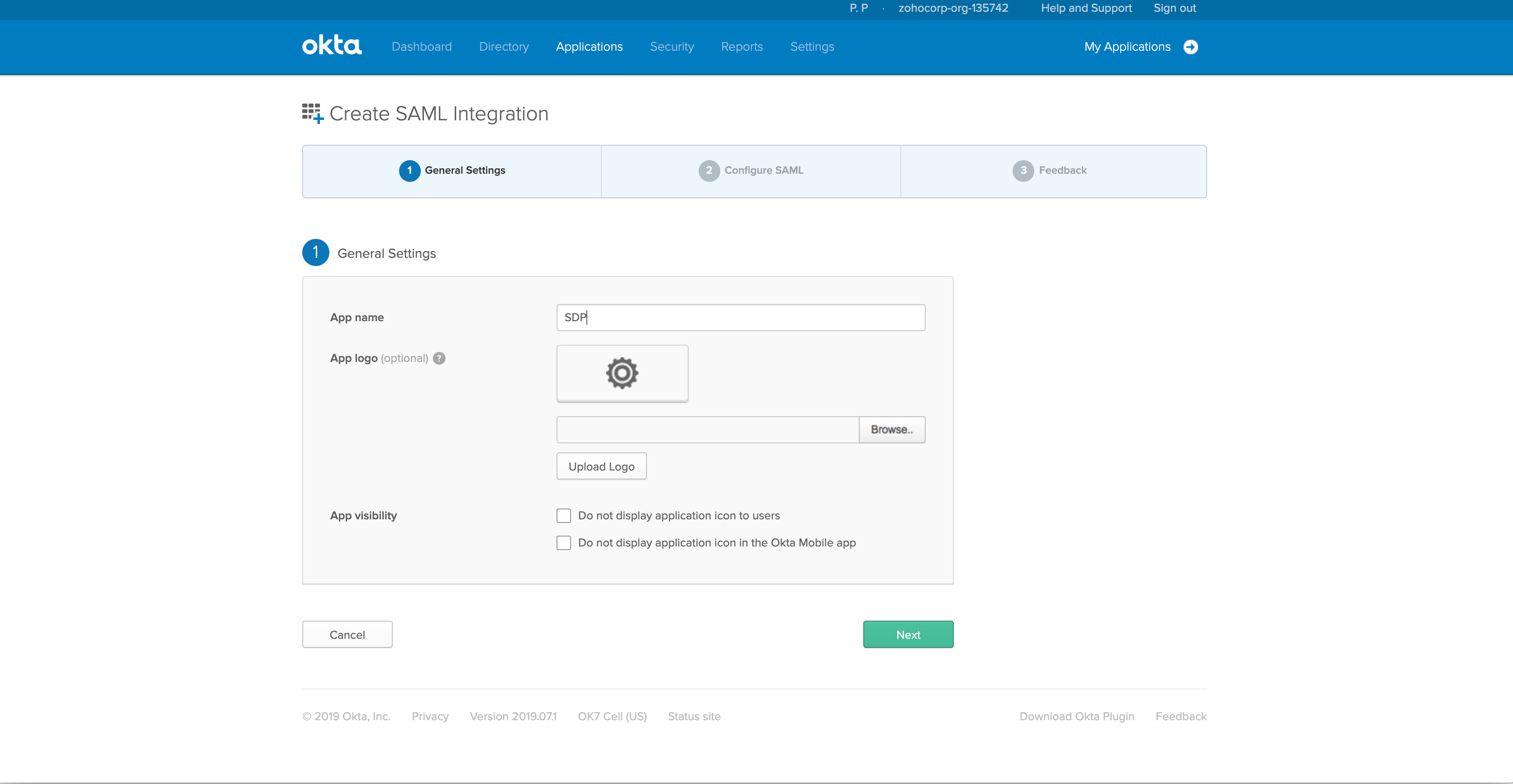
- In the next window, provide a Name for your application.
- Upload the Logo of the application and click Next.

