- Related Products
- Log360
- AD360
- ADManager Plus
- ADAudit Plus
- ADSelfService Plus
- Exchange Reporter Plus
 Click here to expand
Click here to expand
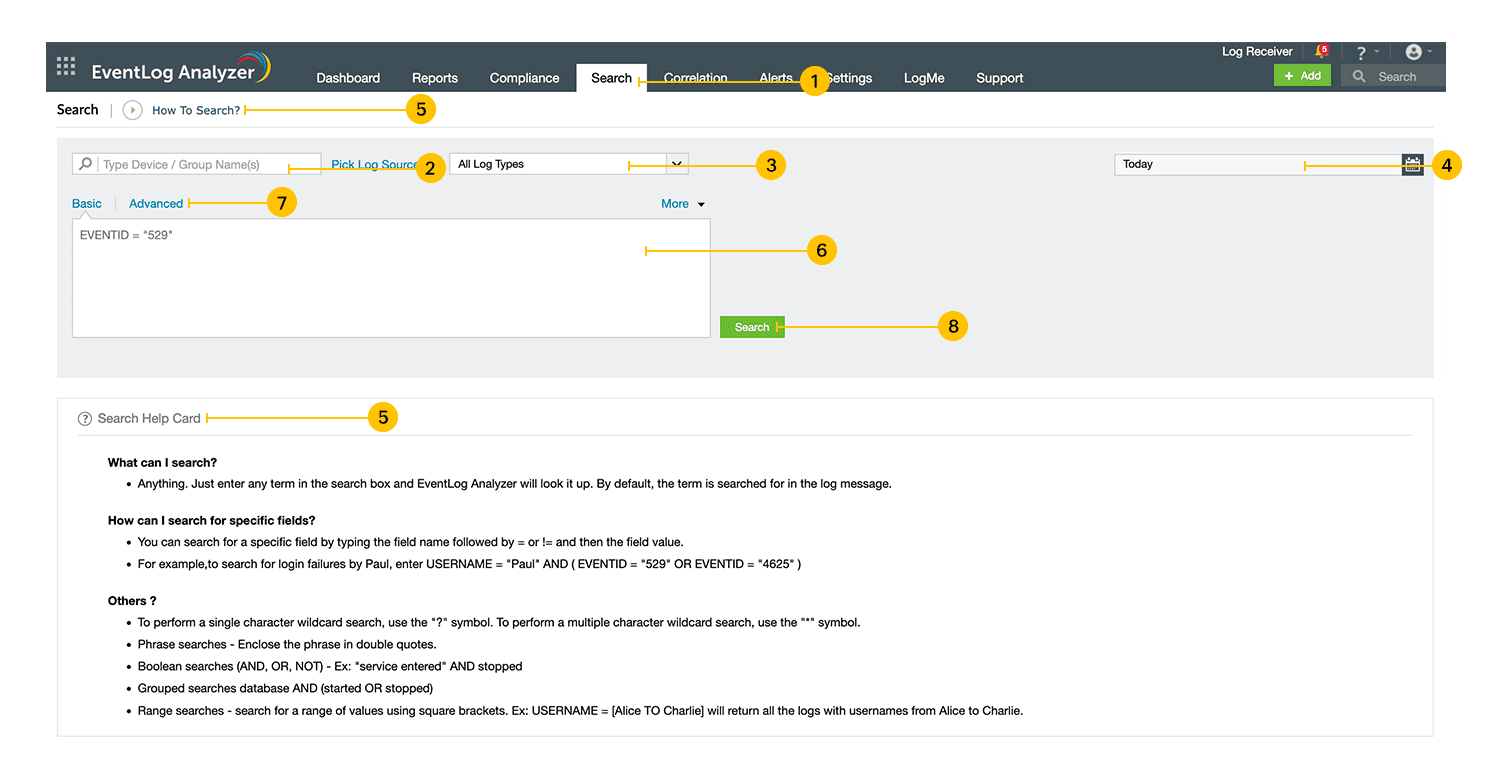
EventLog Analyzer provides a robust search engine to help you retrive log data during investigations. You can search raw logs collected by the server and detect events of interest such as misconfigurations, viruses, unauthorized access, unusual logons, applications errors, and more.
EventLog Analyzer provides basic and advanced search functionalities. Types of search queries supported are wild-card, phrase, boolean, grouped searches.
