Audit policy
Written by Sakthi Sri, IT security team, ManageEngine Updated on August 2025
What is audit policy in Windows?
The Audit Policy feature in Windows helps you establish a security auditing system for your local computer or the entire Windows network. Technically, it is a collection of settings that you can use to tell a Windows computer or domain server the type of security events you want to be scrutinized. When those events occur, every little detail about them is recorded in the machine's security logs for your review. An audit policy, which is built by considering all possible security risks, will effectively yield data that helps you identify security breaches early on.
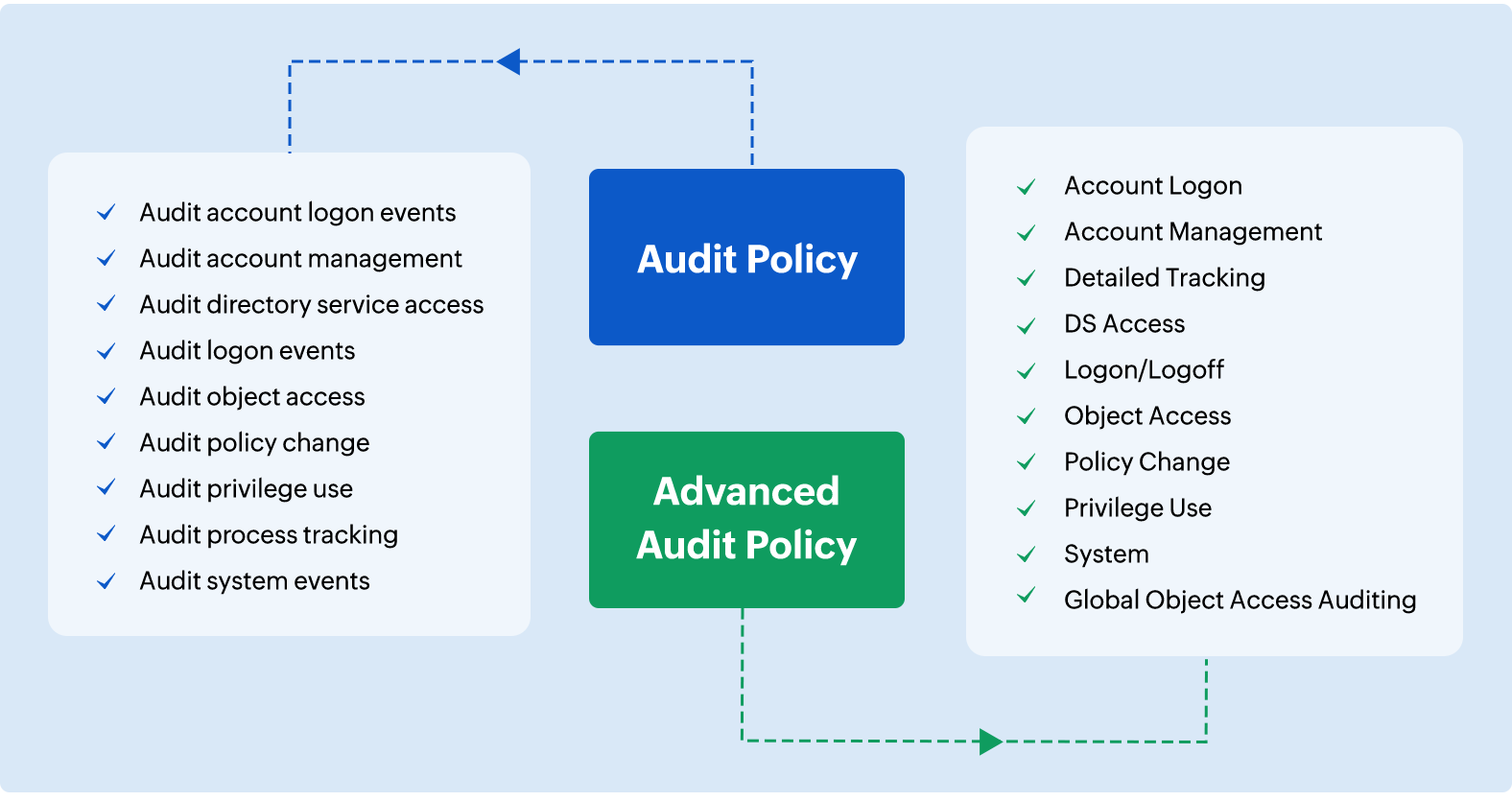
Windows audit policy comes in two flavors:
- Basic audit policy has nine general categories of audit policy settings.