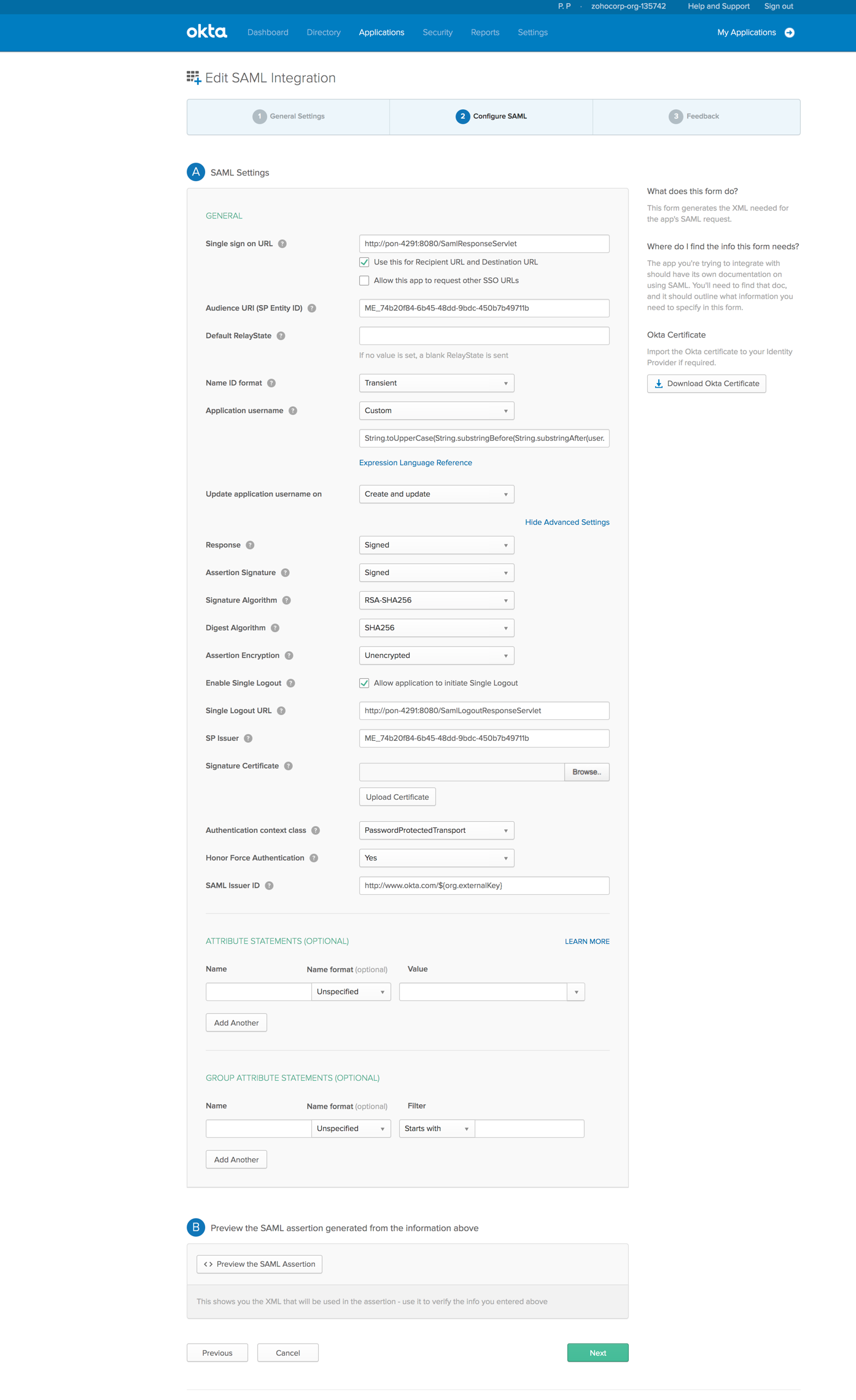
- In the displayed page, enter the Assertion Consumer URL of ServiceDesk Plus MSP under Single Sign-On URL.
- Enter the Entity ID in the Audience URI field and choose transient as the Name ID format. Currently, ServiceDesk Plus MSP supports Transient, Persistent, and Email Address as Name ID formats.
- To login using your username and domain, select Transient or Persistent.
- To login using your email address, select Email Address.
- Choose the Application user name from the drop-down menu. The login name for a new user added into the application will be generated based on the format configured here.