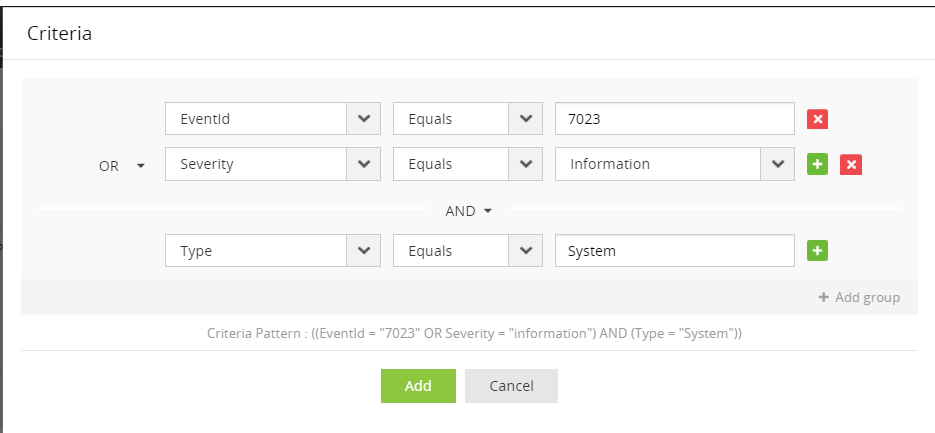
You can use the following boolean operators: AND, OR, NOT.
Syntax: <field name>=<field value> <boolean> <field name>=<field value>.
Example: HOSTNAME = 192.168.117.59 AND USERNAME = guest
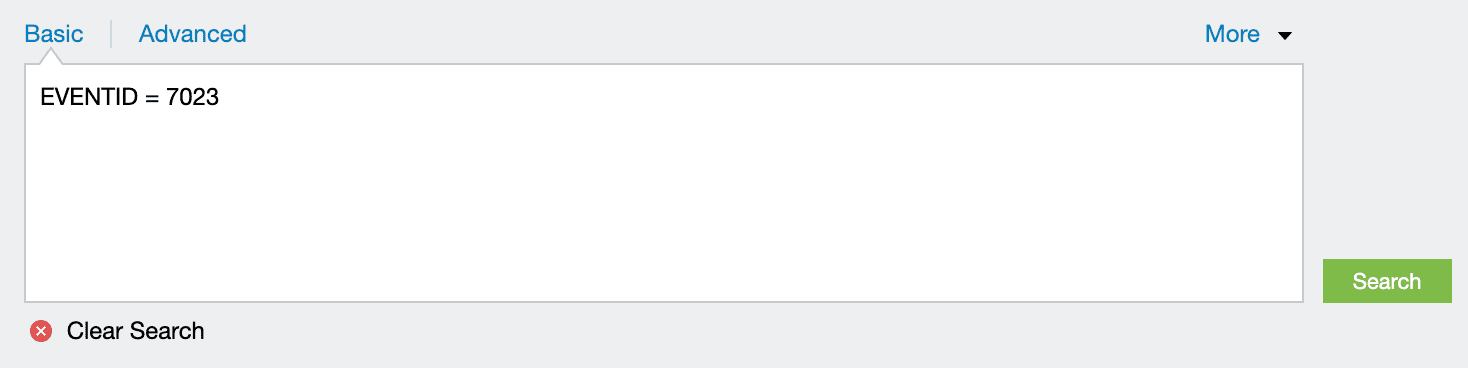
You can use the following comparison operators: =, !=, >, <, >=, <=.
Syntax: <field name> <comparison operator> <field value>.
Example: HOSTNAME = 192.168.117.59
You can use the following wild-card characters: ? for a single character, * for multiple characters.
Syntax: <field name> = <partial field value> <wild-card character>
Example: HOSTNAME = 192.*
Use double quotes ("") to specify a phrase as the field value.
Syntax: <field name> = "<partial field value>"
Example: MESSAGE = "session"
Use round brackets () to enclose groups of search criteria and relate them to other groups or search criteria using boolean operators.
Syntax: (<search criteria group>) <boolean operator> <search criterion>
Example: (SEVERITY = debug OR FACILITY = user) and HOSTNAME = 192.168.117.59
Logs stored in Eventlog Analyzer's Elasticsearch have a retention period that is customizable, and all logs beyond this period will be deleted. Apart from this, there is also an archive period beyond which, the logs will be archived and stored as a zip file. This is done to enhance memory utilization.