- Advanced audit policy, which has 10 categories of audit policy settings, and each category is further divided into subcategories, effectively giving you 53 comprehensive audit policy settings in total.
Before 2003, Windows shipped with all audit policy settings disabled by default. After 2003, the OS shipped with some of those settings turned on. However, those preconfigured settings rarely have any significance on their own. So, it is up to you to turn on the Windows audit policy settings meticulously as per your requirements. In simple terms, the depth of your network’s security audit policy and the information you would find in the security logs all depend on the Windows audit policy settings you make.
Now, let us delve more deeply into these two flavors of audit policies.
Basic audit policy
How to access the basic audit policy:
- Open search bar, type Local security policy, and hit Enter.
- In the console that pops up, look for Local policies and click on Audit policy.
It is best practice to use Local Security Policy only for viewing audit settings. (To edit them, use GPOs.)
As the name implies, it is basic in nature. There are nine general audit settings in this policy, as shown below.
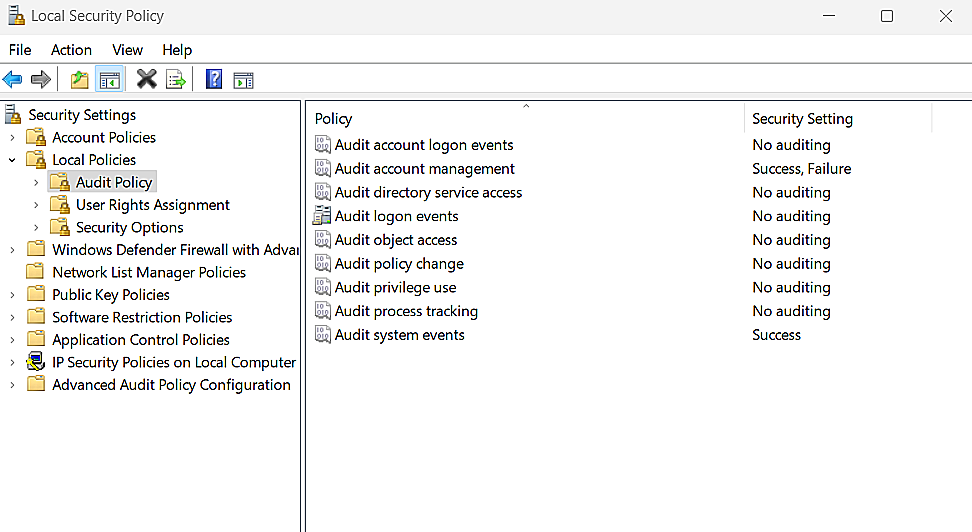
The basic audit policy settings capture security events in a fishnet fashion without any regard for event specificity. Thus, this type of auditing fails to meet the demands of a precision audit such as compliance auditing.
Advanced audit policy
Microsoft introduced Advanced Audit Policy in 2008 as an enhancement to its Basic Security Auditing. At first glance, the Advanced Audit Policy may appear to offer the same nine audit settings found in the Basic Audit Policy. However, there are a couple of major differences.
In the Advanced Audit Policy, each of the nine general audit settings is further divided into sub-categories. In other words, instead of controlling the recording of an entire gamut of events with the click of a single checkbox, these new provisions bundle events under various checkboxes, giving you the freedom to check and track events that matter to you. Therefore, you have a greater degree of flexibility in drafting and implementing a security audit policy that produces less noise.
Think of it like this: Basic audit policy had just nine main switches, each controlling an entire apartment’s electricity supply. Turn on a switch, and every room and every appliance of the corresponding apartment gets turned on, regardless of your need for them. In Advanced Audit Policy, more amenities and appliances were added, and they were all given a switch each so that you could turn on what you needed.
Also, the modern Group policy allows the selective application of an audit policy to a particular set of users or groups. This enables you to track critical security events specific to your business or IT regulations. For example, you can specifically track the actions of a selected group of users on a file server that hosts crucial data.