Note:
Ensure that the attribute chosen here matches the login name generated for a new user in ServiceDesk Plus MSP.
In addition, if the user is under a domain, Okta must return the user name with the domain name in the <domain name\user name> format.
If these conditions are not satisfied, it can lead to redundant user addition. - Click Advanced Settings.
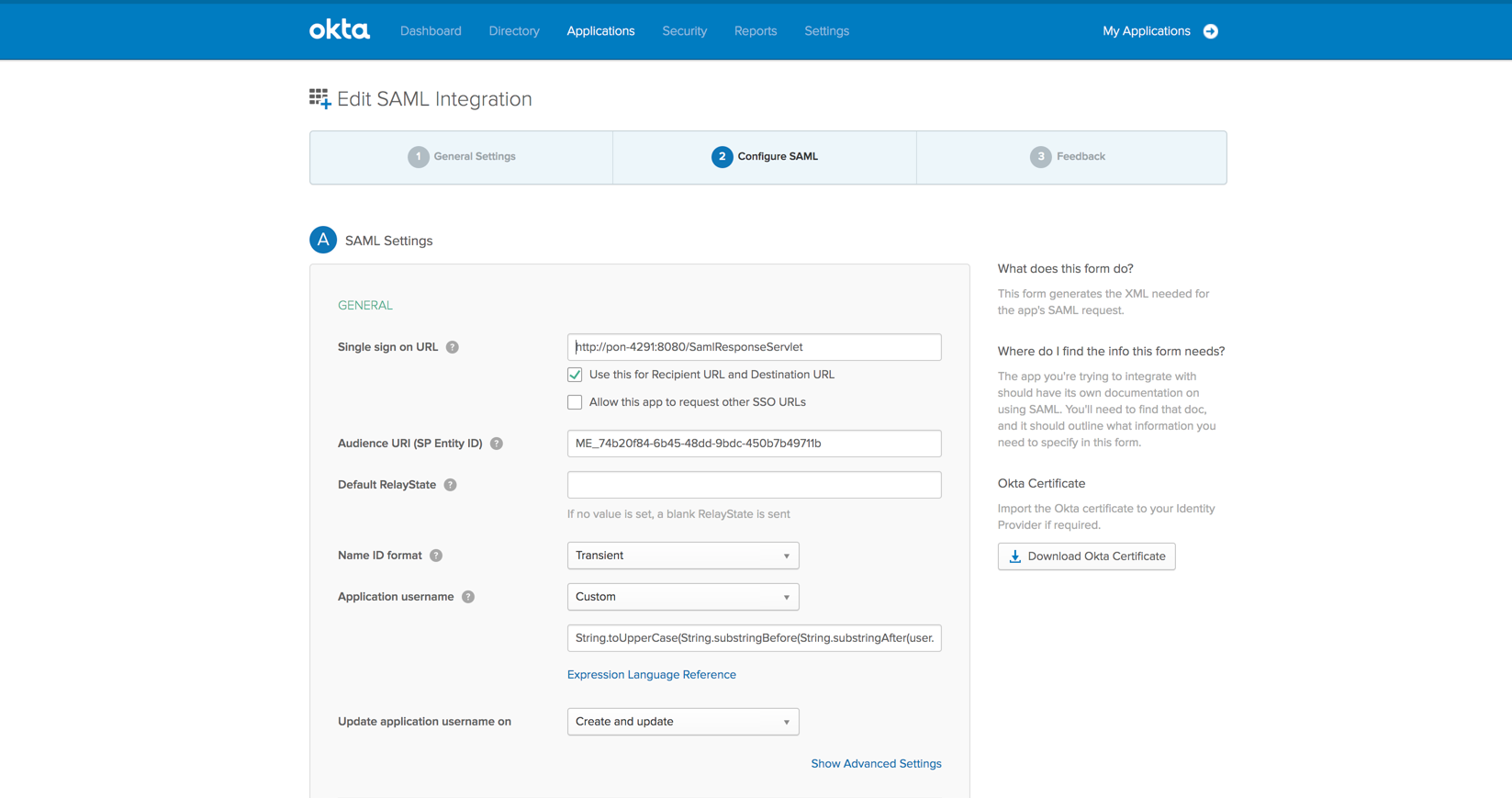
- To enable the SAML logout service, select Allow the application to initiate Single Logout.