For example, if the archive period is set to 30 days and the retention period 90 days, logs less than 30 days old will be available for searching. And, logs older than 30 days but less than 90 days will be archived.
To search for logs beyond the archive period (30 days in this case), these archived logs need to be unarchived first before they can be made available for searching. This process takes some time depending on the log size. The log data will be available as and when a zip file gets unarchived.
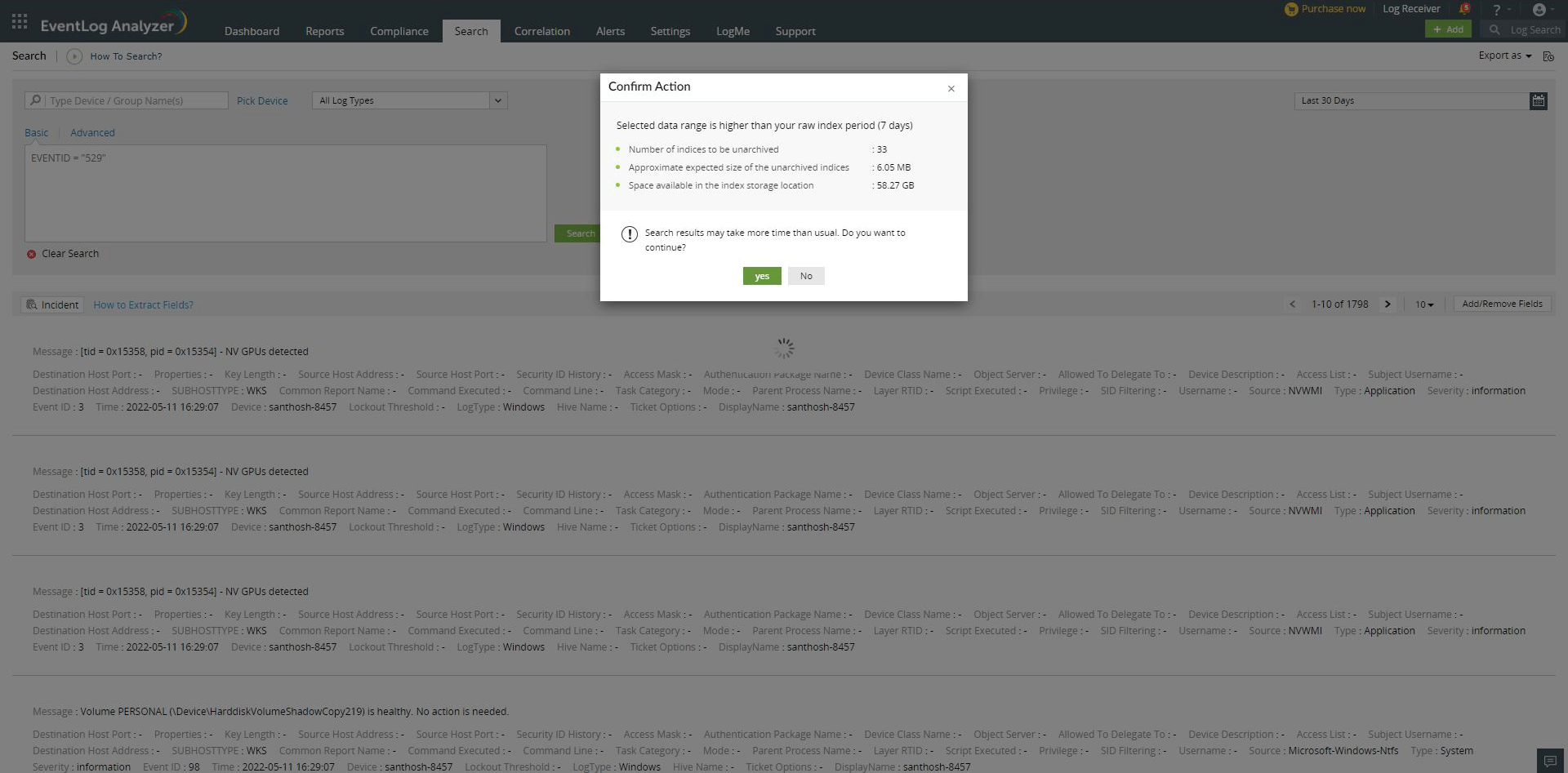
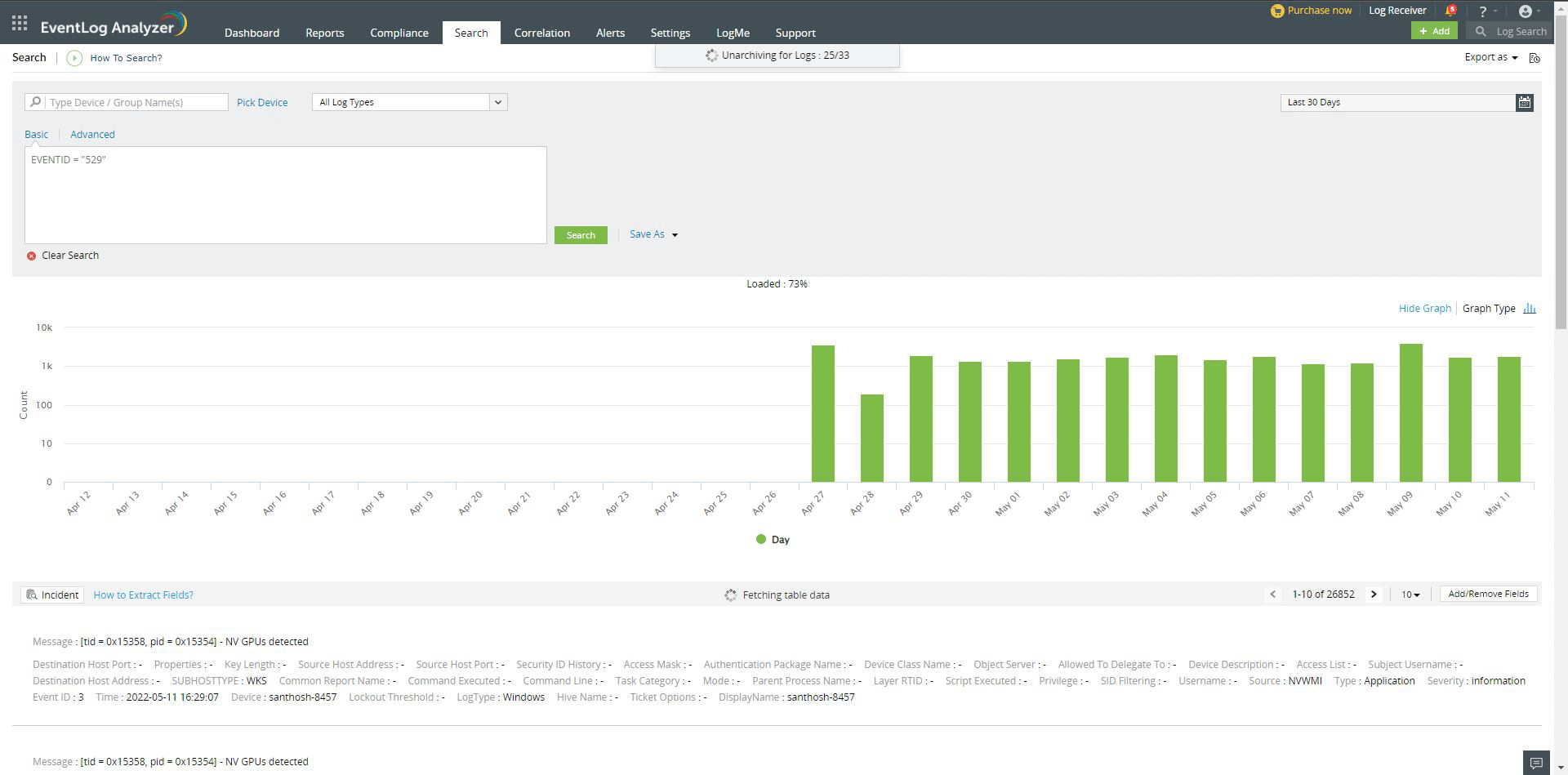
Free space, Expected unarchive size, Number of zip, and whether the user wants to proceed with unarchiving or cancel the option and return to normal search.
Copyright © 2020, ZOHO Corp. All Rights Reserved.