Here are the 10 categories and their sub-categories available in Advanced audit policy:
1. Account logon: Monitors attempts to authenticate account data on a domain controller or on a local Security Accounts Manager (SAM). Under the account logon category, there are 4 subcategories:
- Audit credential validation, which tracks NTLM authentication.
- Audit Kerberos authentication service, which tracks Kerberos authentication ticket granting tickets (TGT).
- Audit Kerberos service ticket operations to track Kerberos service tickets.
- Audit other account logon events help track events that do not come under any of the subcategories.
2. Account management: Monitors changes to user, computer, and group accounts. It has the following six subcategories:
- Audit application group management
- Audit computer account management
- Audit distribution group management
- Audit security group management
- Audit user account management
- Audit other account management events
3. Detailed tracking: Monitors the activities of individual applications and users on a computer and shows how that computer is being used. It has the following 4 subcategories:
- Audit DPAPI activity
- Audit process creation
- Audit process termination
- Audit directory service replication
4. DS Access: Provides a detailed audit trail of attempts to access and modify objects in Active Directory Domain Services. It has 4 subcategories:
- Audit detailed directory service replication
- Audit directory service access
- Audit directory service changes
- Audit directory service replication
5. Logon/logoff: Tracks all the attempts to log on to a computer interactively or over a network. Events in this category are crucial in detecting attacks on the network. This category has 11 subcategories:
- Audit account lockout
- Audit user/ Device claims
- Audit group membership
- Audit IPsec extended mode
- Audit IPsec main mode
- Audit IPsec quick mode
- Audit logoff
- Audit logon
- Audit network policy server
- Audit other logon-logoff events
- Audit special logon
6. Object access: Tracks attempts to access specific objects or types of objects on a network or computer. This one has 14 subcategories:
- Audit application generated
- Audit central access policy staging
- Audit certification services
- Audit detailed file share
- Audit file share
- Audit file system
- Audit filtering platform connection
- Audit filtering platform packet drop
- Audit handle manipulation
- Audit kernel object
- Audit other object access events
- Audit registry
- Audit removable storage
- Audit SAM
7. Policy change: Tracks changes to important security policies on a local system or network.
There are 6 subcategories in this category.
- Audit audit policy change
- Audit authentication policy change
- Audit authorization policy change
- Audit filtering platform policy change
- Audit MPSSVC rule-level policy change
- Audit other policy change events
8. Privilege use: Tracks the use of certain permissions on one or more systems. This has three subcategories:
- Audit non-sensitive privilege use
- Audit sensitive privilege use
- Audit other privilege use events
9. System: Tracks system-level changes to a computer that are not included in other categories and that have potential security implications. It has five subcategories:
- Audit IPsec driver
- Audit other system events
- Audit security state change
- Audit security system extension
- Audit system integrity
10. Global object access auditing: Allows administrators to define computer SACLs per object type for the file system or the registry. This has two subcategories:
- File system
- Registry
The challenge and our solution
It goes without saying that Windows audit policy is a significant component of an organization's security strategy. However, this audit policy stops with just event data collection. It is up to you to find the indicators of compromise in this behemoth of security event data, which is akin to finding a needle in a haystack. Things only get more complicated when you consider the need for context building, the IT regulation reporting requirements, or dealing with the number of machines that the logs get collected from.
So, what you need is a truly continuous monitoring system that can harvest a multitude of logs for you, keep looking for indicators of compromise in them, alert you in real time when it finds one, and also take care of your reporting needs. And that is exactly what ADAudit Plus does.
ADAudit Plus is a UBA-driven auditor that helps keep your AD, Azure AD, file systems (including Windows, NetApp, EMC, Synology, Hitachi, and Huawei), Windows servers, and workstations secure and compliant. ADAudit Plus transforms raw and noisy event log data into real-time reports and alerts, enabling you to get full visibility into activities happening across your Windows Server ecosystem in just a few clicks. For more information about ADAudit Plus, visit manageengine.com/active-directory-audit.
Don't wait for your annual compliance audit.
- Audit your AD and Azure
- Monitor user logon
- Troubleshoot AD lockouts
Thanks!
Please check your inbox for demo details.