- Provide the Single Logout URL and add the entity ID in SP Issuer.
- In Signature Certificate field, click Browse and upload the SP Certificate of ServiceDesk Plus MSP.
- Click Next.
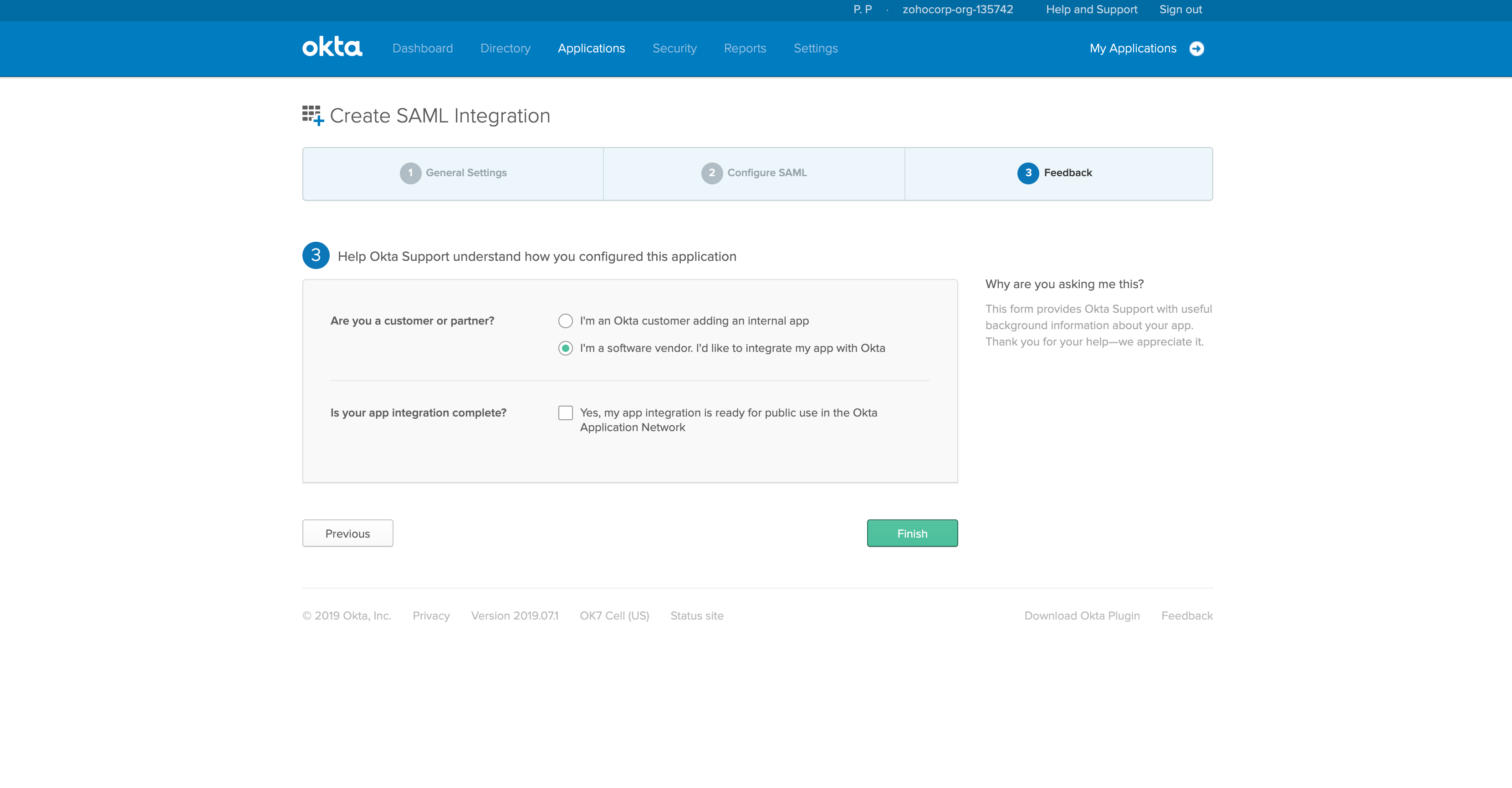
- Choose the option, I'm a Software Vendor. I'd Like to integrate my app with Okta.
- Click Finish.
Now you have configured ServiceDesk Plus MSP as an application.
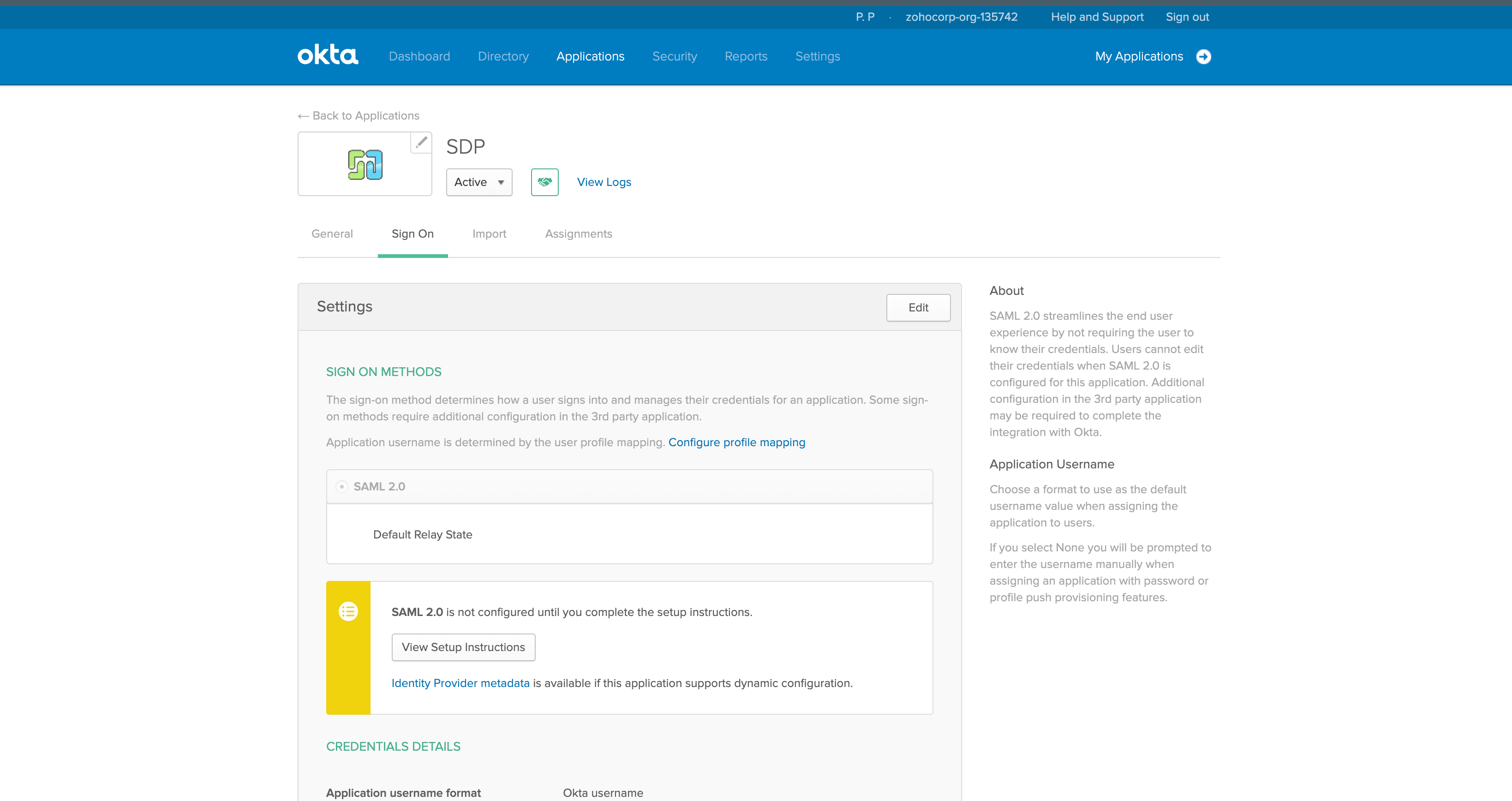
-
Go to the Sign On tab and click View Setup Instructions.
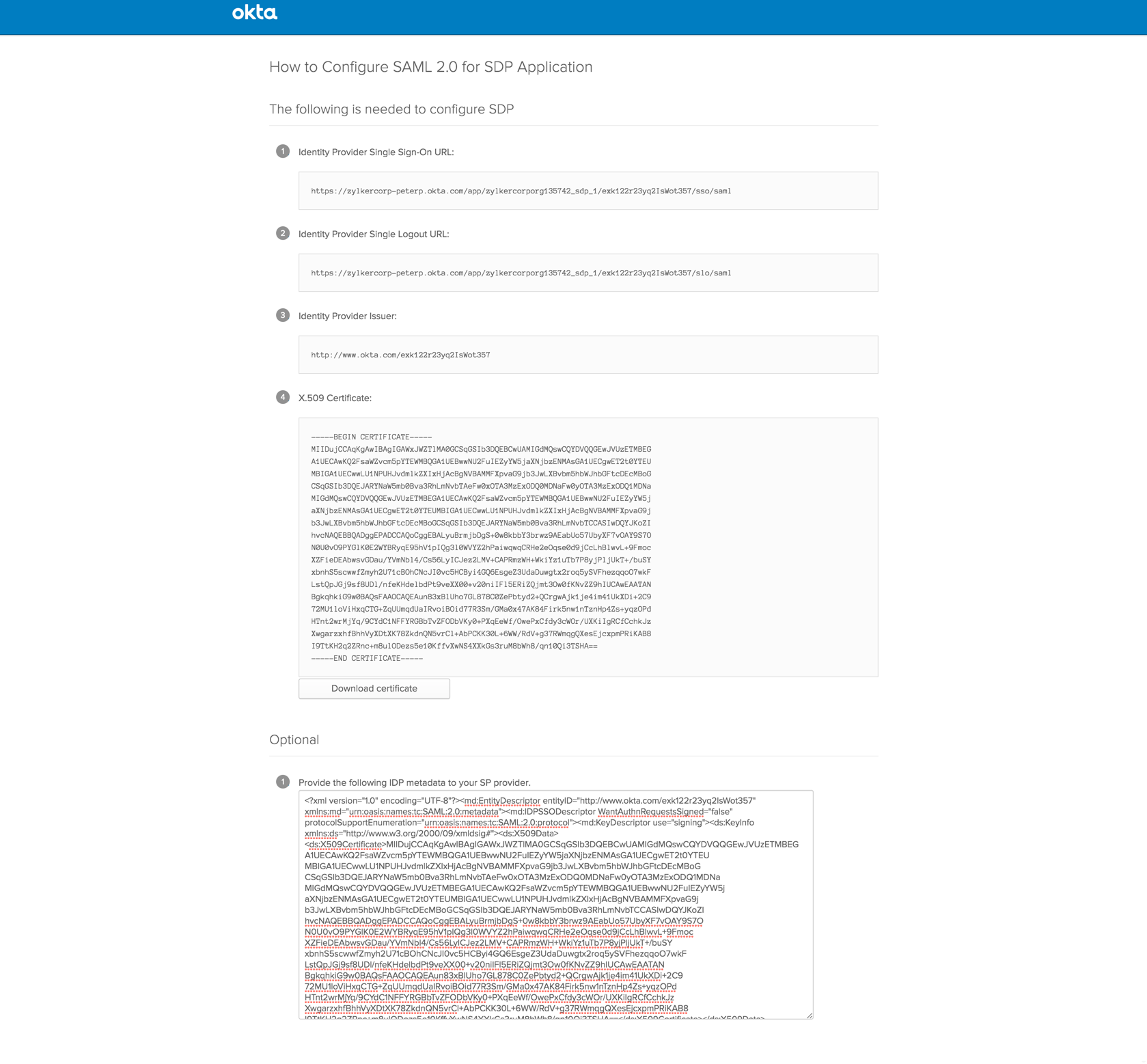
- Another tab with the IdP configurations such as Login URL (Single Sign-On URL), Logout URL (Single Logout URL), and the certificate file will be displayed. Use these to integrate with the IdP.
- Assign the application to people/groups from the Assignments tab, as shown below.
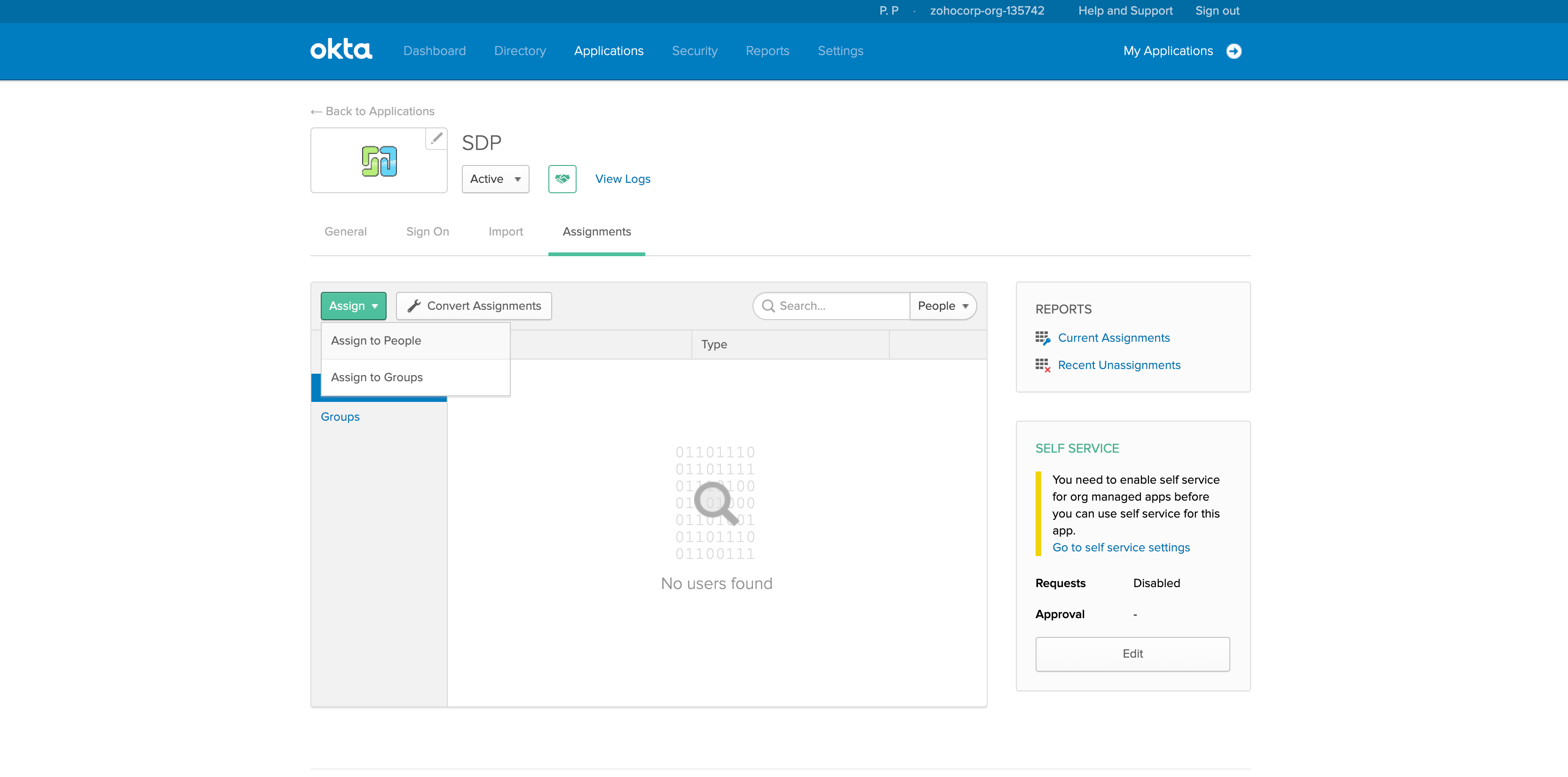
You have now configured ServiceDesk Plus MSP as a service provider in Okta.
Go to the SAML configuration page in ServiceDesk Plus MSP and provide the IdP details to complete the integration.

